-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
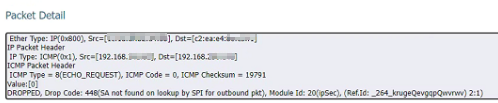
SA not found on lookup by SPI for outbound pkt



Description
The following drop code might be seen if we try to perform the packet capture for the VPN traffic going between two sites through site to site VPN. The most probable cause of this drop is when the local subnet has not been added as a remote network on the remote firewall.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
When we see the mentioned drop for the traffic to any remote subnet connected through the site to site VPN, the firewall will not be able to find an existing tunnel for the Traffic Selectors and will not appear in the currently active VPN tunnels under Network | IPSec VPN | Rules and Settings | Active Tunnels tab.
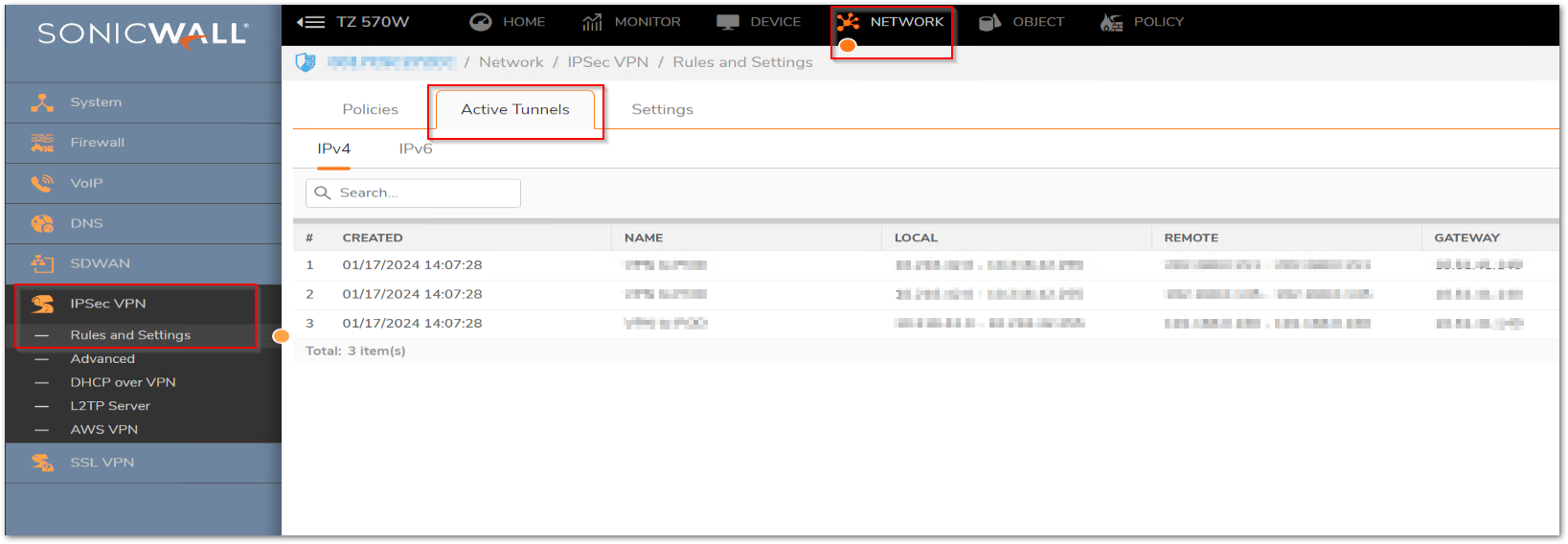
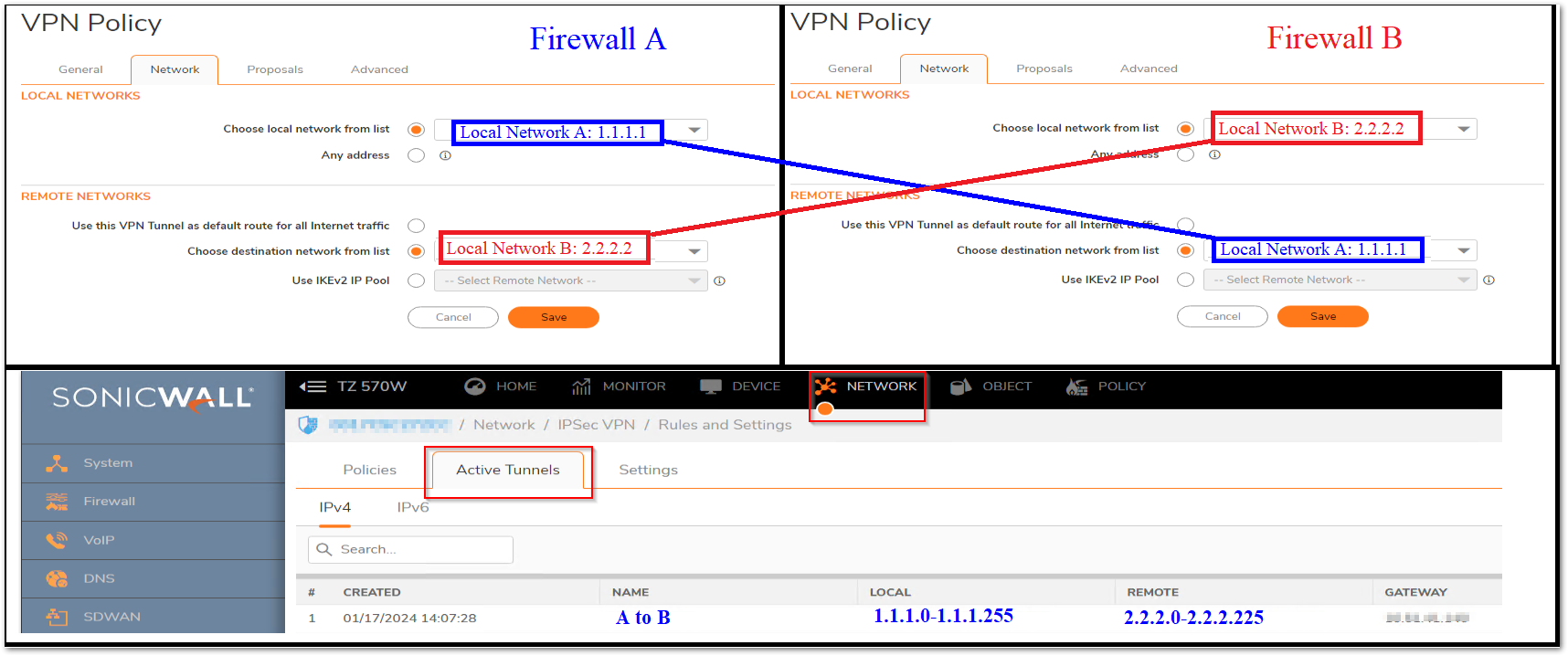
- Navigate to Network | IPSec VPN | Rules and Settings | Policies tab.
- Edit the VPN policy in question and check the Network tab.
- Make sure the networks selected for negotiation are matching on the both sides (Devices) of the tunnel.
 TIP: Any traffic coming from a local subnet, attempting to pass over the tunnel, will be dropped if there is no active VPN tunnel available.
TIP: Any traffic coming from a local subnet, attempting to pass over the tunnel, will be dropped if there is no active VPN tunnel available.
 NOTE: IKE peers agree (traffic selector) to permit traffic through a VPN tunnel once the specified pair of local and remote addresses has been matched. Traffic will be permitted through the associated security association (SA) once it matches a specific traffic selector. See KB 211101021750493 for more details.
NOTE: IKE peers agree (traffic selector) to permit traffic through a VPN tunnel once the specified pair of local and remote addresses has been matched. Traffic will be permitted through the associated security association (SA) once it matches a specific traffic selector. See KB 211101021750493 for more details.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
When we see the mentioned drop for the traffic to any remote subnet connected through the site to site VPN, the firewall will not be able to find an existing tunnel for the Traffic Selectors and will not appear in the currently active VPN tunnels under Manage | VPN | Base Settings tab.
