-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to use the SonicWall ASIM Parsers in your Sentinel workspace?



Description
This article covers how to use the SonicWall ASIM parsers in your Microsoft Sentinel workspace.
This article has a prerequisite: How to Deploy the SonicWall ASIM Parsers into your Sentinel workspace.
While the parsers are built into every Microsoft Sentinel workspace for broader use and unification of NetworkSession or WebSession events across multiple vendors, deploying the SonicWall parsers into the workspace enables the Workbooks, Analytic Rules, Hunting Queries, etc. to function using the workspace function names, rather than the built-in function names.
Parser Overview
Advanced Security Information Model (ASIM) parsers are used in Microsoft Sentinel for parsing and normalization of event data stored in existing table, such as CommonSecurityLog. There are built-in parsers as well as “workspace-deployed” parsers. There are advantages and disadvantages to each.
You can read more about ASIM parsers here: https://learn.microsoft.com/en-us/azure/sentinel/normalization-parsers-overview
ASim and vim parser variants:
- Regular parsers (prefixed with “ASim”) are parsers that do not require filtering parameters, and support setting a time range from a drop down when writing queries on the “Logs” page.
- Parameterized parsers (prefixed with “vim”) require filtering parameters. Filtering parameters can improve your query performance by fine-tuning the query using the available parameters such as start time/end time, source/destination IP address prefix, port number, action, and event result.
- Each schema has a set of filtering parameters.
SonicWall provides a regular parser and parameterized parser for each schema we support. Each schema has a set fields and guidelines, so it’s a good idea to review schema documentation for information about the available fields. Learn more about the Network Session and Web Session schemas at the links in the table below.
| Workspace-deployed Function | Parser variant | Schema |
| ASimNetworkSessionSonicWallFirewall | Regular parser | |
| vimNetworkSessionSonicWallFirewall | Parameterized parser | |
| ASimWebSessionSonicWallFirewall | Regular parser | |
| vimWebSessionSonicWallFirewall | Parameterized parser |
Table of filtering parameters
| Parameter | Details | Type/Example Values |
| disabled | A Boolean value that disables results from the parser. The default value is false for ASim parsers. A value needs to be defined when using the parameterized (vim) parser function (see the example usage of the parser function). Test that the disabled parameter works for each parser function. When disabled is true , a query will not return any results. | Boolean true false |
| dstipaddr_has_any_prefix | Filter only network sessions for which the destination IP address field prefix is in one of the listed values. Prefixes should end with a ., for example: 10.0.. The length of the list is limited to 10,000 items. | Dynamic dynamic([]); dynamic(["192.168.5."]); dynamic([172.16.]); dynamic([10.]); dynamic(["192.168.5.", "172.16.", "10."]); |
| dstportnumber | Filter only network sessions with the specified destination port number. | Integer int(null) 443; "443"; dynamic(443); dynamic("443"); |
| dvcaction | Filter only network sessions for which the Device Action field is any of the values listed. | Dynamic/String dynamic([]); dynamic(["Allow"]); dynamic(["Allow", "Drop"]); |
| endtime | Filter only network sessions that started running at or before this time. | Datetime todatetime('2023-09-12 15:24:55'); |
| eventresult | Filter on a specific event result. The EventResult column has a set of allowed values based on the DvcAction column. DvcAction is based on the parsed fw_action column. Refer to the fw_action to DvcAction to EventResult mapping table below this table. | String Expected values include:
|
| hostname_has_any | Filter only network sessions for which the destination hostname field has any of the values listed. The length of the list is limited to 10,000 items. | Dynamic/String dynamic([]); dynamic(["SALES-PC1"]); "SUPPORT-PC1" |
| httpuseragent_has_any | Web Session parser Filter only web sessions for which the user agent field has any of the values listed. If specified, and the session is not a web session, no result will be returned. The length of the list is limited to 10,000 items. | Dynamic dynamic([]); dynamic(["Mozilla/5.0"]); dynamic(["Mozilla/5.0", "AppleWebKit/537.36"]); |
| ipaddr_has_any_prefix | Filter only network sessions for which the destination IP address field or source IP address field prefix is in one of the listed values. Prefixes should end with a ., for example: 10.0.. The length of the list is limited to 10,000 items. | Dynamic dynamic([]); dynamic(["192.168.5."]); dynamic([172.16.]); dynamic([10.]); dynamic(["192.168.5.", "172.16.", "10."]); |
| srcipaddr_has_any_prefix | Filter only network sessions for which the source IP address field prefix is in one of the listed values. Prefixes should end with a ., for example: 10.0.. The length of the list is limited to 10,000 items. | Dynamic dynamic([]); dynamic(["192.168.5."]); dynamic([172.16.]); dynamic([10.]); dynamic(["192.168.5.", "172.16.", "10."]); |
| starttime | Filter only network sessions that started at or after this time. | Datetime todatetime('2023-09-12 05:04:36'); |
| url_has_any | Web Session parser Filter only Web sessions for which the URL field has any of the values listed. The parser may ignore the schema of the URL passed as a parameter, if the source does not report it. If specified, and the session is not a web session, no result will be returned. The length of the list is limited to 10,000 items. | Dynamic dynamic([]); dynamic(["icloud.com"]); dynamic(["icloud.com", "amazon.com"]); |
Mapping Table: fw_action to DvcAction to EventResult
| fw_action | DvcAction | EventResult | About |
| "\"mgmt\"" ("mgmt") | "Management" | "NA" | Management traffic. SonicWall uses this value. It is not an expected value for DvcAction. EventResult will be NA. |
| "\"NA\"" ("NA") | "NA" | "NA" | SonicWall uses NA commonly. NA could be allowed or denied. |
| "allow" "\"forward\"" ("forward") | "Allow" | "Success" | If the DvcAction is allow, EventResult is success. |
| "deny" "\"drop\"" ("drop") | Any Deny/Reset value Anything not covered above | "Failure" | This is not a comprehensive list of DvcActions. |
Instructions
In your Microsoft Sentinel workspace:
Navigate to the “General” > “Logs” page.
Querying the CommonSecurityLog table
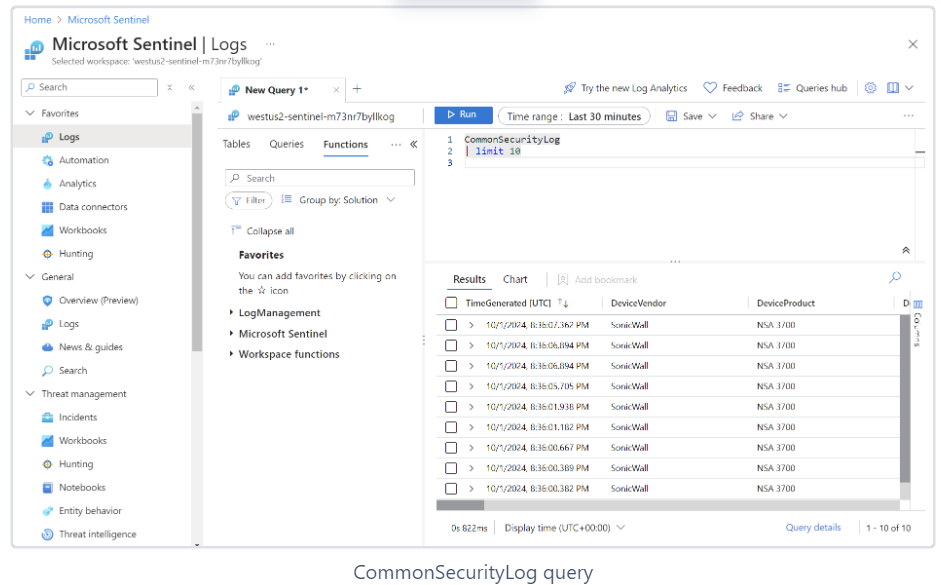
Query the CommonSecurityLog table to confirm data from your firewall is being ingested by Microsoft Sentinel. Use the queries below to display a limited number of events and reorder columns for easier identification by model and serial number. The second query returns a list of distinct serial numbers from the data in CommonSecurityLog. Adjust these queries as needed to confirm that data you expect is reaching Microsoft Sentinel.
CommonSecurityLog
| limit 10
| project-reorder DeviceVendor, DeviceProduct, Computer
CommonSecurityLog
| distinct Computer
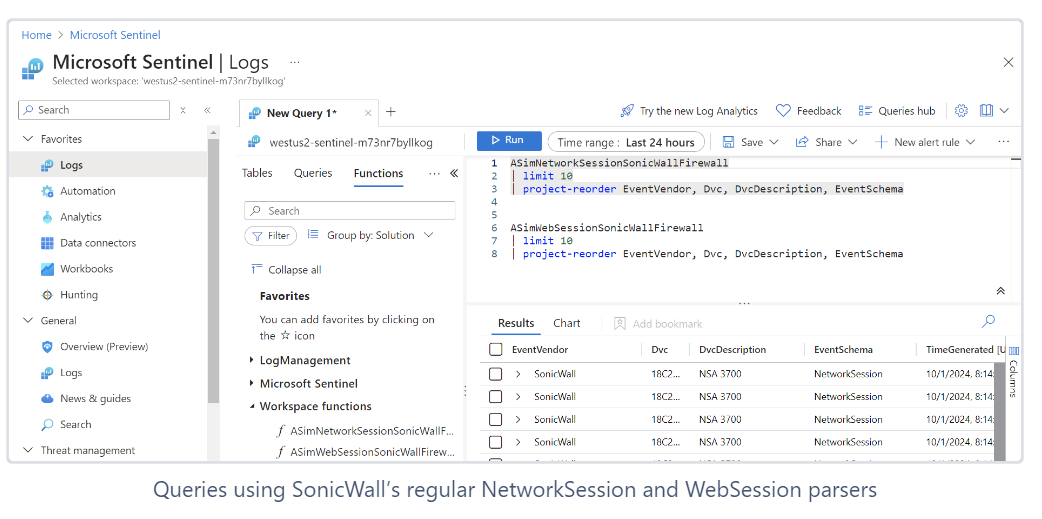
Querying with the regular parsers
Use the following basic queries individually to display events parsed, normalized, and filtered down based on the ASIM schemas. These queries reorder a few columns so that the schema and firewall can be quickly identified.
ASimNetworkSessionSonicWallFirewall
| limit 10
| project-reorder EventVendor, Dvc, DvcDescription, EventSchema
ASimWebSessionSonicWallFirewall
| limit 10
| project-reorder EventVendor, Dvc, DvcDescription, EventSchema
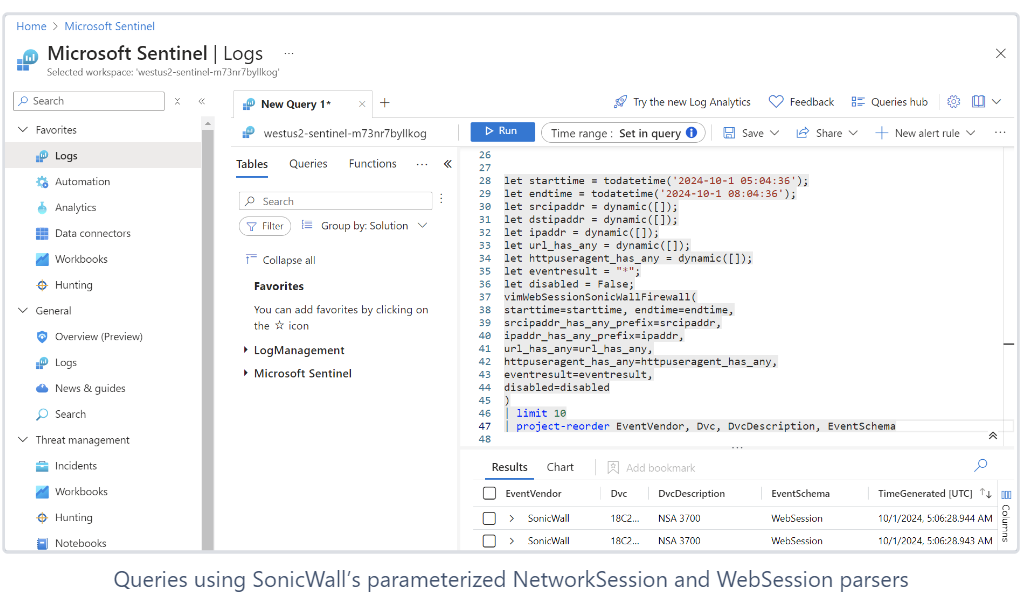
Querying with the parameterized parsers
Use the following queries individually to display events parsed, normalized, and filtered down based on the ASIM schemas. These queries are parameterized, meaning they expect filtering parameters to be applied to the query. Adjust the queries as needed (in particular, the start and end times). Refer to the filtering parameters table above in this article for details and example values.
Network Session:
let starttime = todatetime('2024-10-1 05:04:36');
let endtime = todatetime('2024-10-1 08:04:36');
let srcipaddr_has_any_prefix = dynamic([]);
let dstipaddr_has_any_prefix = dynamic([]);
let ipaddr_has_any_prefix = dynamic([]);
let dstportnumber = int(null);
let hostname_has_any = dynamic([]);
let dvcaction = dynamic([]);
let eventresult = "*";
let disabled = False;
vimNetworkSessionSonicWallFirewall(
starttime=starttime,
endtime=endtime,
srcipaddr_has_any_prefix=srcipaddr_has_any_prefix,
dstipaddr_has_any_prefix=dstipaddr_has_any_prefix,
ipaddr_has_any_prefix=ipaddr_has_any_prefix,
dstportnumber=dstportnumber,
hostname_has_any=hostname_has_any,
dvcaction=dvcaction,
eventresult=eventresult,
disabled=disabled
)
| limit 10
| project-reorder EventVendor, Dvc, DvcDescription, EventSchema
Web Session:
let starttime = todatetime('2024-10-1 05:04:36');
let endtime = todatetime('2024-10-1 08:04:36');
let srcipaddr = dynamic([]);
let dstipaddr = dynamic([]);
let ipaddr = dynamic([]);
let url_has_any = dynamic([]);
let httpuseragent_has_any = dynamic([]);
let eventresult = "*";
let disabled = False;
vimWebSessionSonicWallFirewall(
starttime=starttime, endtime=endtime,
srcipaddr_has_any_prefix=srcipaddr,
ipaddr_has_any_prefix=ipaddr,
url_has_any=url_has_any,
httpuseragent_has_any=httpuseragent_has_any,
eventresult=eventresult,
disabled=disabled
)
| limit 10
| project-reorder EventVendor, Dvc, DvcDescription, EventSchema
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO