-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Provision SonicWall access points on the primary WLAN interface with virtual access points on VLAN



Description
In the article we will explain based on a practical scenario what need to be done to provision (manage) SonicWall access points on a WLAN untagged primary interface using an internal VLAN on the switch to isolate it from the LAN.
We'll setup two SSIDs. One named "First VAP" and the other "Second VAP".
The switch is connected to X7 port on the firewall with 2 virtual interfaces configured.
The SonicWall access points are connected to two different switch ports.
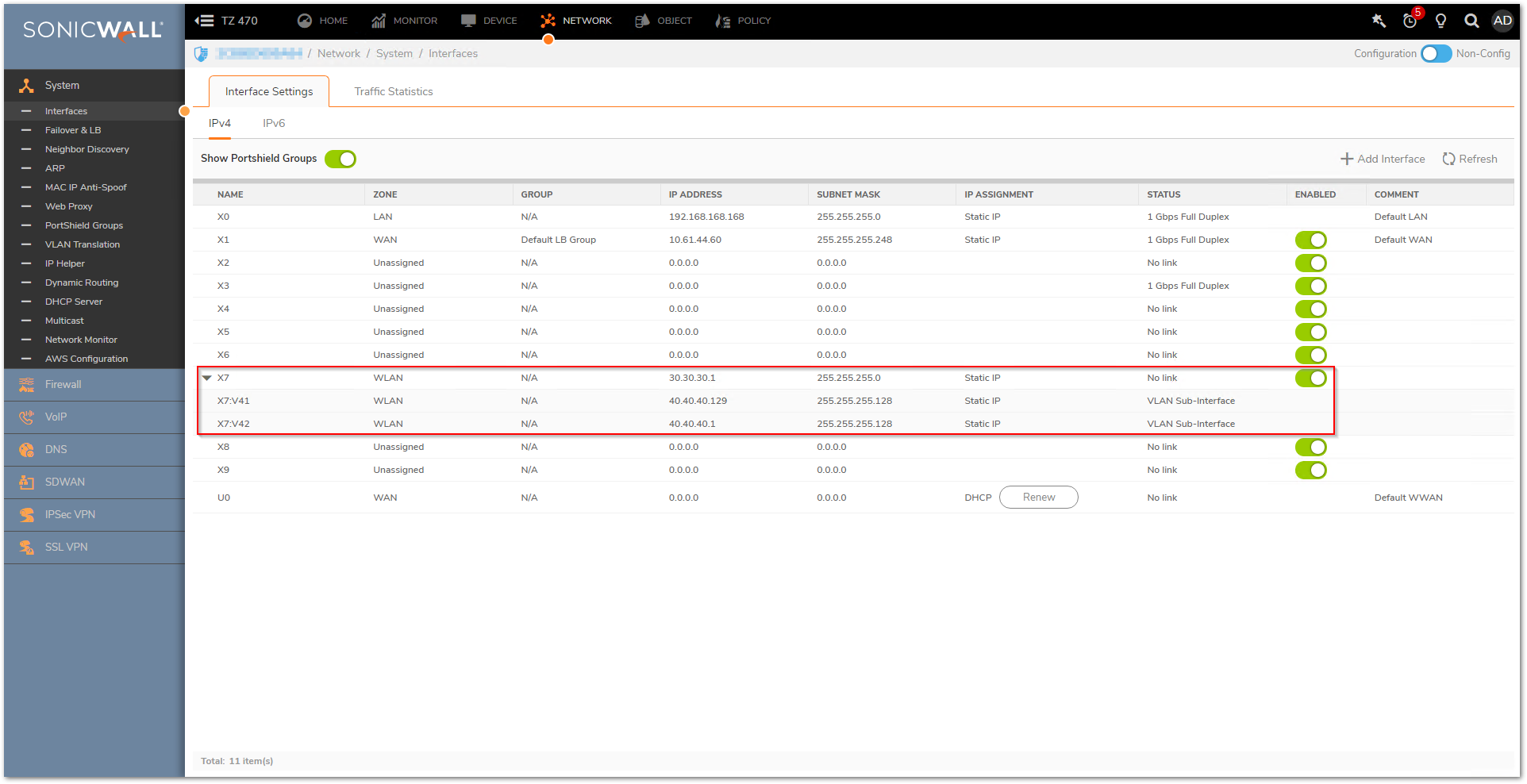
X7: 30.30.30.1/24
X7:V41 40.40.40.129/25
X7:V42 40.40.40.1/25
For the purpose of this tutorial, we will use:
1 x VLAN capable manageable switch
1 x SonicWall Firewall
2 x SonicWall access points (either SonicPoint or SonicWave)
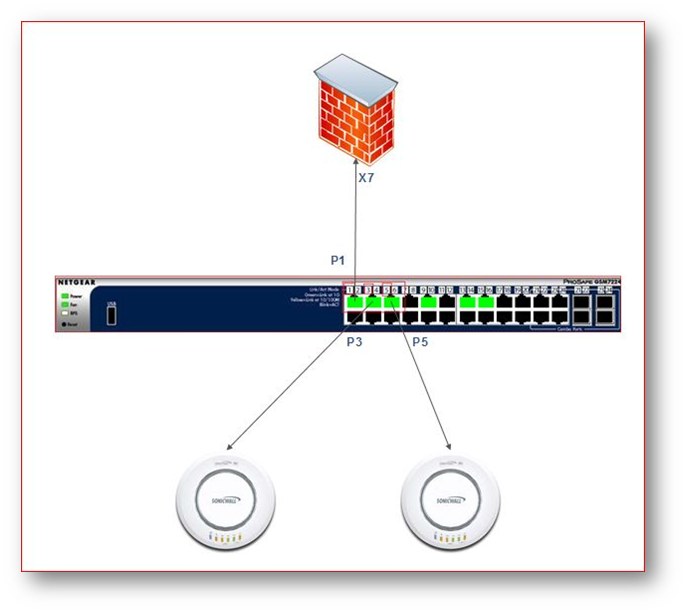
Physical Connectivity
The physical connectivity through the switch is as follows
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Logical Configuration
For the purpose of this tutorial we will create 2 VAPs (SSIDs) on VLANs 41, and 42. The access points themselves will be provisioned (managed) on the the untagged (primary X7 interface). The VAPs will be configured on the VLAN (tagged, trunked) interfaces.
Please see below for the logical configuration of the interfaces:
Zone: WLAN
SonicPoint/SonicWave Limit: Depends on how many access points are being deployed for management.

 NOTE: Choosing the access point limit is only necessary on the WLAN interface which will handle the management.
NOTE: Choosing the access point limit is only necessary on the WLAN interface which will handle the management.
Choosing SonicWall access point limit is NOT necessary on the subnets dedicated for VAPs, in this example X7:V41, X7:V42.
Switch Configuration
For the purpose of the tutorial we will isolate the access point management traffic from the rest of the network connected to the same switch.
For this reason we will use in internal VLAN on the this (VLAN 30), which should be configured in (untagged, native mode) for all switch ports having the WLAN interface and the SonicWall access points. (In this scenario the switch ports will be P1, P3, P5.)
P1 is connected to X5
P3 is connected to the first SP
P5 is connected to the second SP
- Add the necessary VLANs on the switch
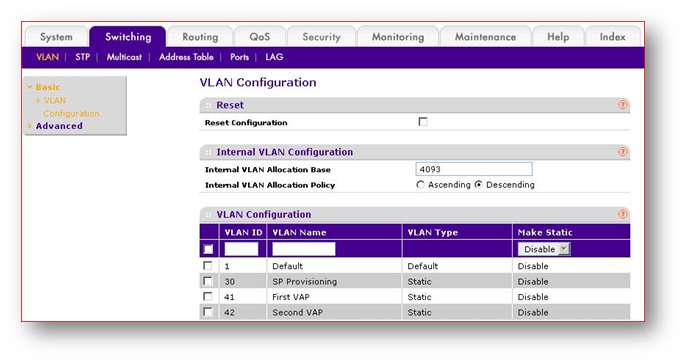
- Assign the Specific VLANs to the switch ports accordingly
Remove the ports P1, P3, P5 from VLAN 1 membership, this will isolate these ports from the LAN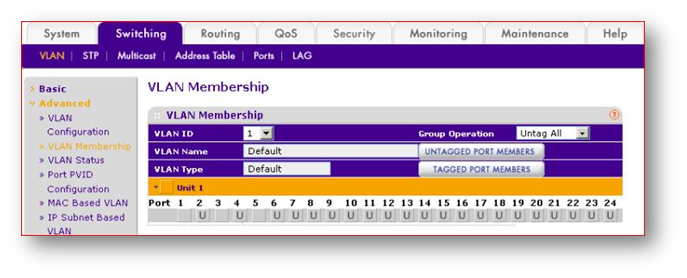
- Change the PVID (native VLAN) of all P1, P3, P5 to 30
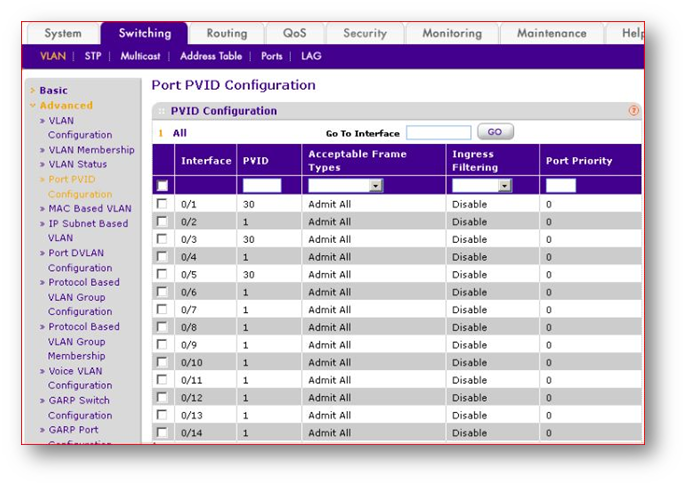
- Make sure VLAN 30 is UNTAGGED on P1, P3, P5, this will ensure the management traffic has no VLANs outside the switch, therefore provisioning the access points on the untagged primary X7 interface.
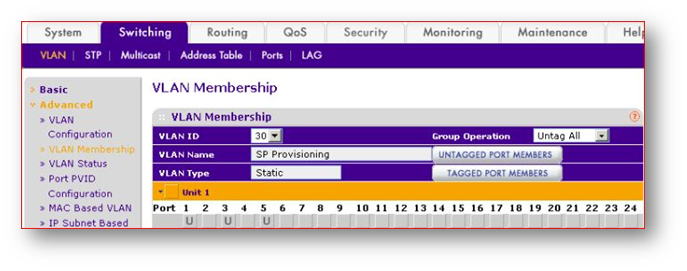
- Make sure VLAN 41 ( First VAP) is TAGGED on P1, P3, P5, this will ensure tagged SSID traffic to the different subnets.
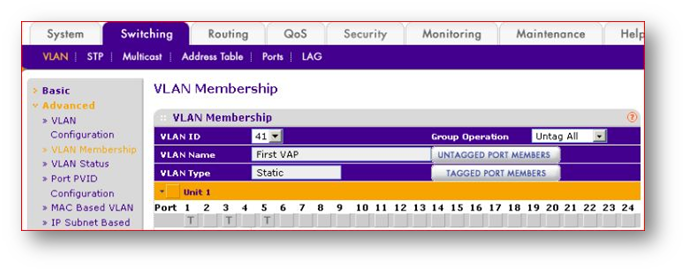
- Make sure VLAN 42 ( First VAP) is TAGGED on P1, P3, P5, this will ensure tagged SSID traffic to the different subnets.
Configure VAPs on the SonicWall
Create 2 VAPs
First VAP - will be dedicated to VLAN 41 - 40.40.40.129/25
Second VAP - will be dedicated to VLAN 42 - 40.40.40.1/25
Create VAP Group (in this scenario Test Group and add these VAPs in that group
 NOTE: You can assign any subnet you would like.
NOTE: You can assign any subnet you would like.
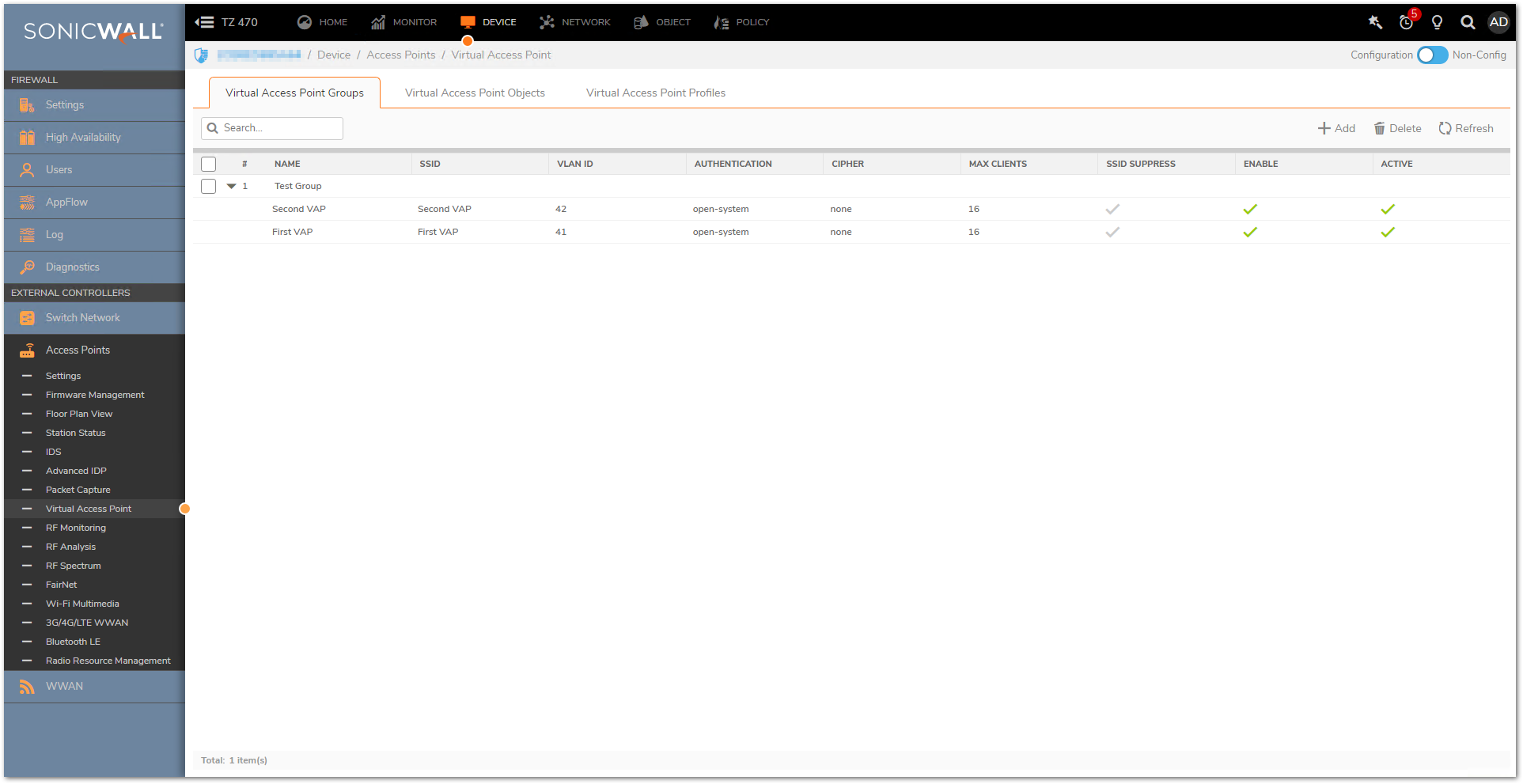
Apply The VAP groups to the SonicWall access points
Navigate to the Device | Access Points | Settings | Access Point Provisioning Profile, and apply Test Group to Profile Settings.
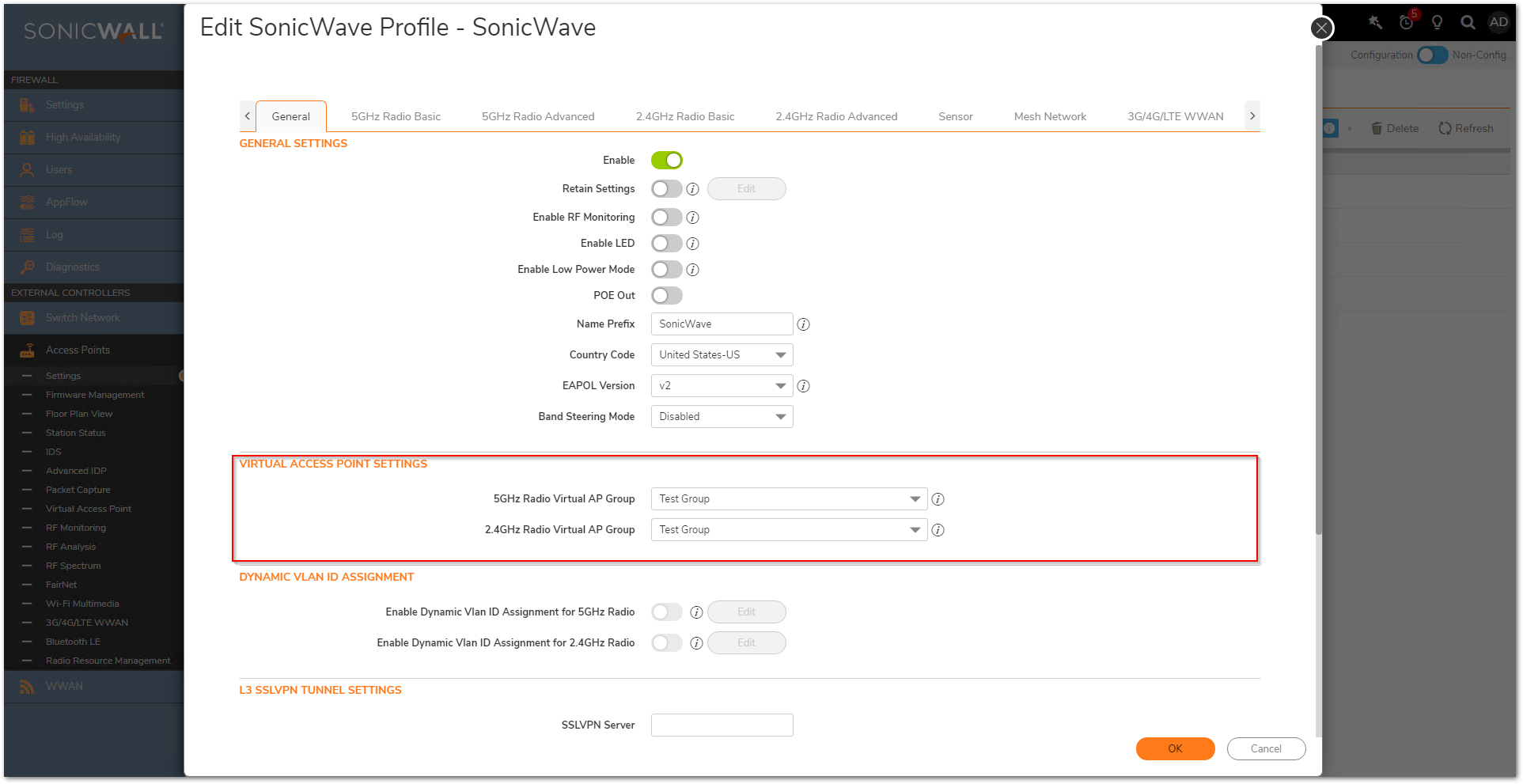
 NOTE: The VAP Group can also be applied to individual Access Points in Device | Access Points | Settings | Access Point Objects page
NOTE: The VAP Group can also be applied to individual Access Points in Device | Access Points | Settings | Access Point Objects page
Confirm clients are able to connect
 NOTE: Please configure DHCP server pool accordingly for X7:V41 and X7:V42 subnets.
NOTE: Please configure DHCP server pool accordingly for X7:V41 and X7:V42 subnets.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Logical Configuration
For the purpose of this tutorial we will create 2 VAPs (SSIDs) on VLANs 41, and 42. The access points themselves will be provisioned (managed) on the the untagged (primary X7 interface). The VAPs will be configured on the VLAN (tagged, trunked) interfaces.
Please see below for the logical configuration of the interfaces:
Zone: WLAN
SonicPoint/SonicWave Limit: Depends on how many access points are being deployed for management.
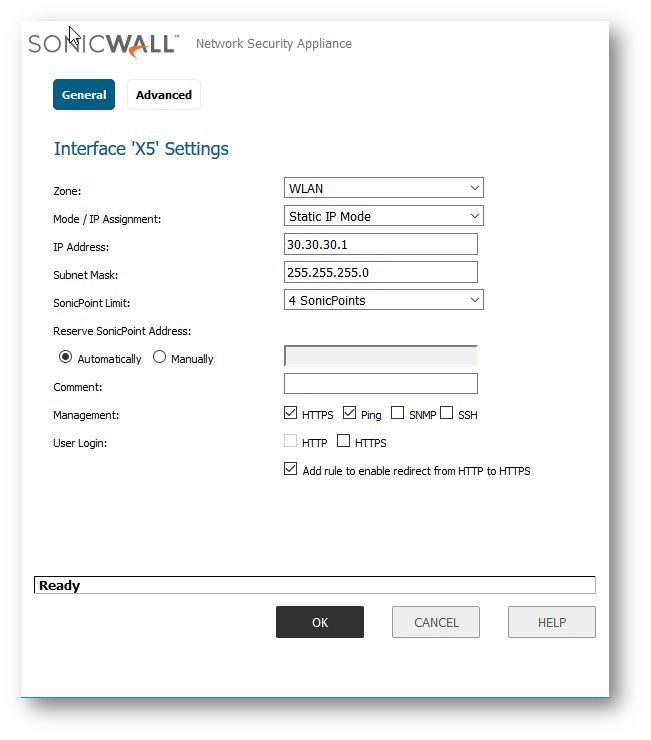
 NOTE: Choosing the access point limit is only necessary on the WLAN interface which will handle the management.Choosing SonicWall access point limit is NOT necessary on the subnets dedicated for VAPs, in this example X7:V41, X7:V42.
NOTE: Choosing the access point limit is only necessary on the WLAN interface which will handle the management.Choosing SonicWall access point limit is NOT necessary on the subnets dedicated for VAPs, in this example X7:V41, X7:V42.
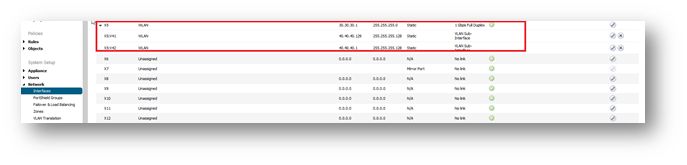
Switch Configuration
For the purpose of the tutorial we will isolate the access point management traffic from the rest of the network connected to the same switch.
For this reason we will use in internal VLAN on the this (VLAN 30), which should be configured in (untagged, native mode) for all switch ports having the WLAN interface and the SonicWall access points. (In this scenario the switch ports will be P1, P3, P5.)
P1 is connected to X5
P3 is connected to the first SP
P5 is connected to the second SP
- Add the necessary VLANs on the switch

- Assign the Specific VLANs to the switch ports accordingly
Remove the ports P1, P3, P5 from VLAN 1 membership, this will isolate these ports from the LAN
- Change the PVID (native VLAN) of all P1, P3, P5 to 30

- Make sure VLAN 30 is UNTAGGED on P1, P3, P5, this will ensure the management traffic has no VLANs outside the switch, therefore provisioning the access points on the untagged primary X7 interface.

- Make sure VLAN 41 ( First VAP) is TAGGED on P1, P3, P5, this will ensure tagged SSID traffic to the different subnets.

- Make sure VLAN 42 ( First VAP) is TAGGED on P1, P3, P5, this will ensure tagged SSID traffic to the different subnets.

Configure VAPs on the SonicWall
Create 2 VAPs
First VAP - will be dedicated to VLAN 41 - 40.40.40.129/25
Second VAP - will be dedicated to VLAN 42 - 40.40.40.1/25
Create VAP Group (in this scenario Test Group and add these VAPs in that group
 NOTE: You can assign any subnet you would like.
NOTE: You can assign any subnet you would like.
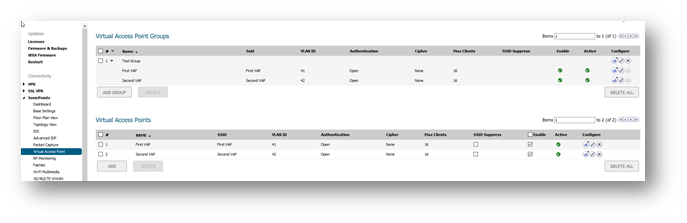
Apply The VAP groups to the SonicWall access points
Navigate to the Manage | SonicPoints | Base Settings | Configure | SonicPoint AC/N Objects, and apply Test Group to Virtual Access Point Settings.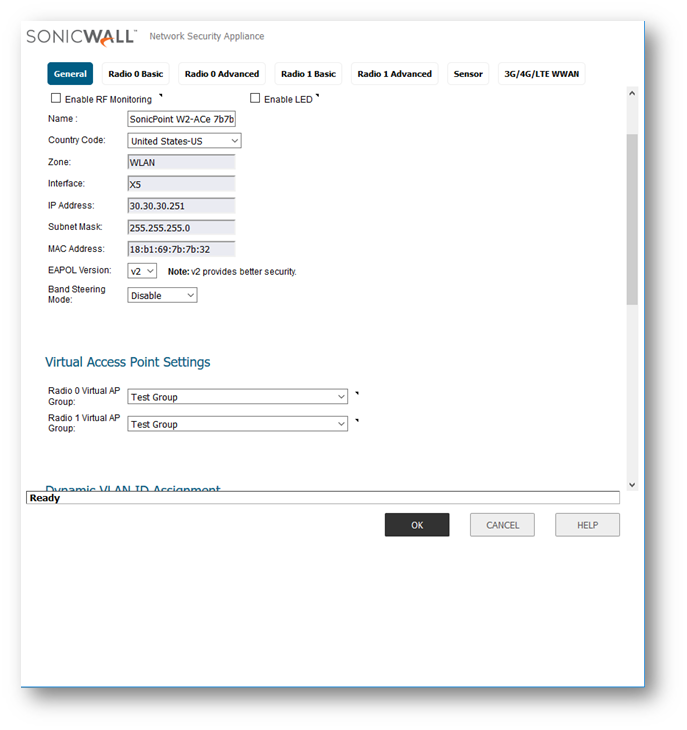
Repeat Step 5 on each SonicPoint/SonicWave.
Confirm clients are able to connect
 NOTE: Please configure DHCP server pool accordingly for X5:V41 and X5:V42 subnets.
NOTE: Please configure DHCP server pool accordingly for X5:V41 and X5:V42 subnets.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Logical Configuration
For the purpose of this tutorial we will create 2 VAPs (SSIDs) on VLANs 41, and 42. The access points themselves will be provisioned (managed) on the the untagged (primary X7 interface). The VAPs will be configured on the VLAN (tagged, trunked) interfaces.
Please see below for the logical configuration of the interfaces:
Zone: WLAN
SonicPoint/SonicWave Limit: Depends on how many access points are being deployed for management.
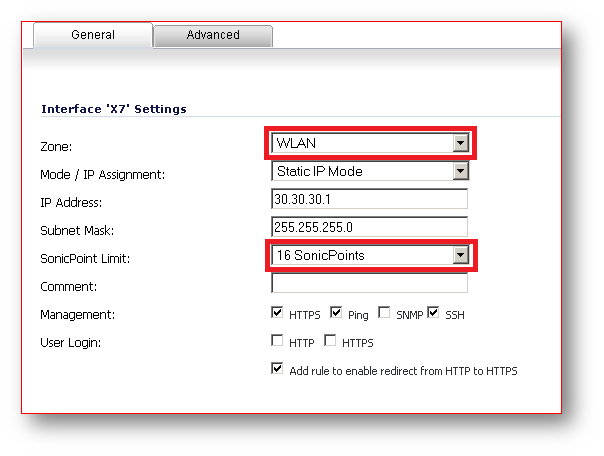
 NOTE: Choosing the access point limit is only necessary on the WLAN interface which will handle the access point management.
NOTE: Choosing the access point limit is only necessary on the WLAN interface which will handle the access point management.
Choosing access point limit is NOT necessary on the subnets dedicated for VAPs, in this example X7:V41, X7:V42.
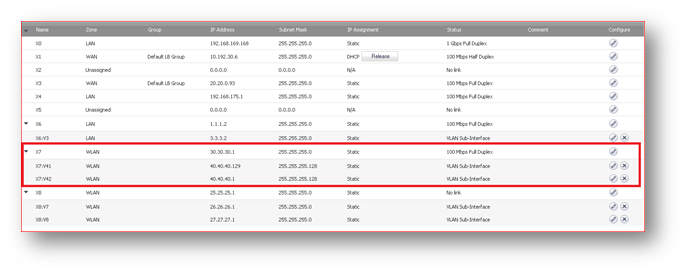
Switch Configuration
For the purpose of the tutorial we will isolate the SonicWall access point management traffic from the rest of the network connected to the same switch.
For this reason we will use in internal VLAN on the this (VLAN 30), which should be configured in (untagged, native mode) for all switch ports having the WLAN interface and the access points. (In this scenario the switch ports will be P1, P3, P5.)
P1 is connected to X7
P3 is connected to the first SP
P5 is connected to the second SP
- Add the necessary VLANs on the switch

- Assign the Specific VLANs to the switch ports accordingly
Remove the ports P1, P3, P5 from VLAN 1 membership, this will isolate these ports from the LAN
- Change the PVID (native VLAN) of all P1, P3, P5 to 30

- Make sure VLAN 30 is UNTAGGED on P1, P3, P5, this will ensure the management traffic has no VLANs outside the switch, therefore provisioning the access points on the untagged primary X7 interface.

- Make sure VLAN 41 ( First VAP) is TAGGED on P1, P3, P5, this will ensure tagged SSID traffic to the different subnets

- Make sure VLAN 42 ( First VAP) is TAGGED on P1, P3, P5, this will ensure tagged SSID traffic to the different subnets

Configure virtual access points (VAPs) on the SonicWall
Create 2 VAPs
First VAP - will be dedicated to VLAN 41 - 40.40.40.129/25
Second VAP - will be dedicated to VLAN 41 - 40.40.40.1/25
Create VAP Group (in this scenario Test Group and add these VAPs in that group.)
 NOTE: You can assign any subnet you would like.
NOTE: You can assign any subnet you would like.
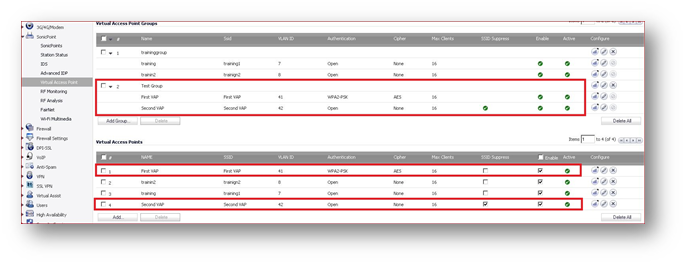
Apply The VAP groups to the SonicWall access points
Navigate to the SonicPoint Configuration | Settings tab | Virtual Access Points Settings, and choose Test Group from the list.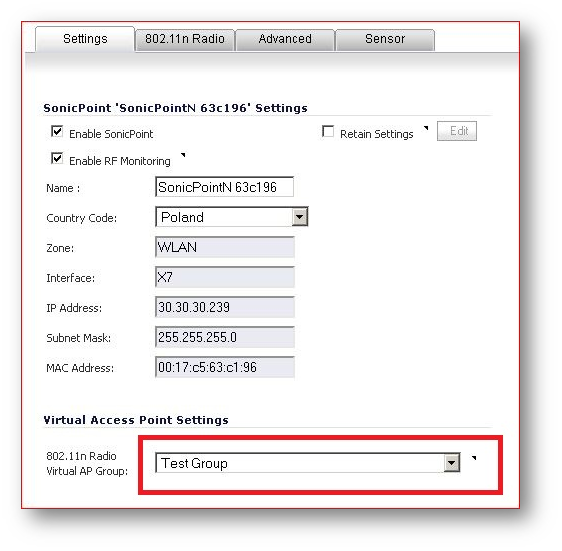
Repeat Step 5 on each access point.
Confirm clients are able to connect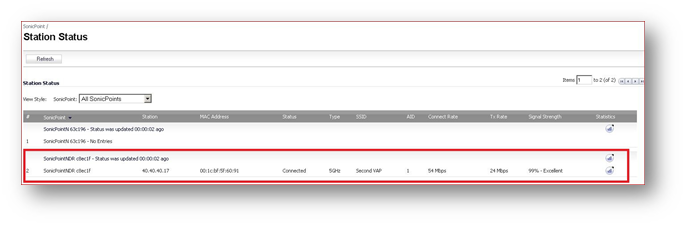
 NOTE: Please configure DHCP server pool accordingly for X7:V41 and X7:V42 subnets
NOTE: Please configure DHCP server pool accordingly for X7:V41 and X7:V42 subnets
Related Articles
- Wireless: SNR, RSSI and Noise basics of wireless troubleshooting
- What happens when a SonicWave's license expires?
- SonicWall deprecates support for WEP and TKIP encryption on SonicOS 8.0.0






 YES
YES NO
NO