-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SMB SSL-VPN: Configuring the SSL-VPN Group Configuration for LDAP Authentication Domains



Description
SMB SSL-VPN: Configuring the SSL-VPN Group Configuration for LDAP Authentication Domains
Resolution
Feature/Application:
Please Note: The Microsoft Active Directory database uses an LDAP organization schema. The Active Directory database may be queried using Kerberos authentication (the standard authentication type; this is labeled "Active Directory" domain authentication in the SonicWall SSL VPN appliance), NTLM authentication (labeled NT Domain authentication in SonicWall SSL VPN appliance), or using LDAP database queries. An LDAP domain configured in the SonicWall SSL VPN appliance can authenticate to an Active Directory server.
Procedure:
To configure LDAP authentication, perform the following steps:
Step 2 Select LDAP from the Authentication Type menu. The LDAP domain configuration fields is displayed.
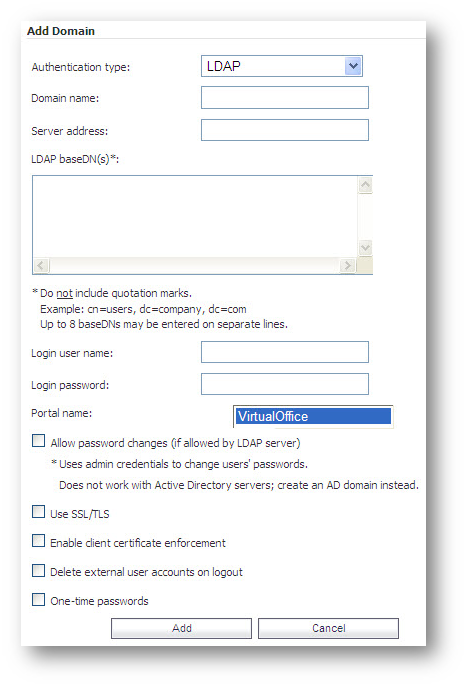
Verify user name matches Common Name (CN) of client certificate - Select this checkbox to require that the user's account name match their client certificate.Verify partial DN in subject - Use the following variables to configure a partial DN that will match the client certificate:User name: %USERNAME%Domain name: %USERDOMAIN%Active Directory user name: %ADUSERNAME%Wildcard: %WILDCARD%
if configured - Only users who have a One Time Password email address configured will use the One Time Password feature.
required for all users - All users must use the One Time Password feature. Users who do not have a One Time Password email address configured will not be allowed to login.
using domain name - Users in the domain will use the One Time Password feature. One Time Password emails for all users in the domain will be sent to username@domain.com .If you selected if configured or required for all users in the One-time passwords drop-down list, the LDAP e-mail attribute drop-down list will appear, in which you can select mail, userPrincipalName, or custom. These are defined as:mail - If your LDAP server is configured to store email addresses using the "mail" attribute, select mail.
mobile or pager - If your AD server is configured to store mobile or pager numbers using either of these attributes, select mobile or pager, respectively. Raw numbers cannot be used, however, SMS addresses can.
userPrincipalName - If your LDAP server is configured to store email addresses using the "userPrincipalName" attribute, select userPrincipalName.
custom - If your LDAP server is configured to store email addresses using a custom attribute, select custom. If the specified attribute cannot be found for a user, the email address assigned in the individual user policy settings will be used. If you select custom, the Custom attribute field will appear. Type the custom attribute that your LDAP server uses to store email addresses. If the specified attribute cannot be found for a user, the email address will be taken from their individual policy settings.
Source: SonicWall SSL VPN 4.0 Administrator's Guide
Related Articles
- How to download Client Installation package and the access agents from the appliance using WinSCP
- SMA 1000: How to update Advanced EPC Signatures to the Latest Version
- If OTP is enabled, NX disconnects after SMA100 Connect Agent installation






 YES
YES NO
NO