-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
NetFlow version 9 Configuration Procedures (5.8 onwards)



Description
NetFlow version 9 Configuration Procedures (5.8 onwards)
Resolution
Feature/Application:
The Log > Flow Reporting screen allows you to view statistics based on Flow Reporting and Internal Reporting. From this screen, you can also configure settings for internal and external flow reporting and
external flow reporting.
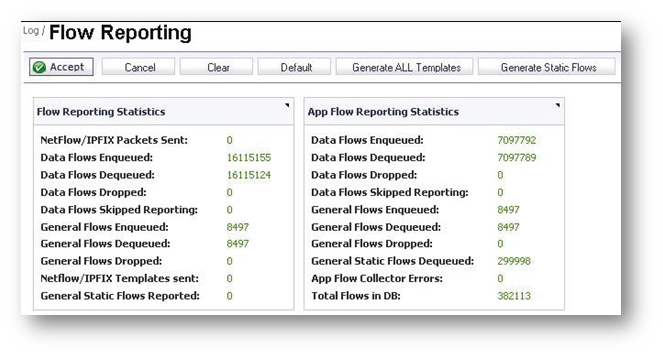
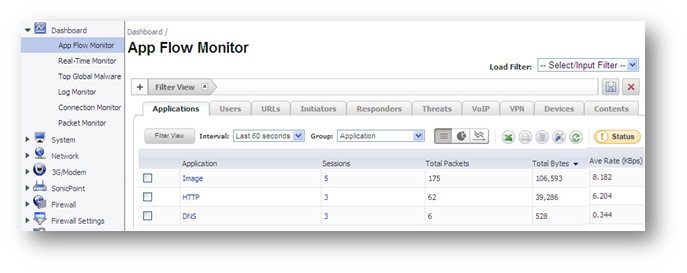
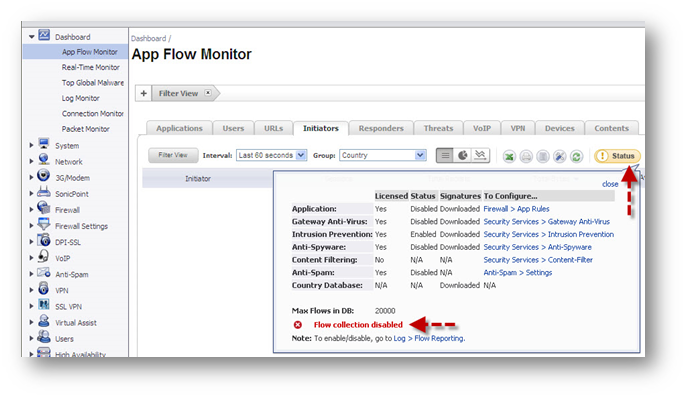
NetFlow version 9 Configuration Procedures
To configure typical Netflow version 9 flow reporting, follow the steps listed below.
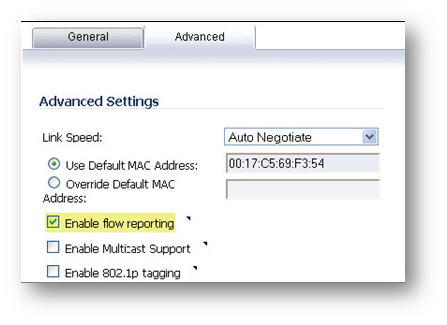
Step 1: Select the checkbox to Enable flow reporting.
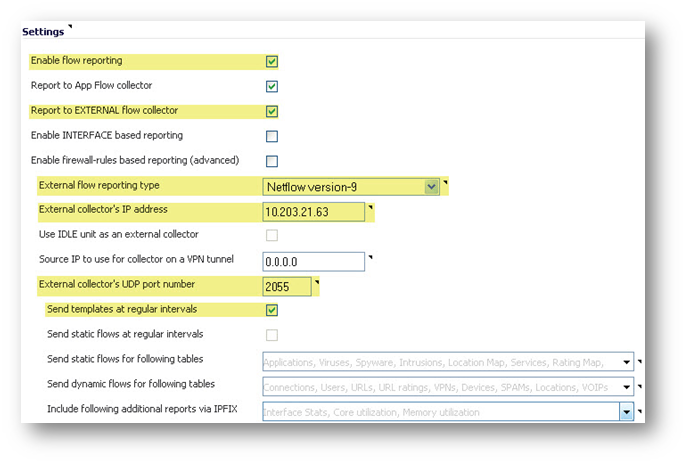
Please Note: that if this option is disabled, both internal and external flow reporting are also disabled.
Step 2: Select the Report to EXTERNAL flow collector checkbox to enable flows to be reported to an external flow collector.
Note that you may enable this option if you prefer to receive external flows, rather than the SonicWall visualization. Remember, not all collectors will work with all modes of flow reporting.
Step 3: Enable INTERFACE based reporting by selecting the checkbox. Once enabled, the flows reported are based on the initiator or responder interface.
Note that this step is optional.
Step 4: Enable Firewall-Rules Based Reporting by selecting the checkbox. Once enabled, the flows reported are based on already existing firewall rules.
Note that this step is optional, but is required if flow reporting is done on selected interfaces.
Step 6: For the Source IP to Use for Collector on a VPN Tunnel, specify the source IP if the external collector must be reached by a VPN tunnel.
Note that this step is optional.
Step 7: Specify the External Collector’s UDP port number in the provided field. The default port is 2055.
Step 8: Enable the option to Send templates at regular intervals by selecting the checkbox. Note that Netflow version-9 uses templates that must be known to an external collector before sending data. After enabling this option, you can Generate ALL Templates by clicking the button in the topmost toolbar.
Note The highlighted fields are the required fields for successful Netflow version 9 configuration. All other configurable fields are optional, as noted in the above steps.
For Realtime or Realtime with bulk, For Periodic, continue to Step 2.
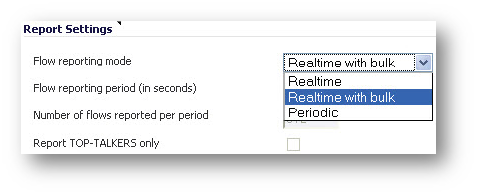
Step 4 Select the Report TOP-TALKERS only checkbox to enable the SonicWall appliance to report flows with the maximum amount of traffic.
After configuring the Report Settings, continue through this section to configure the conditions under which a flow is reported. Selecting a checkbox will enable the configuration.
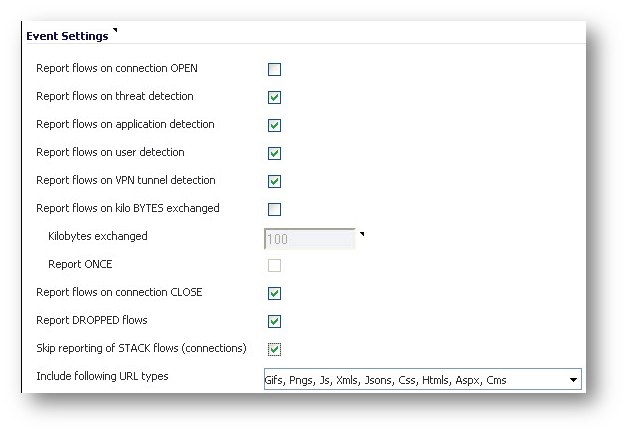
Note: This option is applies to both App Flow (internal) and external reporting when used with IPFIX with extensions.
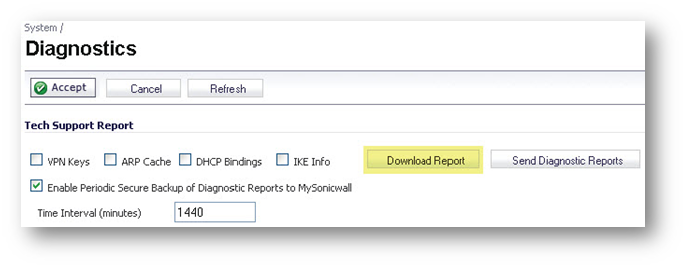
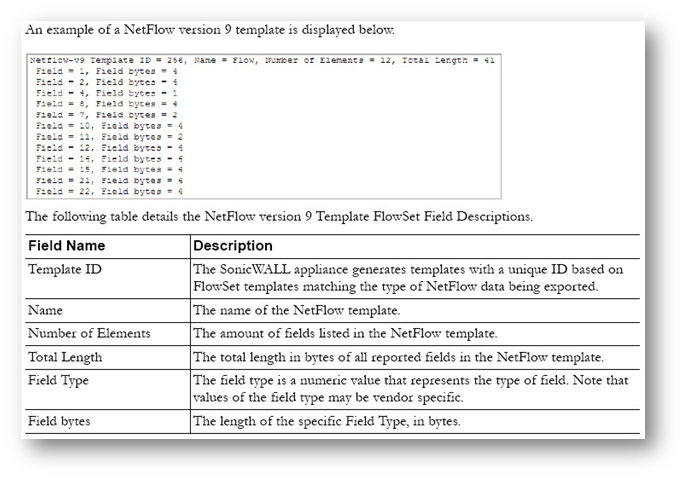
The following section shows examples of the type of Netflow template tables that are exported. You can perform a Diagnostic Report of your own Netflow Configuration by navigating to the System > Diagnostics screen, and click the Download Report button in the “Tech Support Report” section.
NetFlow Version 9
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO