-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
LDAP Communication Error



Description
SonicOS is capable of integrating with LDAP, as well as RADIUS, for purposes of User Authentication. This allows the SonicWall to apply granular policies for Content Filtering, VPN Access, Security Service implementation, and more.
When using LDAP the SonicWall will most often make use of a Bind Account in order to read from the directory. The SonicWall will also require access to the LDAP Server or Servers in order to utilize the Bind and read from the directory. If there are issues with the communication between the SonicWall and LDAP Server when testing a User/Account or attempting to Import from LDAP the SonicWall will display a Communication Error.
This article details what causes these errors, how to troubleshoot them, and how to avoid them.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Overview of LDAP Process
 TIP: To follow along with the examples below navigate to Device | Users | Settings | Configure LDAP.
TIP: To follow along with the examples below navigate to Device | Users | Settings | Configure LDAP.
- The SonicWall establishes a TCP connection with the LDAP Server on Port 389 (or Port 636 if using TLS).
- The SonicWall binds to the LDAP Server, authenticating itself using the DN (Distinguished Name) format of the Login User Name and User tree for login to server, found on the Settings | Login/Bind tab.
 EXAMPLE: the name in the LDAP BindRequest is cn=SWAdmin,cn=Users,dc=rowley,dc=com.
EXAMPLE: the name in the LDAP BindRequest is cn=SWAdmin,cn=Users,dc=rowley,dc=com.

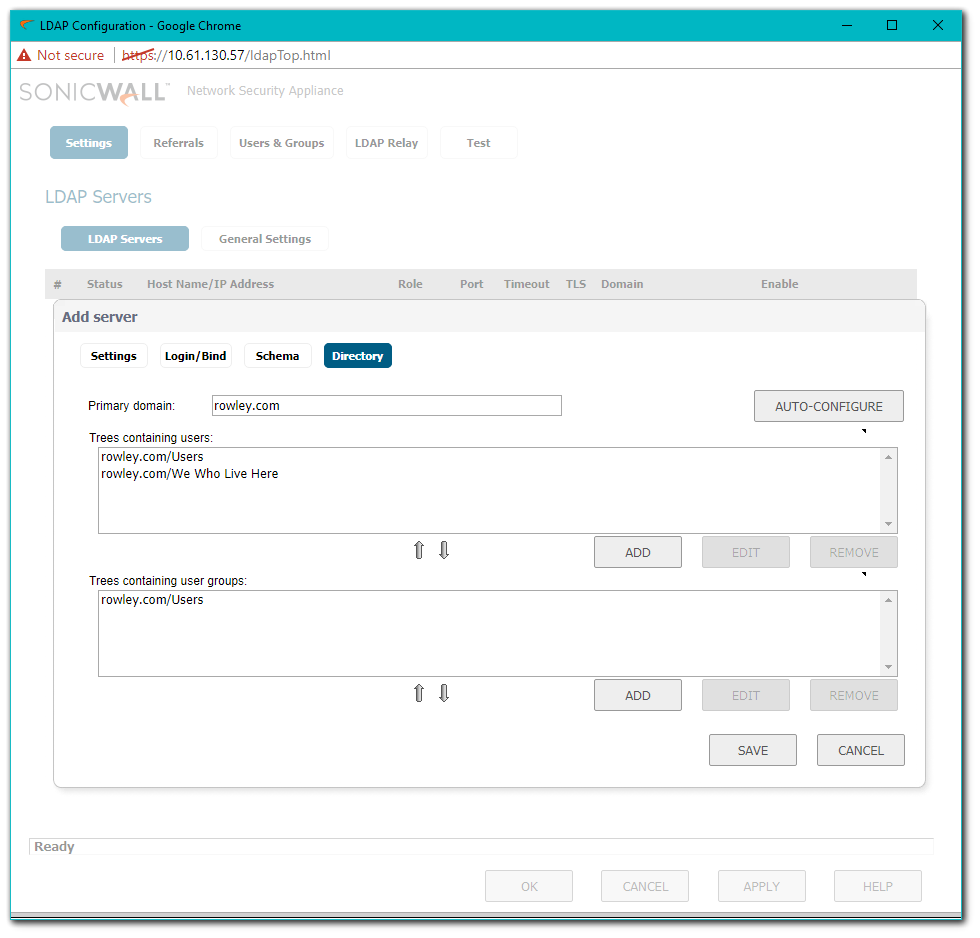
- If the BindResponse from the LDAP server is success, then the SonicWall execute a successful query. In this example, the SonicWall is querying a User, 'jrowley', so the SonicWall will query two BaseObjects: cn=Users,dc=rowley,dc=com and cn=We Who Live Here,dc=rowley,dc=com using the filter sAMAccountName=jrowley. This is because in the screenshot Trees containing users, on the Settings | Directory tab, has two entries, Users and We Who Live Here.
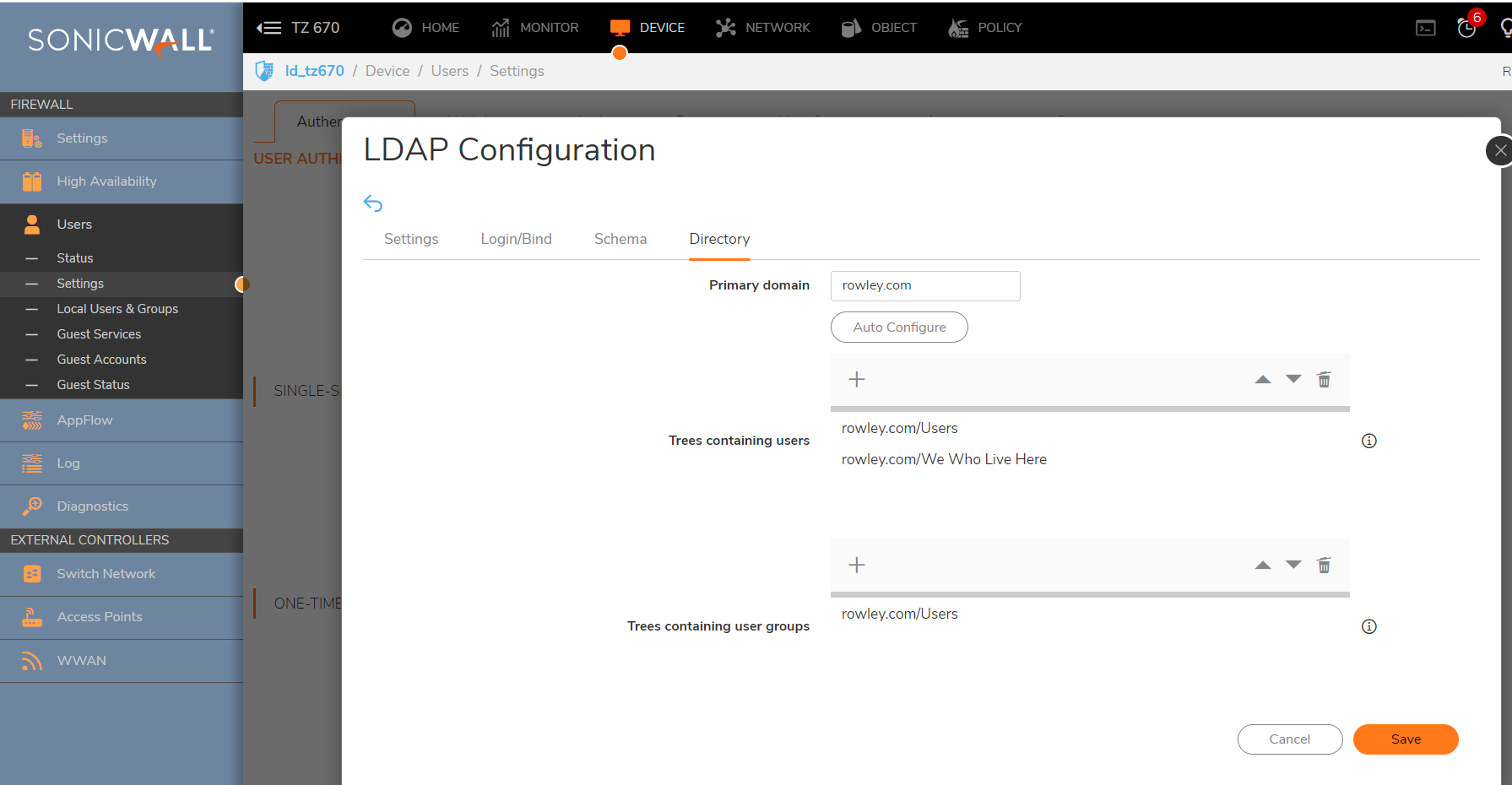
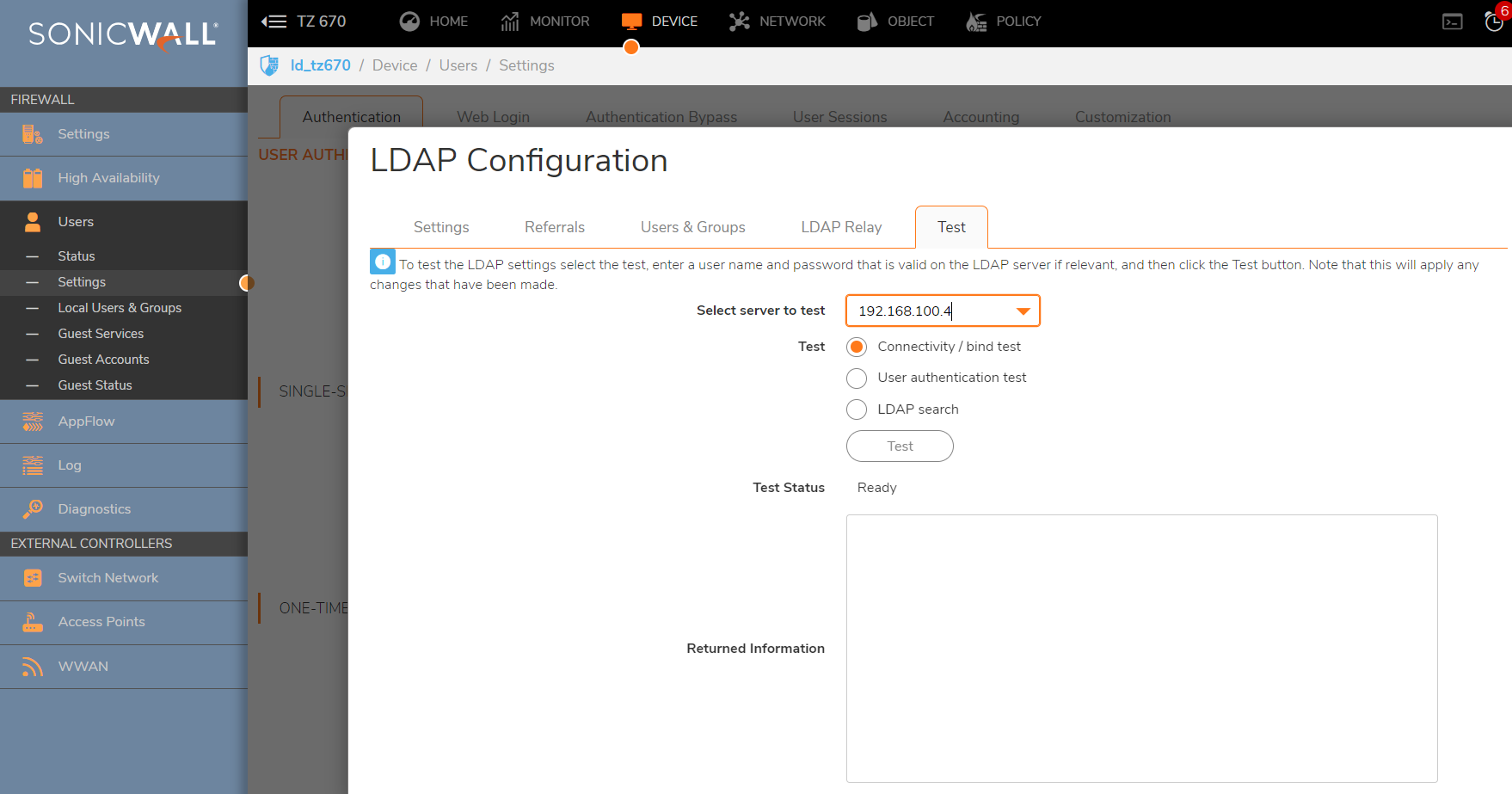
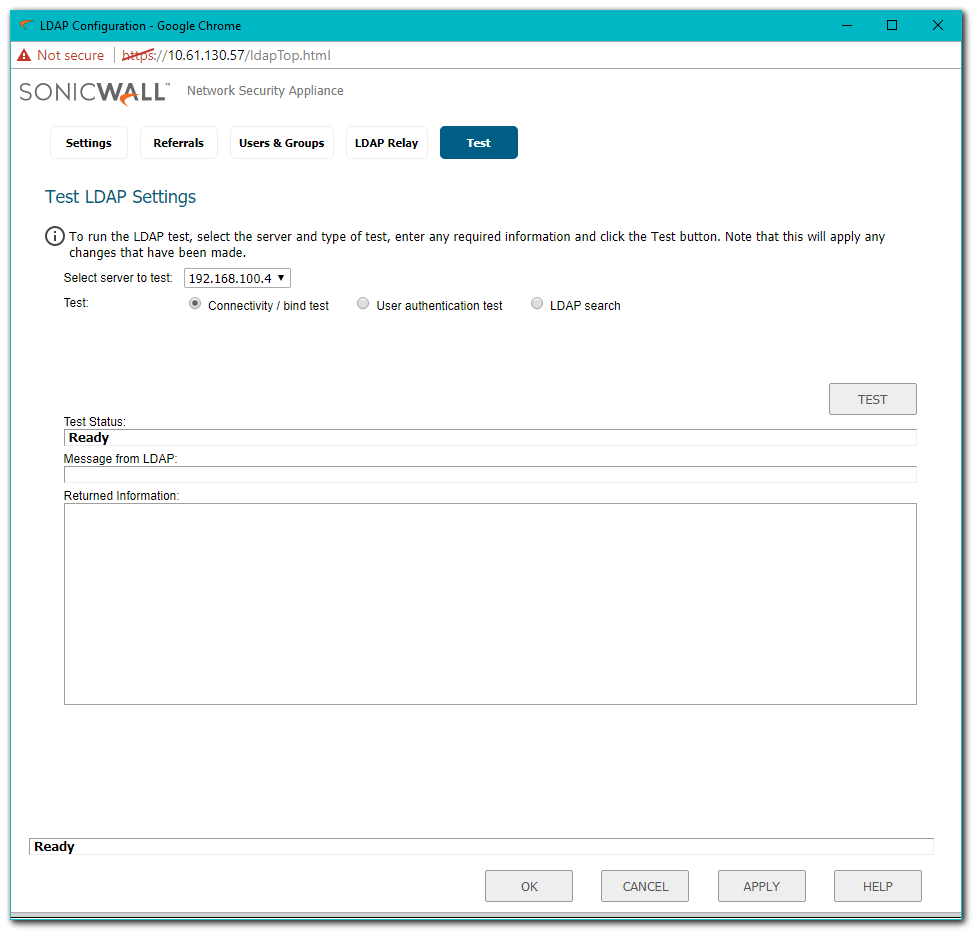
- The LDAP server replies with the user's full DN, which you can view on the Test Tab. When successful the SonicWall is able to find the Organizational Unit and the full distinguished name.
- Now that the SonicWall has the full DN of the user, it establishes a new TCP connection with the LDAP server so it can try to authenticate, this time as the user. The SonicWall sends a BindRequest to the server, using the full DN of the User.
- The LDAP server responds with resultCode: success, which means that the user authentication is successful.
Troubleshooting
- The error message LDAP communication may occur when the DN doesn't confirm to normal formatting. E.g, If the User Tree for login to server is mydomain/Users. In the AD tree the Domain is called 'mydomäin.com'. Because this contains special characters, it cannot be correctly discovered as a Tree containing users. When auto-discovered, it appears with incorrect formatting, and the message “LDAP communication error” may appear. Also, authentication of any user object within this folder may fail.
- This error is typically only a problem with LDAP Protocol Version 2. The fix is to change the Protocol Version on the Settings | General Settings Tab to LDAP Version 3.
- Once this is done, remove the auto-discovered Tree containing users with the incorrect formatting.
 CAUTION: Make sure your LDAP Server supports LDAP Version 3, some legacy Operating Systems do not.
CAUTION: Make sure your LDAP Server supports LDAP Version 3, some legacy Operating Systems do not.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Overview of LDAP Process
 TIP: To follow along with the examples below navigate to Manage | Users | Settings | Configure LDAP.
TIP: To follow along with the examples below navigate to Manage | Users | Settings | Configure LDAP.
- The SonicWall establishes a TCP connection with the LDAP Server on Port 389 (or Port 636 if using TLS).
- The SonicWall binds to the LDAP Server, authenticating itself using the DN (Distinguished Name) format of the Login User Name and User tree for login to server, found on the Settings | Login/Bind tab.
 EXAMPLE: the name in the LDAP BindRequest is cn=SWAdmin,cn=Users,dc=rowley,dc=com.
EXAMPLE: the name in the LDAP BindRequest is cn=SWAdmin,cn=Users,dc=rowley,dc=com.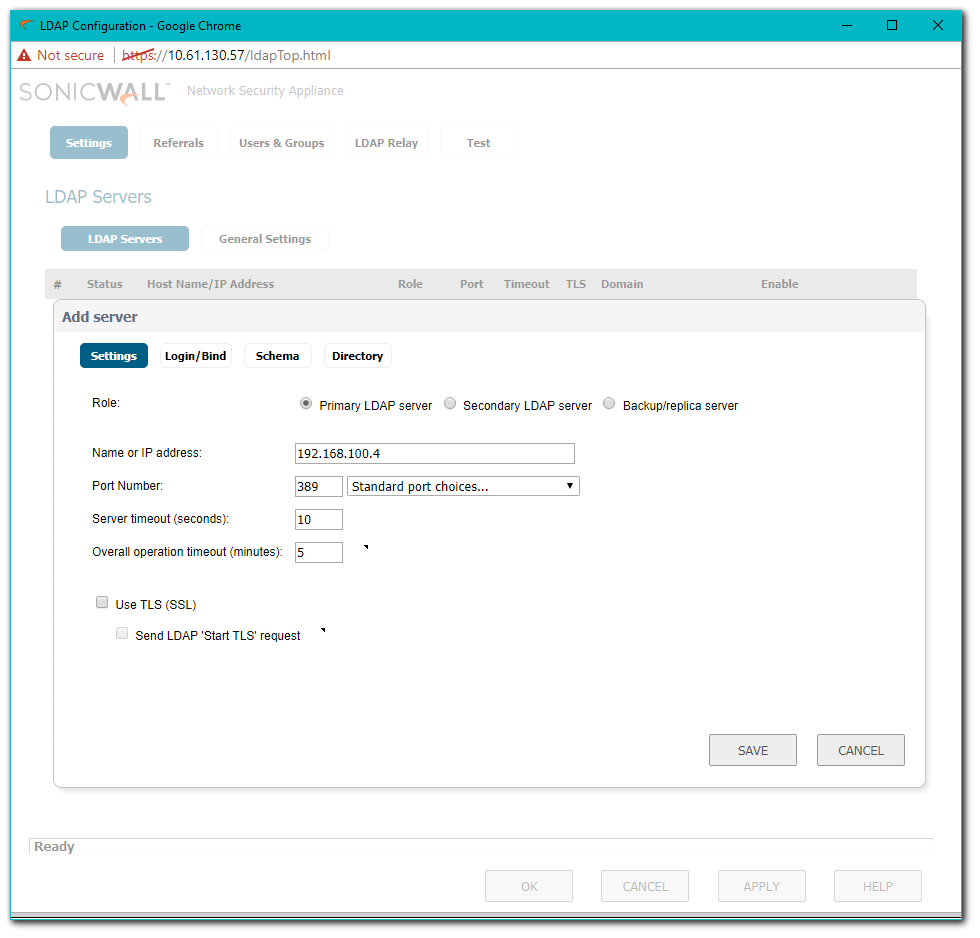
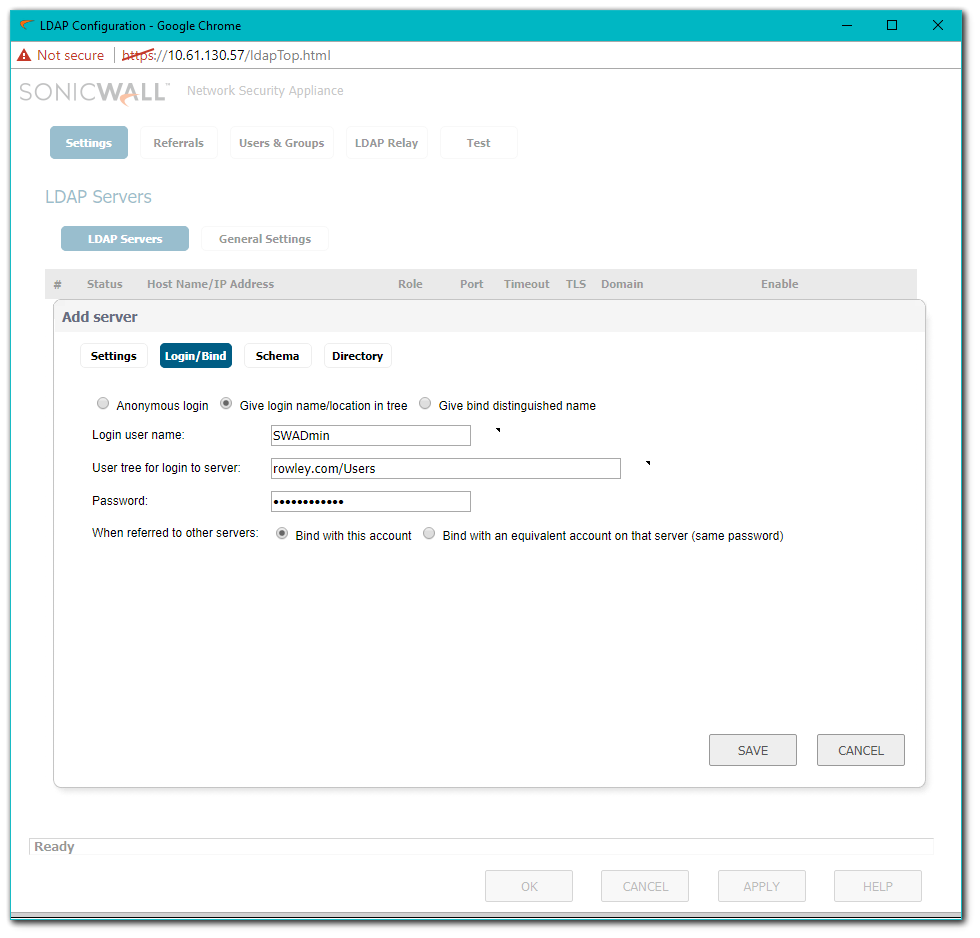
- If the BindResponse from the LDAP server is success, then the SonicWall execute a successful query. In this example, the SonicWall is querying a User, 'jrowley', so the SonicWall will query two BaseObjects: cn=Users,dc=rowley,dc=com and cn=We Who Live Here,dc=rowley,dc=com using the filter sAMAccountName=jrowley. This is because in the above screenshot Trees containing users, on the Settings | Directory tab, has two entries, Users and We Who Live Here.
- The LDAP server replies with the user's full DN, which you can view on the Test Tab. When successful the SonicWall is able to find the Organizational Unit and the full distinguished name.
- Now that the SonicWall has the full DN of the user, it establishes a new TCP connection with the LDAP server so it can try to authenticate, this time as the user. The SonicWall sends a BindRequest to the server, using the full DN of the User.
- The LDAP server responds with resultCode: success, which means that the user authentication is successful.
Troubleshooting
- The error message LDAP communication may occur when the DN doesn't conform to normal formatting. E.g, the User Tree for login to server is mydomain/Users. In the AD tree the Domain is called 'mydomäin.com'. Because this contains special characters, it cannot be correctly discovered as a Tree containing users. When auto-discovered, it appears with incorrect formatting, and the message “LDAP communication error” may appear. Also, authentication of any user object within this folder may fail.
- This error is typically only a problem with LDAP Protocol Version 2. The fix is to change the Protocol Version on the Settings | General Settings Tab to LDAP Version 3.
 CAUTION: Make sure your LDAP Server supports LDAP Version 3, some legacy Operating Systems do not.
CAUTION: Make sure your LDAP Server supports LDAP Version 3, some legacy Operating Systems do not. - Once this is done, remove the auto-discovered Tree containing users with the incorrect formatting.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Overview of LDAP Process
- The SonicWall establishes a TCP connection with the LDAP Server on Port 389 (or Port 636 if using TLS).
- The SonicWall binds to the LDAP Server, authenticating itself using the DN (Distinguished Name) format of the Login User Name and User tree for login to server.
 EXAMPLE:the name in the LDAP BindRequest is cn=SWAdmin,cn=Users,dc=rowley,dc=com.
EXAMPLE:the name in the LDAP BindRequest is cn=SWAdmin,cn=Users,dc=rowley,dc=com.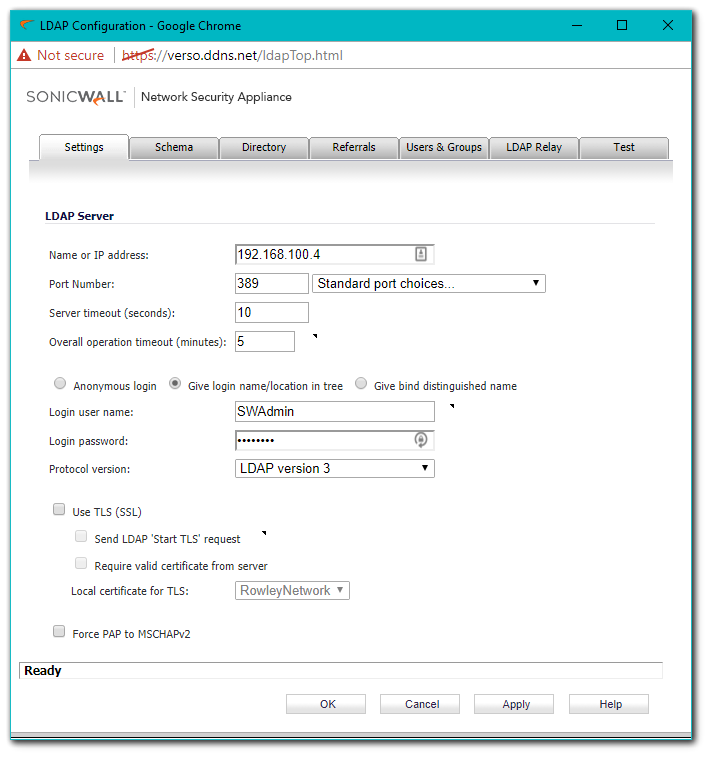
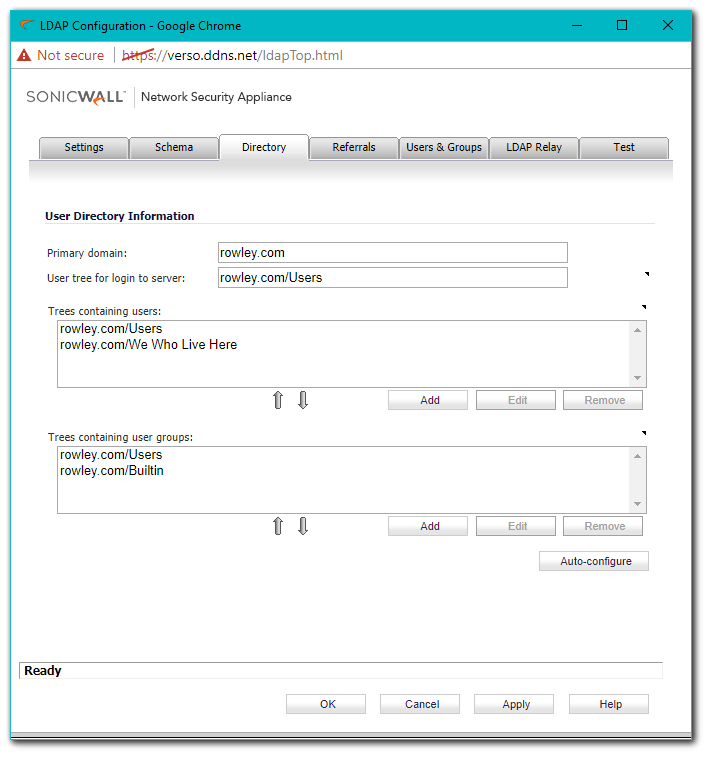
- If the BindResponse from the LDAP server is success, then the SonicWall execute a successful query. In this example, the SonicWall is querying a User, 'jrowley', so the SonicWall will query two BaseObjects: cn=Users,dc=rowley,dc=com and cn=We Who Live Here,dc=rowley,dc=com using the filter sAMAccountName=jrowley. This is because in the above screenshot Trees containing users has two entries, Users and We Who Live Here.
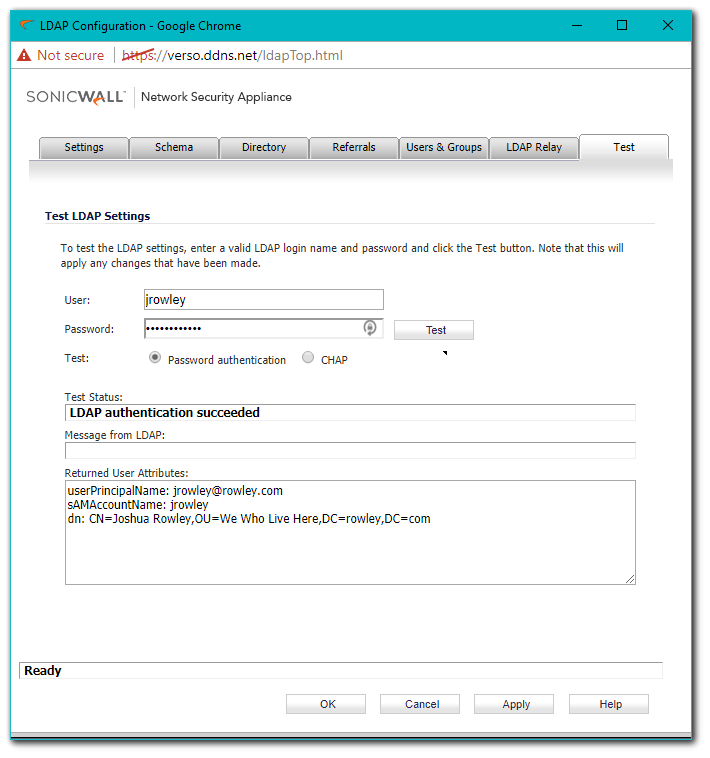
- The LDAP server replies with the user's full DN, which will look something like it does in the above screenshot. As you can see the SonicWall is able to find the Organizational Unit and the full distinguished name.
- Now that the SonicWall has the full DN of the user, it establishes a new TCP connection with the LDAP server so it can try to authenticate, this time as the user. The SonicWall sends a BindRequest to the server, using the full DN of the User.
- The LDAP server responds with resultCode: success, which means that the user authentication is successful.
Troubleshooting
- The error message LDAP communication may occur when the DN doesn't conform to normal formatting.
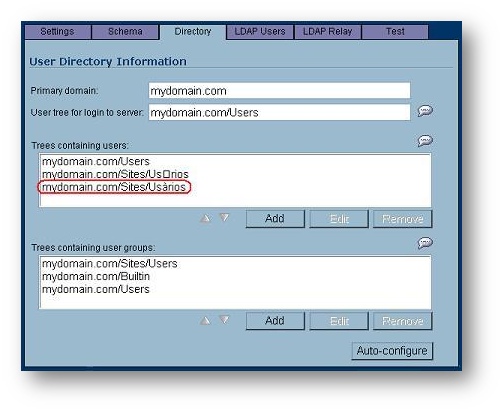
 EXAMPLE: The User Tree for login to server is mydomain/Users. In the AD tree there is a folder called Usàrios, which also contains user objects. Because this contains special characters, it cannot be correctly discovered as a Tree containing users. When auto-discovered, it appears with incorrect formatting, and the message LDAP communication error may appear. Also, authentication of any user object within this folder may fail.
EXAMPLE: The User Tree for login to server is mydomain/Users. In the AD tree there is a folder called Usàrios, which also contains user objects. Because this contains special characters, it cannot be correctly discovered as a Tree containing users. When auto-discovered, it appears with incorrect formatting, and the message LDAP communication error may appear. Also, authentication of any user object within this folder may fail.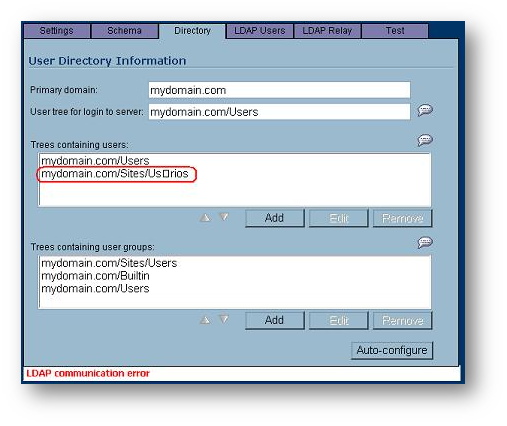
- This is typically only a problem with LDAP Protocol Version 2. The fix is to change the Protocol Version on the Settings tab to LDAP Version 3.
 CAUTION: Make sure your LDAP Server supports LDAP Version 3, some legacy Operating Systems do not.
CAUTION: Make sure your LDAP Server supports LDAP Version 3, some legacy Operating Systems do not.
- Now, when using the Auto-Configure option, the Users folder will be added with the correct formatting.
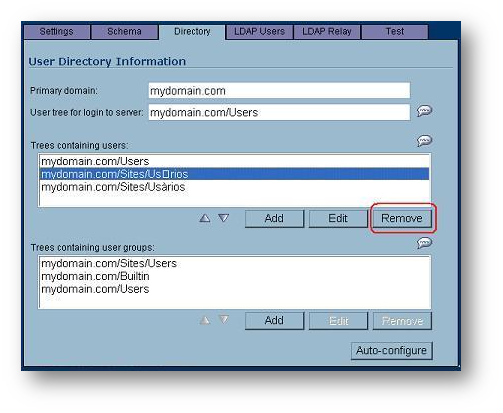
- Once this is done, remove the auto-discovered Tree containing users with the incorrect formatting.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > User Login
- Firewalls > SonicWall SuperMassive E10000 Series > User Login
- Firewalls > TZ Series > User Login
- Firewalls > NSa Series > User Login
- Firewalls > NSv Series > User Login






 YES
YES NO
NO