-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to setup WPA-EAP (Protected EAP or PEAP) on the Sonicwall firewall with Microsoft IAS



Description
How to setup WPA-EAP (Protected EAP or PEAP) on the Sonicwall firewall with Microsoft IAS.
Resolution
Step 1: Launch IAS console and add the Sonicwall firewall as the RADIUS client as follows.
 Step 2: Open the Remote Access Policy and Add a New Policy for the firewall.
Step 2: Open the Remote Access Policy and Add a New Policy for the firewall.
 Step 3: Select Client-IP-Address as Policy Conditions and select ‘Grant remote access permission’
Step 3: Select Client-IP-Address as Policy Conditions and select ‘Grant remote access permission’
Step 4: Click Edit Profile button. The following edit profile window will appear:
 Step 5: Select all the authentication method except CHAP and then click on the ‘EAP Methods’ button
Step 5: Select all the authentication method except CHAP and then click on the ‘EAP Methods’ button
 Step 6: Click on the Add button and select Protected EAP (PEAP) as the Authentication method.
Step 6: Click on the Add button and select Protected EAP (PEAP) as the Authentication method.
 Step 7: Click Apply and OK buttons to return to the Report Access Policies window:
Step 7: Click Apply and OK buttons to return to the Report Access Policies window:
 The RADIUS server is now configured for PEAP authentication. We now need to setup the firewall for the WPA-EAP.
The RADIUS server is now configured for PEAP authentication. We now need to setup the firewall for the WPA-EAP.
Login to the firewall management console and go to Wireless Tab, Setup the SSID and then go to WEP/WPA Encryption Tab.
Select WPA-EAP as the Authentication type, Select TKIP as the Cipher type. Type in the IP address of the RADIUS server (port 1812) and the shared secret key.
The firewall is setup for the EAP authentication now. We can now setup the wireless client for the PEAP authentication. The following are the steps:
(Use windows Wireless Zero Configuration, WZC for the connection; disable third party connection software if there is any)
Step 1: Open Network Connection in the control panel and then go to the Properties of ‘Wireless Network Connect’. Click on the Wireless Network Tab
 Step 2: Click on the Add button to add the new Wireless network. Type in the SSID and select WPA for authentication and TKIP for encryption. Ensure you are selecting WPA not WPA-PSK.
Step 2: Click on the Add button to add the new Wireless network. Type in the SSID and select WPA for authentication and TKIP for encryption. Ensure you are selecting WPA not WPA-PSK.
 Step 3: Go to the Authentication Tab. Check the following boxes and select Protected EAP (PEAP) from the EAP Type dropdown menu.
Step 3: Go to the Authentication Tab. Check the following boxes and select Protected EAP (PEAP) from the EAP Type dropdown menu.
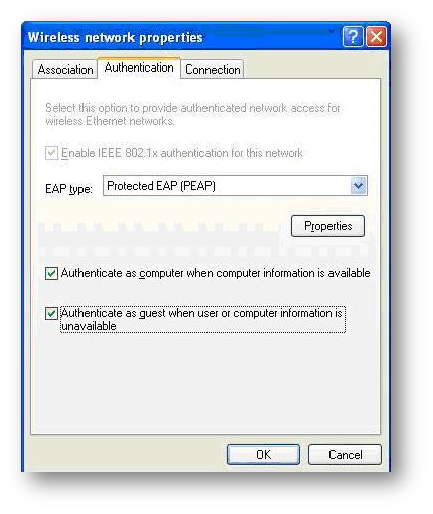
Step 4: Click on the Properties button next to the EAP Type selection. The Protected EAP Properties window opens up as follows:
 Step 5: Uncheck ‘Validate server certificate’ box and select ‘Secured password (EAP-MSCHAP v2) as shown above.
Step 5: Uncheck ‘Validate server certificate’ box and select ‘Secured password (EAP-MSCHAP v2) as shown above.
Step 6: Click on the configure button and uncheck the ‘automatically use Windows logon name, box as follows.
 Step 7: Click OK on all the pages to save the changes and return to Network Connection window. Right click the Wireless network connection and select View Available wireless network. It will show the new wireless network in the available list as Manual and WPA enabled.
Step 7: Click OK on all the pages to save the changes and return to Network Connection window. Right click the Wireless network connection and select View Available wireless network. It will show the new wireless network in the available list as Manual and WPA enabled.
 Step 8: Select this network and click connect. You will see the following bubble pop-up message in the system tray, asking you to select a certificate or other credentials for connection.
Step 8: Select this network and click connect. You will see the following bubble pop-up message in the system tray, asking you to select a certificate or other credentials for connection.
 Step 9: Click on this bubble pop-up message and it will open up the domain login window as follows.
Step 9: Click on this bubble pop-up message and it will open up the domain login window as follows.

Once the user is successfully authenticated by the RADIUS server, the firewall connection with be established. The bubble with pop-up in the system tray showing, it is connected to the network with signal strength.
If you go to the Status page of the Wireless Tab on the firewall management GUI, you will see the user name as the associated client, instead of the computer name. See the screenshot below:
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series







 YES
YES NO
NO