-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Navigating the VOIP Settings



Description
This KB provides instructions on how to configure VOIP on SonicOS 7.X
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Configure VoIP through NETWORK | VoIP | Settings.
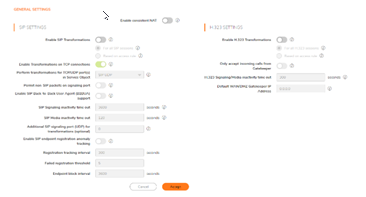
General Settings
There is one option under General Settings: Enable Consistent NAT.
Consistent NAT enhances standard NAT policy to provide greater compatibility with peer-to-peer applications that require a consistent IP address to connect to, such as VoIP. Consistent NAT uses an MD5 hashing method to consistently assign the same mapped public IP address and UDP Port pair to each internal private IP address and port pair.
For example, NAT could translate the private (LAN) IP address and port pairs, 192.116.168.10/50650 and 192.116.168.20/50655 into public (WAN) IP/port pairs, as shown in IP address and port pairs.

With Consistent NAT enabled, all subsequent requests from either host 192.116.168.10 or 192.116.168.20 using the same ports illustrated in IP address and port pairs result in using the same translated address and port pairs. Without Consistent NAT, the port and possibly the IP address change with every request.
Enabling Consistent NAT causes a slight decrease in overall security, because of the increased predictability of the address and port pairs. Most UDP-based applications are compatible with traditional NAT. Therefore, do not enable Consistent NAT unless your network uses applications that require it.
For Consistent NAT to work properly, the minimum time interval between calls must be at least 200 msec.
Enabling Consistent NAT
To enable consistent NAT
- Select the Enable Consistent NAT option. This option is not selected by default.
- Click Accept.
SIP Settings
By default, SIP clients use their private IP address in the SIP (Session Initiation Protocol) Session Definition Protocol (SDP) messages that are sent to the SIP proxy. If your SIP proxy is located on the public (WAN) side of the firewall and the SIP clients are located on the private (LAN) side of the firewall, the SDP messages are not translated and the SIP proxy cannot reach the SIP clients.
To enable SIP
- Navigate to NETWORK | VOIP > Settings.
In the SIP Settings section, choose whether to enable SIP transformation globally or by firewall rule:
- Use global control to enable SIP Transformations. This option is selected by default.
- Use firewall Rule-based control to enable SIP Transformations. Be sure to configure a firewall rule to control SIP transformations as described in SonicOS/X Policies.
- Use global control to enable SIP Transformations. This option is selected by default.
- If you are not configuring SIP transformations, go to Step 12.
Enable SIP Transformations is not selected by default. Select this option to:
-
Transform SIP messages between LAN (trusted) and WAN/DMZ (untrusted).
You need to check this setting when you want the Security Appliance to do the SIP transformation. If your SIP proxy is located on the public (WAN) side of the Security Appliance and SIP clients are on the LAN side, the SIP clients by default embed/use their private IP address in the SIP/Session Definition Protocol (SDP) messages that are sent to the SIP proxy; hence, these messages are not changed and the SIP proxy does not know how to get back to the client behind the Security Appliance.
- Enable the Security Appliance to go through each SIP message and change the private IP address and assigned port.
- Control and open up the RTP/RTCP ports that need to be opened for SIP session calls to happen.
-
NAT translates Layer 3 addresses, but not Layer 7 SIP/SDP addresses, which is why you need to select Enable SIP Transformations to transform the SIP messages.
In general, you should select Enable SIP Transformations unless there is another NAT traversal solution that requires this feature to be turned off. SIP Transformations works in bi-directional mode, meaning messages are transformed going from LAN to WAN and vice versa.
When Enable SIP Transformations is selected, the other options become available.
- To perform SIP transformations on TCP-based SIP sessions, select Enable SIP Transformation on TCP connections. This option is selected by default.
- Select a Service Object from Perform transformations to TCP/UDP port(s) in Service Object. The default is SIP.
Selecting Permit non-SIP packets on signaling port enables applications such as Apple iChat and MSN Messenger, which use the SIP signaling port for additional proprietary messages. This option is not selected by default.
Enabling this checkbox might open your network to malicious attacks caused by malformed or invalid SIP traffic.
If the SIP Proxy Server is being used as a B2BUA, enable the Enable SIP Back-to-Back User Agent (B2BUA) support setting. This option is disabled by default and should be enabled only when the Security Appliance can see both legs of a voice call (for example, when a phone on the LAN calls another phone on the LAN).
If there is no possibility of the firewall seeing both legs of voice calls (for example, when calls are only made to and received from phones on the WAN), the Enable SIP Back-to-Back User Agent (B2BUA) support setting should be disabled to avoid unnecessary CPU usage.
Use the SIP Signaling inactivity time out (seconds) and SIP Media inactivity time out (seconds) options to define the amount of time a call can be idle (no traffic exchanged) before the firewall blocks further traffic. A call goes idle when placed on hold. Specify the maximum idle time when:
- There is no signaling (control) message being exchanged in SIP Signaling inactivity time out. The minimum time is 30 seconds, the maximum time is 1000000 seconds (~1.2 days) and the default is 3600 seconds (60 minutes).
- No media (for example, audio or video) packets are being exchanged in the SIP Media inactivity time out. The minimum time is 30 seconds, the maximum time is 3600 seconds (1 hour), and the default time is 120 seconds (2 minutes).
Use the Additional SIP signaling port (UDP) for transformations setting to specify a non-standard UDP port to carry SIP signaling traffic. Normally, SIP signaling traffic is carried on UDP port 5060. However, a number of commercial VOIP services use different ports, such as 1560. When this setting is non zero (0 is the default; the maximum value is 65535), the Security Appliance performs SIP transformation on these non-standard ports.
Vonage’s VoIP service uses UDP port 5061.
To track SIP endpoint registration anomalies, select the Enable SIP endpoint registration anomaly tracking option. This option is not selected by default. When it is selected, these options become available:
- Registration tracking interval (seconds) – Specify the interval between checking for anomalies. The default is 300 seconds (5 minutes).
- Failed registration threshold – Specify the number of failed registrations before checking for anomalies. The default is 5 failures.
- Endpoint block interval (seconds) – The default is 3600 (60 minutes).
- Registration tracking interval (seconds) – Specify the interval between checking for anomalies. The default is 300 seconds (5 minutes).
Either:
- Click Accept.
- Go to H.323 Settings.
H.323 Settings.
To configure H.323 settings
- Navigate to NETWORK | VoIP > Settings | H.323 Settings.
Choose whether to enable H.323 transformation globally or by firewall rule:
- Use global control to enable H.323 Transformations. This option is selected by default.
- Use firewall Rule-based control to enable H.323 Transformations. Be sure to configure a firewall rule to control H.323 transformations.
- Use global control to enable H.323 Transformations. This option is selected by default.
- If you are not configuring H.323 transformations, go to Step 5.
Select Enable H.323 Transformation to allow stateful H.323 protocol-aware packet content inspection and modification by the firewall. This option is disabled by default. When the option is selected, the other H.323 options become active.
The firewall performs any dynamic IP address and transport port mapping within the H.323 packets, which is necessary for communication between H.323 parties in trusted and untrusted networks/zones.
Disable the Enable H.323 Transformation to bypass the H.323 specific processing performed by the firewall.
- Select Only accept incoming calls from Gatekeeper to ensure all incoming calls go through the Gatekeeper for authentication. The Gatekeeper refuses calls that fail authentication.
- In the H.323 Signaling/Media inactivity time out (seconds) field, specify the amount of time a call can be idle before the firewall blocks further traffic. A call goes idle when placed on hold. The default time is 300 seconds (5 minutes), the minimum time is 60 seconds (1 minute), and the maximum time is 122400 seconds (34 hours).
- The Default WAN/DMZ Gatekeeper IP Address field has a default value of
0.0.0.0.Enter the default H.323 Gatekeeper IP address in this field to allow LAN-based H.323 devices to discover the Gatekeeper using the multicast address225.0.1.41. If you do not enter an IP address, multicast discovery messages from LAN-based H.323 devices go through the configured multicast handling. - Click Accept.
Configuring VOIP Access Rules
By default, stateful packet inspection on the firewall allows all communication from the LAN to the Internet and blocks all traffic to the LAN from the Internet. Additional network access rules can be defined to extend or override the default access rules.
If you are defining VoIP access for client to use a VoIP service provider from the WAN, you configure network access rules between source and destination interface or zones to enable clients behind the firewall to send and receive VoIP calls.
Note: Although custom rules can be created that allow inbound IP traffic, the firewall does not disable protection from Denial of Service attacks, such as the SYN Flood and Ping of Death attacks.
Note: You must select Bandwidth Management on NETWORK | System > Interfaces for the WAN interface before you can configure bandwidth management for network access rules.
Call Status
The NETWORK | VoIP > Call Status page allows you to monitor all currently active VoIP calls. Use the Search feature to locate specific entries.
The VoIP Call Status table displays the following information about the active VoIP connection:
- Caller IP – the IP address of the device from which the call was initiated
- Caller-ID – the unique identifier for each initiated call
- Called IP – the IP address of the device on which the call was received
- Called-ID – the unique identifier for each received call
- Protocol – the type of protocol used by the call
- Bandwidth – the amount of bandwidth in megabits per second (Mbps) used by the call
- Time Started – the date and time that the call began
You can see the caller and called information as well as how long the call has been in progress and the bandwidth used. Both active H.323 and SIP calls are shown on the VoIP Call Status page.
H.323 Transformations and SIP Transformations must be enabled on the NETWORK | VoIP > Settings page for the corresponding calls to be shown. Only when these options are enabled does SonicOS/X inspect the VoIP payload to track call progress.
To reset the connections for all the active calls in progress, click FLUSH ALL. This also removes all VoIP call entries from the table.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO