-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
LDAP Integration in SonicOS 6.5 and above



Description
This article will go through LDAP integration in SonicOS 6.5 and along with an example when LDAP client authentication fails.
- LDAP integration in SonicOS 6.5 and Gen7
- LDAP Client Authentication Failed.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Click DEVICE in the top navigation menu.
- Navigate to Users | Settings | Authentication and select LDAP + Local Users and click Configure LDAP.
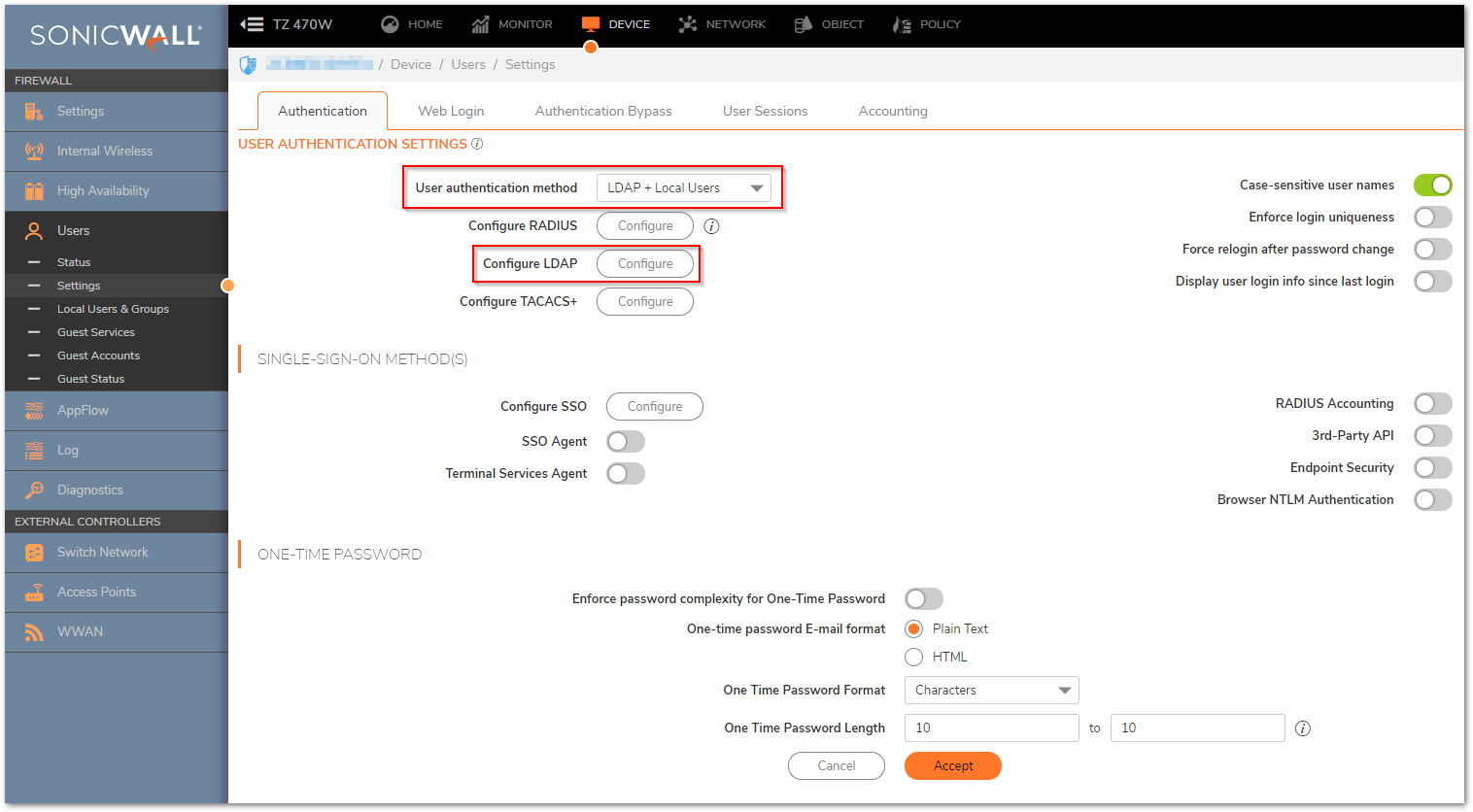
 TIP: If you are connected to your SonicWall appliance via HTTP rather than HTTPS, you will see a dialog box warning you of the sensitive nature of the information stored in directory services and offering to change your connection to HTTPS. If you have HTTPS management enabled for the interface to which you are connected (recommended), check the “Do not show this message again” box and click Yes.
TIP: If you are connected to your SonicWall appliance via HTTP rather than HTTPS, you will see a dialog box warning you of the sensitive nature of the information stored in directory services and offering to change your connection to HTTPS. If you have HTTPS management enabled for the interface to which you are connected (recommended), check the “Do not show this message again” box and click Yes. NOTE: SonicOS 6.5 and above introduces support for user authentication partitioning and multiple LDAP Servers. Multiple LDAP Servers are supported on all platforms.For more information about User Authentication Partitioning and multiple LDAP Servers click Authentication Partitioning and Multiple LDAP Servers.
NOTE: SonicOS 6.5 and above introduces support for user authentication partitioning and multiple LDAP Servers. Multiple LDAP Servers are supported on all platforms.For more information about User Authentication Partitioning and multiple LDAP Servers click Authentication Partitioning and Multiple LDAP Servers. - On the Settings page, click Configure tab next to Configure LDAP and click Add Server to enter the server configuration .
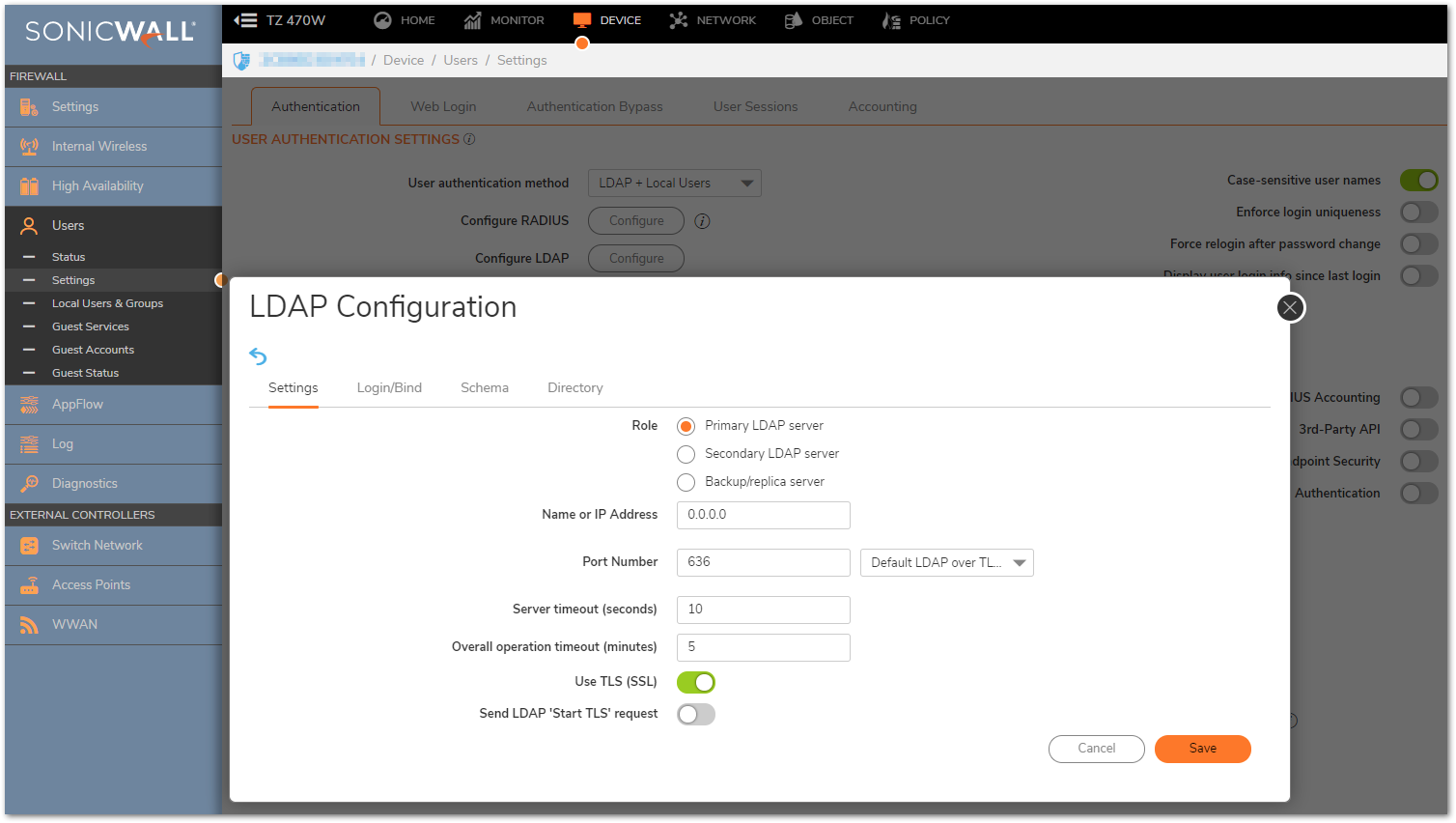
- Name or IP address: The FQDN or the IP address of the LDAP server against which you wish to authenticate. If using a name, be certain that it can be resolved by your DNS server. IP address
of the LDAP server . - Port Number: The default LDAP over TLS port number is TCP 636. The default LDAP (unencrypted) port number is TCP 389. If you are using a custom listening port on your LDAP server, specify it here.
- Server timeout (seconds): The amount of time, in seconds, that the SonicWall will wait for a response from the LDAP server before timing out. Allowable ranges are 1 to 99999, with a default of 10 seconds. Overall operation timeout (minutes): 5(Default).
- Use TL(SSL) : Use Transport Layer Security (SSL) to log in to the LDAP server.
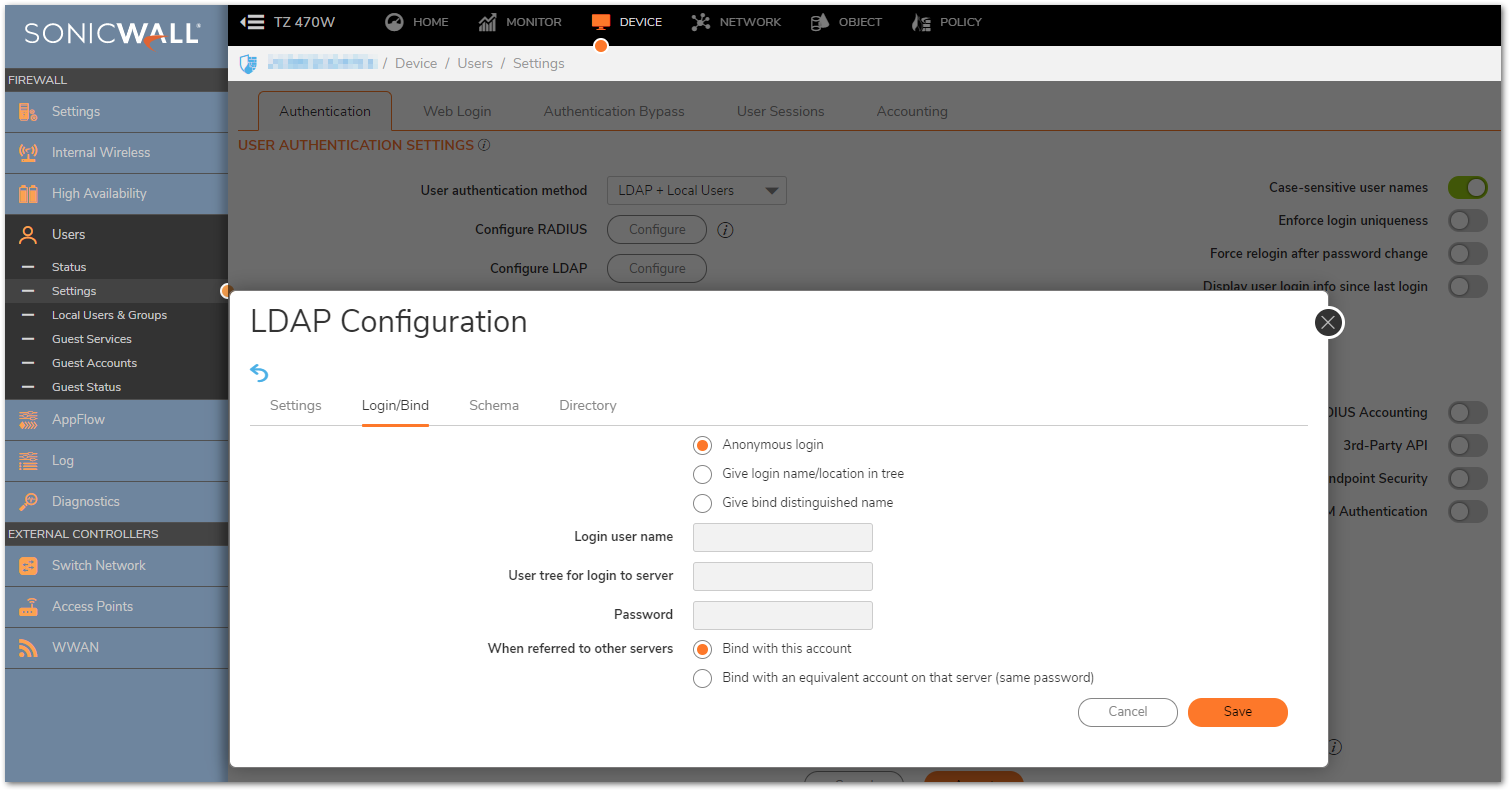
- Anonymous Login – Some LDAP servers allow for the tree to be accessed anonymously. If your server supports this (Active Directory generally does not), then you may select this option.
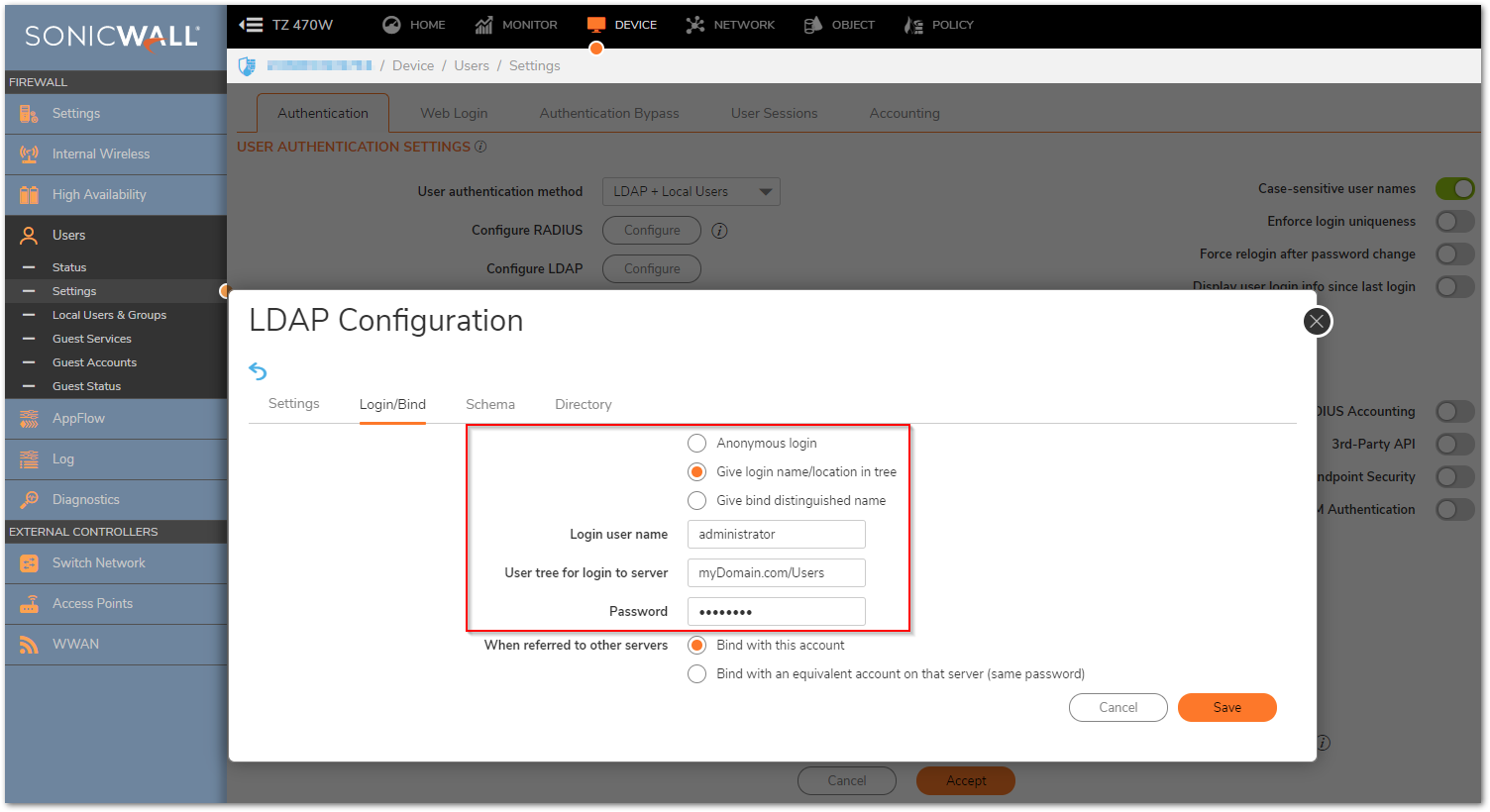
- Login User Name – Specify a user name that has rights to log in to the LDAP directory. The login name will automatically be presented to the LDAP server in full ‘dn’ notation. This can be any account with LDAP read privileges (essentially any user account) – Domain Administrative privileges are not required but preferred if encounter any priviledge issues. Note that this is the user’s display name, not their login ID.
- Click Schema tab and configure the following fields.
- LDAP Schema: Microsoft Active Directory.
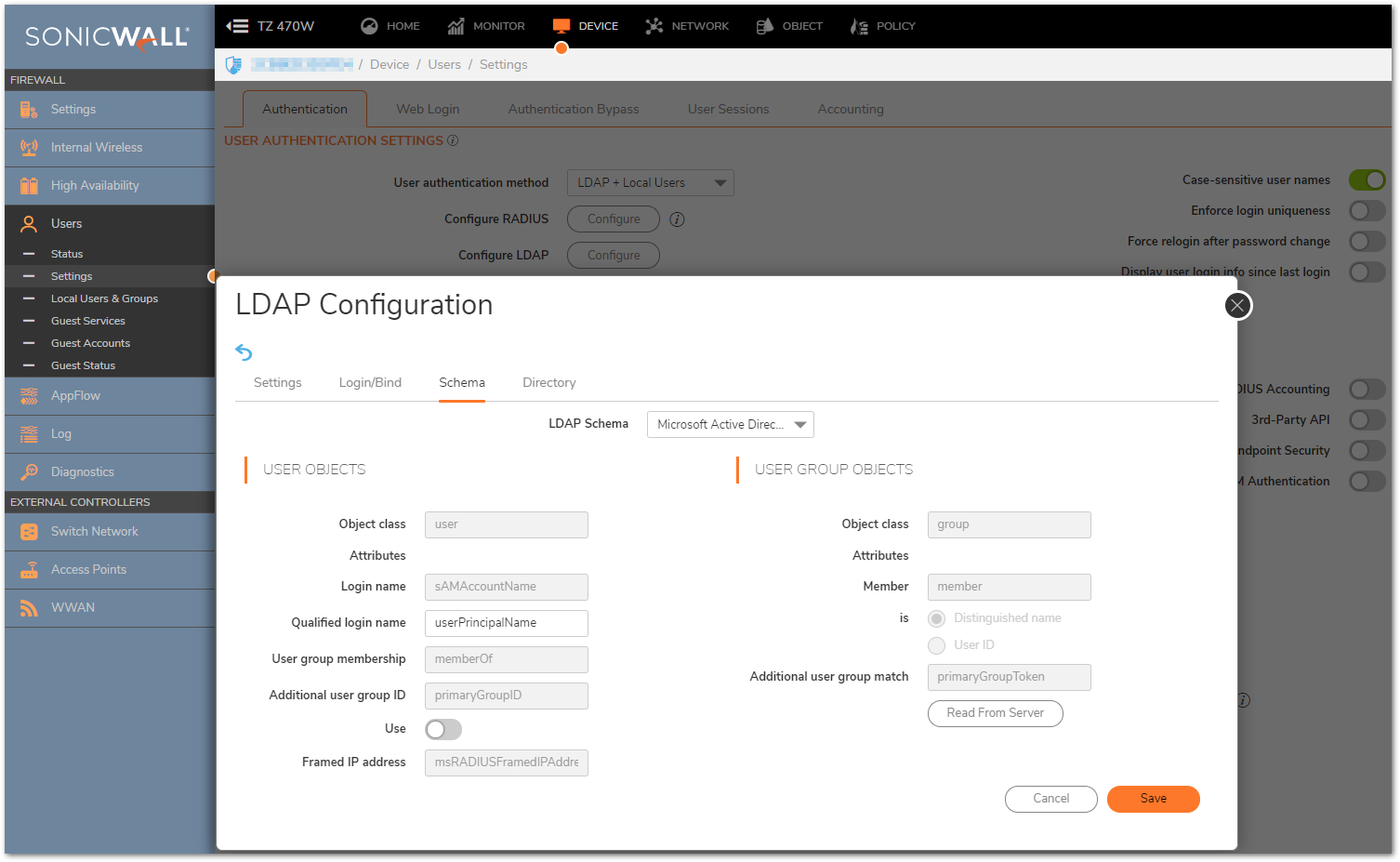
- Click Directory tab and configure the following fields:This will populate the Trees containing users and Trees containing user groups fields by scanning through the directories in search of all trees that contain user objects.
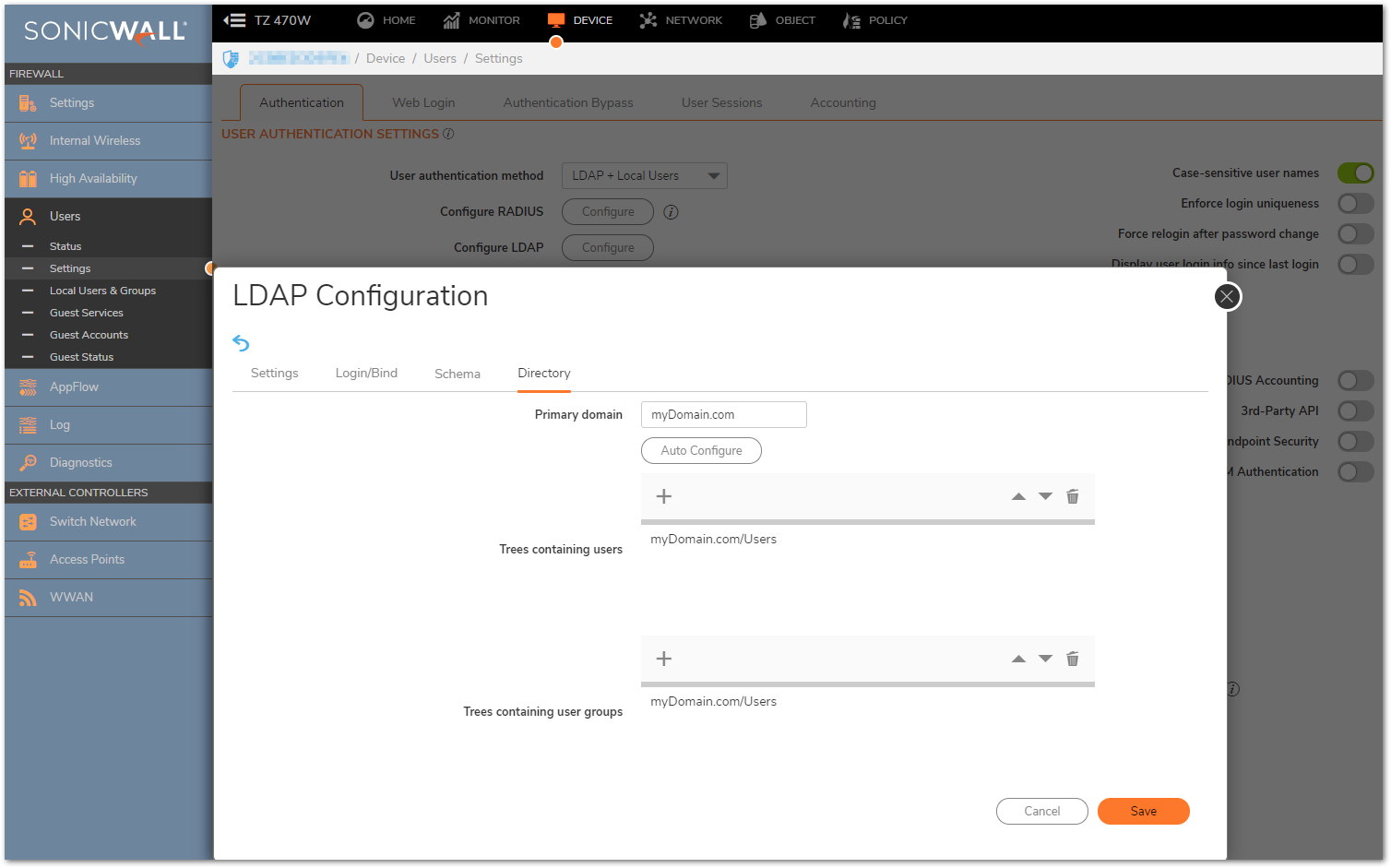
LDAP Authentication Failed
Overview of LDAP Authentication process
- The SonicWall establishes a TCP connection with the LDAP server on port 389 (or 636 if using TLS).
- The SonicWall binds to the LDAP server, authenticating itself using the DN (Distinguished Name) format of the Login user name (Settings tab) + User tree for login to server (Directory tab). In this example, the name in the LDAP bindRequest is cn=Administrator,cn=Users,dc=mydomain,dc=com.
- If the bindResponse from the LDAP server is 'success', then the SonicWall queries the Trees containing users (Directory tab) using the client's username as a filter. In this example, the client is trying to authenticate as oprime, so the SonicWall will query the baseObject "cn=Users,dc=mydomain,dc=com" using the filtersAMAccountName=oprime.
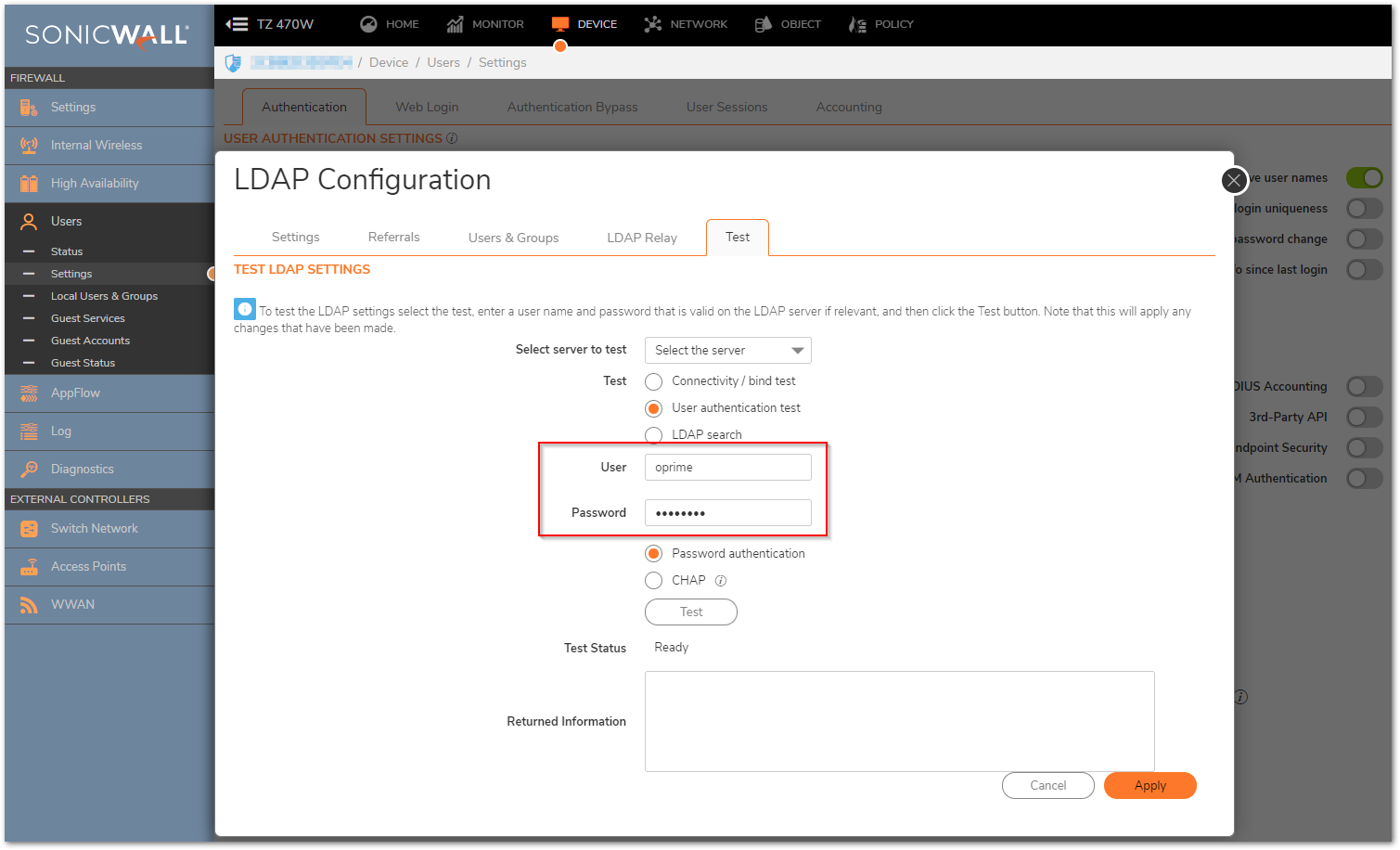
- The LDAP server replies with the user's full DN, which will look something like cn=Optimus Prime,cn=Users,dc=mydomain,dc=com.
- Now that the SonicWall has the full DN of the user, it establishes a new TCP connection with the LDAP server on port 389 (or 636 if using TLS) so it can try to authenticate as the user. The SonicWall sends a bindRequest to the server, using the full DN of the user (cn=Optimus Prime,cn=Users,dc=mydomain,dc=com).
- The LDAP server responds with resultCode - succeeded - and will display information about which groups the user is member of which means that the user authentication is successful.
 TIP: The error message LDAP client authentication failed means that the authentication using the client’s username and password failed. This may happen if any of the following conditions apply.
TIP: The error message LDAP client authentication failed means that the authentication using the client’s username and password failed. This may happen if any of the following conditions apply.
 EXAMPLE: Troubleshooting steps
EXAMPLE: Troubleshooting steps
- The User doesn't’t exist, or doesn’t reside in one of the Trees containing users (Directory tab). Check the LDAP server and make sure that the user object exists in one of the Trees containing users, and that it is spelled correctly.
- The Password is incorrect. Double-check the user’s password.
- There are special characters in the username or password. Most special characters should be OK, but some can cause problems with the bindRequest (such as !, @, ‘ , and ,). To rule out problems with this, test authentication with an account whose username and password have no special characters.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
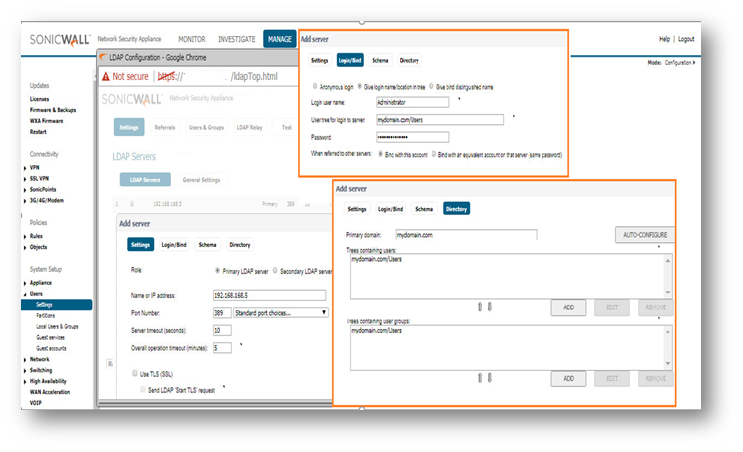
- Click Manage in the top navigation menu.
- Navigate to Users | Settings | Authentication and select LDAP + Local Users and click Configure LDAP.

 TIP: If you are connected to your SonicWall appliance via HTTP rather than HTTPS, you will see a dialog box warning you of the sensitive nature of the information stored in directory services and offering to change your connection to HTTPS. If you have HTTPS management enabled for the interface to which you are connected (recommended), check the “Do not show this message again” box and click Yes.
TIP: If you are connected to your SonicWall appliance via HTTP rather than HTTPS, you will see a dialog box warning you of the sensitive nature of the information stored in directory services and offering to change your connection to HTTPS. If you have HTTPS management enabled for the interface to which you are connected (recommended), check the “Do not show this message again” box and click Yes. NOTE: SonicOS 6.5 introduces support for user authentication partitioning and multiple LDAP Servers. Multiple LDAP Servers are supported on all platforms.For more information about User Authentication Partitioning and multiple LDAP Servers click Authentication Partitioning and Multiple LDAP Servers.
NOTE: SonicOS 6.5 introduces support for user authentication partitioning and multiple LDAP Servers. Multiple LDAP Servers are supported on all platforms.For more information about User Authentication Partitioning and multiple LDAP Servers click Authentication Partitioning and Multiple LDAP Servers. - On the Settings page, click LDAP Servers and click add to enter the server configuration .
- Name or IP address: The FQDN or the IP address of the LDAP server against which you wish to authenticate. If using a name, be certain that it can be resolved by your DNS server. IP address
of the LDAP server . - Port Number: The default LDAP over TLS port number is TCP 636. The default LDAP (unencrypted) port number is TCP 389. If you are using a custom listening port on your LDAP server, specify it here.
- Server timeout (seconds): The amount of time, in seconds, that the SonicWall will wait for a response from the LDAP server before timing out. Allowable ranges are 1 to 99999, with a default of 10 seconds. Overall operation timeout (minutes): 5(Default).
- Use TL(SSL) : Use Transport Layer Security (SSL) to log in to the LDAP server.

 NOTE: SonicOS 6.5 provides two new checkboxes to enforce MSCHAPv2 instead of using the PAP authentication protocol in RADIUS and LDAP authentication. The Force PAP to MSCHAPv2 checkbox is added in Users | Settings on the CONFIGURE LDAP page.
NOTE: SonicOS 6.5 provides two new checkboxes to enforce MSCHAPv2 instead of using the PAP authentication protocol in RADIUS and LDAP authentication. The Force PAP to MSCHAPv2 checkbox is added in Users | Settings on the CONFIGURE LDAP page.
- Anonymous Login – Some LDAP servers allow for the tree to be accessed anonymously. If your server supports this (Active Directory generally does not), then you may select this option.
- Login User Name – Specify a user name that has rights to log in to the LDAP directory. The login name will automatically be presented to the LDAP server in full ‘dn’ notation. This can be any account with LDAP read privileges (essentially any user account) – Domain Administrative privileges are not required but preferred if encounter any priviledge issues. Note that this is the user’s display name, not their login ID.

- Click Schema tab and configure the following fields.
- LDAP Schema: Microsoft Active Directory.

- Click Directory tab and configure the following fields:This will populate the Trees containing users and Trees containing user groups fields by scanning through the directories in search of all trees that contain user objects.

LDAP Authentication Failed
Overview of LDAP Authentication process
- The SonicWall establishes a TCP connection with the LDAP server on port 389 (or 636 if using TLS).
- The SonicWall binds to the LDAP server, authenticating itself using the DN (Distinguished Name) format of the Login user name (Settings tab) + User tree for login to server (Directory tab). In this example, the name in the LDAP bindRequest is cn=Administrator,cn=Users,dc=mydomain,dc=com.
- If the bindResponse from the LDAP server is 'success', then the SonicWall queries the Trees containing users (Directory tab) using the client's username as a filter. In this example, the client is trying to authenticate as oprime, so the SonicWall will query the baseObject "cn=Users,dc=mydomain,dc=com" using the filter sAMAccountName=oprime.
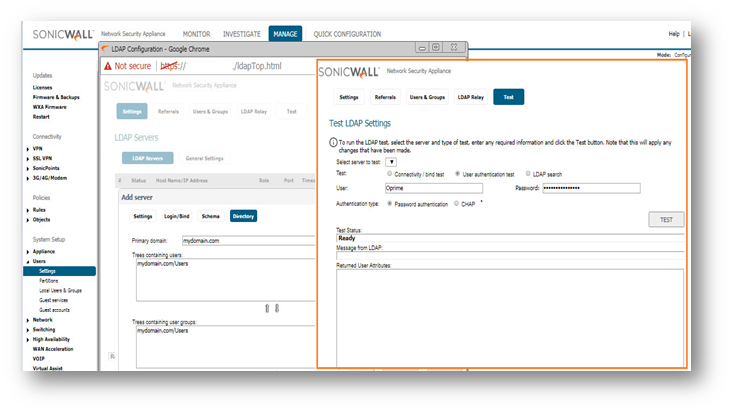
- The LDAP server replies with the user's full DN, which will look something like cn=Optimus Prime,cn=Users,dc=mydomain,dc=com.
- Now that the SonicWall has the full DN of the user, it establishes a new TCP connection with the LDAP server on port 389 (or 636 if using TLS) so it can try to authenticate as the user. The SonicWall sends a bindRequest to the server, using the full DN of the user (cn=Optimus Prime,cn=Users,dc=mydomain,dc=com).
- The LDAP server responds with resultCode - succeeded - and will display information about which groups the user is member of which means that the user authentication is successful.
 TIP: The error message LDAP client authentication failed means that the authentication using the client’s username and password failed. This may happen if any of the following conditions apply.
TIP: The error message LDAP client authentication failed means that the authentication using the client’s username and password failed. This may happen if any of the following conditions apply.
 EXAMPLE: Troubleshooting steps
EXAMPLE: Troubleshooting steps
- The User doesn't’t exist, or doesn’t reside in one of the Trees containing users (Directory tab). Check the LDAP server and make sure that the user object exists in one of the Trees containing users, and that it is spelled correctly.
- The Password is incorrect. Double-check the user’s password.
- There are special characters in the username or password. Most special characters should be OK, but some can cause problems with the bindRequest (such as !, @, ‘ , and ,). To rule out problems with this, test authentication with an account whose username and password have no special characters.
Related Articles
- How to block like/comment/post/share features of Facebook using App Rules
- How to block various YouTube features using App Rules
- How can I enable or disable SonicWall firewall management access?
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > User Login
- Firewalls > TZ Series > User Login
- Firewalls > NSa Series > User Login
- Firewalls > NSv Series > User Login






 YES
YES NO
NO