-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How To Perform a Packet Capture Based on OSI Layer 7 Application



Description
This article explains how can packet capture be performed for specific protocol. General packet capture utility is very useful for troubleshooting purpose.
But there are some limitations where packet can be captured based on either port no. or IP address only but not application layer protocols.
Using Application firewall packet capture can be performed based on layer 7 protocols.
A application firewall rule can be created to be matched and perform packet capture. This article explains capture for SIP traffic. However same can be replicated using any other protocol using app control advance signatures or customer objects.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
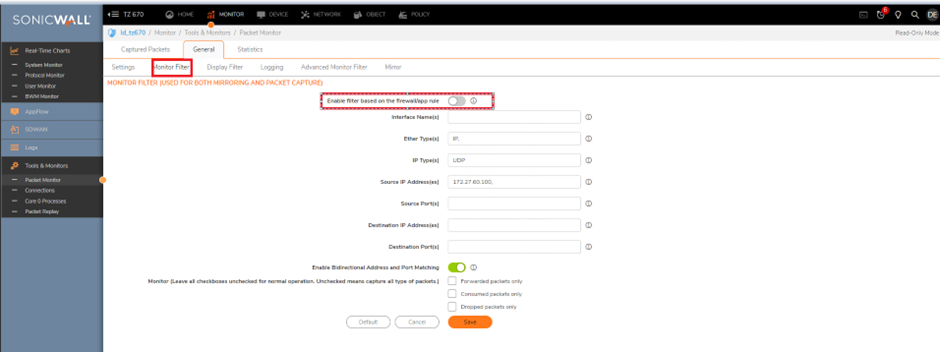
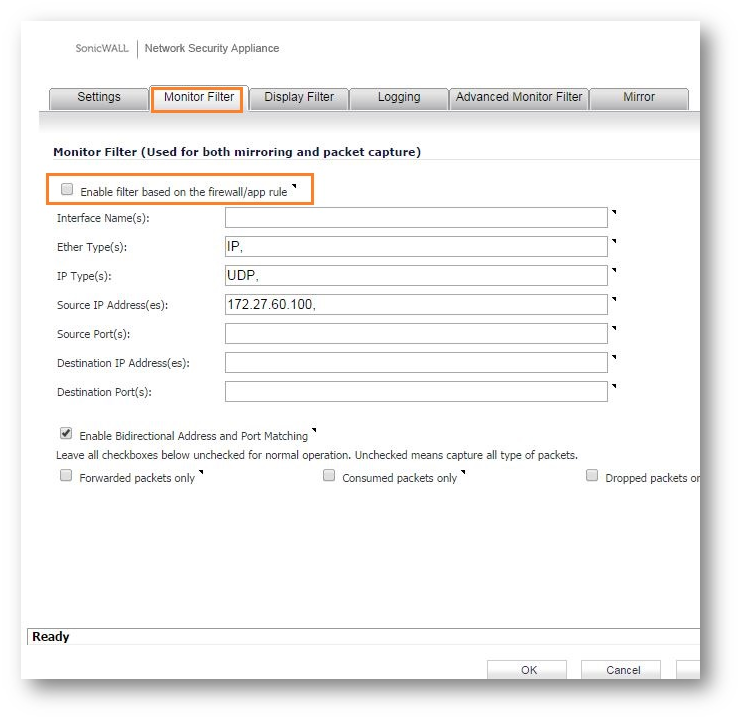
Step 1: Navigate to the Packet Monitor page via Monitor | Tools & Monitor | Packet Monitor and select "Configure". Navigate to "Monitor Filter" and select "Enable firewall based on the firewall/app rule"
NOTE: Remember to Uncheck the option in case doing capture with IP/port generic way as until the "Enable firewall based on the firewall/app rule" option is checked , the Packet monitor will not capture anything that is defined in monitor filter.
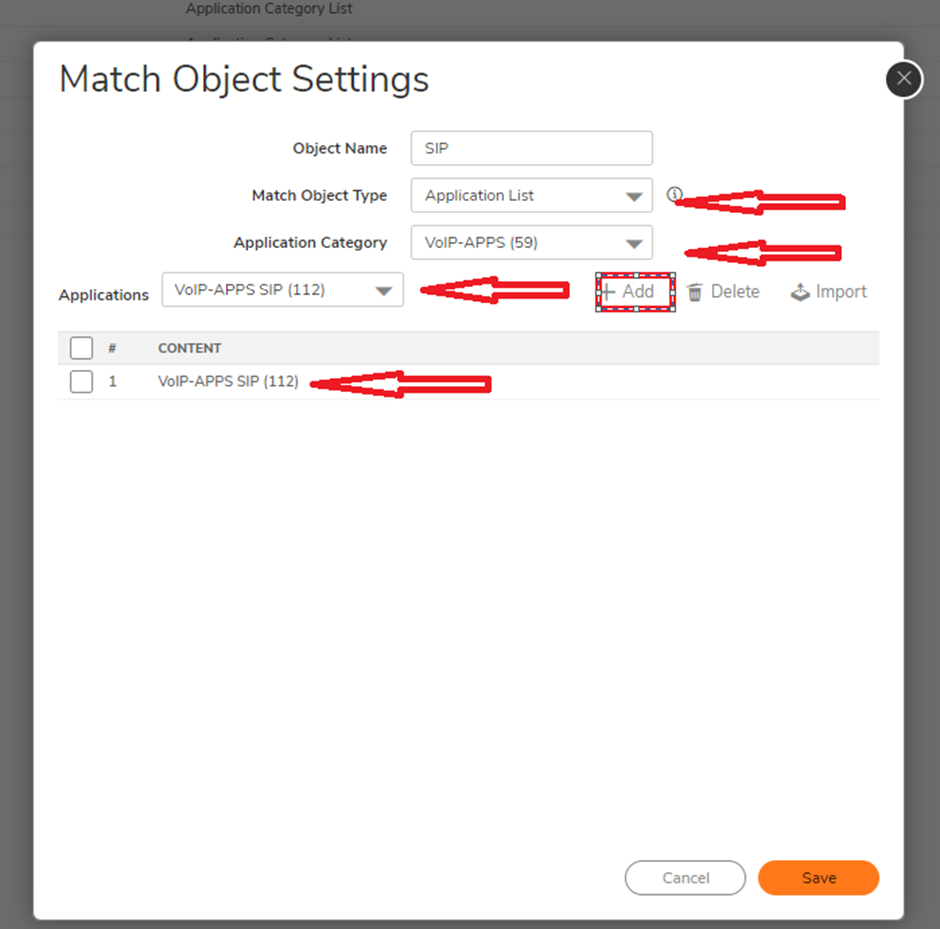
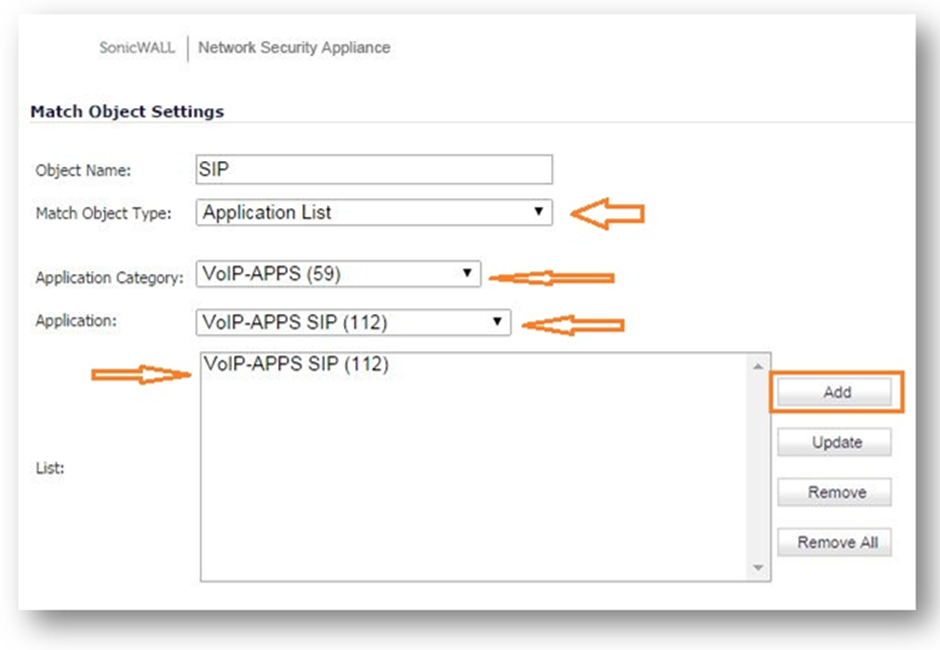
Step 2: Create a match object for SIP protocol.
Navigate to Object | Match object. Click on add and select match object type as "Application list".
Select VOIP-Apps and VOIP-SIP as applications.
As mentioned above this article takes VoIP-sip as an example and any of the pre-defined signatures and applications can be selected.
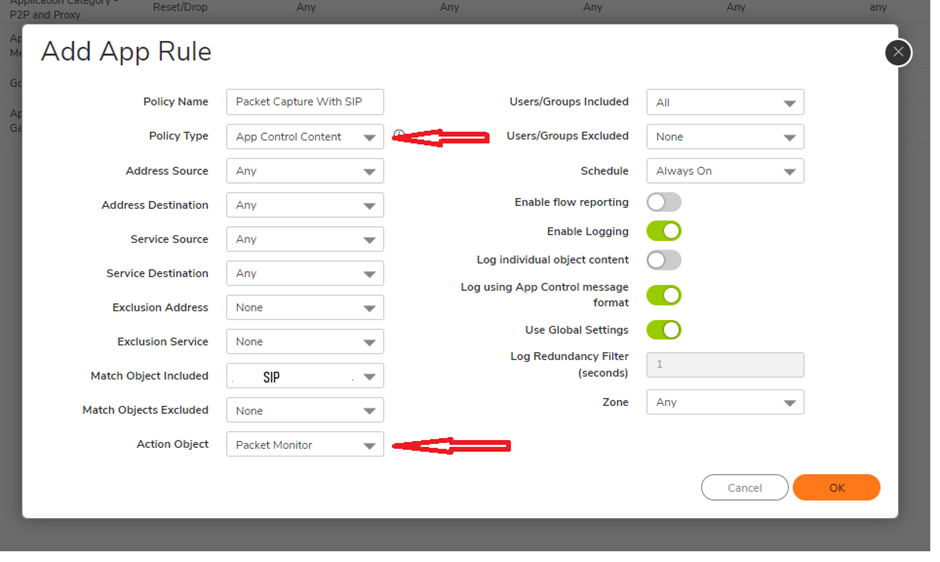
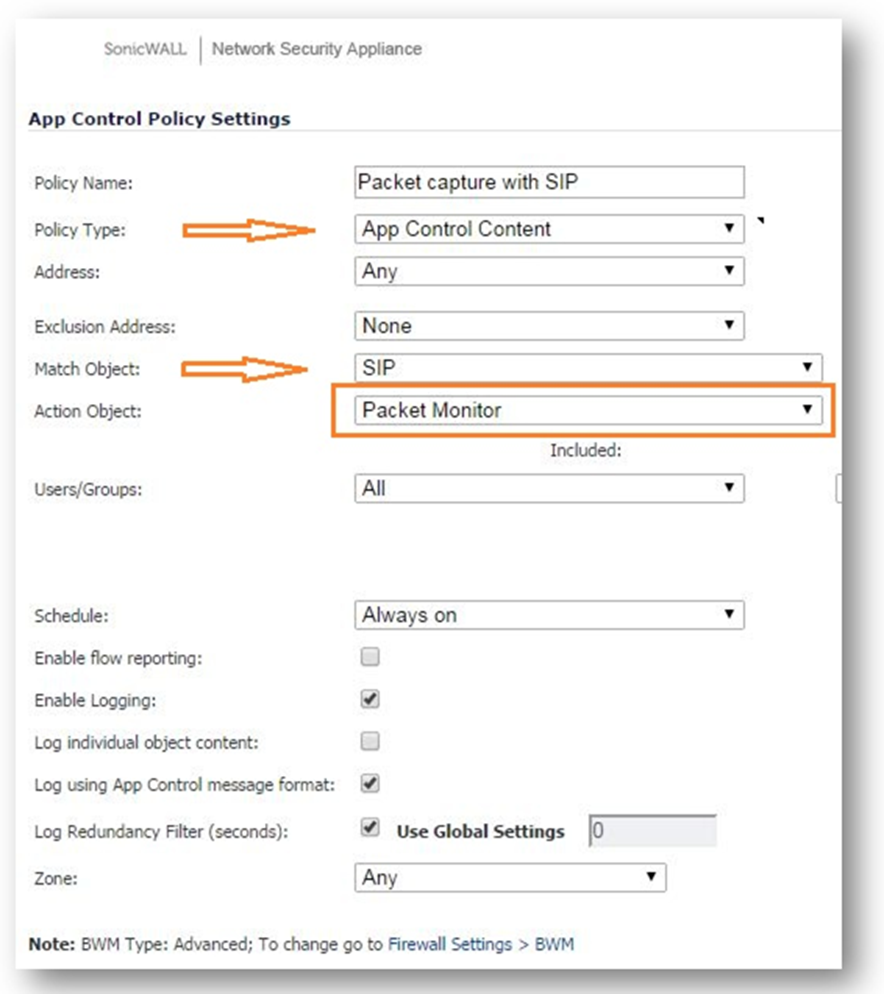
Step 3: Create an application firewall rule.
Navigate to Policy | App rule
Click on add a new rule. Select the type as App control content and select match object "SIP".
Action object should be selected as Packet monitor.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
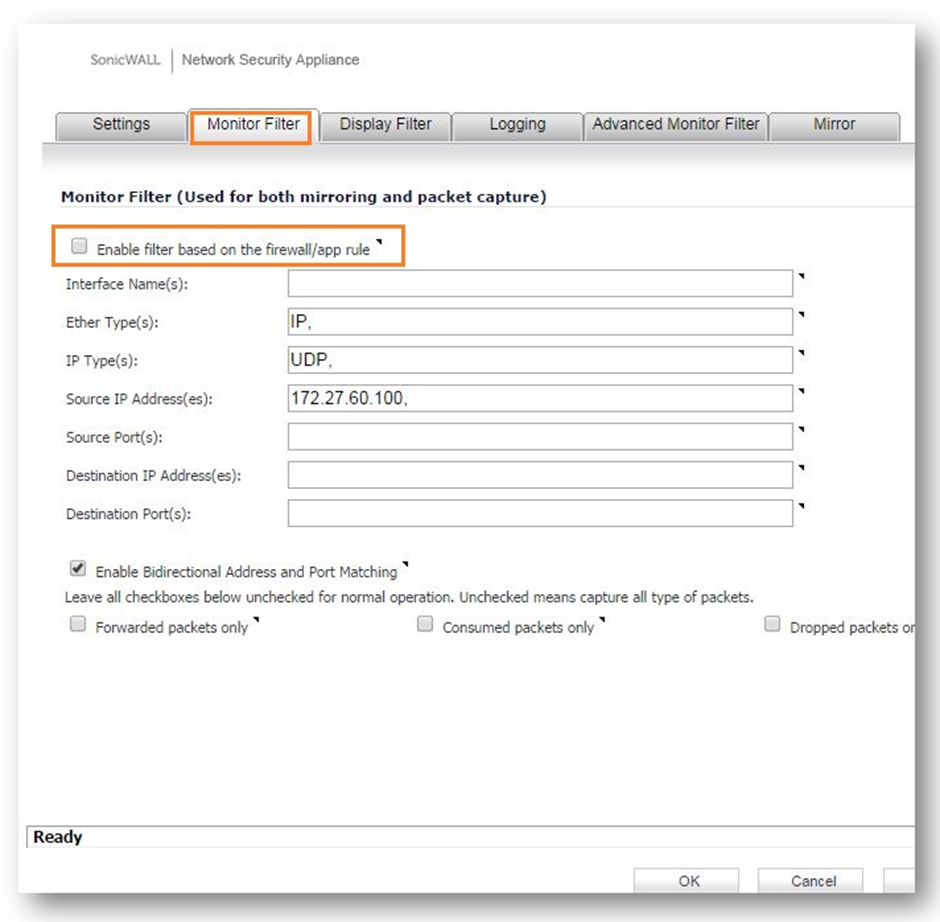
Step 1: Navigate to the Packet Monitor page via Investigate | Packet Monitor and select "Configure". Navigate to "Monitor Filter" and select "Enable firewall based on the firewall/app rule"
NOTE: Remember to Uncheck the option in case doing capture with IP/port generic way as until the "Enable firewall based on the firewall/app rule" option is checked , the Packet monitor will not capture anything that is defined in monitor filter.
Step 2: Create an match object for SIP protocol.
Navigate to Manage | Object | Match object. Click on add and select match object type as "Application list".
Select VOIP-Apps and VOIP-SIP as application.
As mentioned above this article takes VoIP-sip as an example and any of the pre-defined signatures and applications can be selected.
Step 3: Create an application firewall rule.
Navigate to Manage | Rules | App rule
Click on add a new rule. Select the type as App control content and select match object "SIP".
Action object should be selected as Packet monitor.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Step 1: Navigate to the Packet Monitor page via System | Packet Monitor and select "Configure". Navigate to "Monitor Filter" and select "Enable firewall based on the firewall/app rule"
 NOTE: Remember to Uncheck the option in case doing capture with IP/port generic way as until the "Enable firewall based on the firewall/app rule" option is checked ,Packet monitor will not capture anything that is defined in monitor filter.
NOTE: Remember to Uncheck the option in case doing capture with IP/port generic way as until the "Enable firewall based on the firewall/app rule" option is checked ,Packet monitor will not capture anything that is defined in monitor filter.
Step 2: Create an match object for SIP protocol.
Navigate to Firewall | Match object. Click on add and select match object type as "Application list".
Select VOIP-Apps and VOIP-SIP as application.
As mentioned above this article takes VoIP-sip as an example and any of pre-defined signatures and applications can be selected.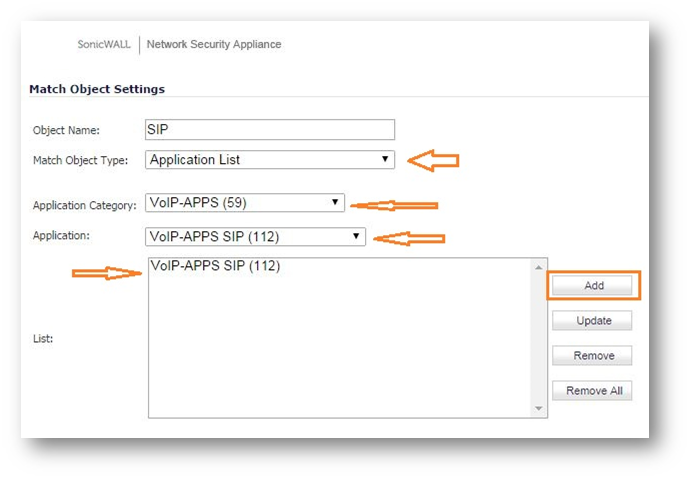
Step 3: Create an application firewall rule.
Navigate to Firewall | App rule
Click on add a new rule. Select the type as App control content and select match object "SIP".
Action object should be selected as Packet monitor.
How to Test:-
Start the packet capture and initiate SIP traffic. Relevant capture would start flowing.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO