-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
No Internet access when connected to Global VPN Client (GVC)



Description
This article explains troubleshooting scenarios where users connected to Global VPN Client can access the VPN networks, but not the Internet.
Cause
This issue could be caused if either of the modes of using GVC; Split Tunnel and Tunnel All (Route All VPN) are not configured correctly.
Split Tunnel: This is the most common deployment. This allows the users to access the VPN resources while using their own local Internet Connection for web traffic.
Tunnel All: In this mode, all web traffic from the user computer is sent across the VPN connection and sent out through the firewall's Internet connection.
There are certain settings required for using either of these modes. If we configure a Tunnel all Mode without giving access to the required networks, the Internet traffic from the client computer will be blocked. Similarly, if split tunnels are not configured as expected, the the firewall might receive traffic that it is not expecting, and drop it.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- The configuration can be changed by navigating to Network | IPSec VPN | Rules and Settings | WAN GroupVPN.
- Under the Advanced tab, ensure that the default gateway is set to 0.0.0.0.
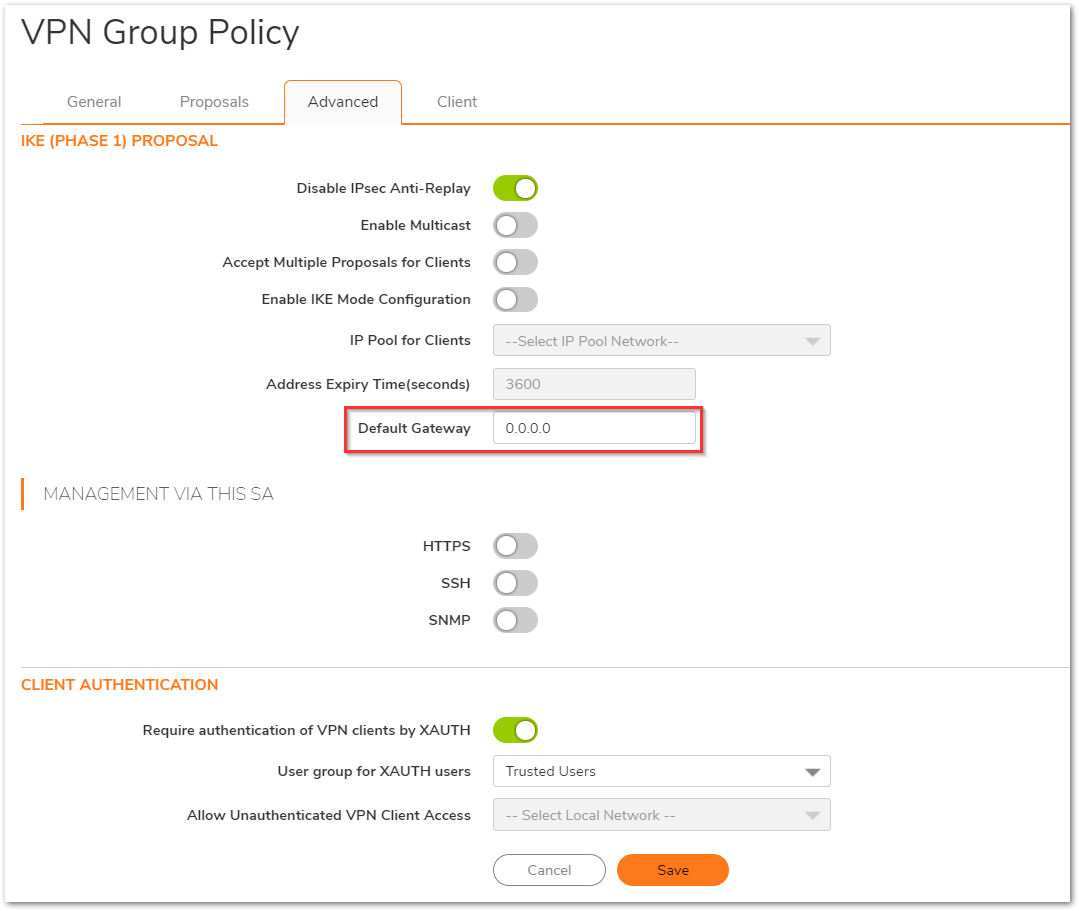
- Under the Client Tab, the Allow Connections to option decides whether you are using Split Tunnels or Tunnel All mode.
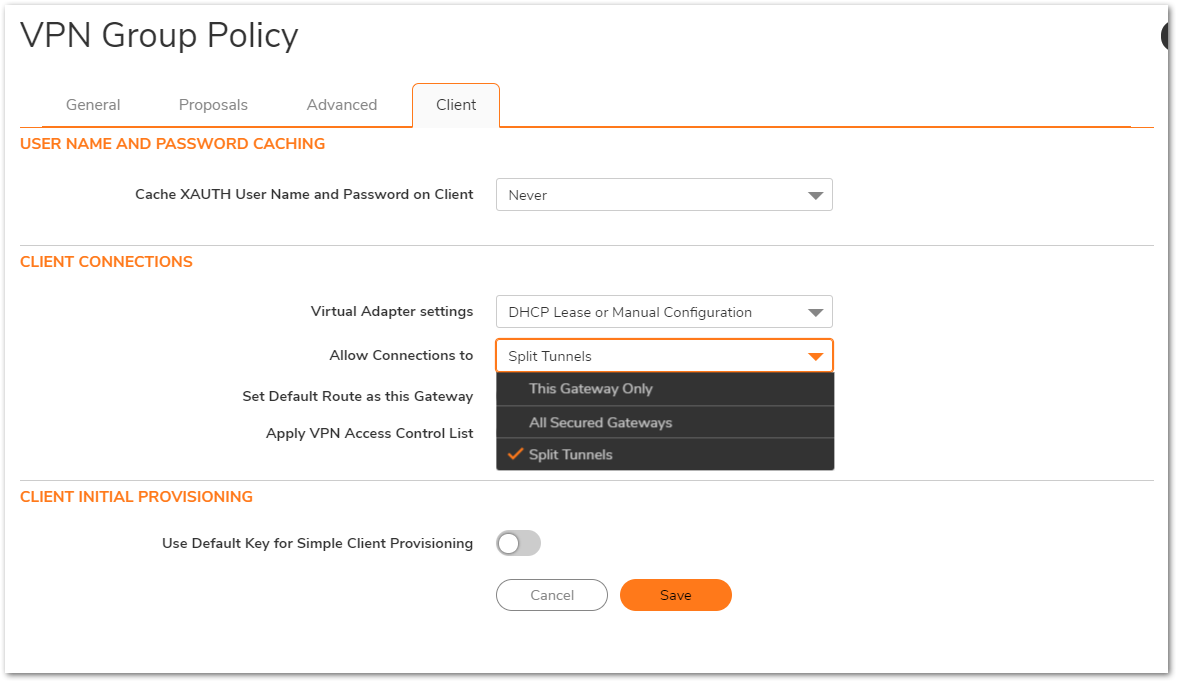
- The following are the settings for each
- For Split Tunnel, the Allow Connections to is set to Split Tunnel and the Set Default Route as this Gateway is unchecked.
- For Tunnel All, the Allow Connections to is set to This Gateway Only and the Set Default Route as this Gateway is checked.
 NOTE: If Tunnel all is configured and the default route checkbox is not checked, the traffic will make it to the firewall from the host computer, but the firewall will drop it.
NOTE: If Tunnel all is configured and the default route checkbox is not checked, the traffic will make it to the firewall from the host computer, but the firewall will drop it.
Another factor that comes into play for Tunnel All mode is the VPN Access option for users. This can be seen under Users | Local Users. Select the specific user and click on the configure option.- Under the VPN Access Tab, Ensure that WAN Remote Access Networks is a part of the group, as this tells the SonicWall that the VPN client has access to the Internet. If this is not added, the traffic will be dropped by the firewall as Packet dropped: Policy Drop.
 TIP: NAT policies also affect how the firewall sends the traffic out in case of a Tunnel All Mode. If the firewall does not have a NAT policy configured for all traffic coming in from the GVC client, it will drop traffic with Packet dropped: Enforced Firewall Rule.
TIP: NAT policies also affect how the firewall sends the traffic out in case of a Tunnel All Mode. If the firewall does not have a NAT policy configured for all traffic coming in from the GVC client, it will drop traffic with Packet dropped: Enforced Firewall Rule.
Navigate to Policy | Rules and Policies | NAT Rules to add the outbound NAT for GVC clients. Considering X1 is the primary WAN connection as well as the WAN you are connecting GVC to, the following NAT can be added.
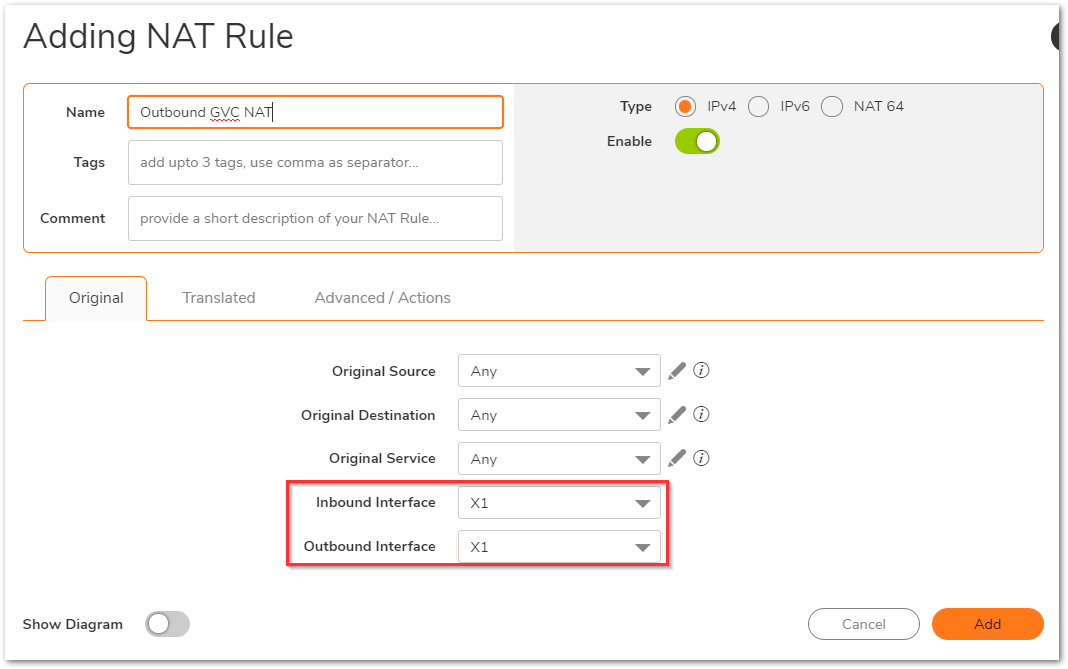
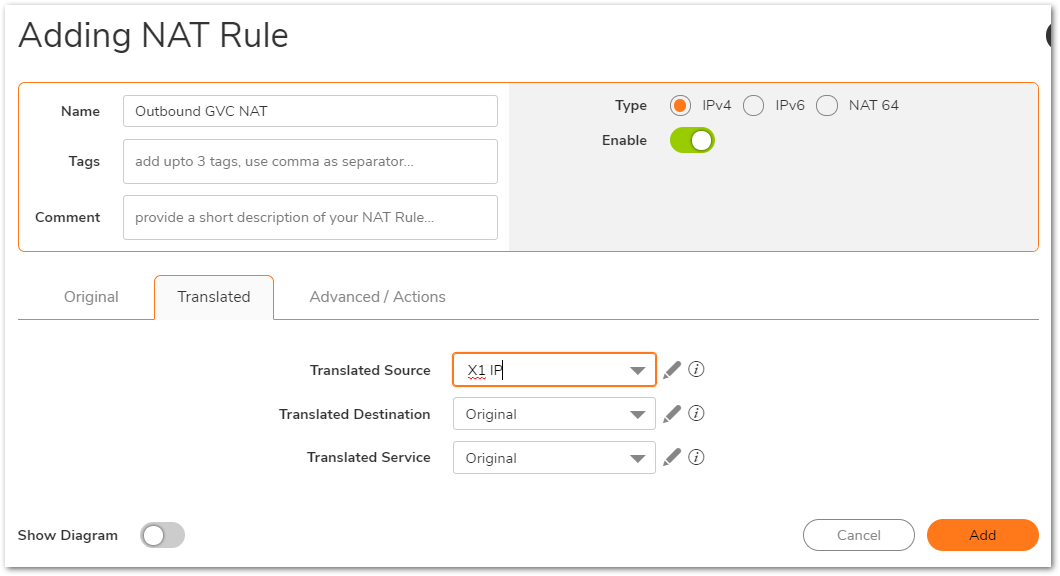
 NOTE: The NAT policy instructs the firewall to translate any traffic going to any destination to be NAT'ed to the WAN IP of the firewall ( In this case, X1 IP). The traffic is controlled by specifying the Inbound and Outbound Interface.
NOTE: The NAT policy instructs the firewall to translate any traffic going to any destination to be NAT'ed to the WAN IP of the firewall ( In this case, X1 IP). The traffic is controlled by specifying the Inbound and Outbound Interface.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- The configuration can be changed by navigating to Manage|VPN|Base Settings|WAN GroupVPN.
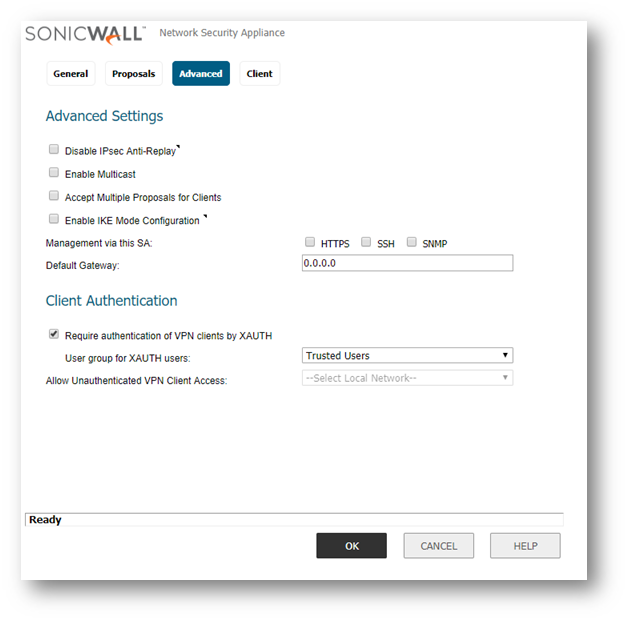
- Under the Advanced tab, ensure that the default gateway is set to 0.0.0.0.
- Under the Clients Tab, the Allow Connections to option decides whether you are using Split Tunnels or Tunnel All mode.
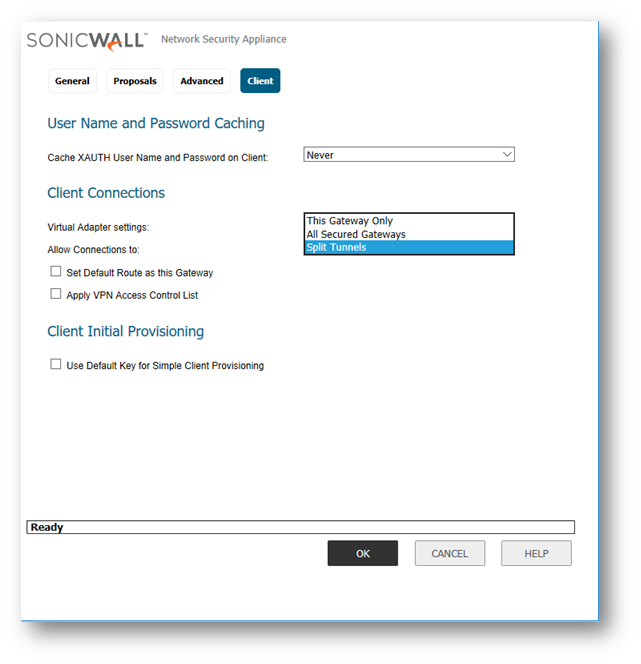
- The following are the settings for each
- For Split Tunnel, the Allow Connections to is set to Split Tunnel and the Set Default Route as this Gateway is unchecked.
