-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to open ports for a server on the other side of a VPN



Description
Manually opening Ports from Internet to a server behind the remote firewall which is accessible through Site to Site VPN involves the following steps to be done on the local SonicWall.
Resolution
Step 1: Creating the necessary Address Objects
Step 2: Defining the NAT Policy.
Step 3: Creating the necessary WAN | Zone Access Rules for public access.
The following example covers allowing RDP (Terminal services) from the Internet to a server located in Site B with private IP address as 192.168.1.5. Once the configuration is complete, Internet users can access the server behind Site B SonicWall UTM appliance through the Site A WAN (Public) IP address 1.1.1.3.

Procedure:
Step 1: Creating the necessary Address objects
1. Select Network | Address Objects.
2. Click on Add button and create two address objects one for Server IP on VPN and another for Public IP of the server:

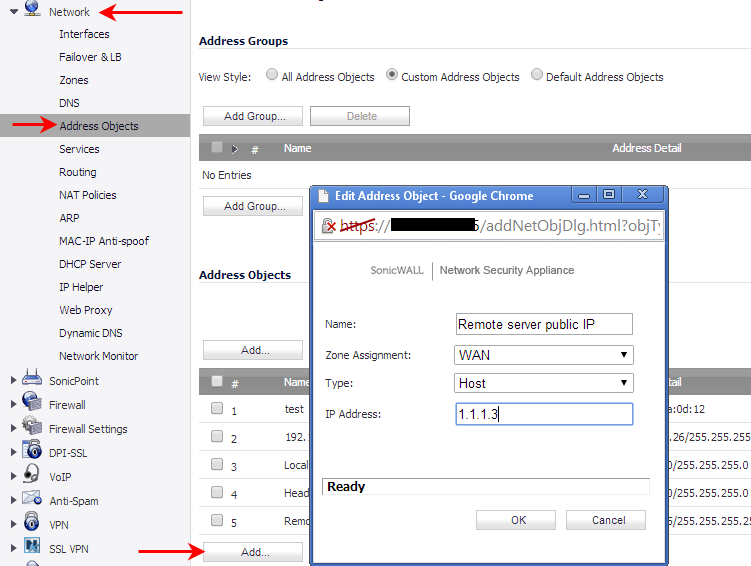
Step 2: Defining the NAT policy.
1. Select Network | NAT Policies.
2. Click the Add a new NAT Policy button and choose the following settings from the drop-down menu:
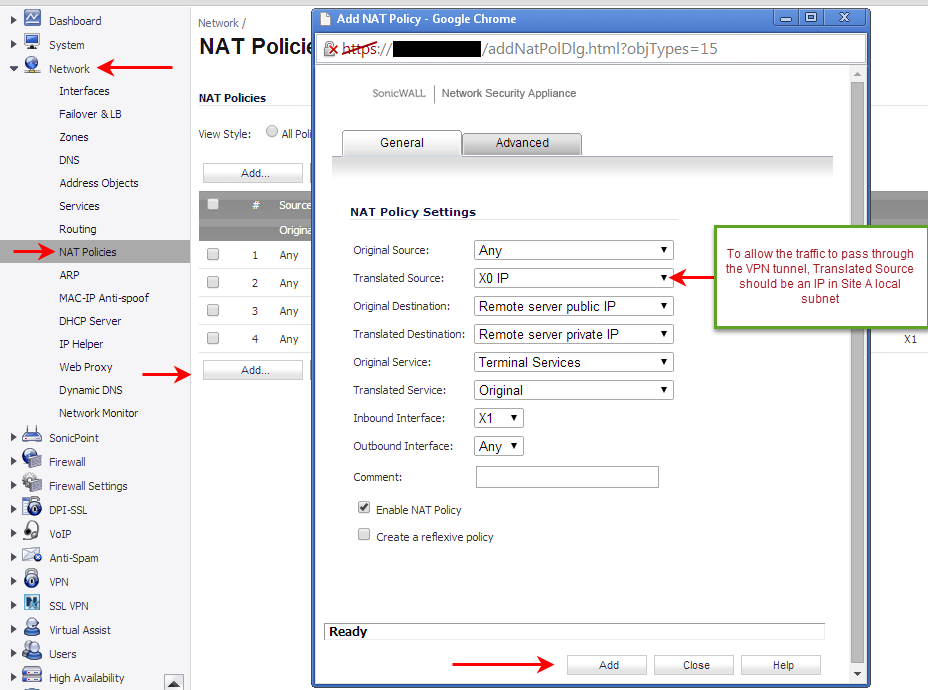
The VPN tunnel is established between 192.168.20.0/24 and 192.168.1.0/24 networks. To route this traffic through the VPN tunnel, the local SonicWall UTM device should translate the outside public IP address to a unused or its own IP address in LAN subnet as shown in the above NAT policy.
Step 3: Creating Firewall access rules.
1. Click Firewall | Access Rules tab.
2. Select the type of view in the View Style section and go to WAN to VPN access rules.
3. Click Add and create the rule by entering the following into the fields:
 Caution: The ability to define network access rules is a very powerful tool. Using custom access rules can disable firewall protection or block all access to the Internet. Use caution when creating or deleting network access rules.
Caution: The ability to define network access rules is a very powerful tool. Using custom access rules can disable firewall protection or block all access to the Internet. Use caution when creating or deleting network access rules.
4. Under the Advanced tab, you can leave the “Inactivity Timeout in Minutes” at 15 minutes. Some protocols, such as Telnet, FTP, SSH, VNC and RDP can take advantage of longer timeouts where increased
5: Click OK.
How to Test:
Testing from within the private network: Try to access the server through its private IP address using “Remote Desktop Connection” to ensure it is working from within the private network itself.
Testing from Site A: Try to access the server using “Remote Desktop Connection” from a computer in Site A to ensure it is accessible through the VPN tunnel.
Testing from the Internet: Login to a remote computer on the Internet and try to access the server by entering the public IP 1.1.1.3 using “remote Desktop Connection”.
Troubleshooting:
Ensure that the Server's Default Gateway IP address is Site B SonicWALL's LAN IP address.
Ensure that the server is able to access the computers in Site A.
Make use of Logs and Sonicwall packet capture tools to isolate the problem.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO