-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to create a Decryption Policy in SonicOSX 7.0?



Description
Decryption policies are used to create groups of rules defining which traffic should be decrypted. This decision is based on match criteria such as source IPs and destination IPs. Each decryption policy can have its own match criteria, along with an associated action. Once the match is done, we can decide whether we need to decrypt or bypass.
In SonicOSX 7.0, the HTTPS content filtering is no longer present. So, if we want to allow HTTPS websites, we need Client DPI SSL and a corresponding decryption policy to inspect them.
Resolution
Decryption policy rules define what type of traffic needs to be decrypted. There are three types of rules that can be added, each with its own parameters that can be used for the match.
- DPI-SSL Client Rules
- DPI-SSL Server Rules
- DPI-SSH Rules
The match criteria for these rules can contain the following traffic parameters:
Client-side SSL Rules:
- Source IP address
- Destination IP address
- Destination service (port/IP type)
- User
- Websites
- Web category
- Geo location
- Schedule
Server-side SSL Rules:
- Source IP address
- Destination IP address
- Destination service (port/IP type)
- User
- Geo location
- Schedule
SSH Rules:
- Source IP address
- Destination IP address
- Destination service (port/IP type)
- User
- Geo location
- Schedule
Before we can create a decryption policy, these features should be enabled globally.
To Enable Client DPI-SSL:
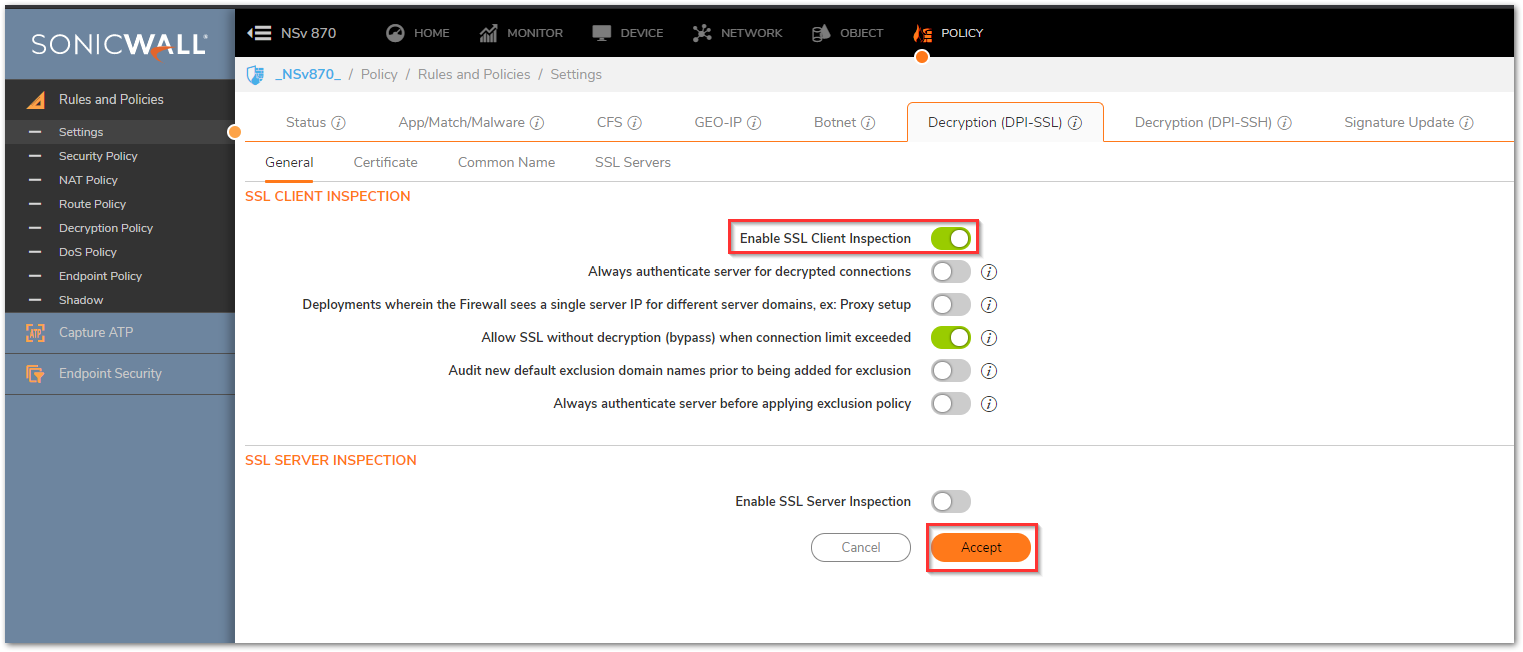
- Navigate to the Policy | Rules and Policies | Settings and Decryption (DPI-SSL) tab.
- Under the General tab, use the toggle button to enable SSL Client Inspection, then click Accept at the bottom.
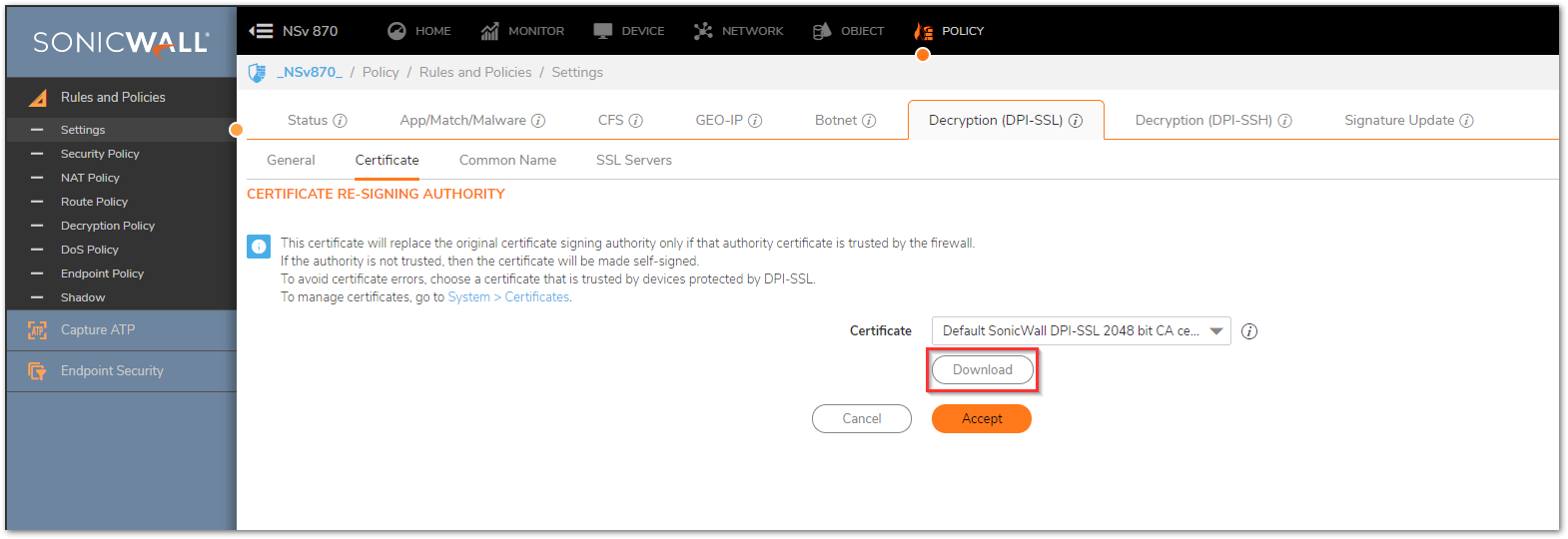
- The DPI-SSL certificate should be installed on all end user machines for which this decryption policy is being created. You can either install the certificates manually or use a group policy to push the certificates to all machines that are part of the domain. You can download the DPI-SSL certificate by navigating to Policy | Rules and Policies | Settings | Decryption (DPI-SSL) and selecting the Certificate tab.
To enable Server DPI-SSL:
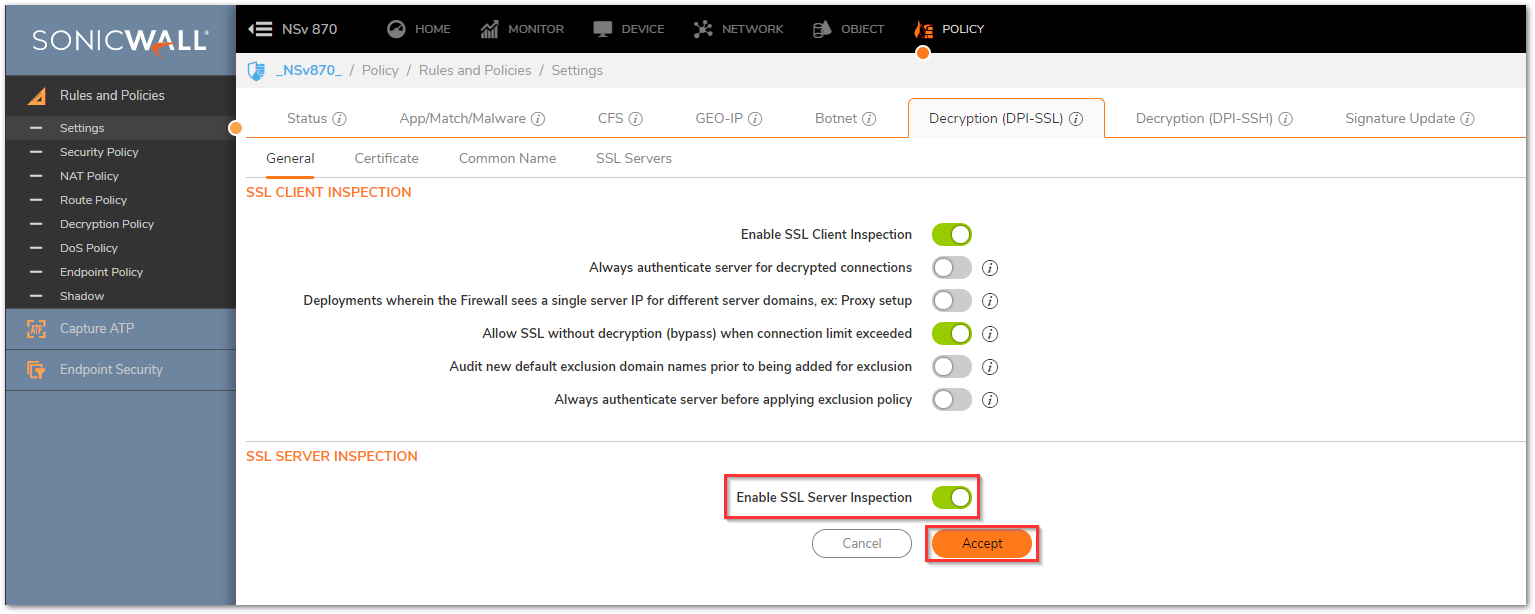
- Navigate to the Policy | Rules and Policies | Settings and Decryption (DPI-SSL) tab.
- Under the General tab, use the toggle button to turn on Enable SSL Server Inspection and then click Accept at the bottom.
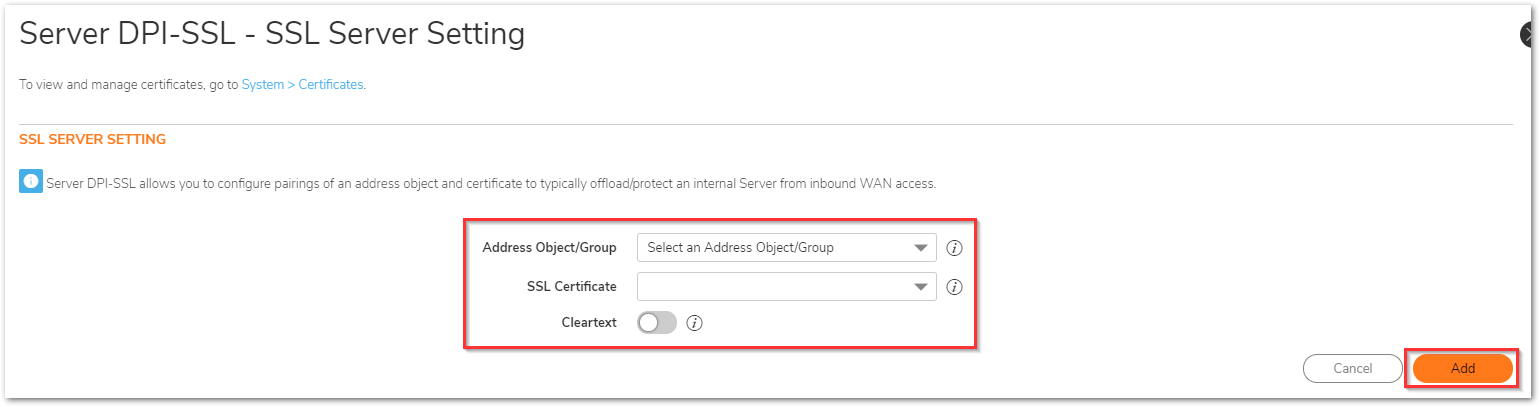
The certificate and the server address object can be added by navigating to the Policy | Rules and Policies | Settings | Decryption (DPI-SSL) tab, then selecting the SSL Servers tab. Click Add.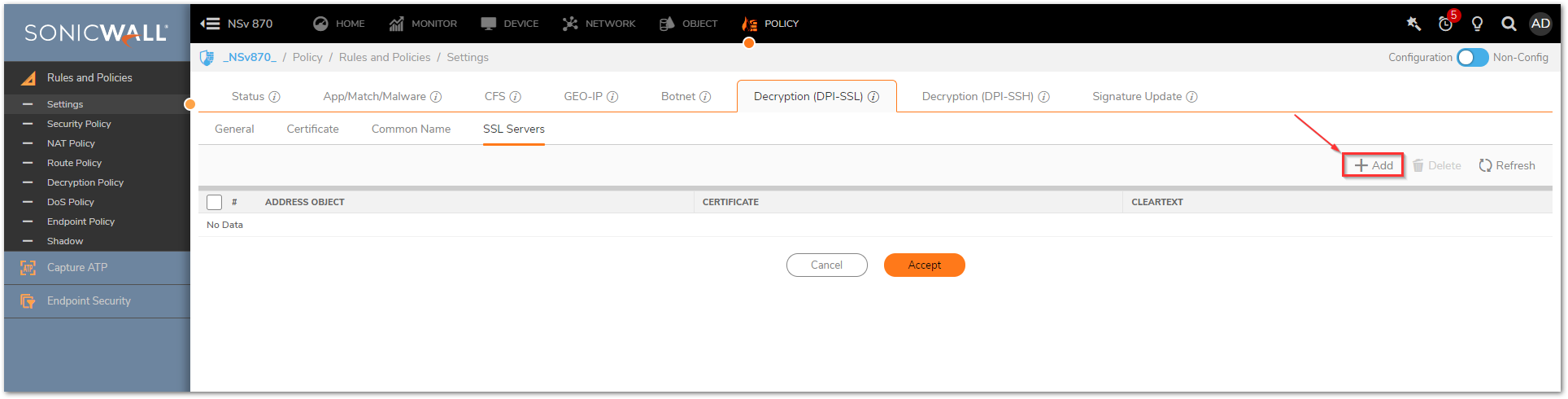
- The following options should be selected:
- In the Address Object/Group pulldown menu, select the address object or group for the server or servers you want to apply DPI-SSL inspection to.
- In the SSL Certificate pulldown menu, select the certificate that will be used to sign the traffic for the server.
- The cleartext option indicates that the portion of the TCP connection between the UTM appliance and the local server will be in the clear without the SSL layer, thus allowing SSL processing to be offloaded from the server by the appliance. If you'd like to enable this, you will need to create a PAT rule to remap the encrypted service such as HTTPS to unencrypted service HTTP. Once selected, click Add.
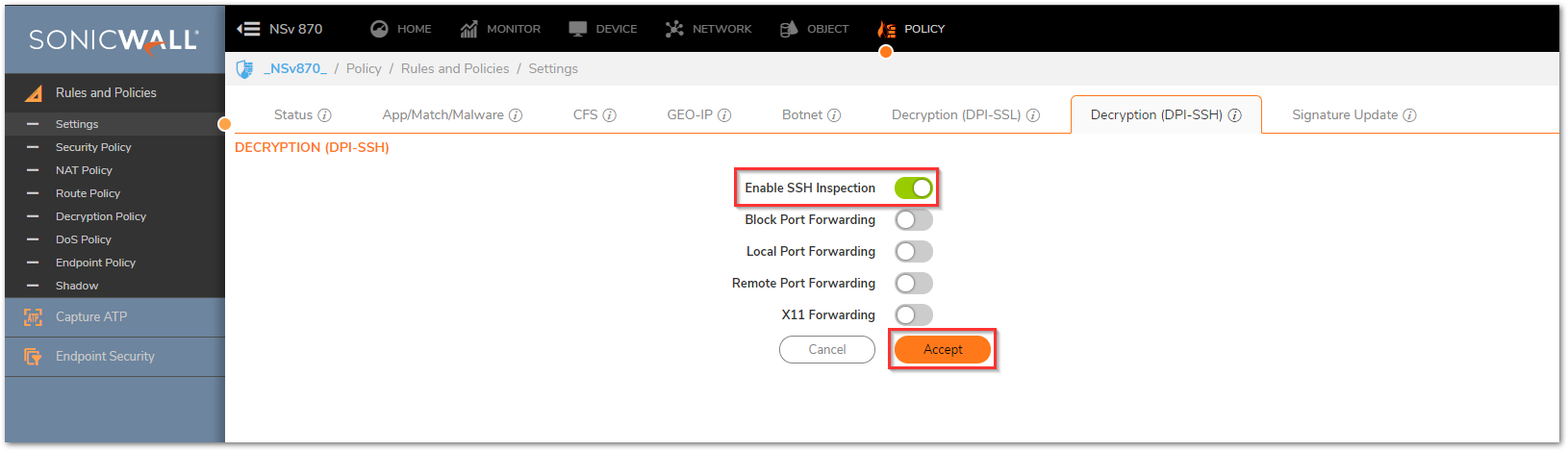
To enable DPI-SSH
- Navigate to Policy | Rules and Policies | Settings and Decryption (DPI-SSH) tab.
- Use the toggle button to turn on Enable SSH Inspection, then click Accept at the bottom.
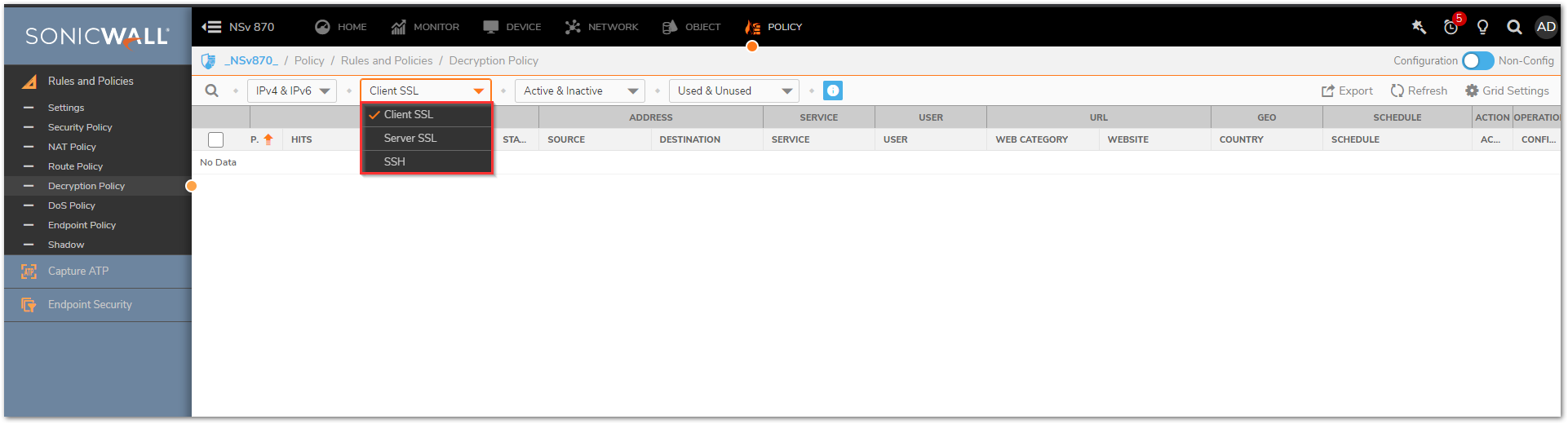
To create a Client SSL Decryption Policy
- Navigate to the Policy | Rules and Policies | Decryption Policy tab. Make sure that the drop-down option at the top of the screen is set to Client SSL.
- Click Top at the bottom of the screen. If you have multiple policies it is very important to properly prioritize them in order to make sure that the decryption policy is getting applied to the correct traffic.
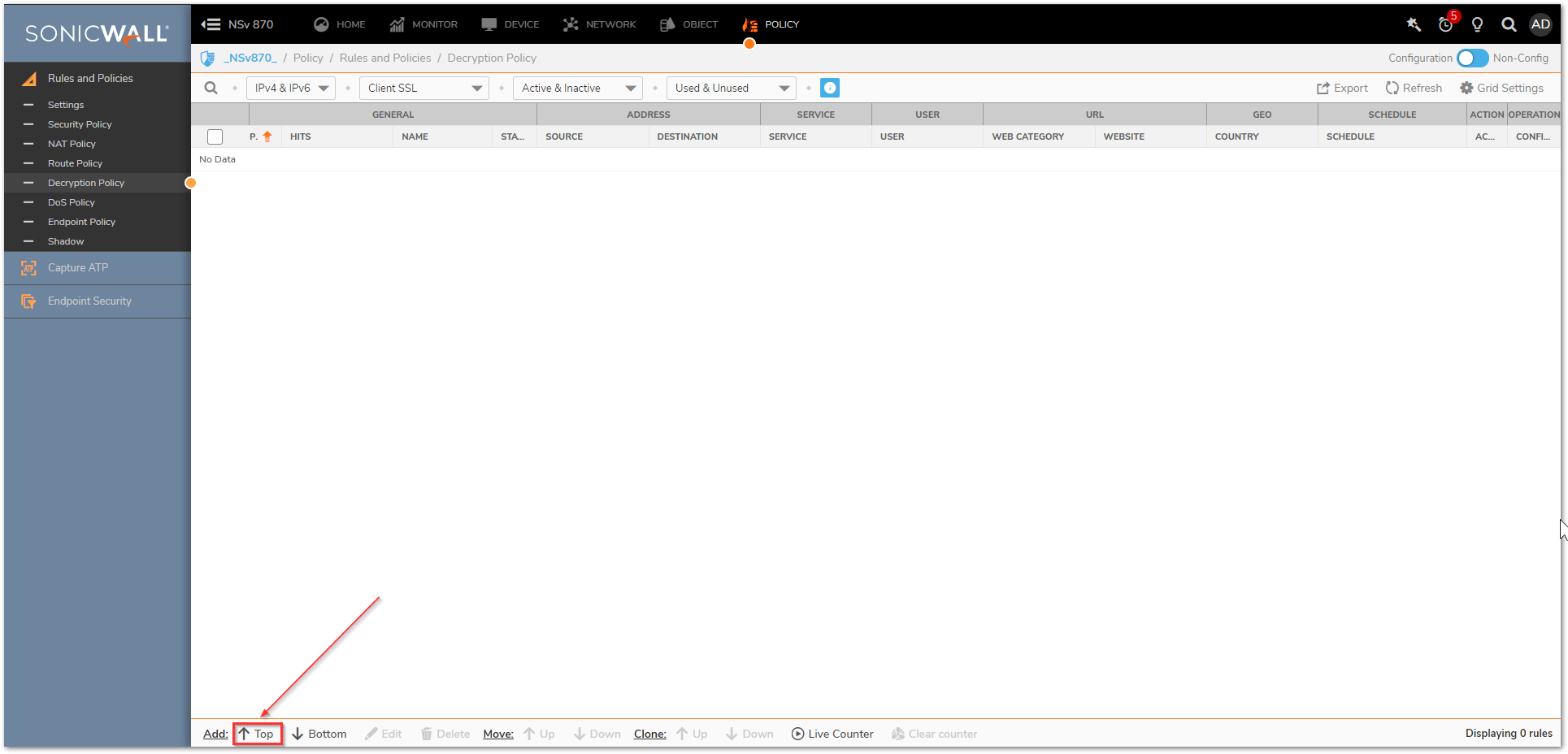
- Select the appropriate source/destination/service, or leave it set to Any to decrypt all traffic.
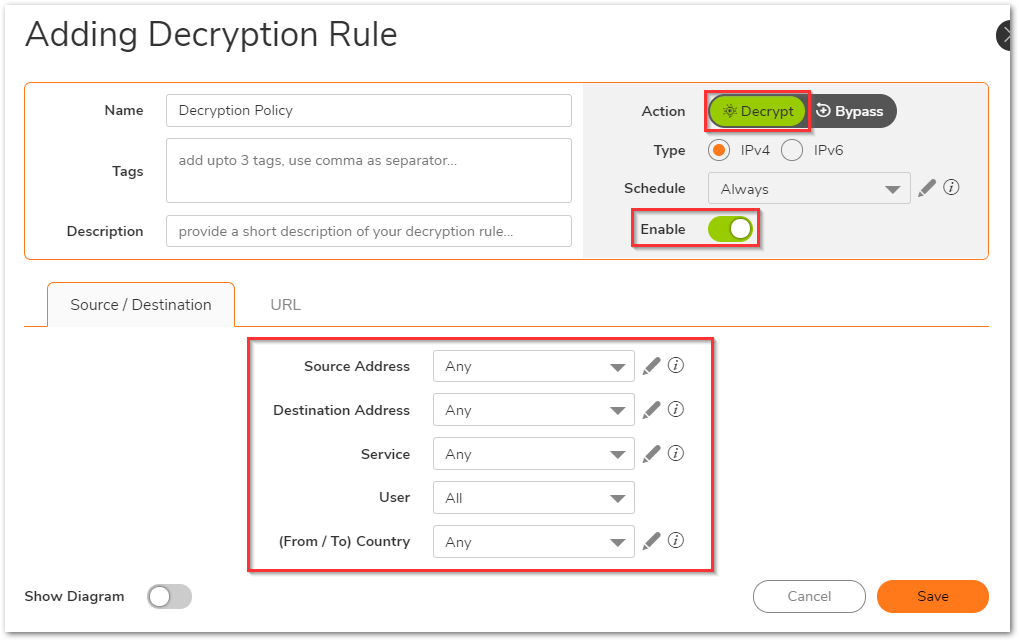
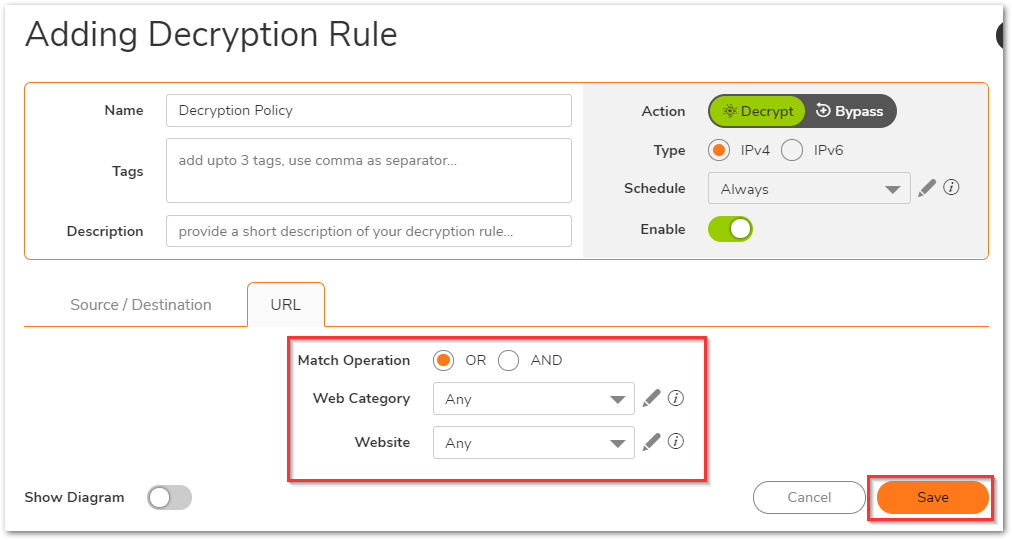
- Under the URL tab, you can select the Web Category and Website lists as well. In the Action section choose whether you'd like to Decrypt or Bypass.
- Click Save.
To Create a Server SSL/SSH Decryption Policy
- Navigate to the Policy | Rules and Policies | Decryption Policy tab. Make sure that the drop-down option at the top of the screen is set to Server SSL or SSH.
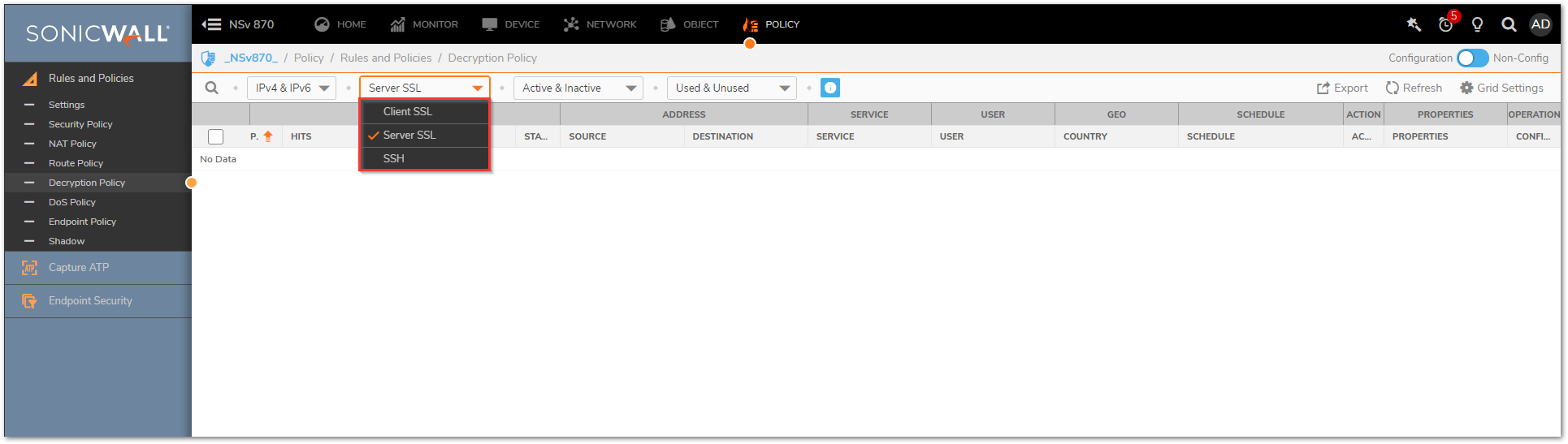
- From here, you'll follow the same steps outlined above to create rules .
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation






 YES
YES NO
NO