-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to create a custom zone?



Description
A zone is a logical grouping of one or more interfaces designed to make management, such as the definition and application of Access Rules, a simpler and more intuitive process than following strict physical interface scheme. Zone-based security is a powerful and flexible method of managing both internal and external network segments, allowing the administrator to separate and protect critical internal network resources from unapproved access or attack.
SonicOS zones allows you to apply security policies to the inside of the network. This allows the administrator to do this by organizing network resources to different zones, and allowing or restricting traffic between those zones. This way, access to critical internal resources such as payroll servers or engineering code servers can be strictly controlled.
Zones also allow full exposure of the NAT table to allow the administrator control over the traffic across the interfaces by controlling the source and destination addresses as traffic crosses from one zone to another. This means that NAT can be applied internally, or across VPN tunnels, which is a feature that users have long requested.
SonicWALL security appliances can also drive VPN traffic through the NAT policy and zone policy, since VPNs are now logically grouped into their own VPN zone.
Each zone has a security type, which defines the level of trust given to that zone. There are five security types:
- Trusted : Trusted is a security type that provides the highest level of trust—meaning that the least amount of scrutiny is applied to traffic coming from trusted zones. Trusted security can be thought of as being on the LAN (protected) side of the security appliance. The LAN zone is always Trusted.
- Encrypted : Encrypted is a security type used exclusively by the VPN zone. All traffic to and from an Encrypted zone is encrypted.
- Wireless : Wireless is a security type applied to the WLAN zone or any zone where the only interface to the network consists of SonicWALL SonicPoint/Sonicwave devices. Wireless security type is designed specifically for use with SonicPoint/Sonicwave devices. Placing an interface in a Wireless zone activates SDP (SonicWALL Discovery Protocol) and SSPP (SonicWALL Simple Provisioning Protocol) on that interface for automatic discovery and provisioning of SonicPoint/Sonicwave devices.
- Public : A Public security type offers a higher level of trust than an Untrusted zone, but a lower level of trust than a Trusted zone. Public zones can be thought of as being a secure area between the LAN (protected) side of the security appliance and the WAN (unprotected) side. The DMZ, for example, is a Public zone because traffic flows from it to both the LAN and the WAN. By default traffic from DMZ to LAN is denied. But traffic from LAN to ANY is allowed. This means only LAN initiated connections will have traffic between DMZ and LAN. The DMZ will only have default access to the WAN, not the LAN.
- Untrusted : The Untrusted security type represents the lowest level of trust. It is used by both the WAN and the virtual Multicast zone. An Untrusted zone can be thought of as being on the WAN (unprotected) side of the security appliance.By default, traffic from Untrusted zones is not permitted to enter any other zone type without explicit rules, but traffic from every other zone type is permitted to Untrusted zones.
Resolution
Following steps will guide you in creating a custom network zone on SonicWall UTM appliance:
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Click Object in the top menu
- Navigate to Match Objects | Zones | Click Add Zone
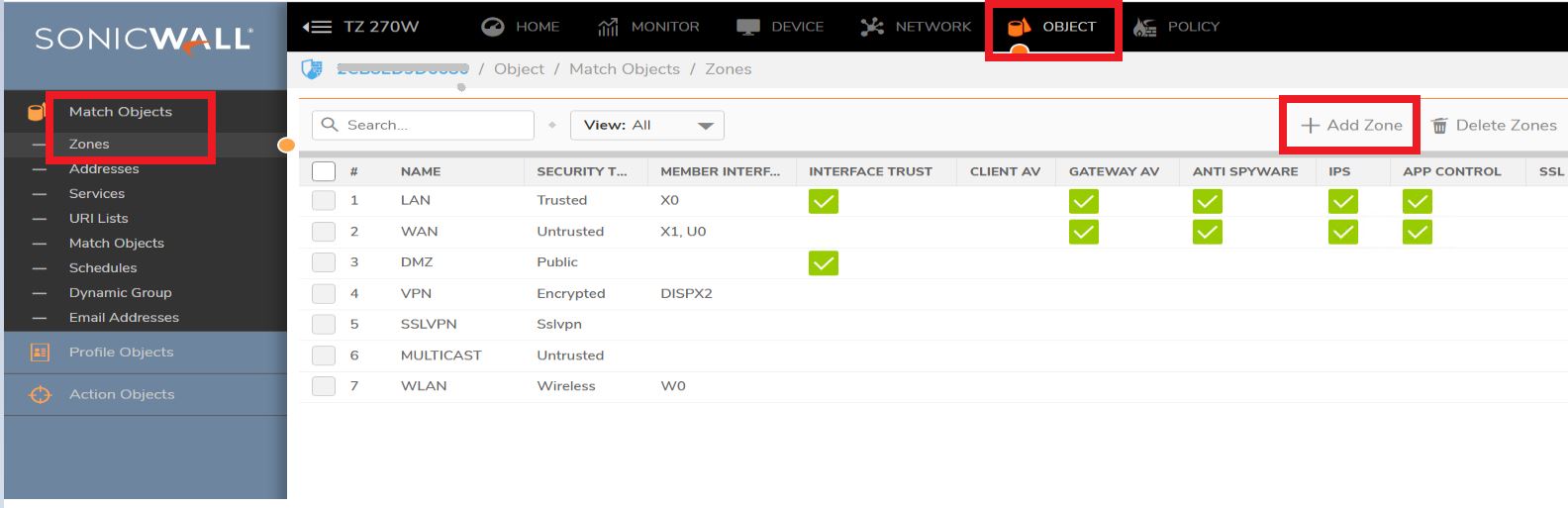
- Select the security type for the zone appropriately
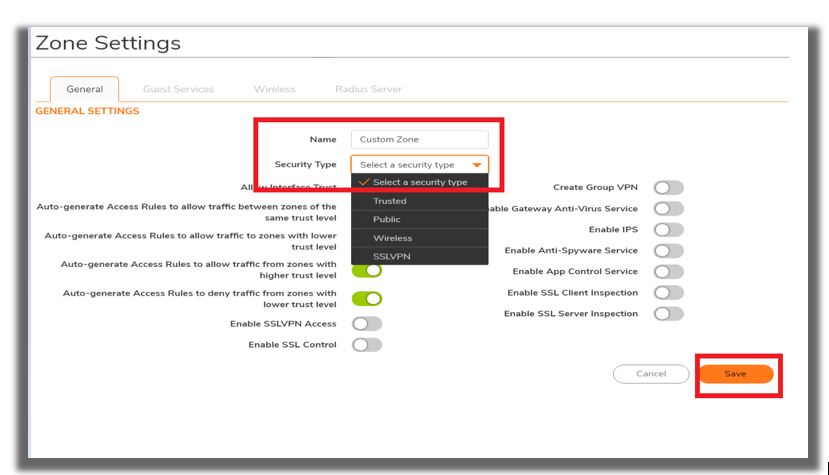
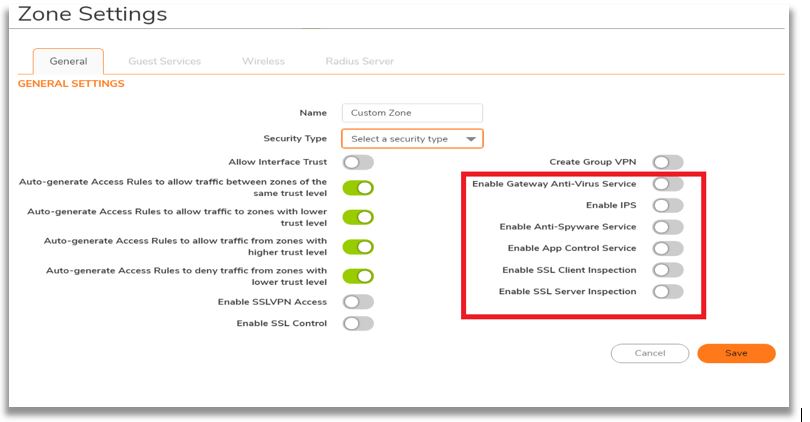
- Apply the required security services on the custom zones.
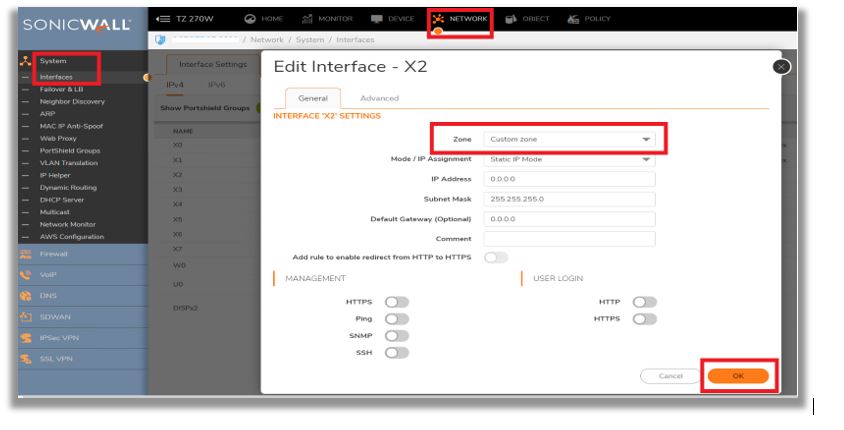
- Bind the newly created custom zone to a physical interfaces to allow for configuration of Access Rules to govern inbound and outbound traffic. If there is no interface, traffic cannot access the zone or exit the zone. Navigate to Network | Interface | Edit the interface to which you would like to bind this zone.
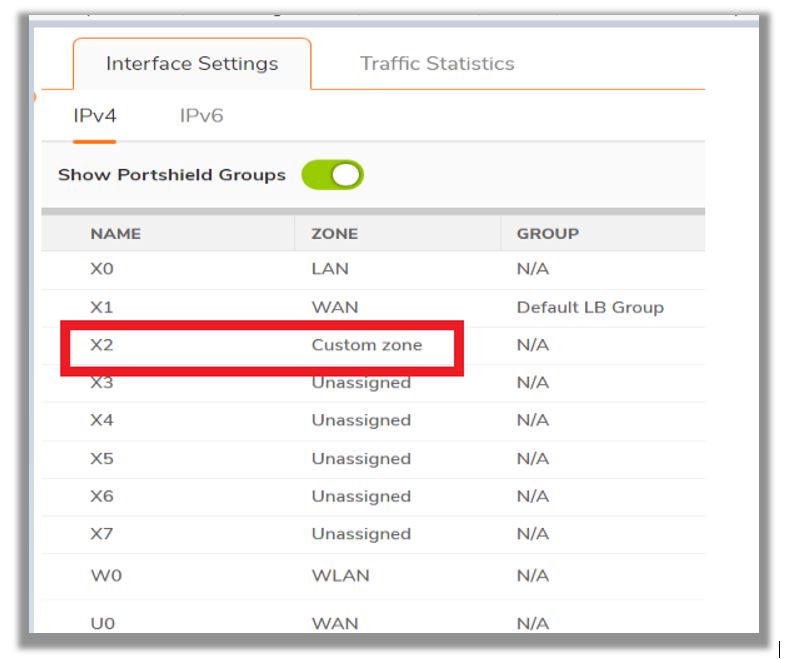
Deleting a Zone:
You can delete a custom zone by clicking the delete icon under Objects| Match Objects | Zones | Click Add Zone
 NOTE: Pre-Defined zones can't be deleted.
NOTE: Pre-Defined zones can't be deleted.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
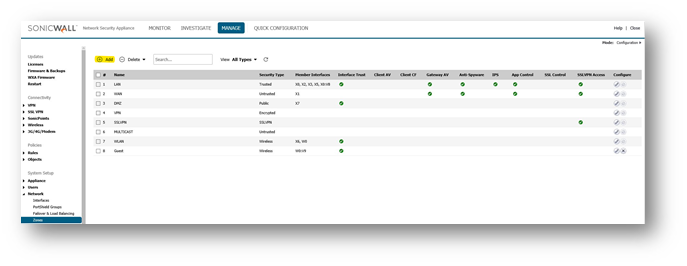
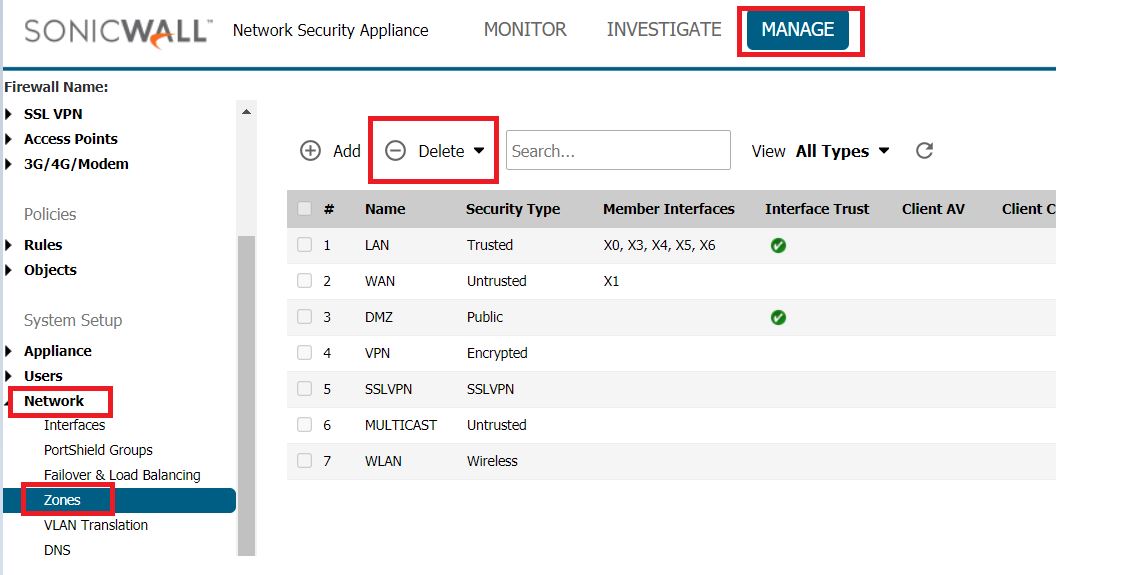
- Navigate to Manage | System Setup | Networks | Zones | Add
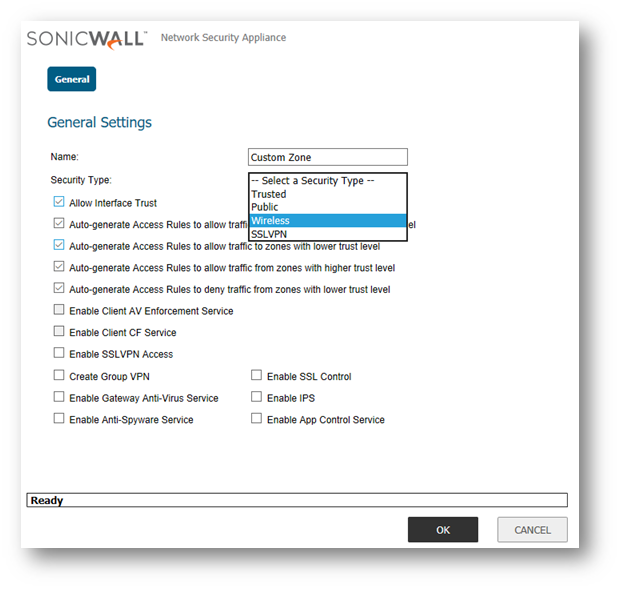
- Select the security type for the zone appropriately.
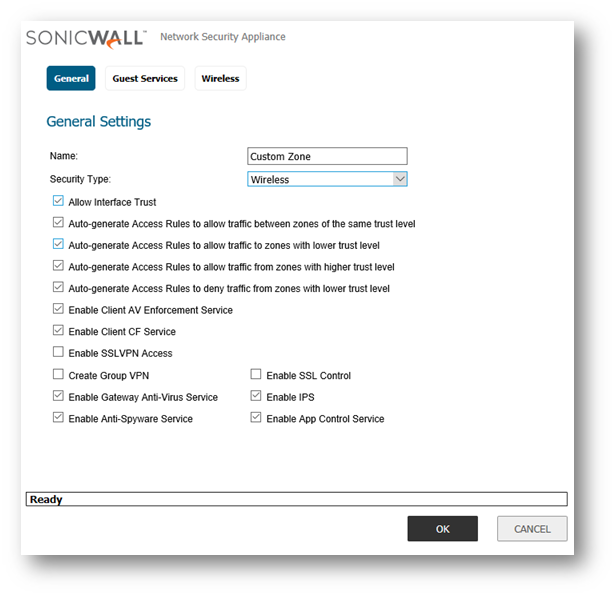
- Apply security services on the custom zones. You can enable SonicWall Security Services for traffic across zones. For example, you can enable SonicWall Intrusion Prevention Service for incoming and outgoing traffic on the WLAN zone to add more security for internal network traffic. You can enable the following SonicWall Security Services on zones:
- Enforce Content Filtering Service - Enforces content filtering on multiple interfaces in the same Trusted, Public and WLAN zones.
- Enforce Client Anti-Virus Service - Enforces anti-virus protection on multiple interfaces in the same Trusted, Public or WLAN zones.
- Enable Gateway Anti-Virus - Enforces gateway anti-virus protection on multiple interfaces in the same Trusted, Public or WLAN zones.
- Enable IPS - Enforces intrusion detection and prevention on multiple interfaces in the same Trusted, Public or WLAN zones.
- Enable Anti-Spyware Service - Enforces anti-spyware detection and prevention on multiple interfaces in the same Trusted, Public or WLAN zones.
- Create Group VPN - Creates a GroupVPN policy for the zone, which is displayed in the VPN Policies table on the VPN | Settings page. You can customize the GroupVPN policy on the VPN | Settings page. If you uncheck Create Group VPN, the GroupVPN policy is removed from the VPN | Settings page.
- Applying the custom zone on an interface, physical interfaces must be assigned to a zone to allow for configuration of Access Rules to govern inbound and outbound traffic. Security zones are bound to each physical interface where it acts as a conduit for inbound and outbound traffic. If there is no interface, traffic cannot access the zone or exit the zone. Navigate to Manage > System Setup > Network > Interface > Configure:
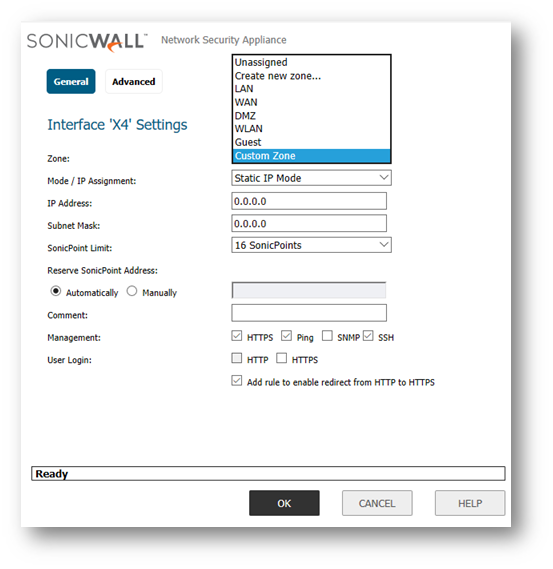
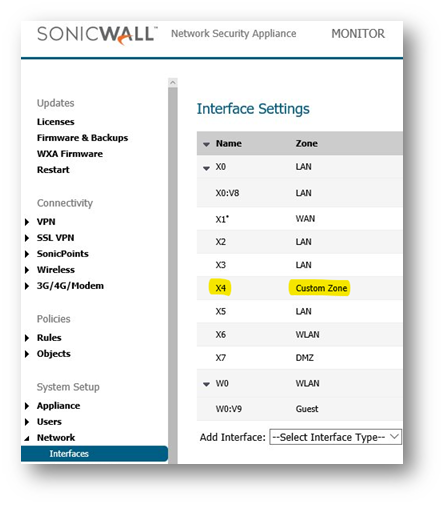
Deleting a Zone:
You can delete a custom zone by clicking the delete icon in the Configure column in Network > Zones
 NOTE: Pre-Defined zones can't be deleted.
NOTE: Pre-Defined zones can't be deleted.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Navigate to Networks | Zones | Add
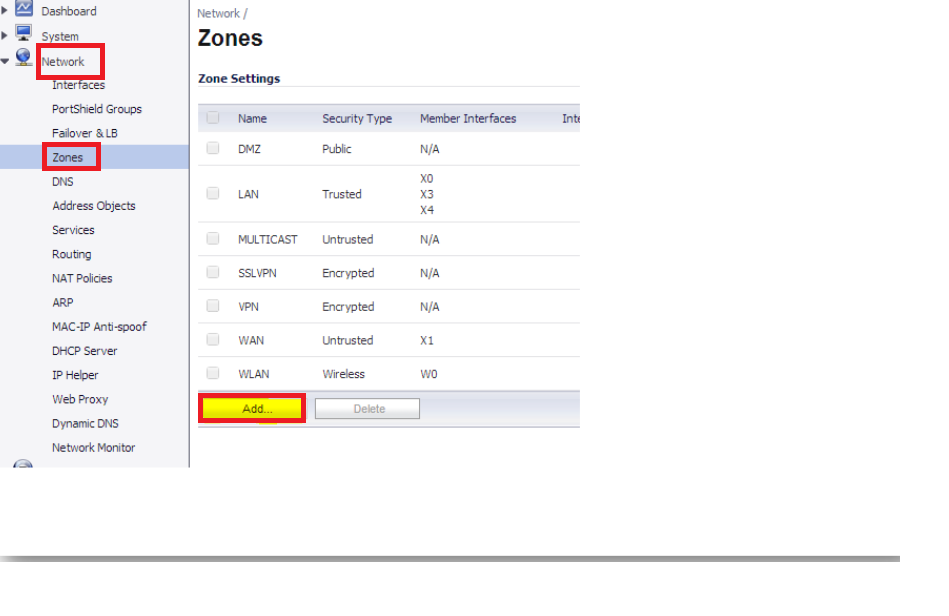
- Assign a custom name to the zone and select the security type for the zone appropriately.
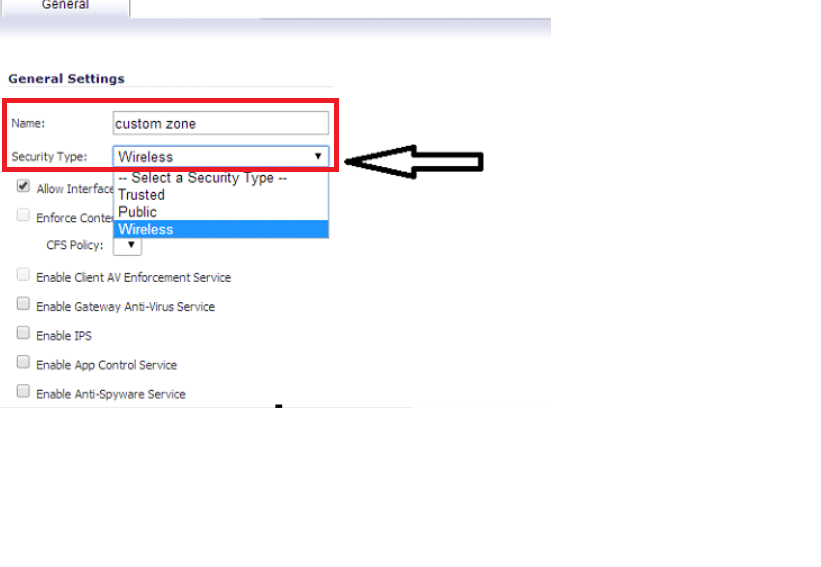
- Apply security services on the custom zones. You can enable SonicWall Security Services for traffic across zones. For example, you can enable SonicWall Intrusion Prevention Service for incoming and outgoing traffic on the WLAN zone to add more security for internal network traffic. You can enable the following SonicWall Security Services on zones:
- Enforce Content Filtering Service - Enforces content filtering on multiple interfaces in the same Trusted, Public and WLAN zones.
- Enforce Client Anti-Virus Service - Enforces anti-virus protection on multiple interfaces in the same Trusted, Public or WLAN zones.
- Enable Gateway Anti-Virus - Enforces gateway anti-virus protection on multiple interfaces in the same Trusted, Public or WLAN zones.
- Enable IPS - Enforces intrusion detection and prevention on multiple interfaces in the same Trusted, Public or WLAN zones.
- Enable Anti-Spyware Service - Enforces anti-spyware detection and prevention on multiple interfaces in the same Trusted, Public or WLAN zones.
- Create Group VPN - Creates a GroupVPN policy for the zone, which is displayed in the VPN Policies table on the VPN | Settings page. You can customize the GroupVPN policy on the VPN | Settings page. If you uncheck Create Group VPN, the GroupVPN policy is removed from the VPN | Settings page.
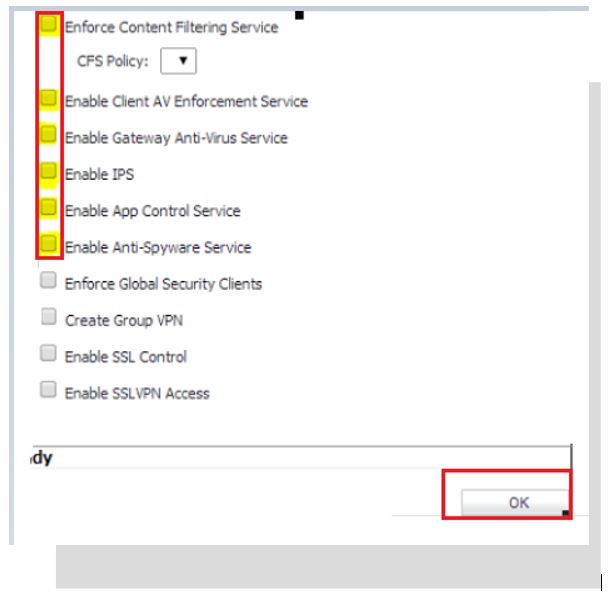
- Applying the custom zone on an interface, physical interfaces must be assigned to a zone to allow for configuration of Access Rules to govern inbound and outbound traffic. Security zones are bound to each physical interface where it acts as a conduit for inbound and outbound traffic. If there is no interface, traffic cannot access the zone or exit the zone. Navigate to Network | Interface | Edit Icon:
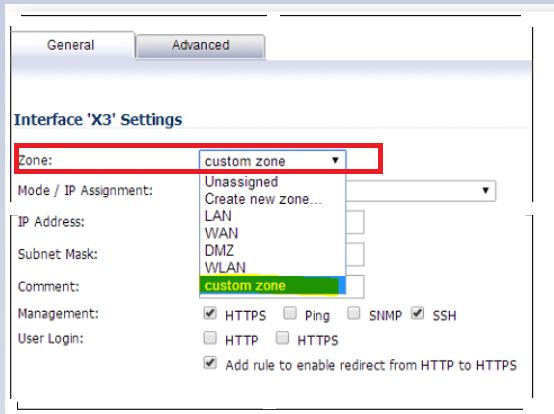
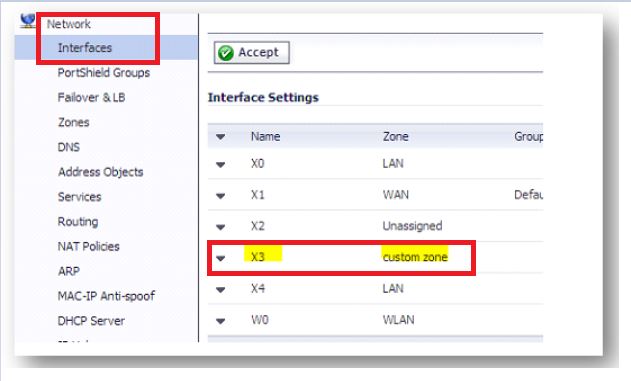
Deleting a Zone:
You can delete a custom zone by clicking the delete icon in the Configure column in Network | Zones
 NOTE: Pre-Defined zones can't be deleted.
NOTE: Pre-Defined zones can't be deleted.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall NSA Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > NSa Series






 YES
YES NO
NO