-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Single-sign-on (SSO) using NTLM Browser Authentication in SonicOS 5.8. and above



Description
Single-sign-on (SSO) using NTLM Browser Authentication in SonicOS 5.8. and above
Resolution
As an enhancement to Single Sign-On, SonicOS can now use NTLM authentication to identify users who are browsing using Mozilla-based browsers (including Internet Explorer, Firefox, Chrome and Safari). NTLM is part of a browser authentication suite known as “Integrated Windows Security” and should be supported by all Mozilla-based browsers. It allows a direct authentication request from the SonicWall appliance to the browser with no SSO agent involvement. NTLM authentication works with browsers on Windows, Linux and Mac PCs, and provides a mechanism to achieve Single Sign-On with Linux and Mac PCs that are not able to interoperate with the SSO agent
NTL authentication can be used as a supplment to identifying users via an SSO agent or, with some limitations, on its own without the agent. If the user is logged into the domain and the browser sees the SonicWall appliance as being located in the local intranet of the domain then the authentication can be fully automatic and transparent to the user, using the user's domain credentials which the appliance authenticate via RADIUS. In other cases the browser may ask the user to enter credentials to authenticate with the appliance, but even then the browser can cache those credentials so that further authentications will happen transparently.
NTLM is a challenge-response authentication protocol. It consists of the following three messages:
- NEGOTIATE_MESSAGE (Type 1: Sent by client to Server listing supported features.
- CHALLENGE_MESSAGE (Type 2) Sent by server listing supported and agreed upon features. It also includes a server challenge.
- AUTHENTICATE_MESSAGE (Type 3): Response from the client containing the domain and username of the client among other things.
In the SonicWall context when a client computer tries to access a website on the internet, the above translates to the following:
- Client GET request for the intended website.
- SonicWall redirects the client to http:///ntlmAuth.html (eg. http://192.168.168.168/ntlmAuth.html)
- Client NEGOGIATE Message with client OS, workstation domain & workstation name.
- SonicWall CHALLENGE Message with target domain, server name etc.
- Client AUTHENTICATE Message with Domain name, User name & Host name.
Having obtained the user information from the cilent computer, SonicWall queries the RADIUS server whether the user can be allowed access:
- SonicWall sends a RADIUS Access Request message to the RADIUS server, requesting authorization to grant access to the client based on the credentials supplied.
- The RADIUS server responds with Access Accept message to grant access to the client if the credentials supplied by the client meet the criteria defined in the RADIUS server.
If the client is granted access by the RADIUS server, SonicWall gets the user's group membership information from the LDAP server in the following manner:
- SonicWall sends a searchRequest message with the cilent's username and domain name to the LDAP server to get group membership information.
- The LDAP server responds with the CN of the user followed by the user's group membership information.
Based on the user group membership information and based on CFS, App Control and App Rules policies, SonicWall allows / blocks the user from accessing the requested site.
Deployment:
This article describes the method to configure Browser NTLM Authentication in SonicWall:
1. Configuring LDAP in SonicWall
2. Configuring Radius in SonicWall
3. Configuring SonicWall SSO Agent as the primary single-sign-on method
4. Configuring SSO using Browser NTLM Authentication
5. Client Computer Configuration
In this section we illustrate the method to configure LDAP NTLM authentication.
- Login to the SonicWall managment GUI.
- Navigate to the Users > Settings page.
- In the Users > Settings page, select LDAP under Authentication method for login.
- Click on Configure to bring up the LDAP Configuration window.
- Configure the following settings:
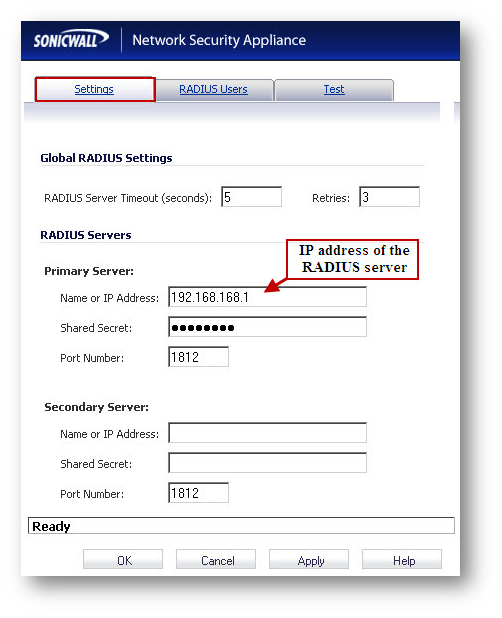
Configuring Radius in SonicWall
In this section we illustrate the method to configure RADIUS NTLM authentication.
- In the Users > Settings page click on the 3rd Configure button next to RADIUS may also be required for CHAP/NTLM (Please Note: This option is available only when LDAP is selected as the authentication method).
- Click on Configure to bring up the RADIUS Configuration window.
- Configure the following settings:
Configuring SonicWall SSO Agent as the primary single-sign-on method
Although NTLM can be used as a stand-alone single-sign-on method, SonicWall recommends using the SonicWall SSO Agent as the primary single-sign-on method and use NTLM if the SonicWall SSO Agent fails.
- On the Users > Settings page, select SonicWall SSO Agent under Single-sign-on method and click on the Configure button.
- In the SonicWall SSO Agent Authentication Configuration window, configure the following settings:
Configuring SSO using Browser NTLM Authentication
- In the Users > Settings page, select Browser NTLM authentication only under Single-sign-on method.
- Click on Configure to bring up the SonicWall SSO Agent Authentication Configuration window.
- Configure the following settings:
Although in most cases authentication would be automatic using the user's domain credentials, in some cases the browser may prompt the use to enter credentials. Whether the browser will use the domain credentials to give fully transparent and automatic authentication depends on its seeing the appliance domain name or IP address. Browsers may require some configuration to be able to see the appliance domain name or ip address.
Internet Explorer, Chrome: It may be necessary to add the appliance's domain name or ip address under Internet Options > Security > Local Intranet > Sites > Advanced. This can also be done using Windows Group Policy.
Firefox: Add the appliance's domain name or ip address under About:Config > network.automatic-ntlm-auth.trusted-uris
Windows 7 or Vista PCs
In the newer Windows operating systems like Windows 7 or Vista, NTLM authentication is disabled by default and has to be enabled manually. When enabling NTLM authentication it is not recommended to choose only NTLMv2 as it does not support RADIUS and MS-CHAPv2. To enable NTLM authentication, follow these steps:
- Open Control Panel
- Select Administrative Tools
- Click on Local Security Policy
- Go to Local Policies > Security Options
- Edit the "Network Security: LAN Manager authentication level" setting.
- Set it to "Send NTLM response only" or "Send LM & NTLM - use NTLMv2 session security if negotiated".

Once a client computer is successfully authenticated the following log message would appear under Log > View

Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series


















 YES
YES NO
NO