-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
L2TP - Error 809: Cannot connect L2TP to SonicWall from Windows



Description
When trying to establish a L2TP connection to the SonicWall from Windows machines (such as Windows 7, 8.1, 10 or Windows Server 2008, 2016, etc.), error 809 is shown.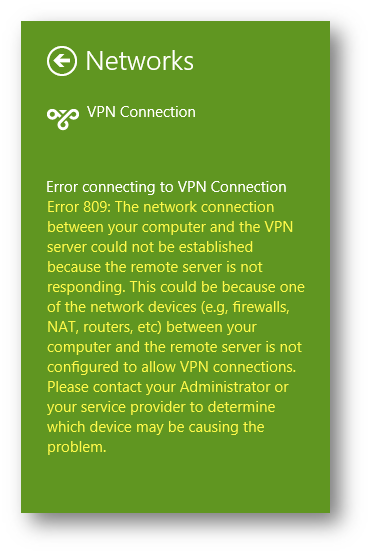
Configuration:
- SonicWall behind another router (NAT)
- WAN IP address of the main router: 89.70.177.xxx
- SonicWall WAN X1 IP: 192.168.0.250
- Ports 500, 4500, 1701 are forwarded to SonicWall
- GVC is working fine
- Cannot establish the connection over L2TP from Windows PCs
- New install of Mac Os 10.10 and Windows 8.1 (fully updated, but no additional software)
This article is assuming that the L2TP configuration is fine and it was checked by making a connection from Mac OS.
Here is a packet capture when trying to establish the connection from Mac Os: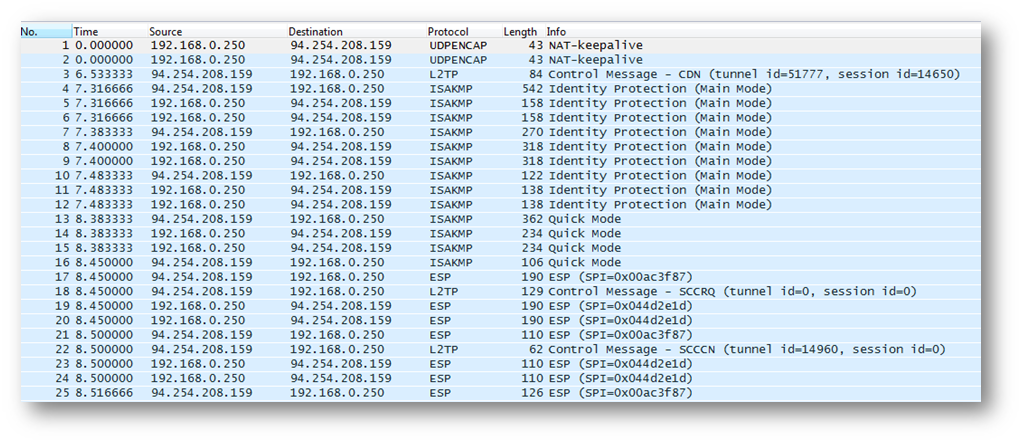
As you can see, all packets are seen: ISAKMP, ESP and L2TP. The connection is working fine without any problems.
Below is a packet capture to the same SonicWall with the same credentials but using a Windows 8.1 PC.It was a new Windows 8.1 installation, with all the updates and without additions software.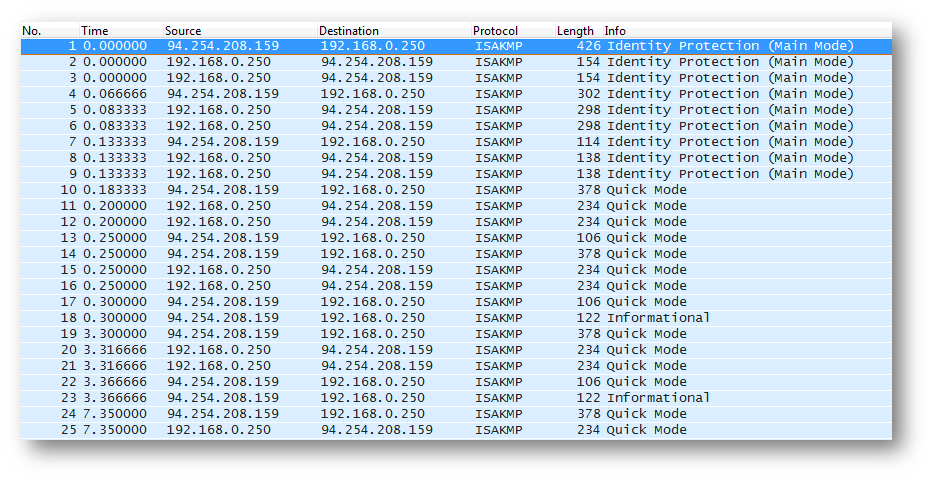
On this packet capture we see that there are only ISAKMP packet and there are no L2TP and ESP packes.The PC cannot establish the connection in this way and we see the error 809.
Cause
The problem in this case is on the Windows site.
Windows (Vista, Server 2008, 7, 8.1, 10) operating systems do not support Internet Protocol security (IPSec) network address translation (NAT) Traversal (NAT-T) security associations to servers that are located behind a NAT device. Therefore, if the virtual private network (VPN) server is behind a NAT device, a Windows VPN client computer cannot make a Layer Two Tunneling Protocol (L2TP)/IPSec connection to the VPN server.
Because of the way in which NAT devices translate network traffic, you may experience unexpected results when you put a server behind a NAT device and then use an IPSec NAT-T environment. Therefore, if you need IPSec for communication, we recommend that you use public IP addresses for all servers that you want connect to from the Internet. However, if you have to put a server behind a NAT device and then use an IPsec NAT-T environment, you can enable communication by changing a registry value on the VPN client computer and the VPN server.
Resolution
 NOTE: This is the workaround you may apply. As this is a Windows issue, you will need to refer to its Knowledge Base for further information.
NOTE: This is the workaround you may apply. As this is a Windows issue, you will need to refer to its Knowledge Base for further information.
- Login to the PC as Administrator or an user who is a member of the Administrator Group.
- Navigate to Start | Run or Start | All Programs | Accessories | Run and type regedit.
- Locate the entry HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent.
- Create a new DWORD (32-bit) value (Edit | New).
- Add AssumeUDPEncapsulationContextOnSendRule and save.
- Modify the new entry and change Value Data from 0 to 2.
Value 0 -| Cannot establish security associations with servers that are located behind NAT devices.
Value 2 -| Can establish security associations with servers that are located behind NAT devices. - Reboot the computer and try to setup the connection one more time.
- After the reboot we should be able to connect to the SonicWall with the same configuration as before.
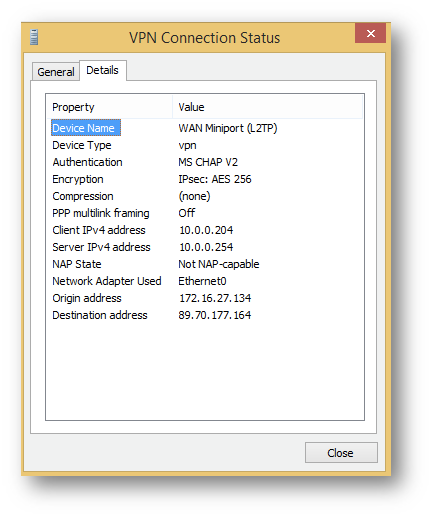
Let us check the packet capture from this device: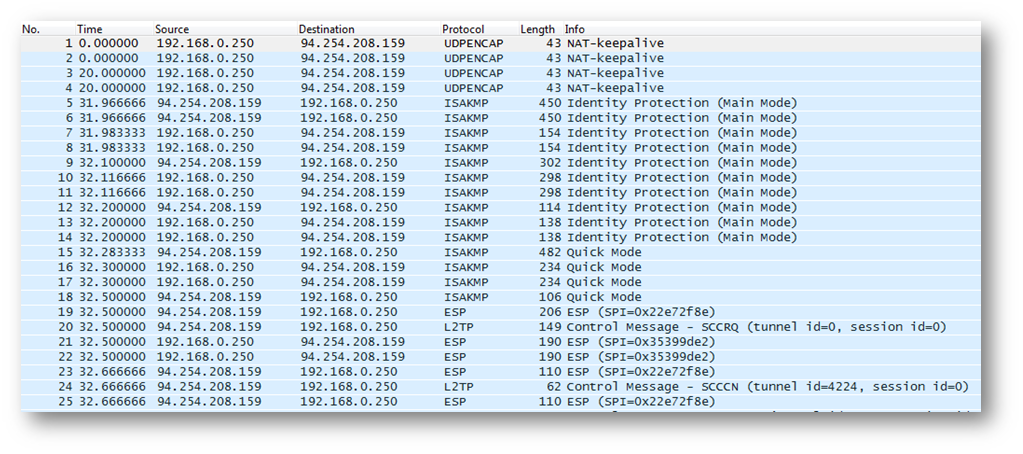
Now we see the ISAKMP, ESP and L2TP packets.All the traffic is working fine and we are able to access the resources behind the SonicWall.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > NSa Series > GVC/L2TP
- Firewalls > NSv Series > GVC/L2TP
- Firewalls > TZ Series > GVC/L2TP






 YES
YES NO
NO