-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SMA100: Access Policy to allow RDP but block all services over NetExtender/Mobile Connect



Description
The Secure Mobile Access web-based management interface provides granular control of access to the SMA appliance. Access policies provide different levels of access to the various network resources that are accessible using the SMA appliance. There are three levels of access policies: global, groups, and users. You can block and permit access by creating access policies for an IP address, an IP address range, all addresses, or a network object.
Resolution
Access Policy Hierarchy:
An administrator can define user, group and global policies to predefined network objects, IP addresses, address ranges, or all IP addresses and to different Secure Mobile Access services. Certain policies take precedence.
The Secure Mobile Access policy hierarchy is:
• User policies take precedence over group policies
• Group policies take precedence over global policies
• If two or more user, group or global policies are configured, the most specific policy takes precedence
 EXAMPLE: Let us consider that we have a user test connecting to the SMA using NetExtender and once connected would like to get access to IP: 172.27.64.194 which is present on X0. We want it to be able to only RDP to this client and allow no other services like Telnet, ping etc.
EXAMPLE: Let us consider that we have a user test connecting to the SMA using NetExtender and once connected would like to get access to IP: 172.27.64.194 which is present on X0. We want it to be able to only RDP to this client and allow no other services like Telnet, ping etc.
To achieve this, we can create two set of policies.
- A global deny rule that blocks all traffic to that IP address. You can also set this for the entire network at a global level and allow access on group and user level. In this example, we are creating these rules specific to one IP address.
Navigate to Services | Policies and click on Add Policy. Select the following for the policy.
Policy Owner: Global Policy
Policy Name: Block all services
Apply Policy To: IP address
IP Address: 172.27.64.194
Protocols: ALL
Service: All Services
Status: Deny
Click on Accept.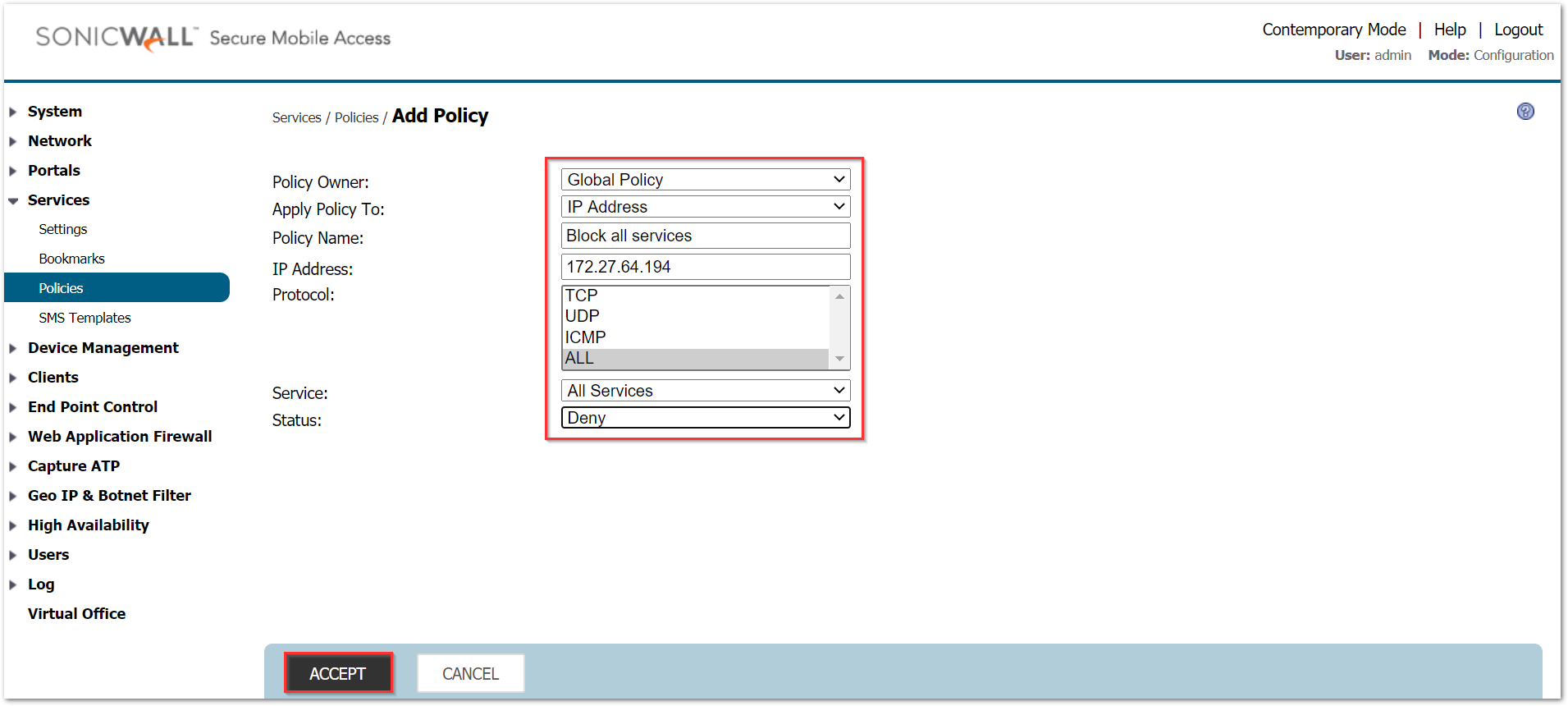
- A group level policy to allow RDP to the same IP address.
Click on Add policy. Select the following for the policy.
Policy Owner: Group policy (support)
Policy Name: Allow only RDP
Apply Policy To: IP address
IP Address: 172.27.64.194
Protocols: TCP
Port Range/Port Number: 3389
Service: All Services
Status: Allow
Click on Accept.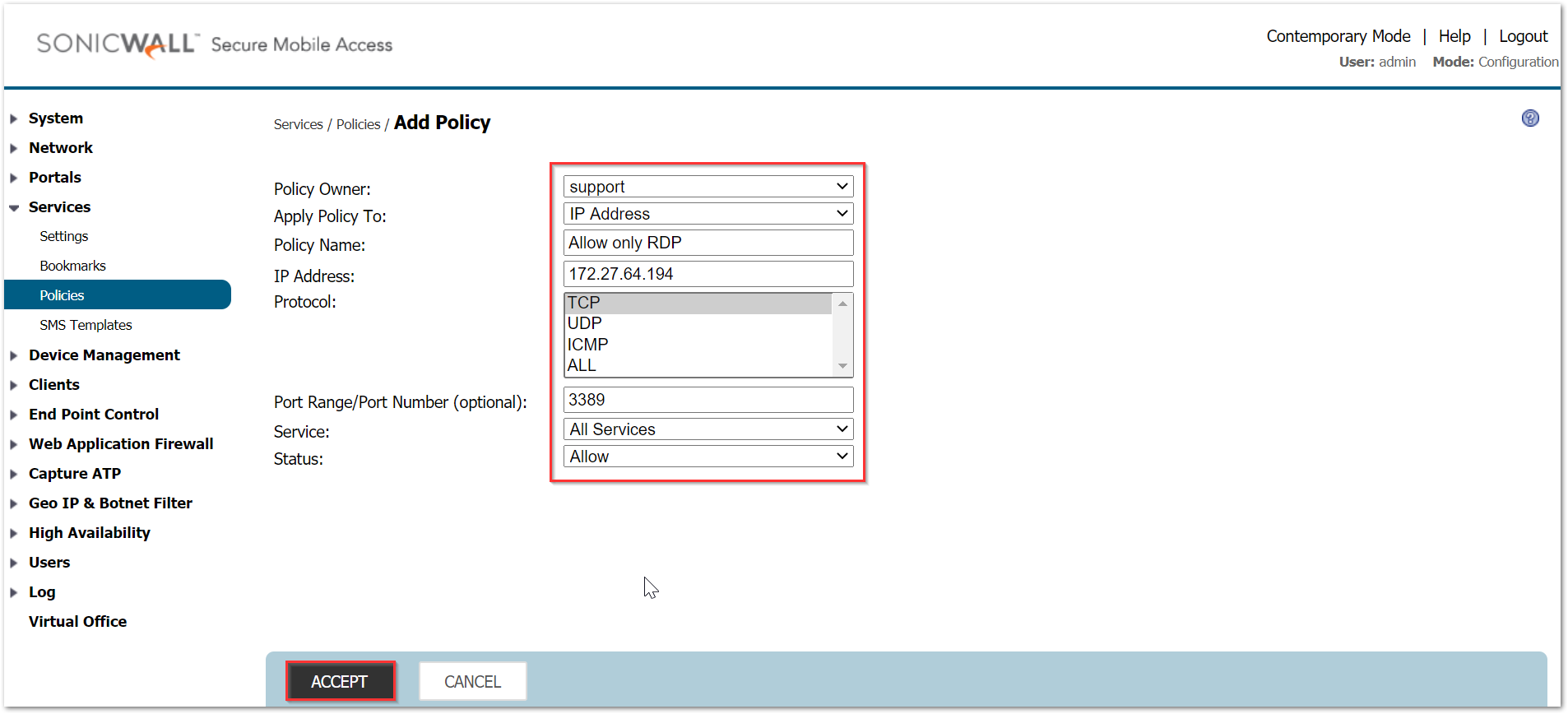
 NOTE: It is highly important to select the Services as 'All Services' and explicitly mention the port number. There is also an option to select the service as 'Terminal Services RDP' but that will not trigger for connections made using NetExtender or Mobile Connect.
NOTE: It is highly important to select the Services as 'All Services' and explicitly mention the port number. There is also an option to select the service as 'Terminal Services RDP' but that will not trigger for connections made using NetExtender or Mobile Connect.
Both the policies will show up and it does not matter which one is on top of the list as the allow policy is created on group level and takes precedence over the deny rule at global level.
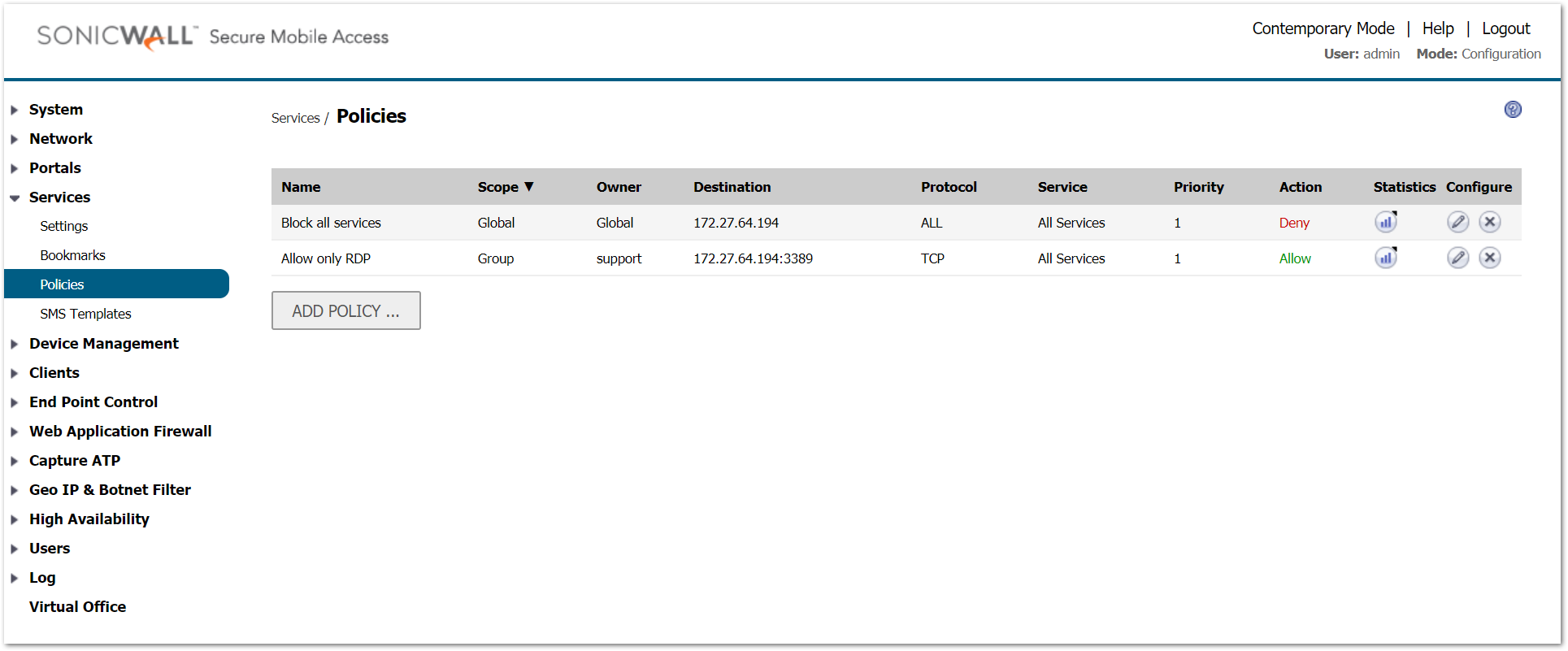
How to Test:
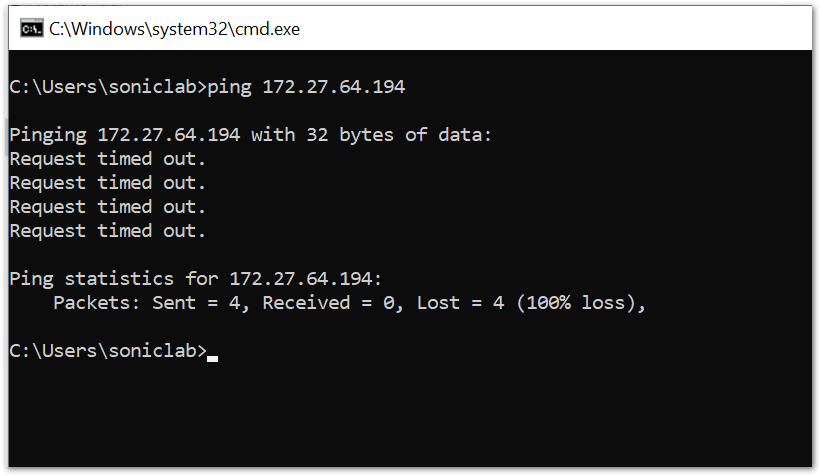
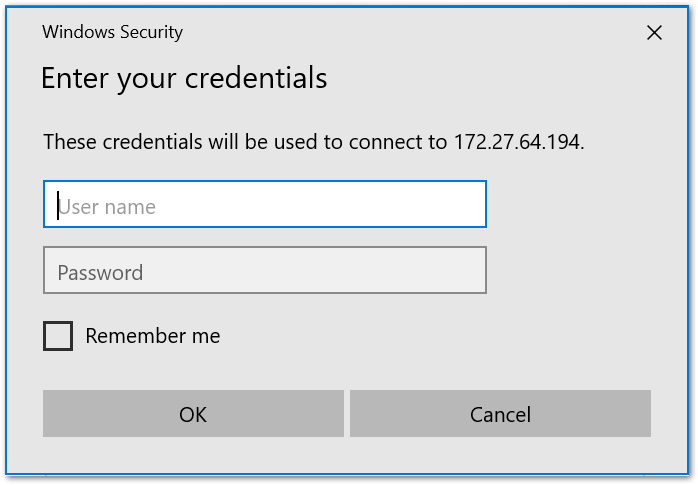
Connect using the user 'test' that belongs to the group 'support' and perform RDP and ping tests to 172.27.64.194 post connection.
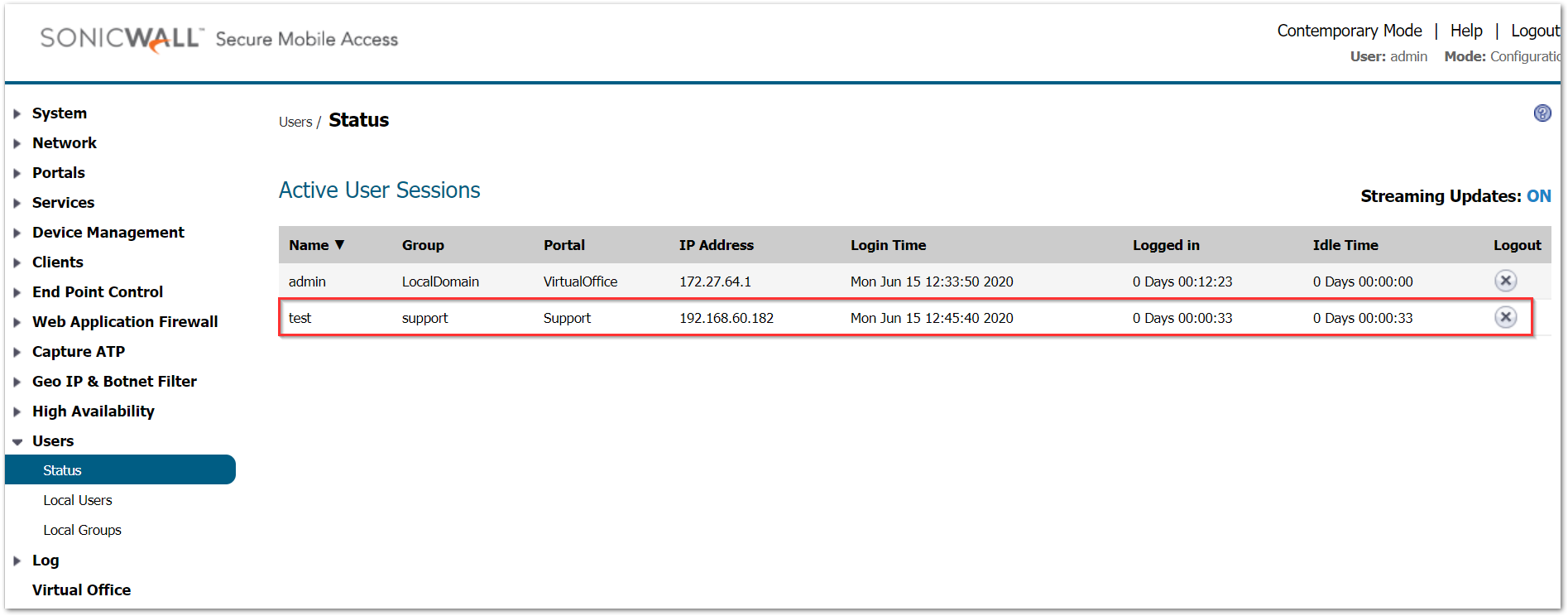
The ping test fails due to the global policy:
The RDP connection succeeds due to the group policy:
Related Articles
- How to download Client Installation package and the access agents from the appliance using WinSCP
- SMA 1000: How to update Advanced EPC Signatures to the Latest Version
- If OTP is enabled, NX disconnects after SMA100 Connect Agent installation






 YES
YES NO
NO