-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SonicWall CAS Manual Integration with Office 365



Description
Section 1:
Journal Rule
1.1 Use Classic Exchange admin center, in the Exchange admin center under ‘compliance management’ select ‘journal rules’.
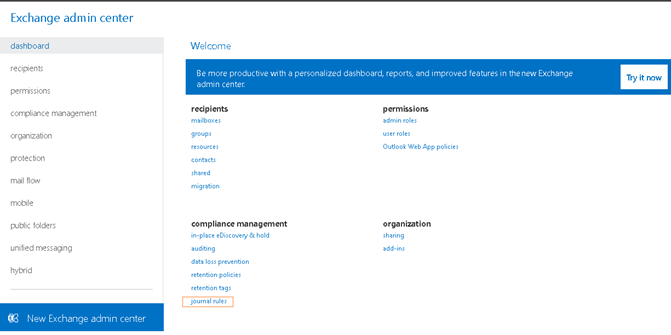
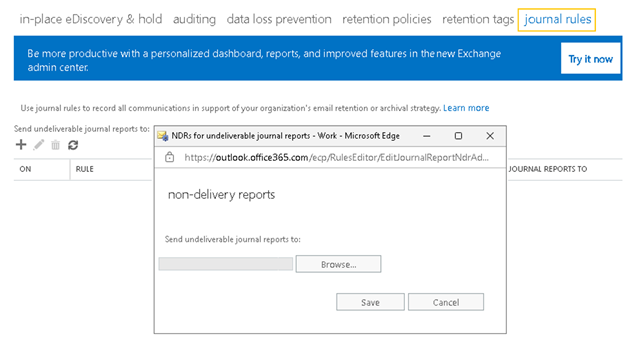
1.2 Add an account to receive journal reports that can’t be delivered to the journal destination.Click ‘Browser’ button to select an user, also could create a new user for this purpose.
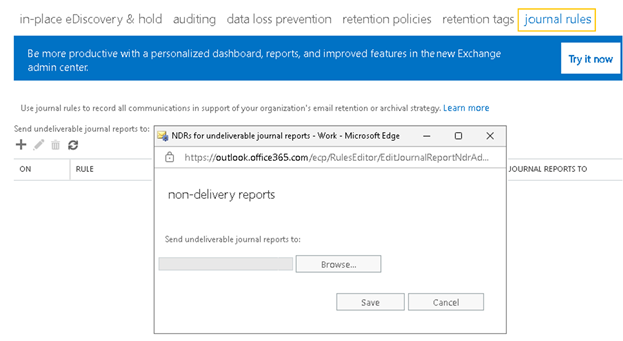
1.3 Click the plus button to add a new rule and fill out the fields in the popup window.
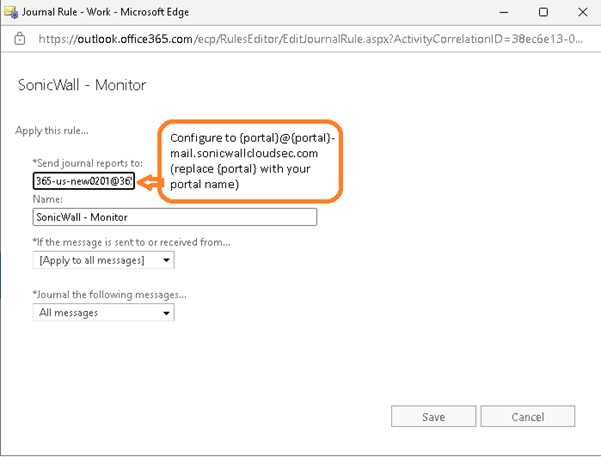
Note that in some configurations we refer to {portal}, this is an indication of your portal name. For
example, if your CAS portal url is ‘abc.sonicwallcloudsec.com', then you will need to replace ‘{portal}’ with
‘abc’ and should be added as abc@abc-mail.sonicwallcloudsec.com in the above Journal rule.
Section 2:
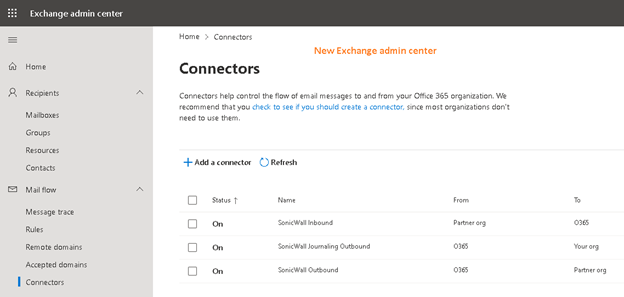
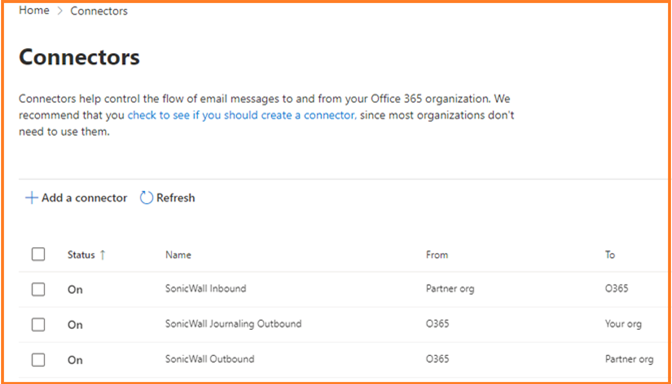
2.1.1 From Exchange admin center under ‘mail flow’ select ‘connectors’ to create 3 connectors.
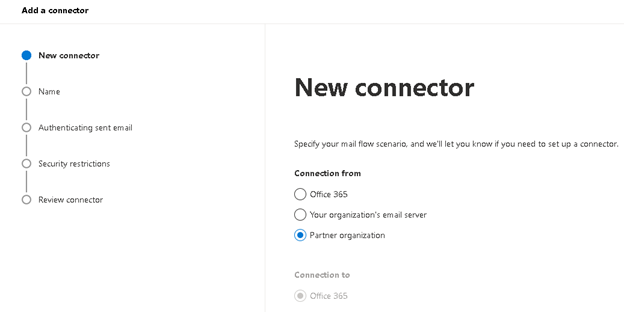
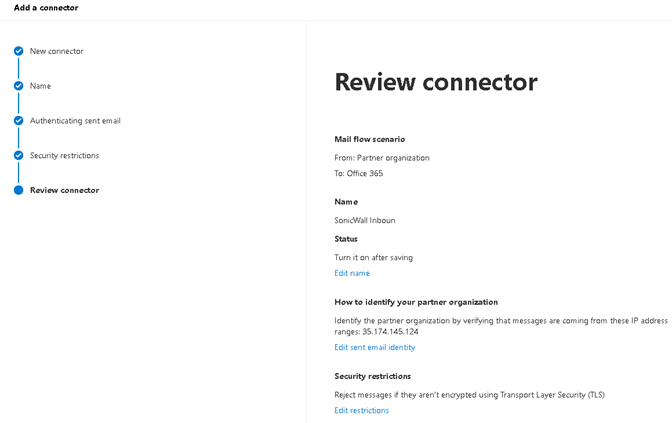
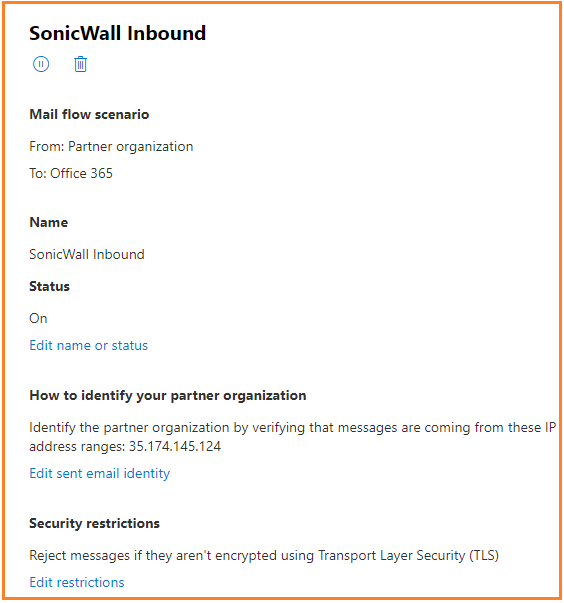
2.1.2 Add ‘SonicWall Inbound’ connector. Select connection from ‘Partner organization’. To ‘Office 365’ is selected.
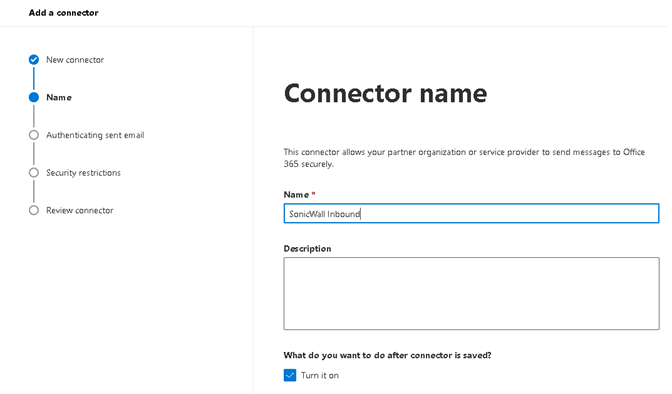
2.1.3 Name the connector ‘SonicWall Inbound’ and option to enter the description. ‘Turn it on’ is automatically checked. Click ‘Next’.
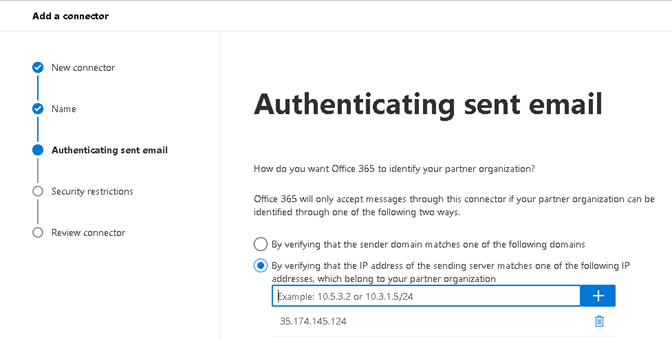
2.1.4 Select ‘By verifying the IP address of the sending server matches one of the following IP address…
Enter IP ’35.174.145.124’ and click ‘+’ to add.