- For Tunnel All, the Allow Connections to is set to This Gateway Only and the Set Default Route as this Gateway is checked.
NOTE: If Tunnel all is configured and the default route checkbox is not checked, the traffic will make it to the firewall from the host computer, but the firewall will drop it. - Another factor that comes into play for Tunnel All mode is the VPN Access option for users. This can be seen under Users | Local Users. Select the specific user and click on the configure option.
- Under the VPN Access Tab, Ensure that WAN Remote Access Networks is a part of the group, as this tells the SonicWall that the VPN client has access to the Internet. If this is not added, the traffic will be dropped by the firewall as Packet dropped: Policy Drop.
 TIP:NAT policies also affect how the firewall sends the traffic out in case of a Tunnel All Mode. If the firewall does not have a NAT policy configured for all traffic coming in from the GVC client, it will drop traffic with Packet dropped: Enforced Firewall Rule.
TIP:NAT policies also affect how the firewall sends the traffic out in case of a Tunnel All Mode. If the firewall does not have a NAT policy configured for all traffic coming in from the GVC client, it will drop traffic with Packet dropped: Enforced Firewall Rule.
Navigate to MANAGE | Rules | NAT Policy to add the outbound NAT for GVC clients. Considering X1 is the primary WAN connection as well as the WAN you are connecting GVC to, the following NAT can be added.
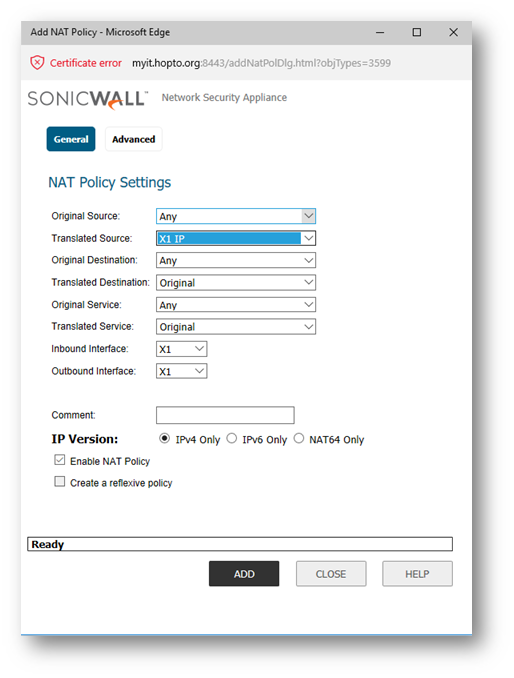
 NOTE: The NAT policy instructs the firewall to translate any traffic going to any destination to be NAT'ed to the WAN IP of the firewall ( In this case, X1 IP). The traffic is controlled by specifying the Inbound and Outbound Interface.
NOTE: The NAT policy instructs the firewall to translate any traffic going to any destination to be NAT'ed to the WAN IP of the firewall ( In this case, X1 IP). The traffic is controlled by specifying the Inbound and Outbound Interface.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series > GVC/L2TP
- Firewalls > SonicWall SuperMassive 9000 Series > GVC/L2TP
- Firewalls > NSa Series > GVC/L2TP
- Firewalls > NSv Series > GVC/L2TP






 YES
YES NO
NO