-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to deploy SonicWall NSv High Availability using Azure Load balancers ?



Description
Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model or entrust Microsoft with all your computing and network needs with Infrastructure as a Service (IaaS).
Product Matrix 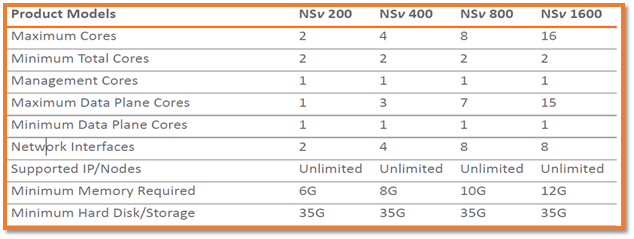
Topology
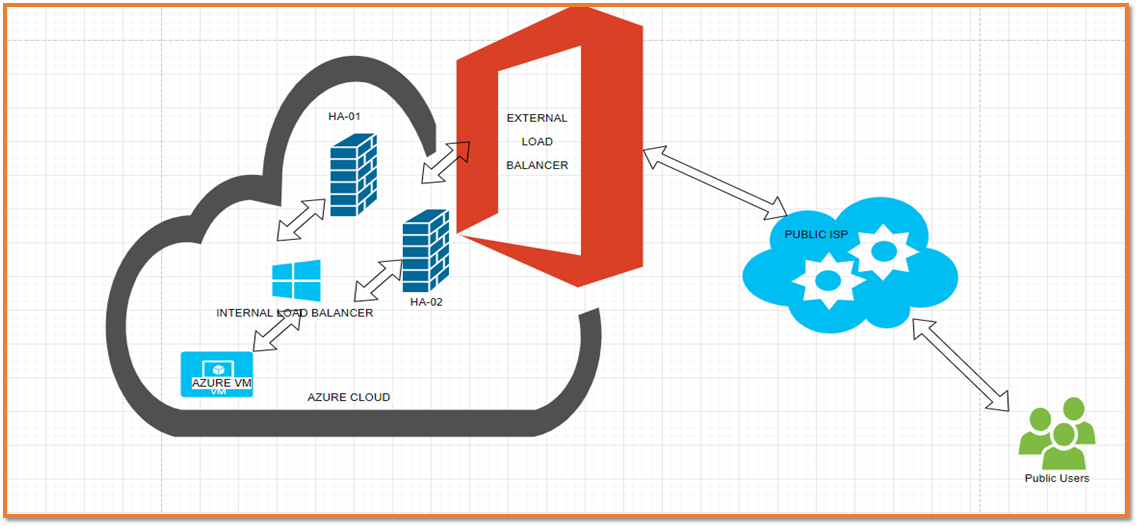
IP Addresses used in this article | ||
NSv_Azure_HA-01 | ||
VNET | 192.168.0.0/16 | |
VNET NAME | NSv_Azure_HA | |
WAN IP | X1 :192.168.1.4/24 | |
LAN IP | X0: 192.168.2.4/24 | |
IP Addresses used in this article | ||
NSv_Azure_HA-02 | ||
VNET | 192.168.0.0/16 | |
VNET NAME | NSv_Azure_HA | |
WAN IP | X1 :192.168.1.5/24 | |
LAN IP | X1 :192.168.2.5/24 | |
ELB IP | 40.80.226.218 | |
ILB IP | 192.168.2.6/24 | |
Resolution
Logging Azure Account
- Navigate to SonicWall NSv Azure Template using your Microsoft Azure Account.
- ARM template deployment, click Deploy to Azure.

Configure the following options:
- Resource group
- Location
- Storage Account
- VM Name
- Virtual Network Name
- Authentication type
- Virtual machine size
- Create Internal Load Balancer


 NOTE: The above configuration will deploy NSv_Azure_HA1, NSv_Azure_HA2 along with external Load balancer NSv_Azure_HA-ELB and internal Load balancer NSv_Azure_HA-ILB.
NOTE: The above configuration will deploy NSv_Azure_HA1, NSv_Azure_HA2 along with external Load balancer NSv_Azure_HA-ELB and internal Load balancer NSv_Azure_HA-ILB.
To find the associated Virtual NSv
- Navigate to Azure Home | Load balancers | ELB Load balancer | Backend Pools.
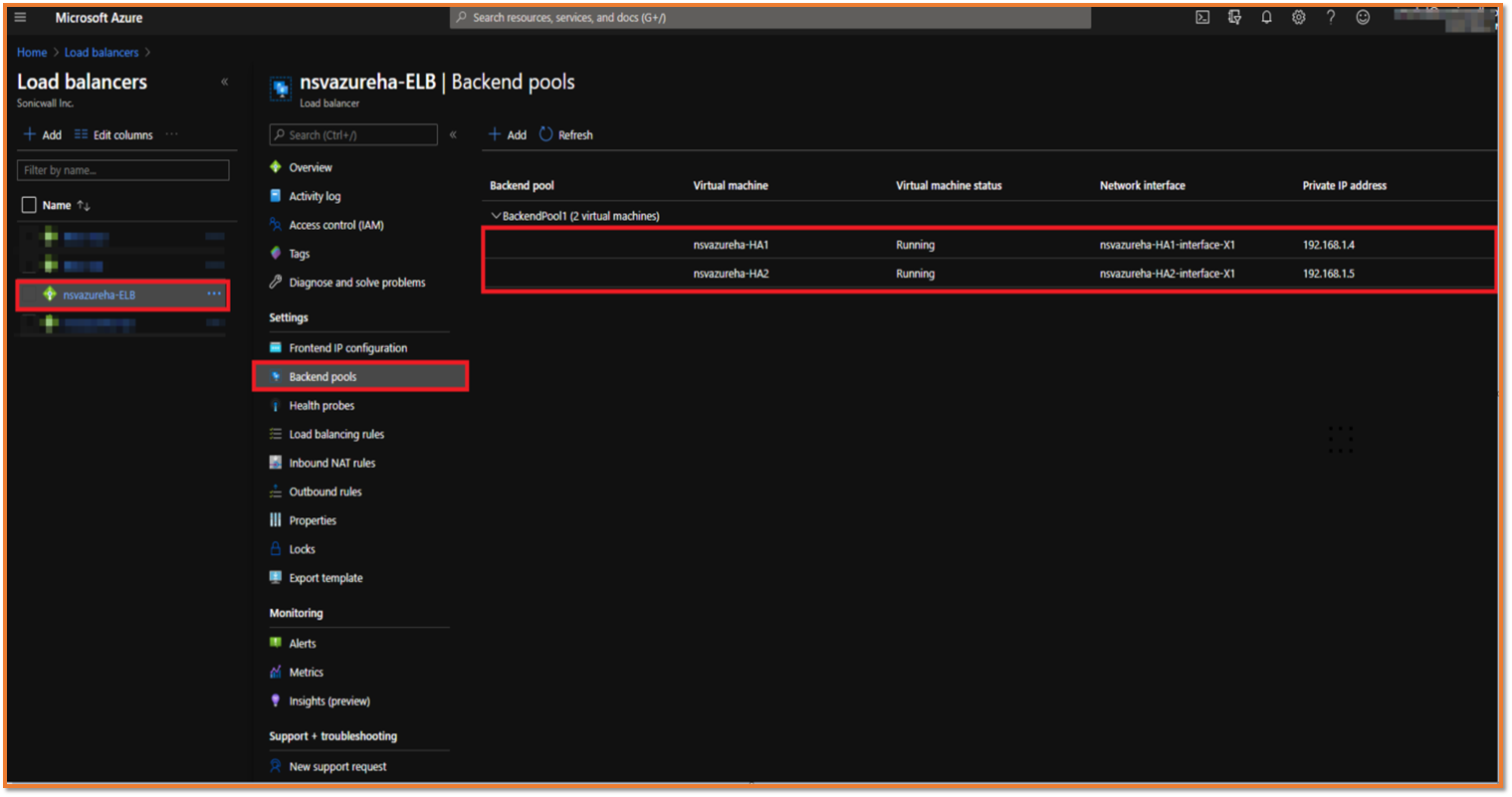
Configure the Load balancing rules to access the internal Virtual Machines from the public network
- Navigate to Azure Home | Load balancers | ELB Load balancer | Load balancing rules.


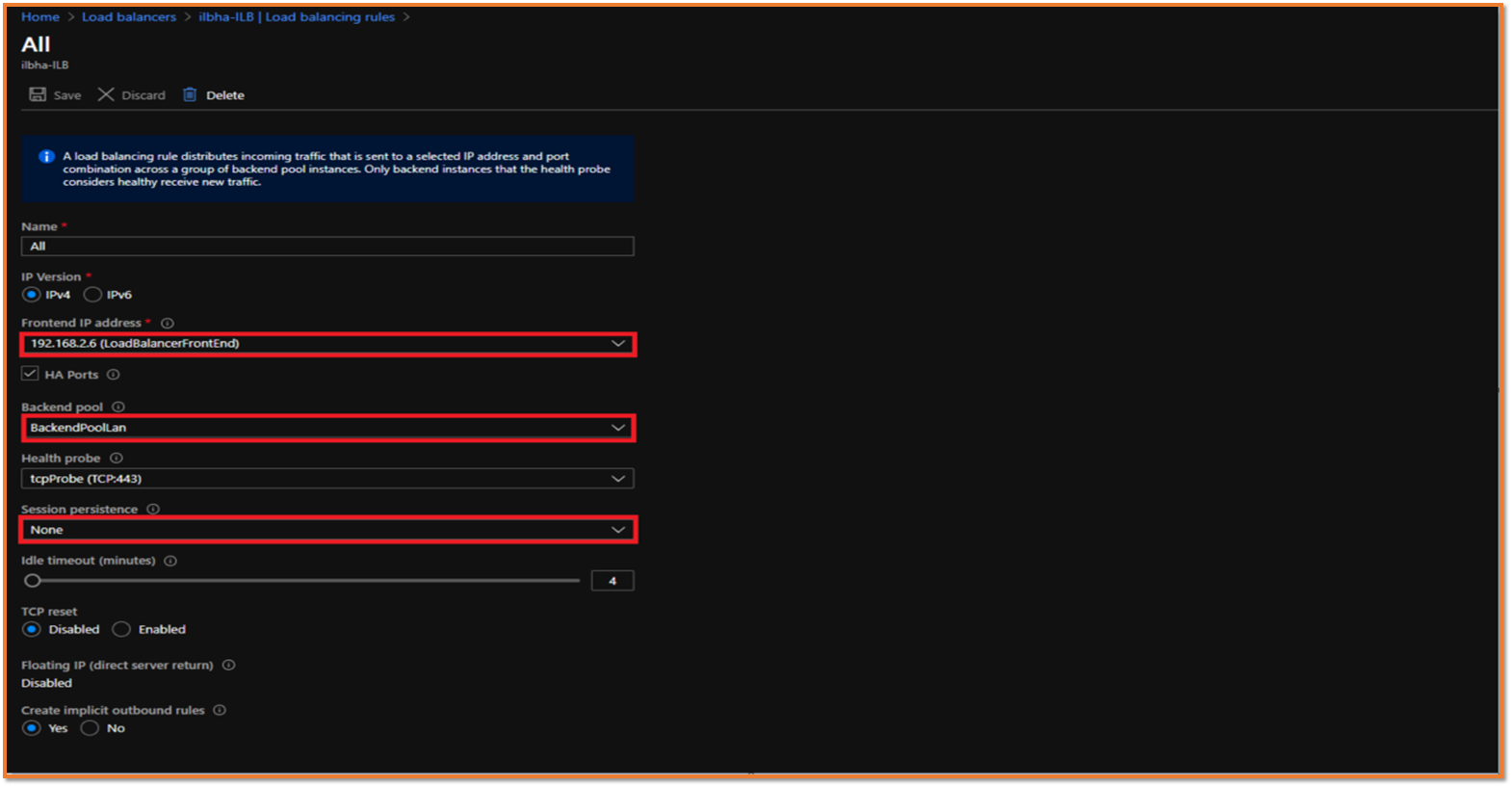
 TIP: Session persistence specifies that traffic from a client should be handled by the same virtual machine in the backend pool for the duration of a session. "None" specifies that successive requests from the same client may be handled by any virtual machine. "Client IP" specifies that successive requests from the same client IP address will be handled by the same virtual machine. "Client IP and protocol" specifies that successive requests from the same client IP address and protocol combination will be handled by the same virtual machine.
TIP: Session persistence specifies that traffic from a client should be handled by the same virtual machine in the backend pool for the duration of a session. "None" specifies that successive requests from the same client may be handled by any virtual machine. "Client IP" specifies that successive requests from the same client IP address will be handled by the same virtual machine. "Client IP and protocol" specifies that successive requests from the same client IP address and protocol combination will be handled by the same virtual machine. NOTE: Remote Desktop Service TCP port 3389 has been used for the Demo purpose.
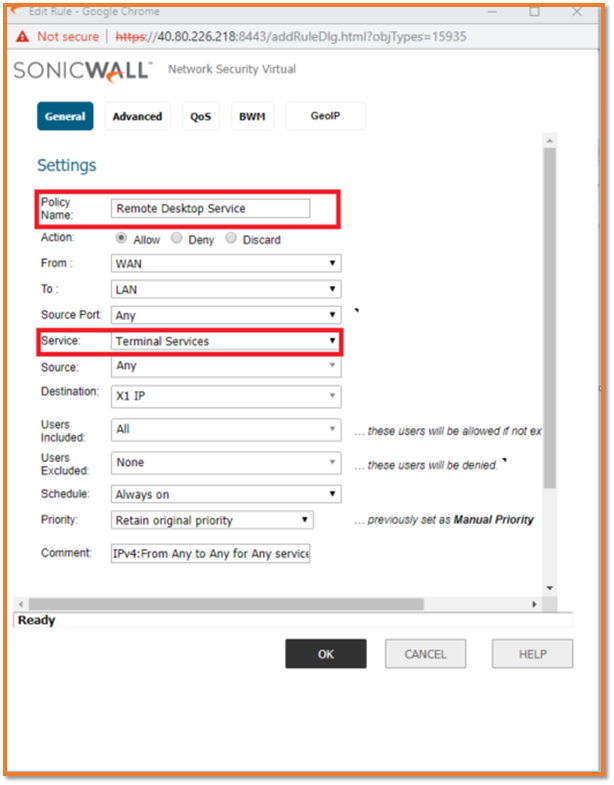
NOTE: Remote Desktop Service TCP port 3389 has been used for the Demo purpose.
To find the Inbound NSv GUI Access rule on port number 8443 and 8444
- Navigate to Azure Home | Load balancers | ELB Load balancer | Inbound NAT rules.
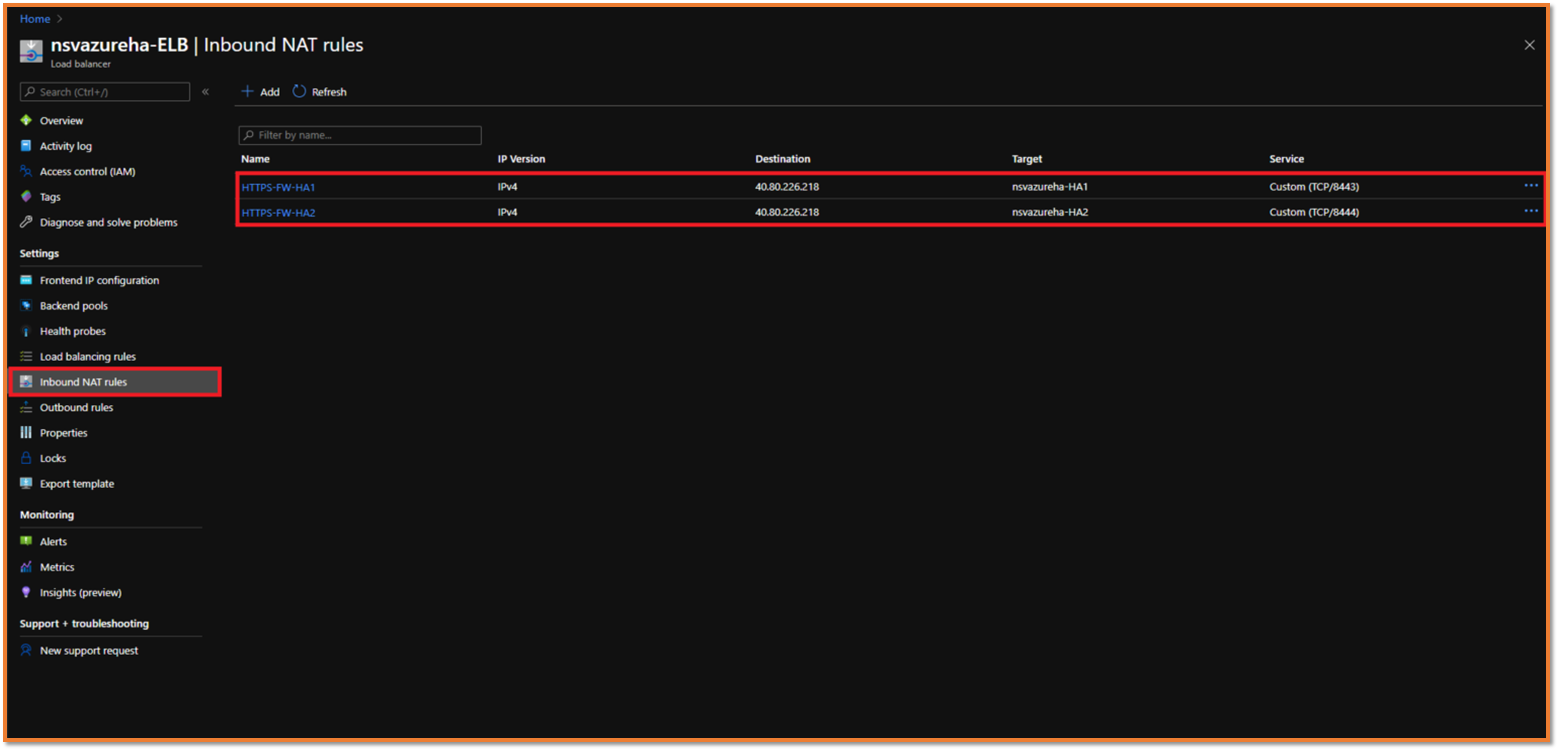
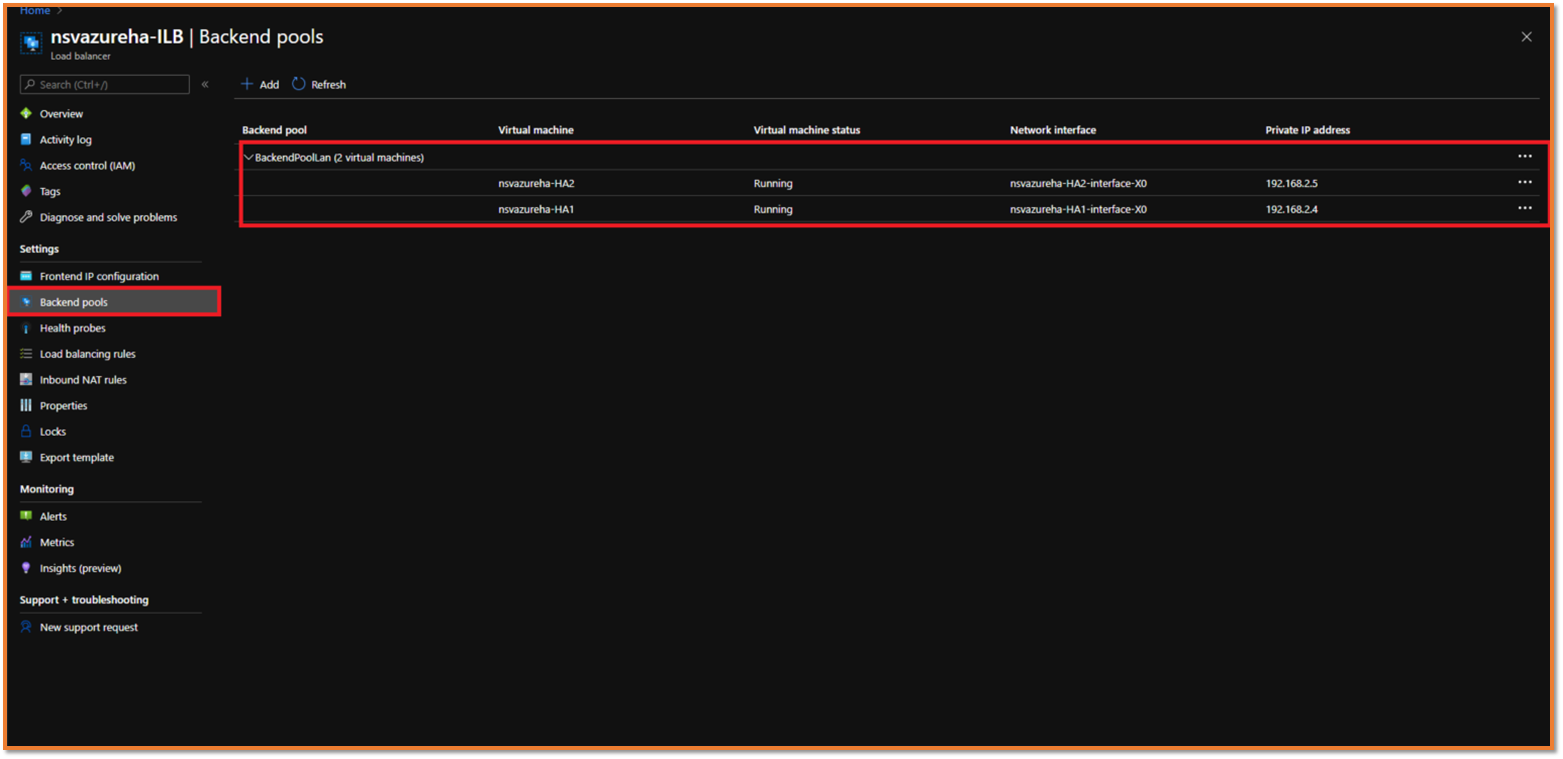
To find the associated Virtual NSv
- Navigate to Azure Home | Load balancers | ILB load balancer | Backend Pools.
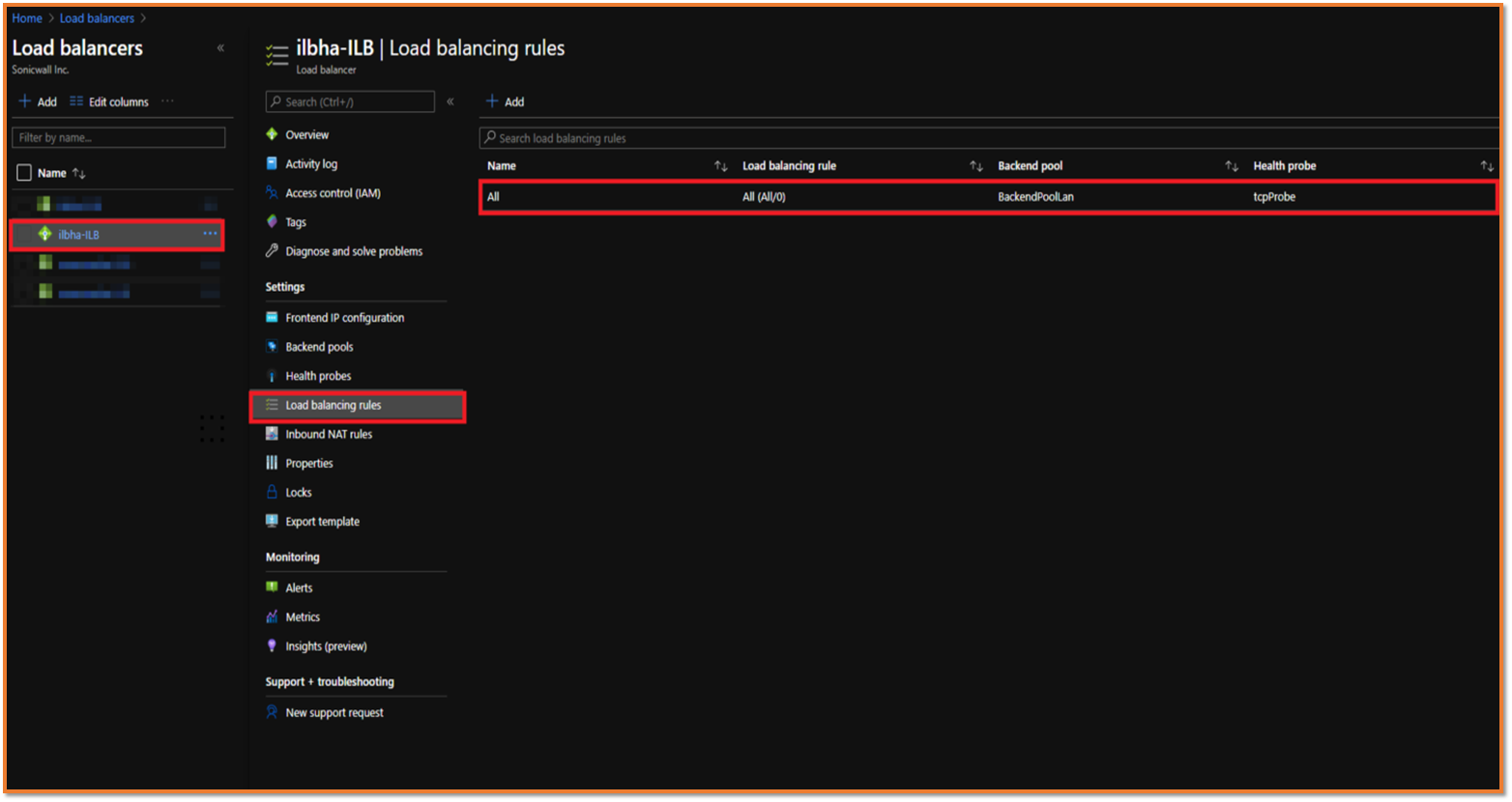
Configure the Load balancing rules to forward the internal Virtual Machines traffic through ILB
- Navigate to Azure Home | Load balancers | ILB Load balancer | Load balancing rules.
SonicWall Configuration Steps
Adding an access rule to allow interesting traffic
- Navigate to SonicWall NSv Firewall | Access Rule.
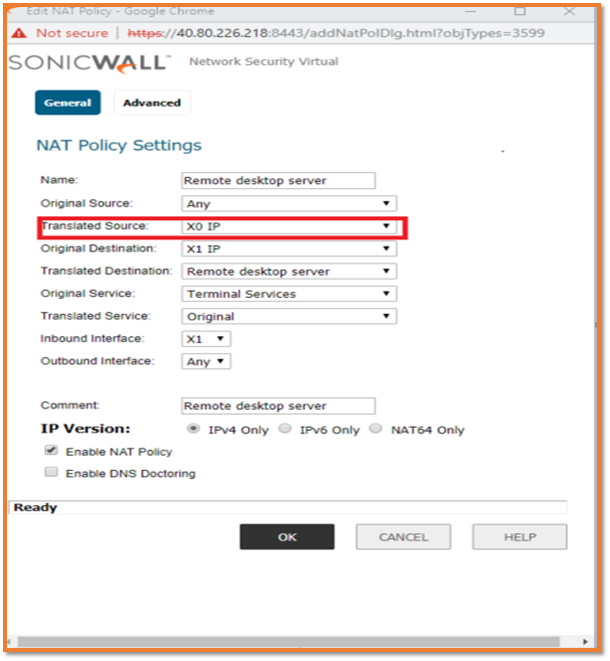
Adding a NAT ruleto allow interesting traffic and translating the source as X0 ip
- Navigate to Firewall | NAT Rule.
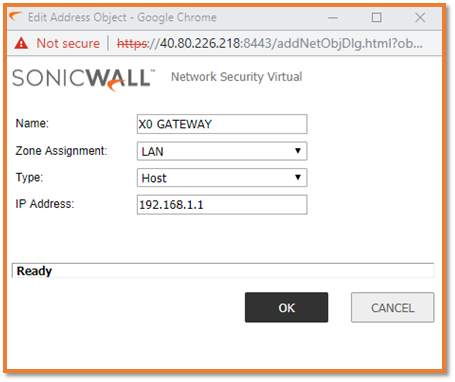
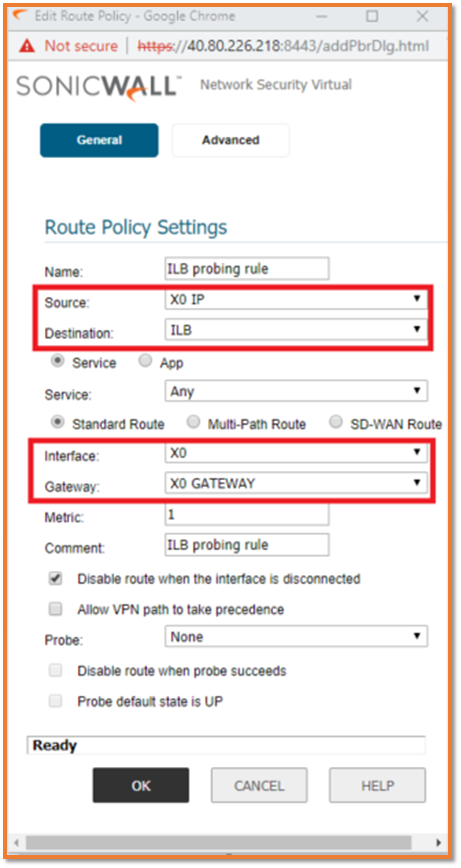
Adding a route rule replying to the Internal Load balancer probe on 443 port
- Navigate to Network| Routing.
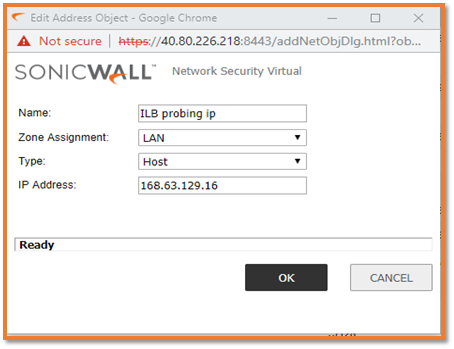
 CAUTION: Load Balancer uses a distributed probing service for its internal health model. Load Balancer health probes originate from the IP address 168.63.129.16 and must not be blocked for probes to mark up your instance. The above deployment is an Active/Active HA. Microsoft does not support L2 HA deployment and requires manually Sync by importing the .exp file every time from NSv_Azure_HA-01 to NSv_Azure_HA-02 or with the help of Cloud GMS.
CAUTION: Load Balancer uses a distributed probing service for its internal health model. Load Balancer health probes originate from the IP address 168.63.129.16 and must not be blocked for probes to mark up your instance. The above deployment is an Active/Active HA. Microsoft does not support L2 HA deployment and requires manually Sync by importing the .exp file every time from NSv_Azure_HA-01 to NSv_Azure_HA-02 or with the help of Cloud GMS.
 NOTE: The local hosted Virtual Subnets will not be accessed through the Public IP once the route table is created on Azure.
NOTE: The local hosted Virtual Subnets will not be accessed through the Public IP once the route table is created on Azure.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSv Series > Azure






 YES
YES NO
NO