2.1.5 Select ‘Reject email messages if they aren’t sent over TLS’.
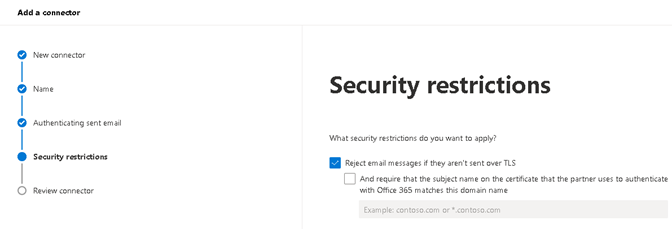
2.1.6 After done reviewing the configuration click ‘Create connector’.
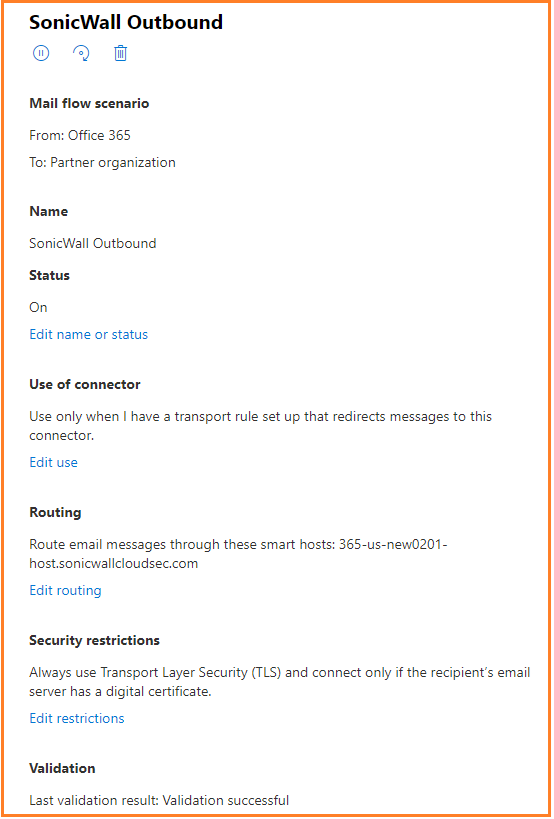
3.1.1 Add ‘SonicWall Outbound’ connector. Select Connection from ‘Office 365’ to ‘Partner organization’.
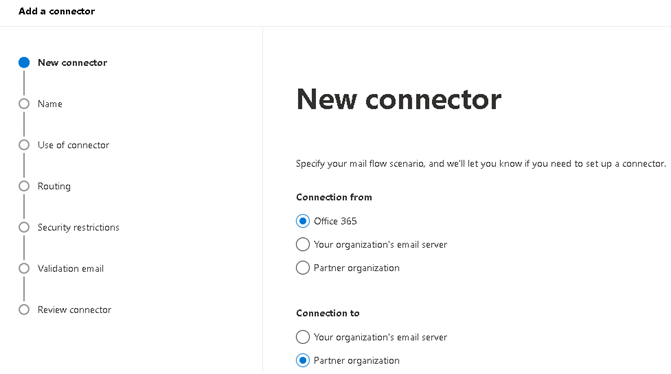
3.1.2 Name the connector ‘SonicWall Outbound’ and option to enter the description. ‘Turn it on’ was automatically checked. Click ‘Next’.
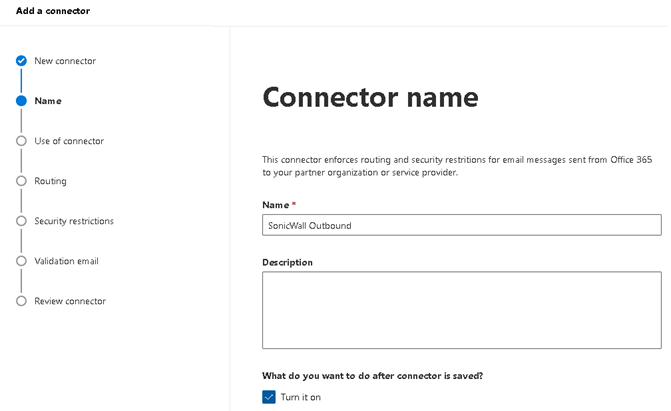
3.1.3 Select ‘Only when I have a transport rule setup that redirects messages to this connector’.
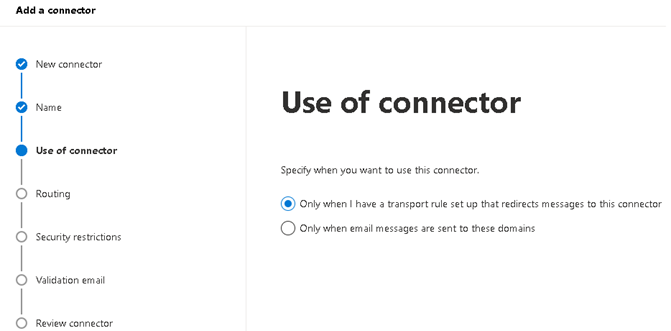
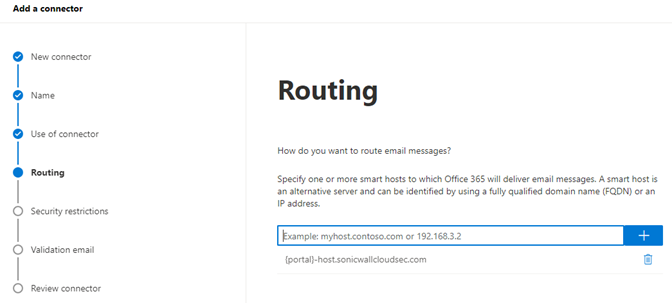
3.1.4 Routing: Select ‘Route email through these smart hosts’. Enter {portal}-host.sonicwallcloudsec.com and click plus sign.
Note that in some configurations we refer to {portal}, this is an indication of your CAS portal name. For
example, if your CAS portal url is ‘abc.sonicwallcloudsec.com', then you will need to replace ‘{portal}’ with
‘abc’ and should be added as abc-host.sonicwallcloudsec.com in the above ‘SonicWall Outbound’ Connector.
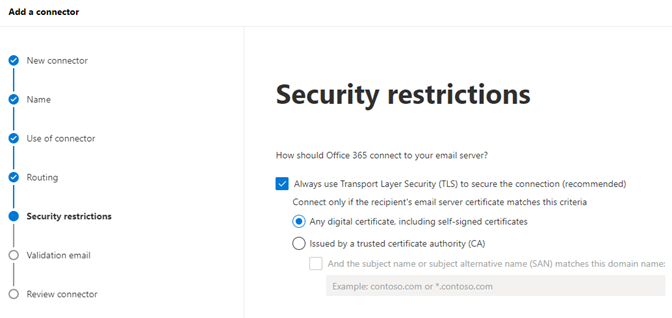
3.1.5 Check Always use Transport Layer Security (TLS) to secure the connection (recommended) and select ‘Any digital certificate, including self-signed certificates.
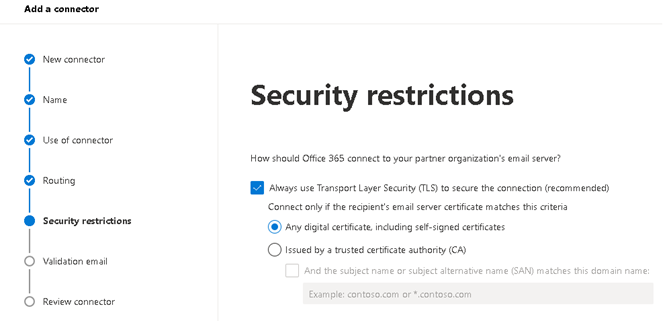
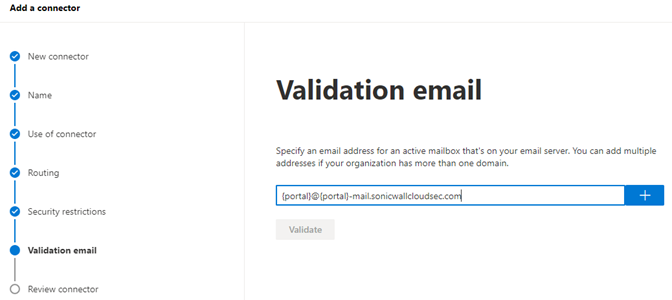
3.1.6 Enter {portal}@{portal}-mail.sonicwallcloudsec.com to validate email. Review connector and click ‘Create Connector’.
4.1.1 Add ‘SonicWall Journaling Outbound’ connector.
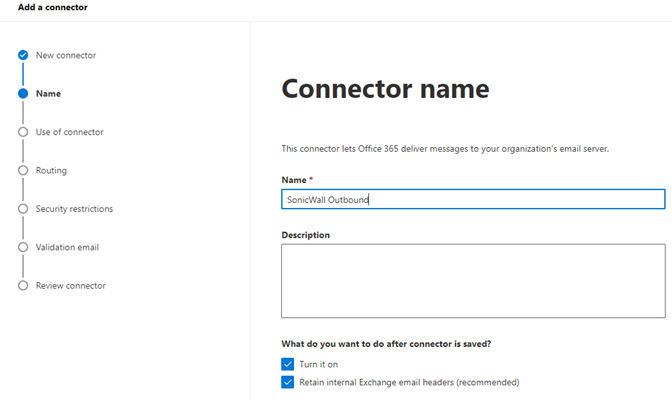
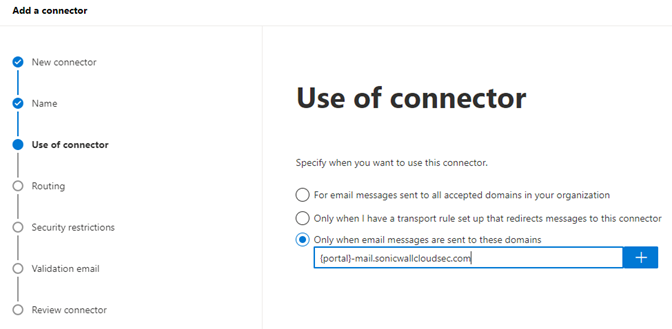
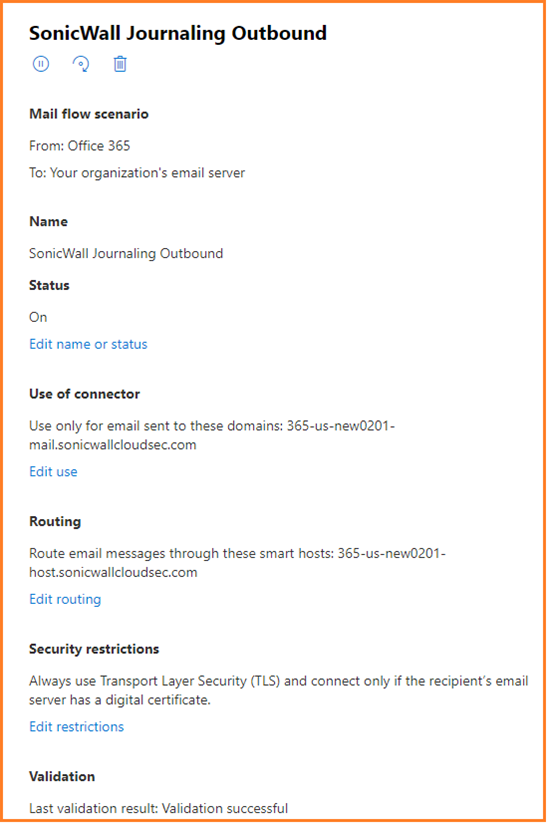
After all 3 connectors finished:
Section 3:
Mail Flow Rule
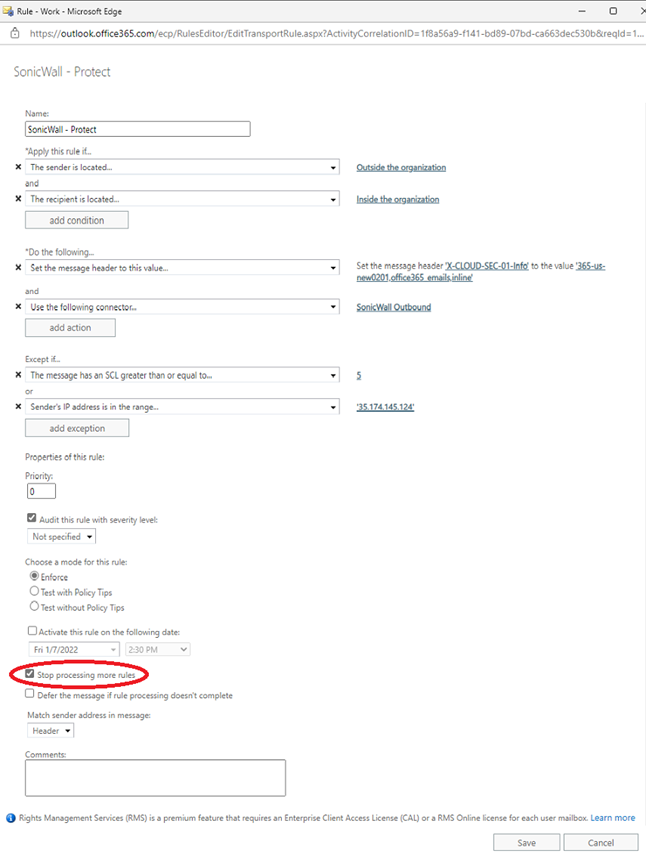
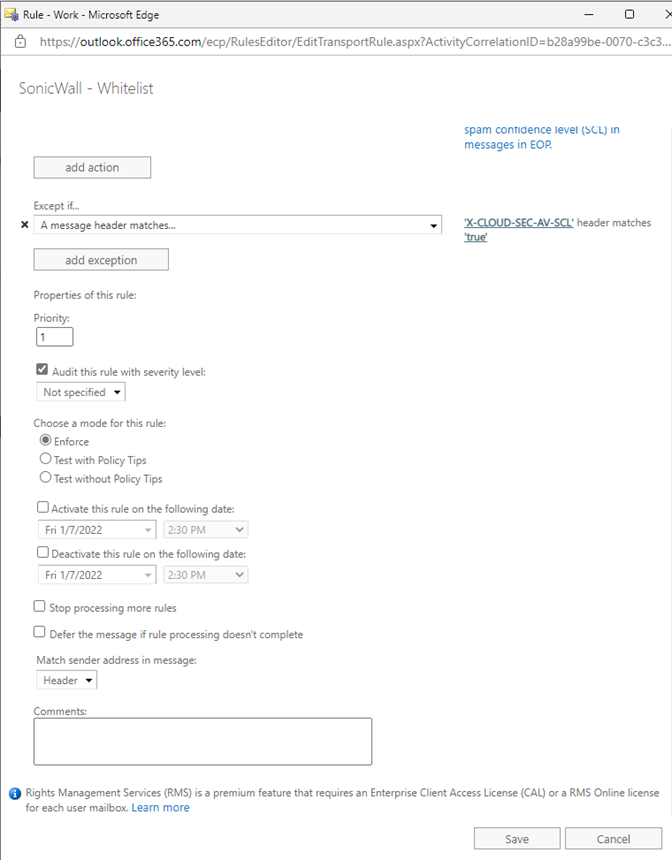
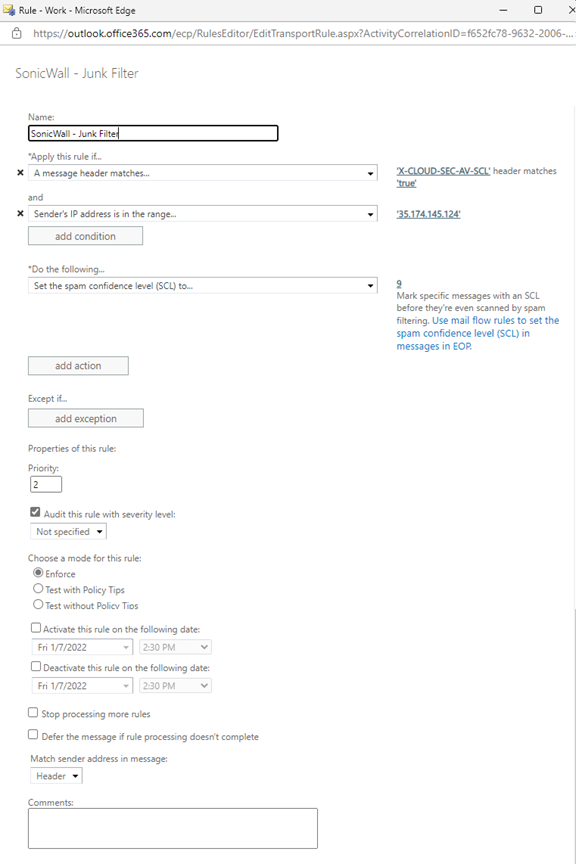
After completed all three rules.
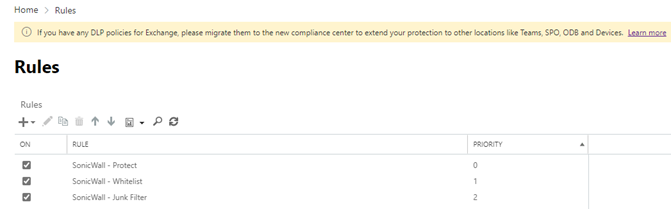
Once all above configured in Exchange admin center then CAS Admin can login to cloud.sonicwall.com to start onboarding O365Mail and select manual option.
Related Articles
- Converting Cloud App Security licenses from annual to monthly
- Cloud Application Security FAQs
- Cloud Edge License Provisioning and Management through MSSP Monthly






 YES
YES NO
NO