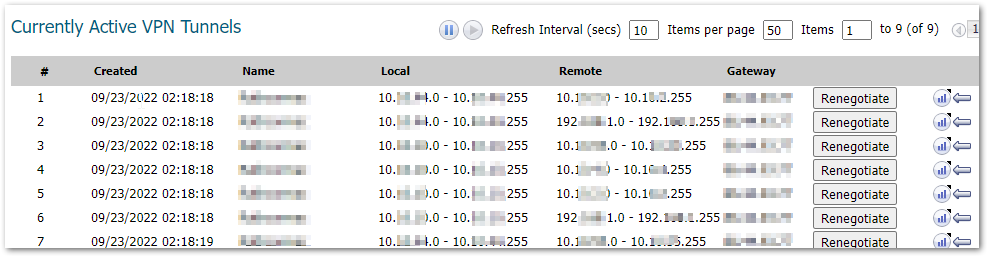
- Navigate to Manage | VPN | Base Settings tab.
- Edit the VPN policy in question and check the Network tab.
- Make sure the networks selected for negotiation are matching on the both sides (Devices) of the tunnel.
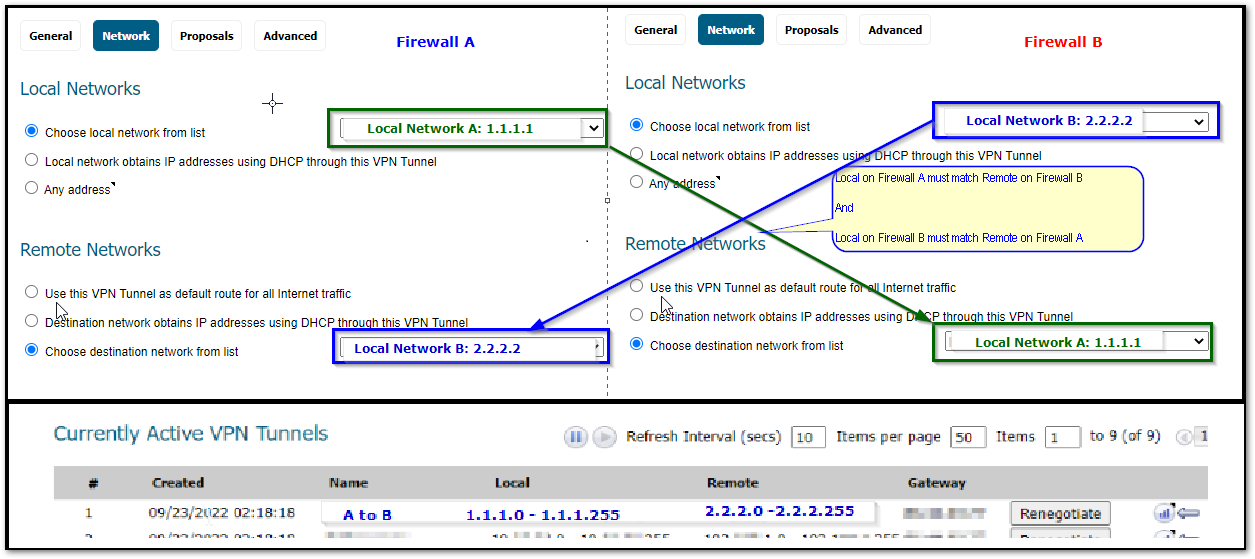
 TIP: Any traffic coming from a local subnet, attempting to pass over the tunnel, will be dropped if there is no active VPN tunnel available.
TIP: Any traffic coming from a local subnet, attempting to pass over the tunnel, will be dropped if there is no active VPN tunnel available.
 NOTE: IKE peers agree (traffic selector) to permit traffic through a VPN tunnel once the specified pair of local and remote addresses has been matched. Traffic will be permitted through the associated security association (SA) once it matches a specific traffic selector. See KB Warning : "Traffic Selectors Unacceptable". for more details.
NOTE: IKE peers agree (traffic selector) to permit traffic through a VPN tunnel once the specified pair of local and remote addresses has been matched. Traffic will be permitted through the associated security association (SA) once it matches a specific traffic selector. See KB Warning : "Traffic Selectors Unacceptable". for more details.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO