-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to fix the error "SSH Protocol Version 1 Session Key Retrieval"



Description
PCI scan of the SonicWall UTM appliance reports the following vulnerability: "SSH Protocol Version 1 Session Key Retrieval".
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
SonicWall UTM appliances uses SSH1 along with SSH2 and as of now we cannot disable SSH1 alone. But this vulnerability can be remedied using one of the following resolutions.
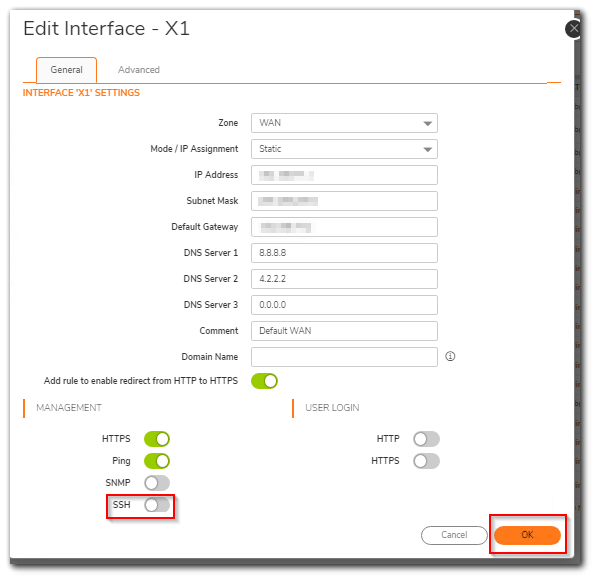
Resolution1: Disable SSH on the WAN interfaces.
Step 1: Click Network|System|Interfaces. Click Configure icon on the Wan interface.
![]()
Step 2: Disable SSH management and click OK.
Resolution 2: Allow SSH management access only from specific trusted source IP Addresses.
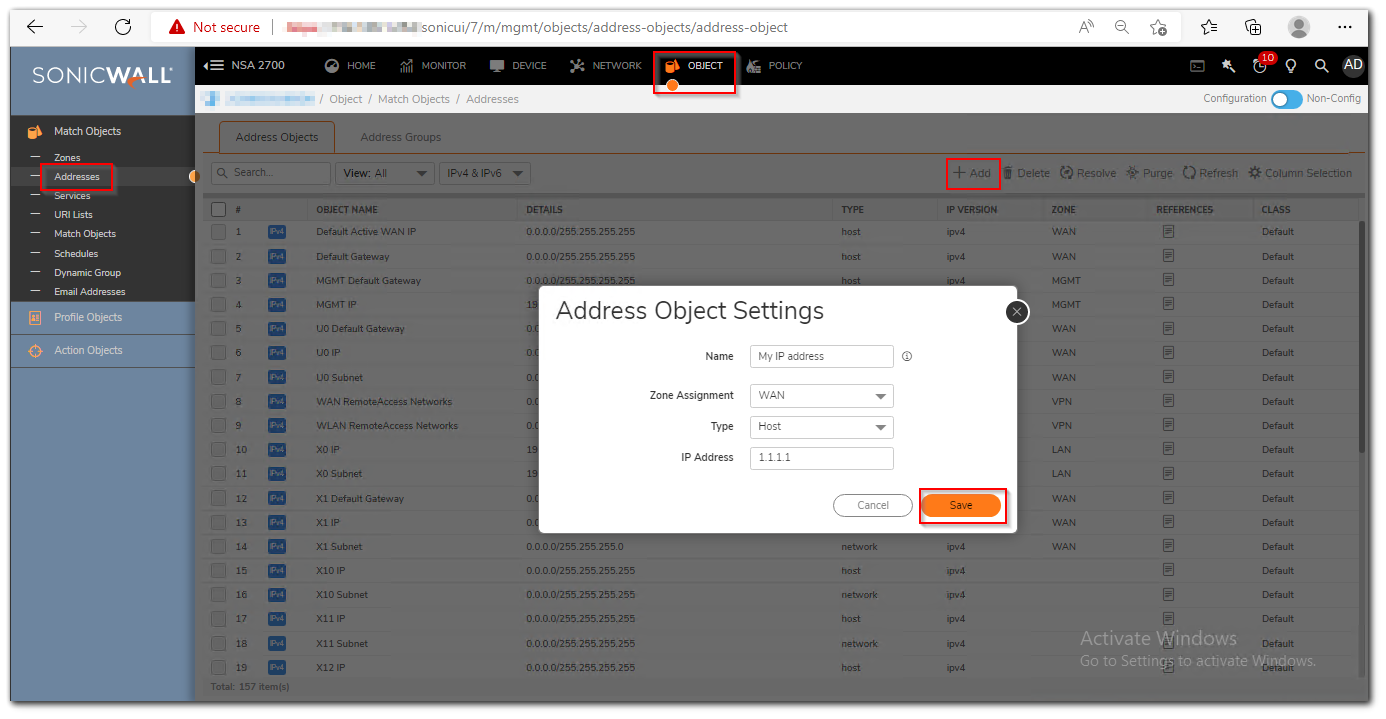
Step1: Click Object in the top navigation menu. Go to Match Objects | Addresses and click Add under address objects.
Step2: Enter the name for the object and enter the IP address of the computer from where you are trying to take SSH session. Select the zone as WAN.
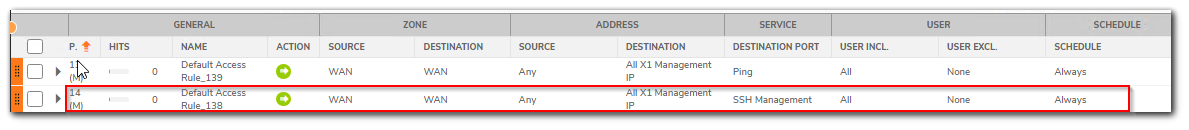
Step3: Go to Policy | Rules and Policies | Access Rules and select WAN > WAN rule. You can see the SSH management rule.
Step4: Edit the rule and select "My IP address" from the drop down list.
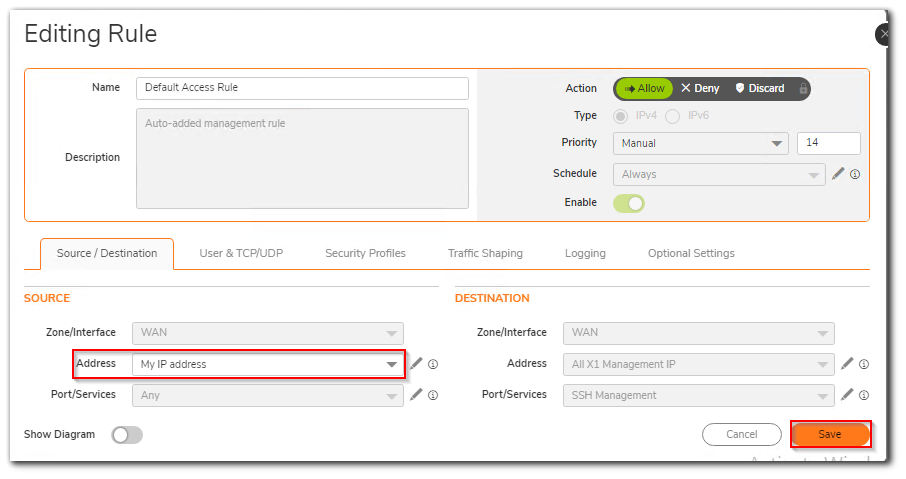
Note: If you want to allow multiple IP addresses, you need to create address objects and group them together in a address group. Then select the address group in the source of access rule.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
SonicWall UTM appliances uses SSH1 along with SSH2 and as of now we cannot disable SSH1 alone. But this vulnerability can be remedied using one of the following resolutions.
Resolution1: Disable SSH on the WAN interfaces.
Step 1: Click Manage in the top navigation menu. Go to Network | Iinterfaces. Click Configure icon on the WAN interface.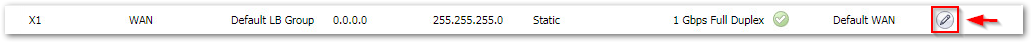
Step 2: Disable SSH management and click OK.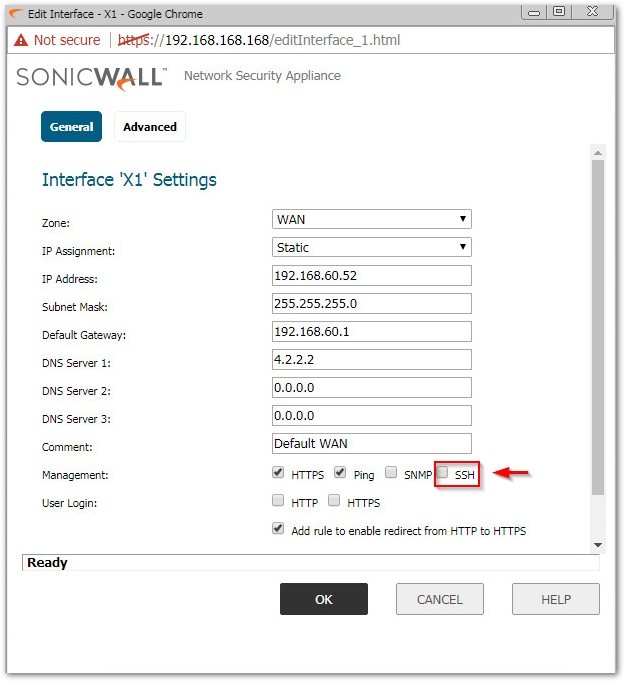
Resolution 2: Allow SSH management access only from specific trusted source IP Addresses.
Step1: Click Manage in the top navigation menu. Go to Objects | Address Objects and click Add under address objects.
Step2: Enter the name for the object and enter the IP address of the computer from where you are trying to take SSH session. Select the zone as WAN. 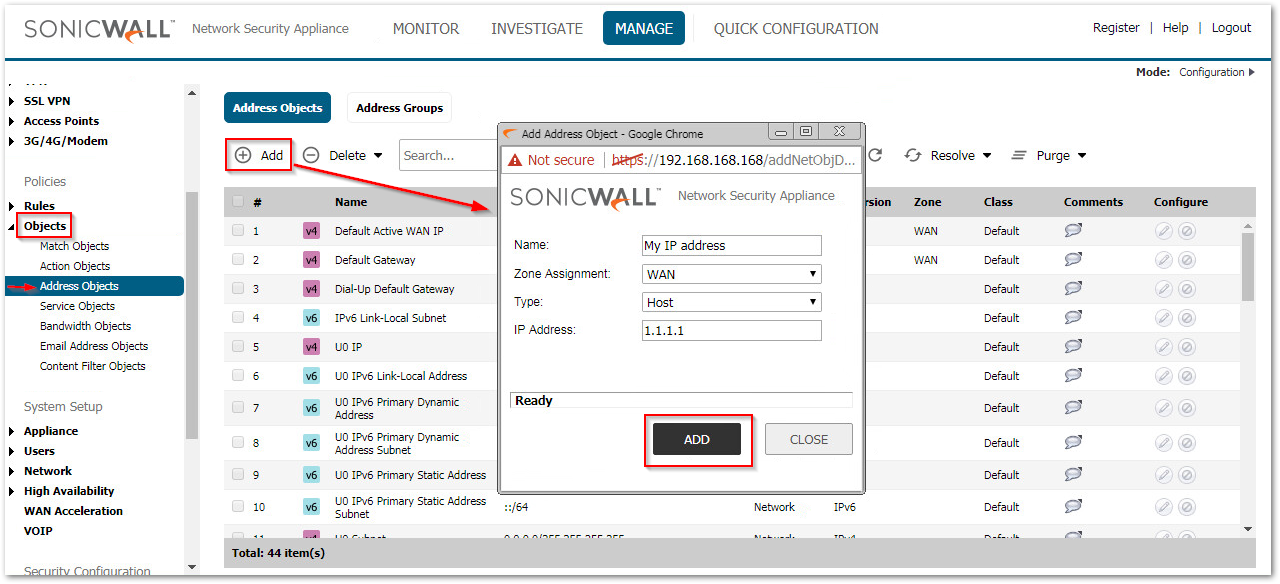
Step3: Go to Rules | AcceSS Rules and select WAN > WAN rule. You can see the SSH management rule.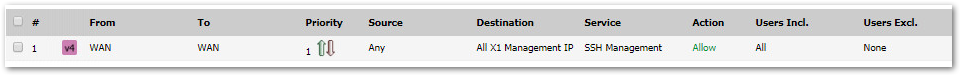
Step4: Edit the rule and select "My IP address" from the drop down list.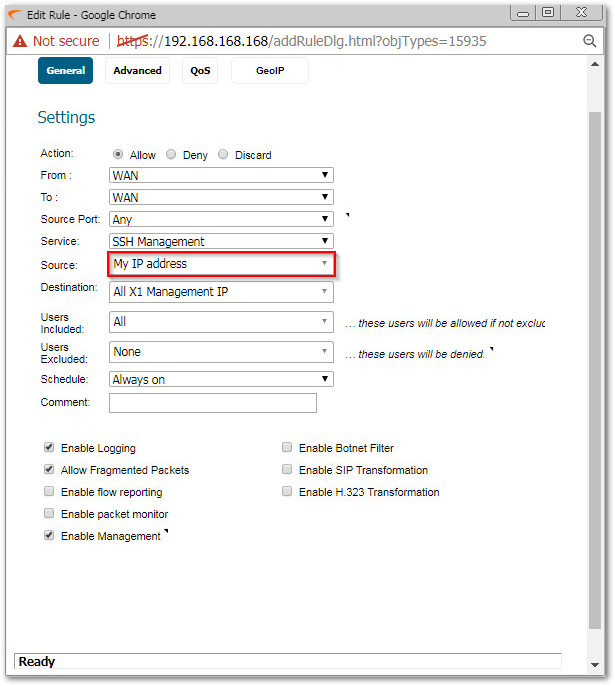
Note: If you want to allow multiple IP addresses, you need to create address objects and group them together in a address group. Then select the address group in the source of access rule.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
SonicWall UTM appliances uses SSH1 along with SSH2 and as of now we cannot disable SSH1 alone. But this vulnerability can be remedied using one of the following resolutions.
Resolution1: Disable SSH on the WAN interfaces.
Step 1: Goto Network | Iinterface. Click Configure icon on the WAN interface.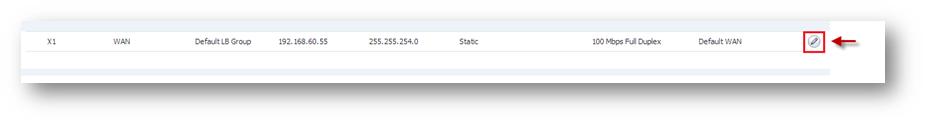
Step 2: Disable SSH management and click OK.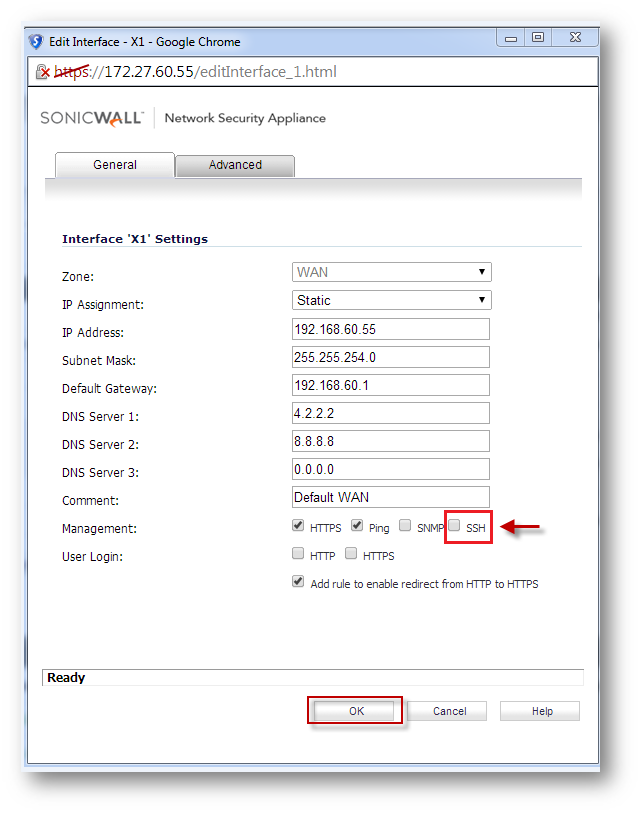
Resolution 2: Allow SSH management access only from specific trusted source IP Addresses.
Step1: Go to Firewall | Address Objectt and click Add under address objects.
Step2: Enter the name for the object and enter the IP address of the computer from where you are trying to take SSH session. Select the zone as WAN.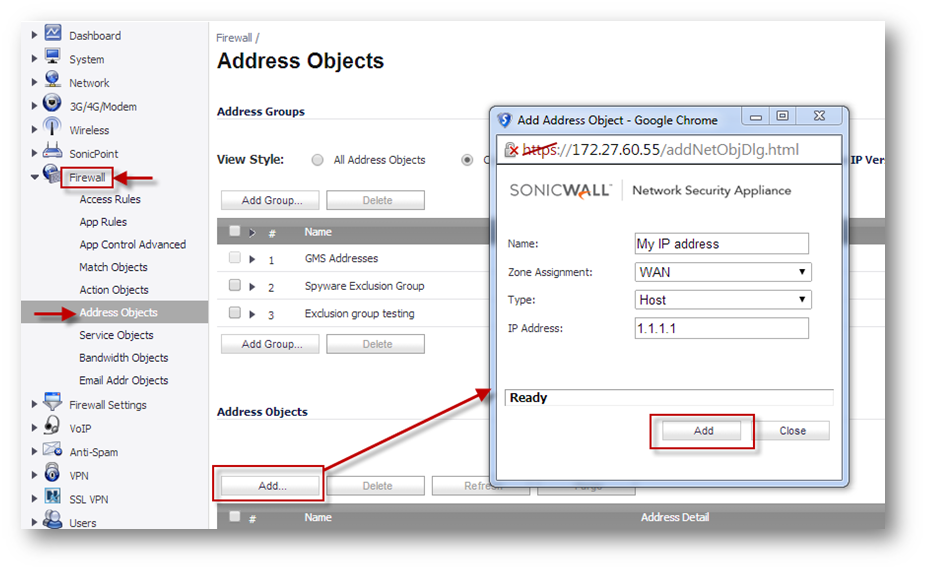
Step3: Goto Firewall | AcceSS Rule and select WAN > WAN rule. You can see the SSH management rule.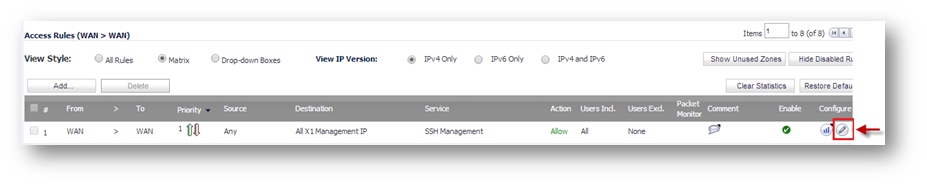
Step4: Edit the rule and select "My IP address" from the drop down list.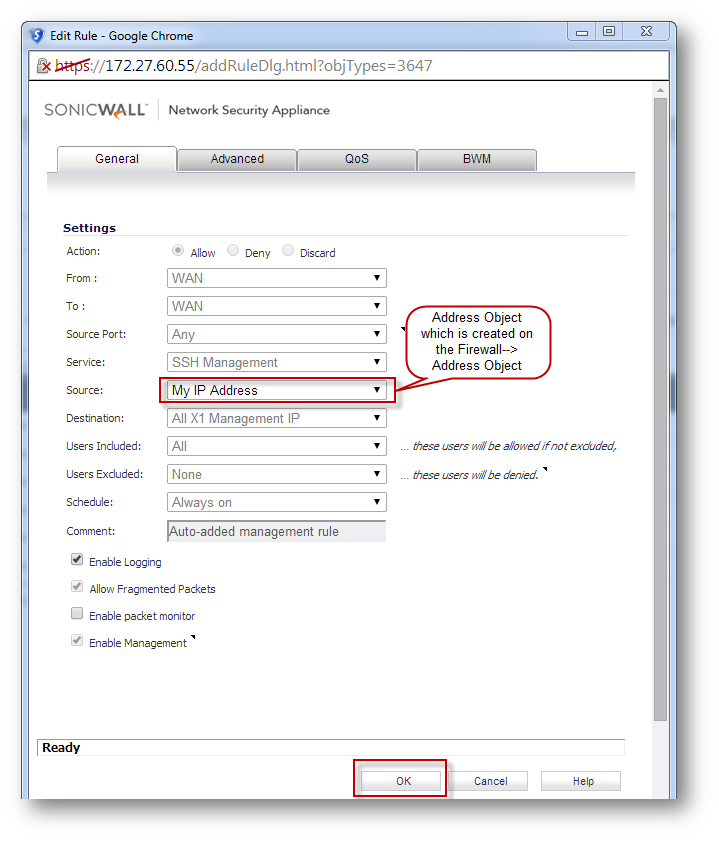
Note: If you want to allow multiple IP addresses, you need to create address objects and group them together in a address group. Then select the address group in the source of access rule.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall NSA Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall SuperMassive E10000 Series






 YES
YES NO
NO