-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SMA (Secure Mobile Access) Appliance Management Console Troubleshooting: Part 2



Description
SMA (Secure Mobile Access) Appliance Management Console Troubleshooting: Part 2
This provides general troubleshooting instructions and discusses the troubleshooting tools available in the Appliance Management Console (AMC). Failure in core networking services (such as DHCP, DNS, or WINS) will cause unpredictable failures.
The User Sessions page in AMC can be used to monitor, troubleshoot or terminate sessions on your appliance or HA pair of appliances. You can sort through the summary of session details and, if needed, display details on how a device was classified, and why. About 24 hours worth of data is kept; even items that have been deleted or modified are displayed. See Viewing User Access and Policy Details in the SMA 11.3 Administration Guide.
SMA (Secure Mobile Access) Appliance Management Console Troubleshooting: Part 2
Topics in Part 2 will cover:
- AMC Issues
- Authentication Issues
- Using Personal Firewalls with Agents
- Secure Mobile Access Services Issues
Resolution
AMC Issues
One of the most common errors in AMC is to make a configuration change and then forget to apply it. A Pending changes link appears in the top-right corner in AMC whenever changes have been made but not applied. Click the link and then click Apply Changes to automatically restart the services.
Troubleshooting AMC issues
| Issue | Solution |
| Can't access AMC | If you can't access AMC, connect a cable to the internal network interface on the appliance and verify that you can access AMC without any network. If this type of connection is impractical, put the laptop on the same network segment as the internal interface (to get as close to the appliance as possible). If you still can't access AMC, make sure your URL includes the https:// protocol identifier. Also verify that you've included the port number 8443 in the URL. |
| Can't log in to AMC on the internal network | If your browser cannot log in to AMC on the internal network, ensure that traffic from the client to the IP address of the appliance's internal interface actually arrives at the internal interface. Using the network traffic utility in AMC, which is based on tcpdump, you can capture traffic on the internal interface (eth0). Any client attempts to reach AMC should show traffic TCP SYN packets from the client's IP address directed to port 8443. See Capturing Network Traffic in the AMC Administration Guide for more information. |
| Can't log in | If AMC login fails with the error "Invalid Login Credentials, " verify the spelling of your username and password. Passwords are case-sensitive; ensure that Caps Lock and Num Lock are not enabled. |
| CPU utilization is spiking | If you are using nested group lookup on your LDAP or AD authentication server, make sure that you are also caching the lookup results: searching the entire directory tree takes time and increases the CPU usage on both the appliance and your authentication server. |
Authentication Issues
An authentication server is referenced in a realm.
Troubleshooting authentication issues
| Issue | Solution |
| Access to the external authentication server(s) | Verify that you can access the external authentication server by using the network traffic utility in AMC, which is based on tcpdump. You can send this network traffic data to Technical Support, or review it using a network protocol analyzer like Wireshark. See Capturing Network Traffic in the AMC Administration Guide for more information. |
| Authentication server credentials | Verify that AMC contains the proper credentials for access to your external server. For LDAP, check the Login DN and Password settings and click Test Connection. For RADIUS, check the Shared secret setting. |
| Authentication server logs | Review the authentication server logs. Make sure you're not entering invalid credentials or having connectivity problems. |
| User authentication using an LDAP or AD server takes too long or times out | If you are using nested group lookup on your LDAP or AD server, make sure that you are also caching the lookup results, because searching the entire directory tree takes time. To reduce the load on your directory and get better performance, cache the attribute group or static group search results by selecting the Cache group checking check box. |
Using Personal Firewalls with Agents
Some firewall products display a security alert during the provisioning of Secure Mobile Access agents or EPC components. This is because the firewalls are regulating outbound connections by process (in addition to port and protocol). In most cases, the user can simply "unblock " or "permit " the outbound connection.
Connect Tunnel users should configure their personal firewalls to allow the Secure Mobile Access VPN service (ngvpnmgr.exe) and Secure Endpoint Manager (AventailComponents.exe) to access the Internet and to add the SMA appliance by host name or IP address as a trusted host or zone. In addition, Windows Vista users should make an exception for epiVista.exe.
There are a few firewalls, such as one supplied by Trend Micro, that do not permit a user with restricted rights to override the firewall settings. For corporate systems on which users have limited access rights, you may need to update the firewall settings before deploying the Secure Mobile Access VPN so that users won't have to respond to security dialog prompts.
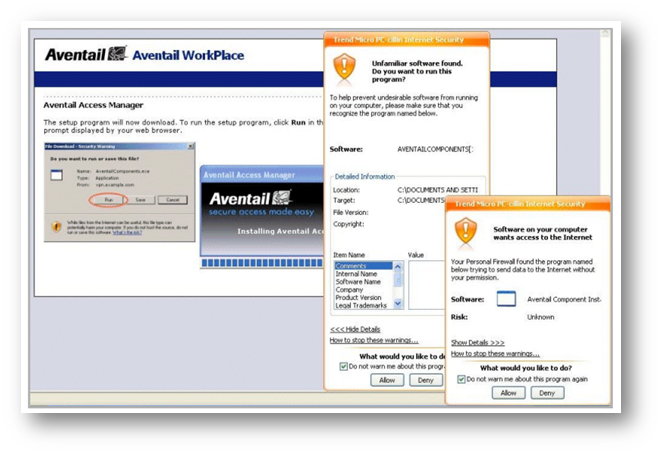
Consult the documentation for your corporate personal firewall to determine the firewall policy. If a firewall update proves necessary, a rule that allows all processes to communicate with the appliance over port 443 is recommended.
Secure Mobile Access Services Issues
To see a brief summary of which services are running, click Services on the main navigation menu.
Web Proxy Service Issues
- Temporarily increase the server log level in AMC to Verbose. (Don't forget to click Pending changes in the top-right corner of any AMC page, and then click Apply Changes to automatically restart the service.)
- To see the Web proxy service log, click Logging in the main navigation menu, and then select Web proxy audit log from the Log file list. Verify that your connection request appears in the log.
- Verify that your DNS server can resolve the Web proxy service Server name setting in AMC to the IP address of the Web proxy service interface. You can use the lookup tool within AMC (see Using DNS Lookup in the Administration Guide), or you can issue the nslookup or dig commands from a command prompt.
- If your network uses NAT to translate IP addresses, make sure that the Web proxy service Server name setting contains the IP address of the outside (or public) IP address that is being substituted using NAT.
Web Proxy Agent Issues
The Web proxy agent provides access to URL resources on Windows systems with Internet Explorer 7.0 or later. WorkPlace indicates that Web proxy mode is active on a client by displaying "Secure Mobile Access Web proxy " in the Connection Status area.
To troubleshoot whether the Web proxy agent is running properly on a client machine, follow these steps:
- On the client machine, press Ctrl+Alt+Delete and then click Task Manager.
- Look in Windows Task Manager's Processes list for the process ewpca.exe. If that file is present, the standard Web mode access agent is running, although it may not be receiving network traffic.
- To confirm that the Web proxy agent is receiving traffic, start Internet Explorer and then select Tools > Internet Options. On the Connections tab, click LAN Settings or Settings for the dial-up/VPN connection you are using to connect to the appliance.
- In the appropriate Settings dialog box for your connection type, verify that the Use automatic configuration script check box is selected and that the Address box contains the following address:
http://127.0.0.1:/redirect.pac
Internet Explorer uses the redirect.pac file to determine which connections to send to the Web proxy agent.
- To view the resource addresses that are redirected by the redirect.pac file, open the file in a text editor.
The file is located on the client machine in this folder:
Documents and SettingsApplication DataAventailewpca
The //Redirection Rules// section of the redirect.pac file lists the addresses defined as destinations that are sent through the standard Web proxy agent. These addresses come from the list of network and URL resources defined in AMC.
Related Articles
- How to download Client Installation package and the access agents from the appliance using WinSCP
- SMA 1000: How to update Advanced EPC Signatures to the Latest Version
- If OTP is enabled, NX disconnects after SMA100 Connect Agent installation






 YES
YES NO
NO