-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How To Restrict traffic from only selected MAC addresses using MAC-IP Anti-Spoof Protection



Description
This article explains how to restrict traffic initiated from internal network, based on MAC addresses, using MAC-IP Anti-spoof protection. The MAC-IP Anti-Spoof feature lowers the risk of these attacks by providing administrators different ways to control access to a network, and by eliminating spoofing attacks at OSI Layer 2/3.
The MAC-IP Anti-Spoof cache validates incoming packets and determines whether they are to be allowed inside the network. An incoming packet's source MAC and IP addresses are looked up in this cache. If they are found, the packet is allowed through. The MAC-IP Anti-Spoof cache is built through one or more of the following sub-systems:
- DHCP Server-based leases (SonicWall's - DHCP Server)
- DHCP relay-based leases (SonicWall's - IP Helper)
- Static ARP entries
- User created static entries
This article explains the use of Static ARP (Address Resolution Protocol) by Binding an IP to a MAC address and ensuring only IP's with static ARP entries are allowed on the network and rest will be blocked. This would serve two purposes, blocking unauthorized access, and allow only listed Mac addresses in the network.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Step 1: Enable MAC-IP Anti-Spoof protection under System | MAC-IP Anti-Spoof on a specific interface (it is based on interface and not on zones), for example enable it on X0 as shown below:
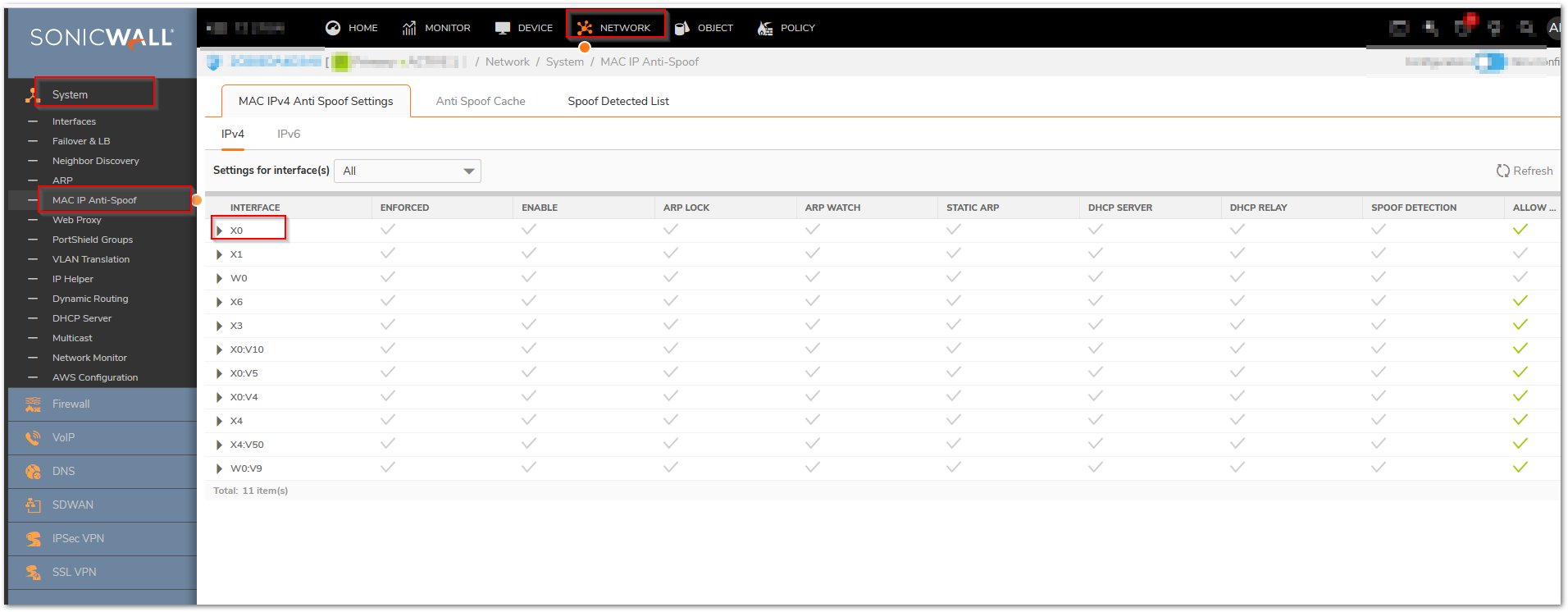
Step 2: Click on the "Configure" pencil edit circle to to configure settings for interface X0, select the options as shown below:
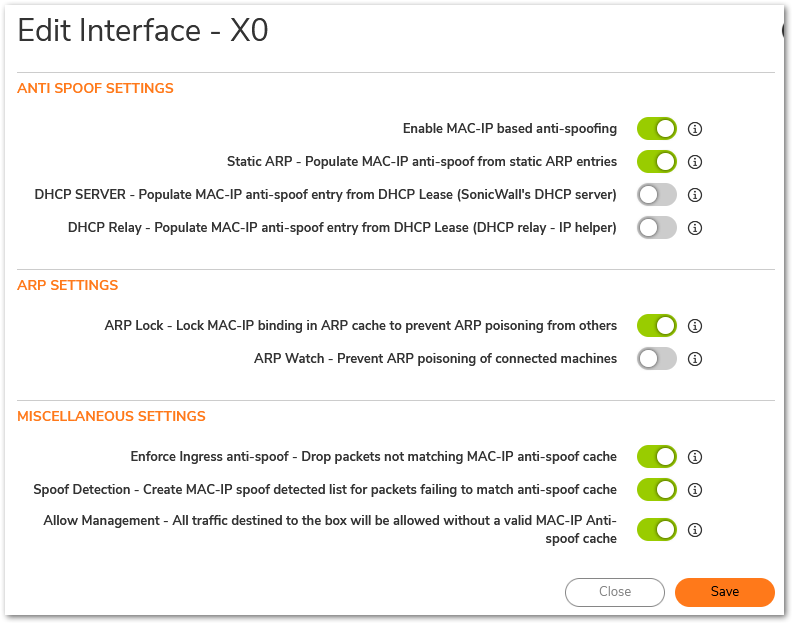
Step 3: Check if the settings have been applied as shown below:
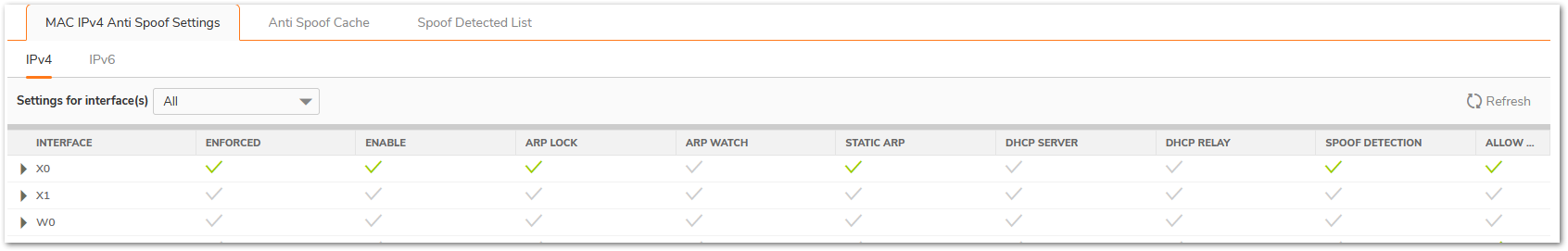
Note: Once ARP Lock and Enforce Ingress anti-spoof options are enabled SonicWall firewall will check the static ARP entries and load them in MAC-IP Anti-Spoof cache. Traffic from any other MAC address and IP address combination would be dropped.
How to Test:
If another machine whose MAC address is not listed in the cache would try to communicate through firewall , it would be dropped as shown below: MAC-IP Anti-Spoof check enforced for hosts.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Step 1: Enable MAC-IP Anti-Spoof protection under Manage| Network | MAC-IP Anti-Spoof on a specific interface (it is based on interface and not on zones), for example enable it on X0 as shown below:
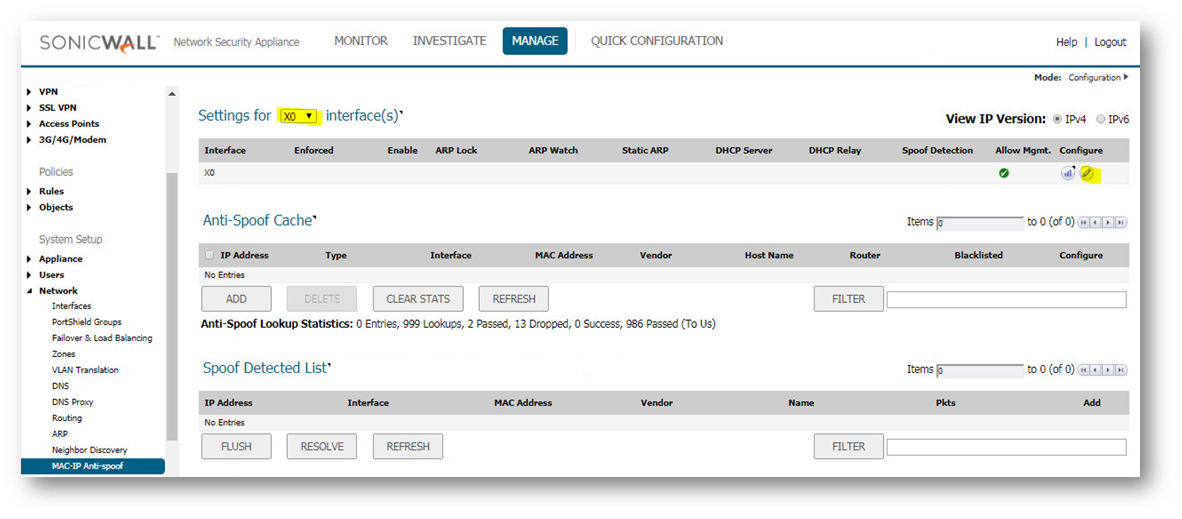
Step 2: Click on the "Configure" pencil edit circle to to configure settings for interface X0, select the options as shown below:
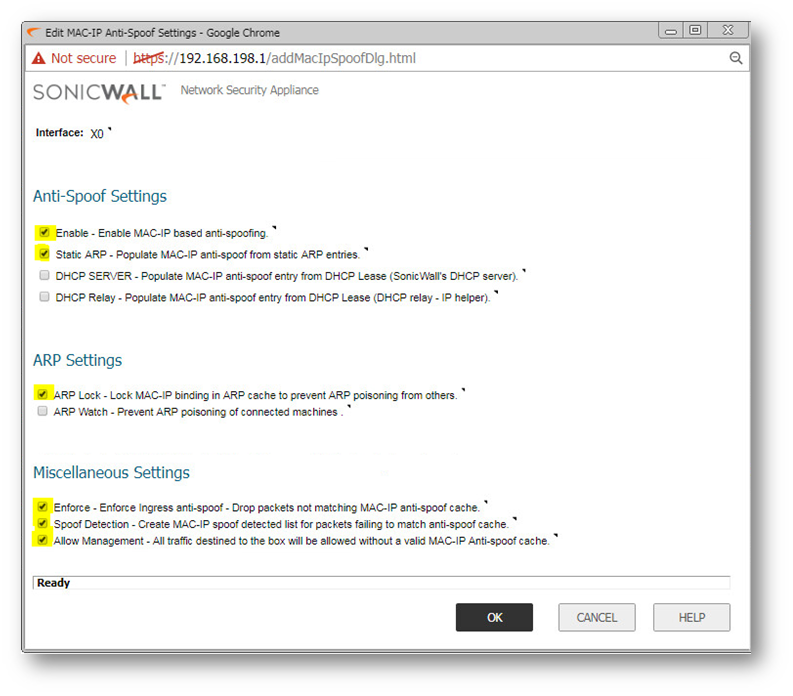
Step 3: Check if the settings have been applied as shown below:
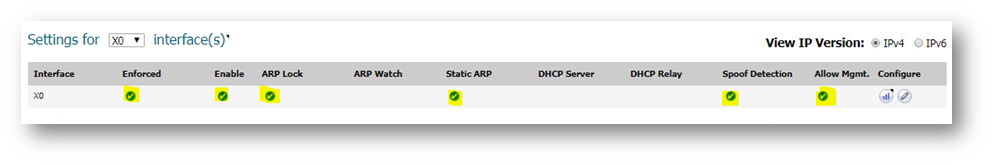
Note: Once ARP Lock and Enforce Ingress anti-spoof options are enabled SonicWall firewall will check the static ARP entries and load them in MAC-IP Anti-Spoof cache. Traffic from any other MAC address and IP address combination would be dropped.
How to Test:
If another machine whose MAC address is not listed in the cache would try to communicate through firewall , it would be dropped as shown below:
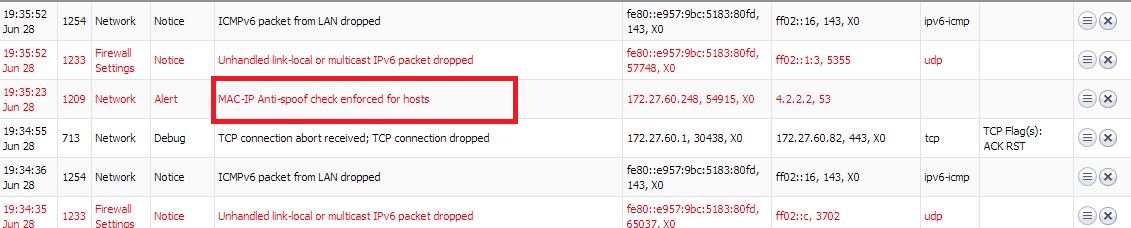
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Step 1: Enable MAC-IP Anti-Spoof protection under Network | MAC-IP Anti-Spoof on a specific interface (it is based on interface and not on zones), for example enable it on X0 as shown below:
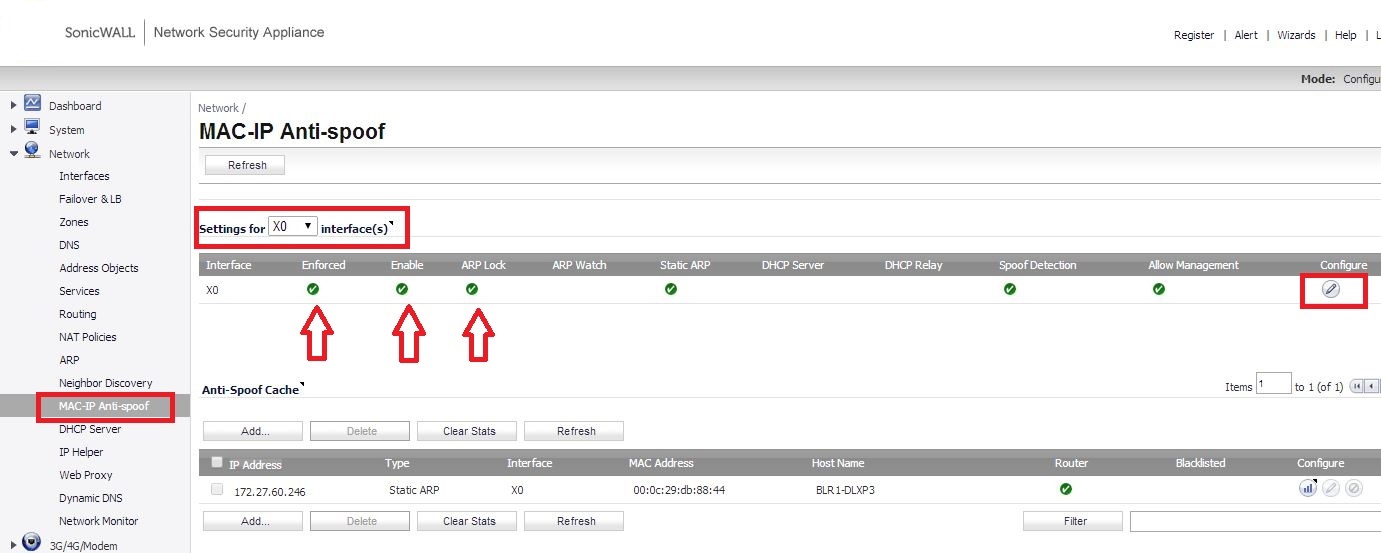
Step 2: Click on the "Configure" pencil edit circle to to configure settings for interface X0, select the options as shown with pointing arrows below:
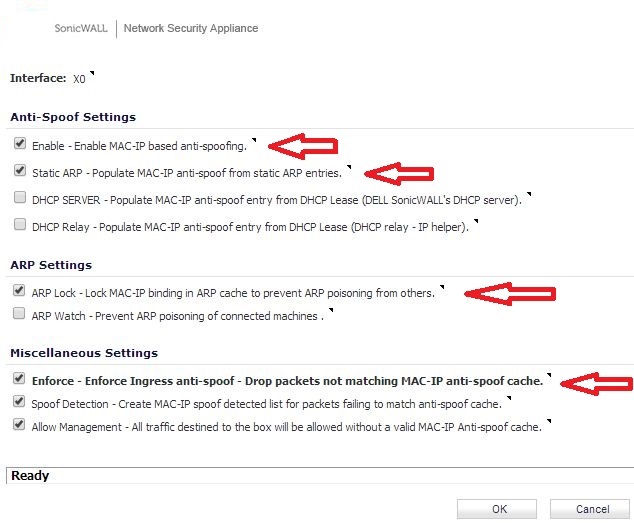
Note: Once ARP Lock and Enforce Ingress anti-spoof options are enabled SonicWall firewall will check the static ARP entries and load them in MAC-IP Anti-Spoof cache. Traffic from any other MAC address and IP address combination would be dropped.
How to Test:
If another machine whose MAC address is not listed in the cache would try to communicate through firewall , it would be dropped as shown below:

Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO