-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to connect to IPSec GroupVPN from an internal Zone using Global VPN Client?



Description
This article explains how to enable the ability to connect to the VPN for secure access to resources from a less secure Internal Zone
Cause
In many environments, we have observed that many hosts connected to some less secure zones like WLAN, DMZ, or any other Custom Zones require access to the secure servers, resources, etc. Creating an Access Rule to Allow traffic between the zones can be seen as a potential vulnerability and requires manual intervention like disabling/deleting the rule, when not in use.
We can enable the ability to connect to VPN internally and allow access to resources the hosts require without creating/maintaining the access rules manually.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Enable and Configure GroupVPN
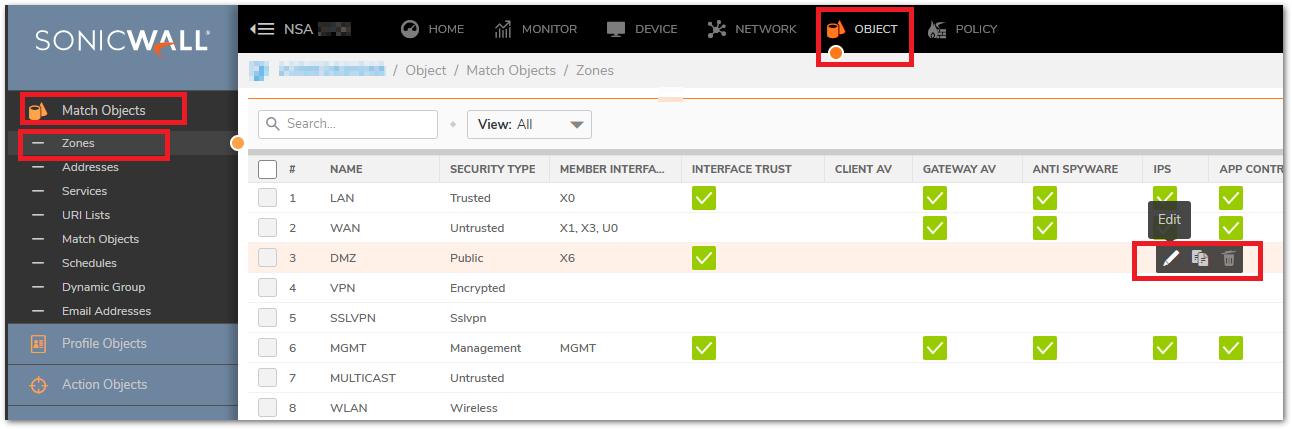
- Navigate to OBJECT | Match Objects > Zones
- Click Edit on the Zone from where you would like to connect to the VPN. [I have used DMZ in my example]
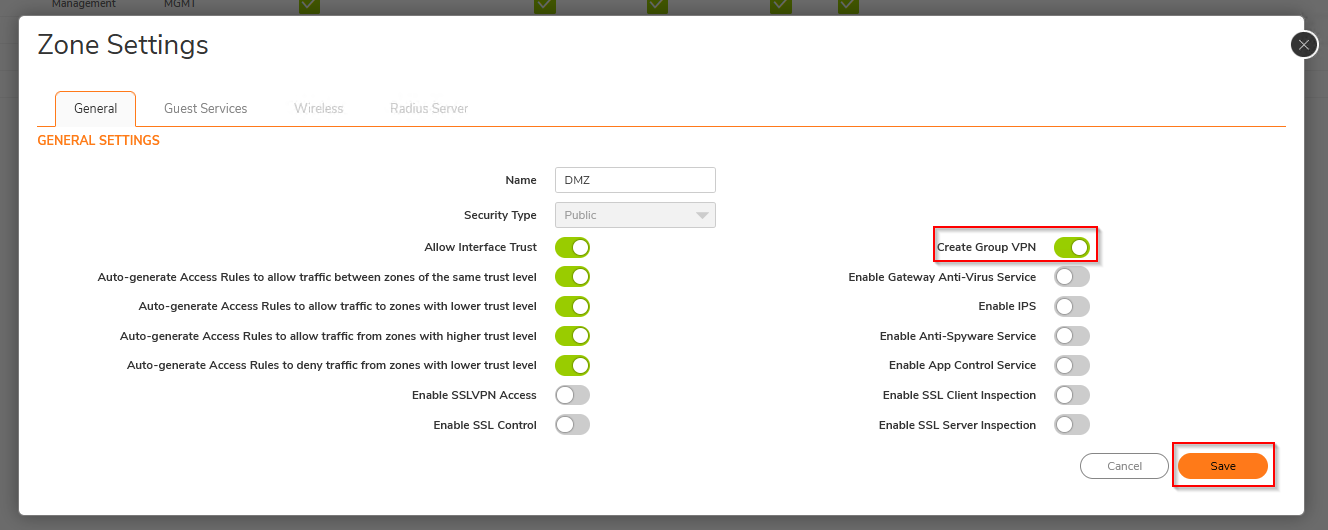
- Enable the option Create Group VPN and then Click on Save.
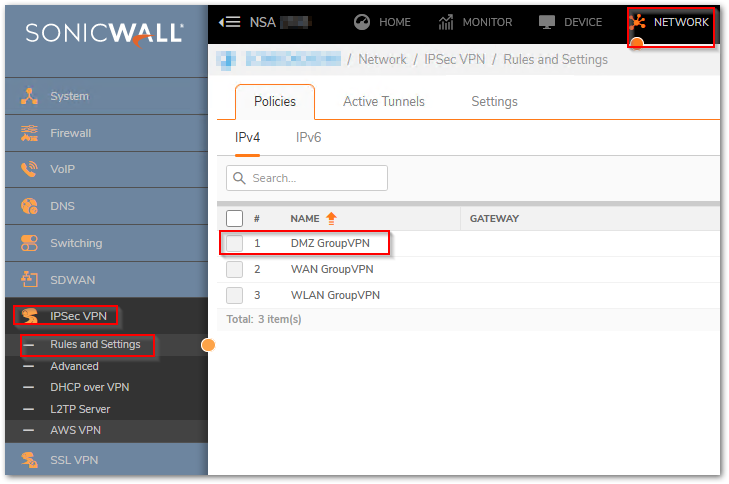
- Navigate to NETWORK | IPSec VPN > Rules and Settings, and you will be able to notice a new Group VPN. [For my example, I see DMZ GroupVPN].
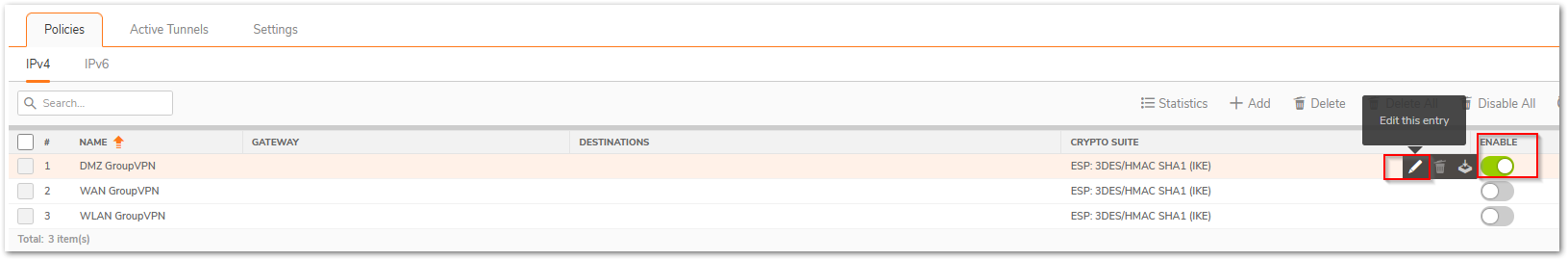
- Enable the checkbox on the right-hand side and then click on Edit this entry on the GroupVPN.
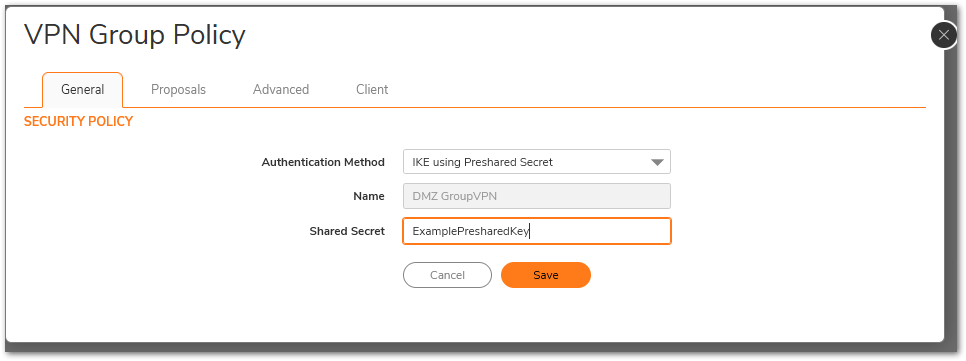
- The VPN Group Policy Window is displayed. In the General tab, IKE using Preshared Secret is the default setting for Authentication Method. Add the desired Shared Secret Key in the Shared Secret field.
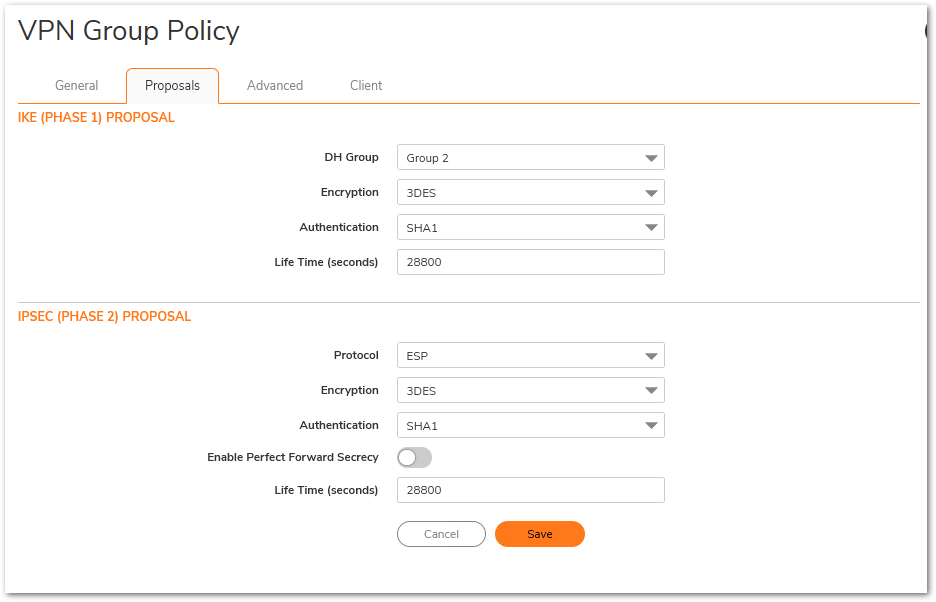
- Click on the Proposals tab, use the default settings, or choose the desired Encryption and Authentication options for Phase 1 and Phase 2 proposals
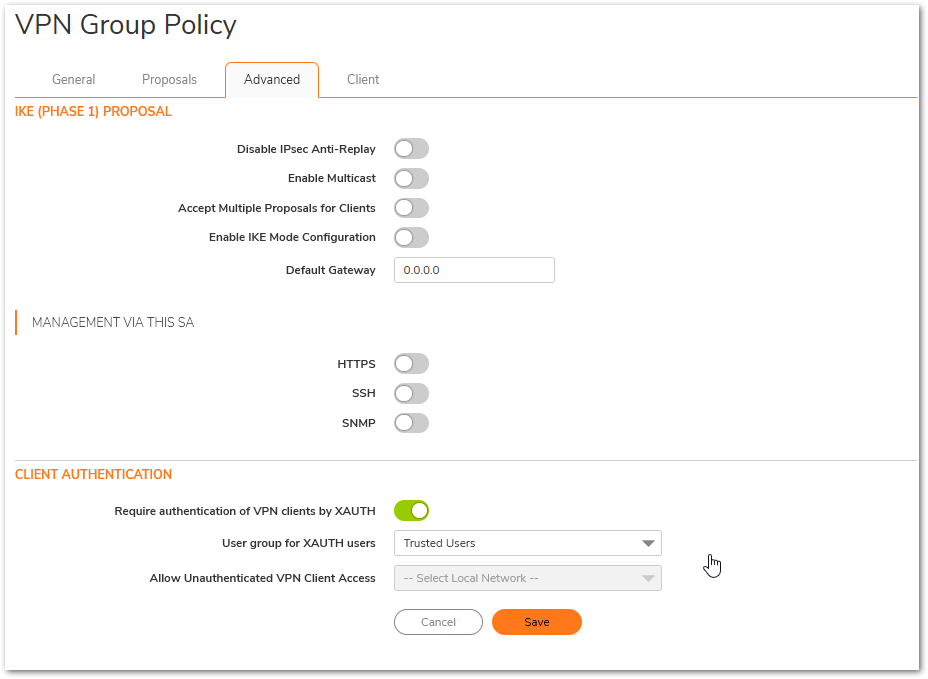
- Click on the Advanced tab and leave the configurations as Default.
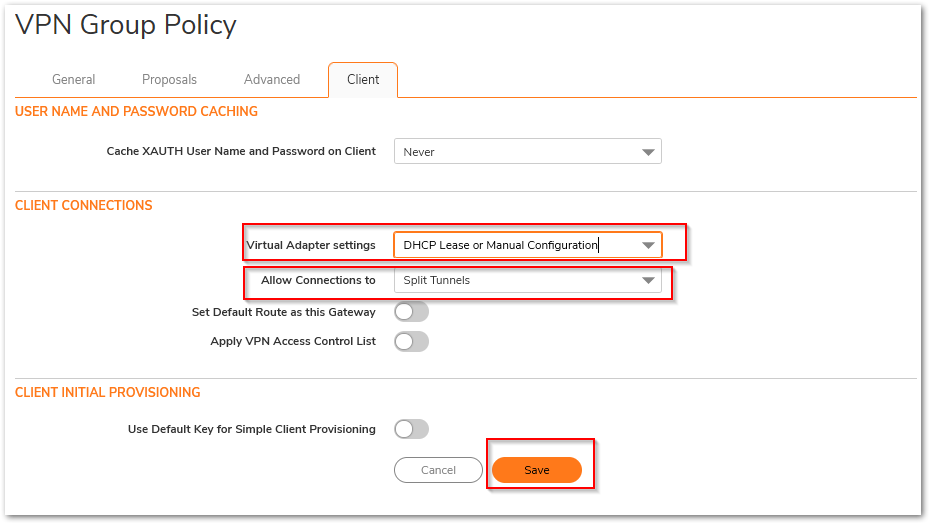
- Click on the Client tab, select the following settings as in the image below, and click on Save.
Configure DHCP over VPN
- Navigate to NETWORK | IPSec VPN > DHCP over VPN. Under the Gateway Dropdown, select Central.
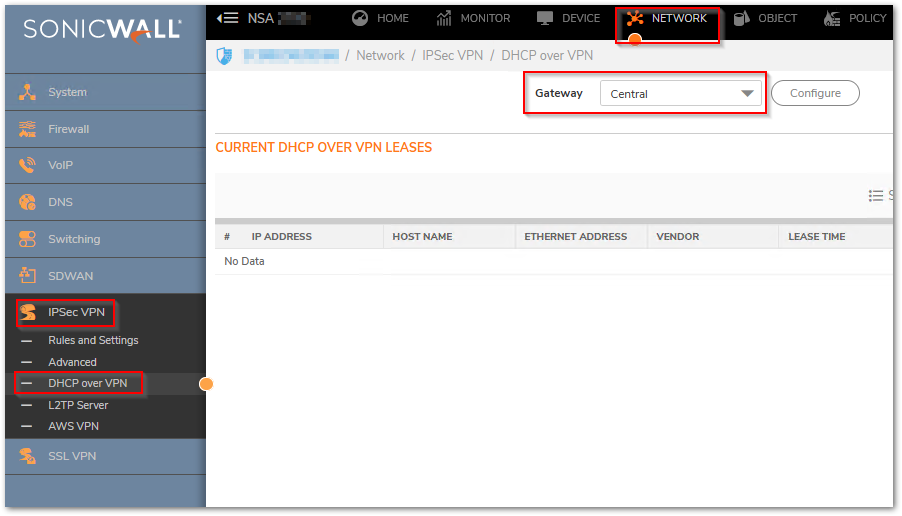
- Click on Configure and the DHCP over VPN Configuration window is displayed. Select the appropriate options for your configuration. Refer to the information below for more details:
Use Internal DHCP Server
Enables the SonicWall to be the DHCP server for either the Global VPN Client connections to this SonicWall or for Remote firewall connections via VPN. For this example, we would only be concerned with the Global VPN Client (GVC).
Send DHCP requests to the server addresses listed below
Enables the SonicWall to forward DHCP requests to the server indicated below in the IP Address Field. NOTE: You will need to separately add the DHCP server using the ADD button.
NOTE: You will need to separately add the DHCP server using the ADD button.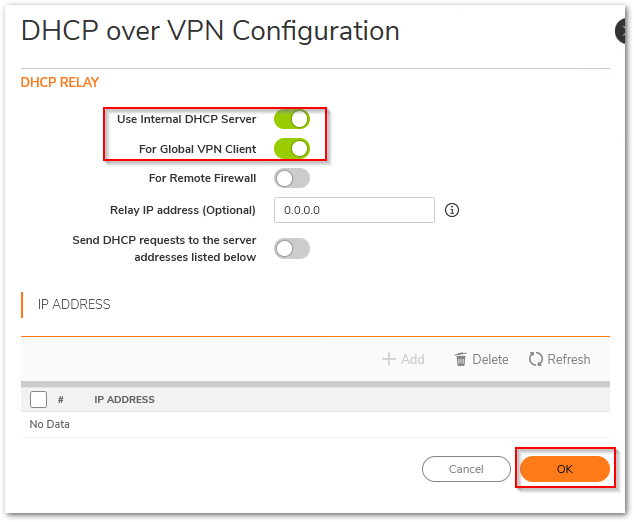
- Click OK.
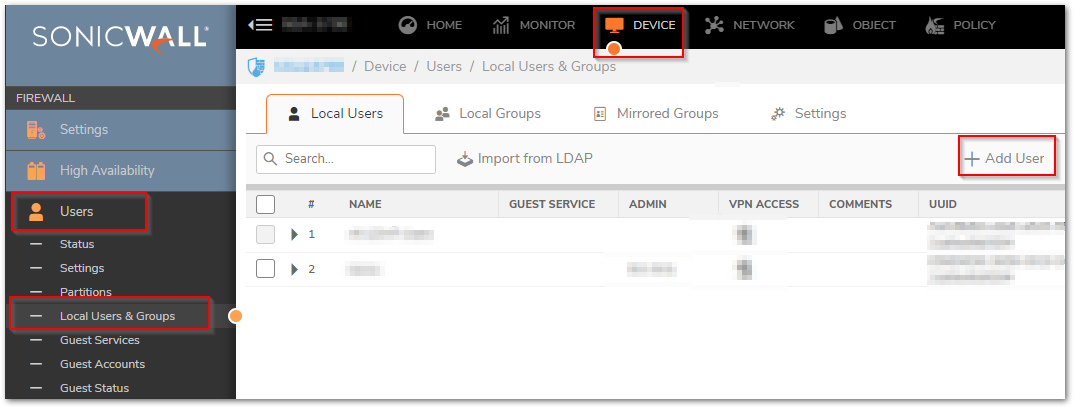
Configure User Accounts
- Navigate to Device | Users > Local Users & Groups - Local Users. Click Add User.
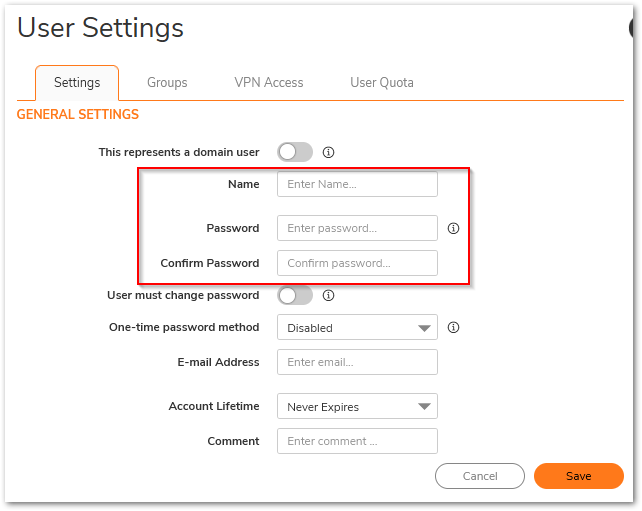
- Under the Settings tab enter the desired Name and Password.
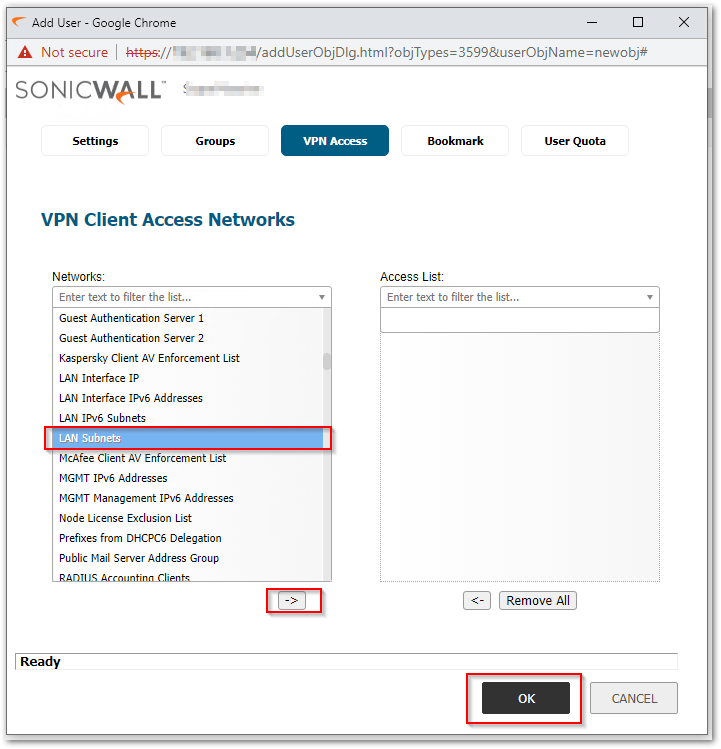
- On the VPN Access tab, select the Address Objects or Address Groups that the user needs access to and add to the user's access list using the Right Arrow Icon and then click on Save.
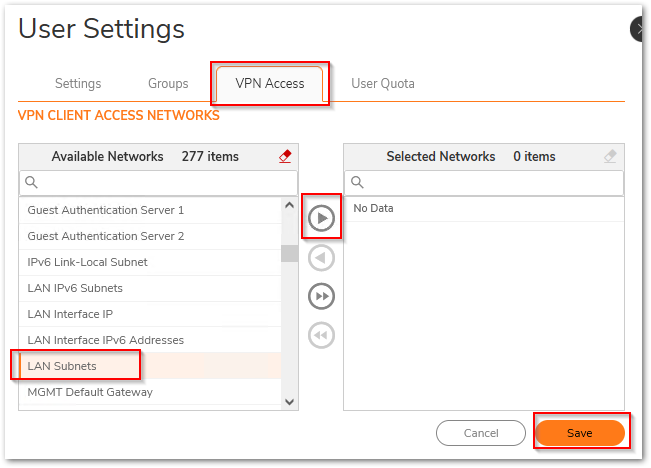
GVC Settings
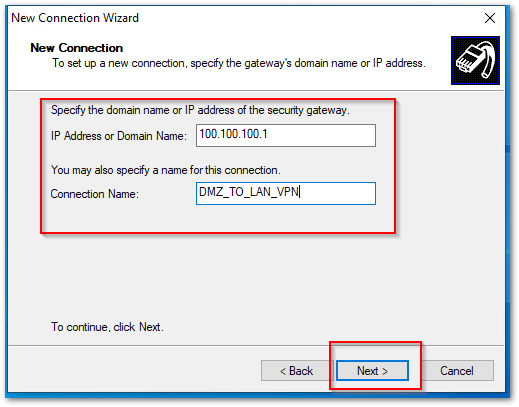
- When setting up a new connection for Connection to an Internal Zone, Enter the IP address of the Internal Zone Interface from where you are trying to connect in the IP Address or Domain Name field and click Next. [For my example I used DMZ(X6), I am going to use my X6 IP in the IP Address or Domain Name field.]
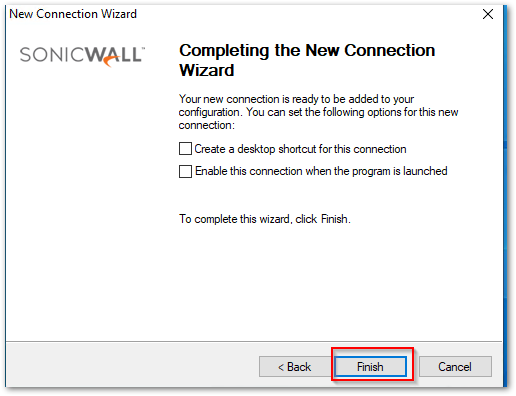
- On the Completing the New Connection Wizard, enable the checkboxes as per your preference and click Finish.
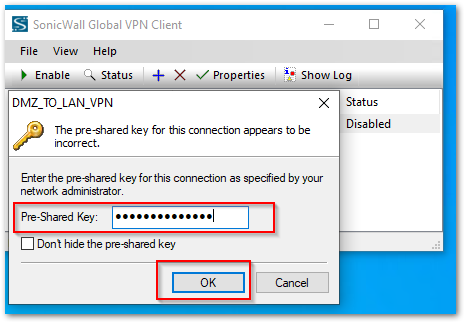
- Enable the connection on the GVC to connect to the DMZ_TO_LAN_VPN. You will get a prompt to enter the Pre-Shared key. [Pre Shared Key is the same that was configured in Step 6 under Enable and Configure GroupVPN section above.]
- After this, you will get a Prompt to enter the credentials for the user account. Use the Username and Password for the User that was created above and Click OK
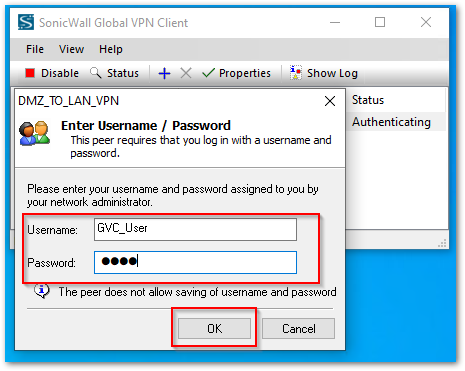
- The User will be connected after that and you will be able to access the Internal Network resources from a less secure Internal Zone.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Enable and Configure GroupVPN
- Navigate to MANAGE | Network > Zones.
- Configure the Zone from where you would like to connect to the VPN. [I have used DMZ in my example]
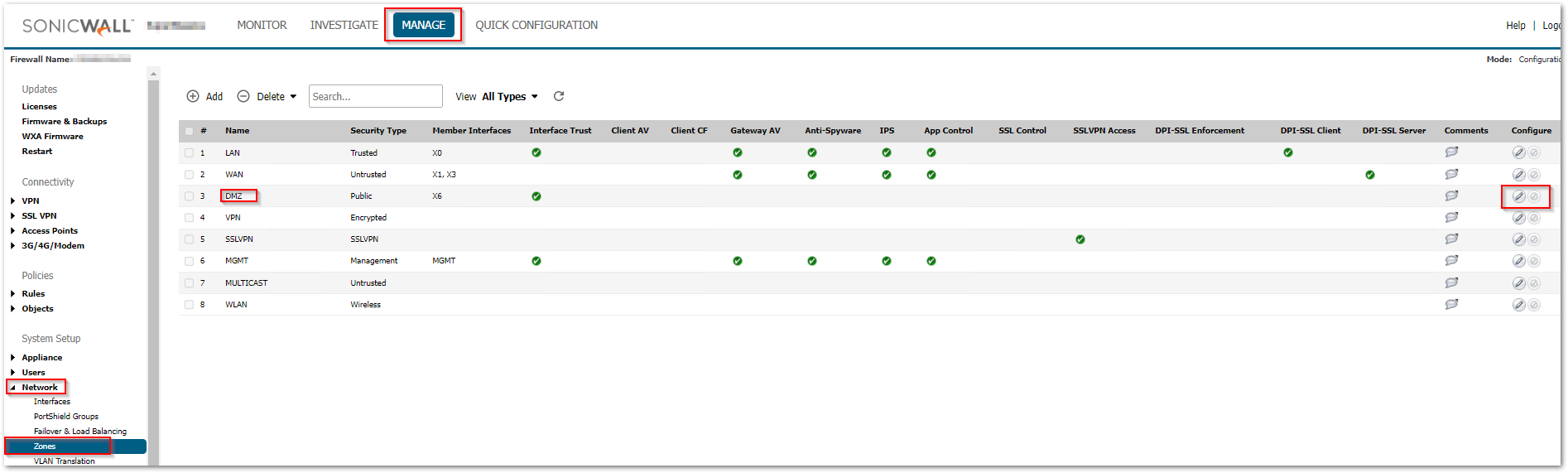
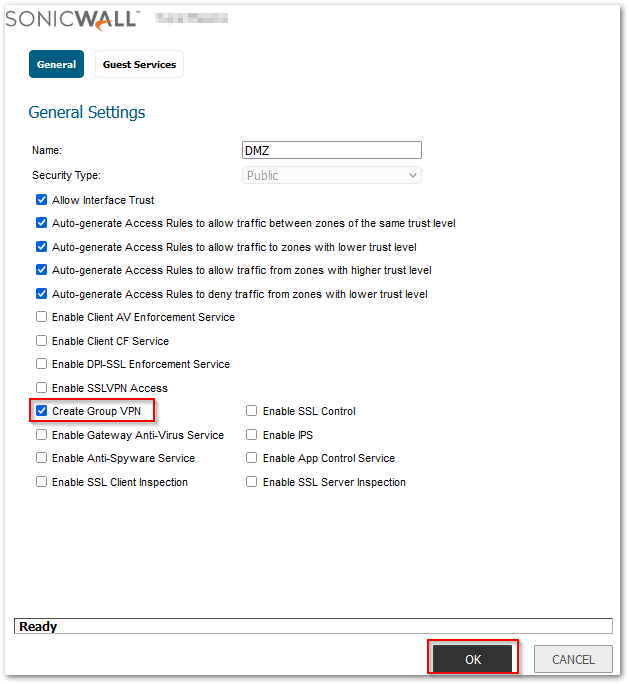
- Enable the checkbox Create Group VPN and then Click on OK.
- Navigate to MANAGE | VPN > Base Settings, and you will be able to notice a new Group VPN. [For my example, I see DMZ GroupVPN]
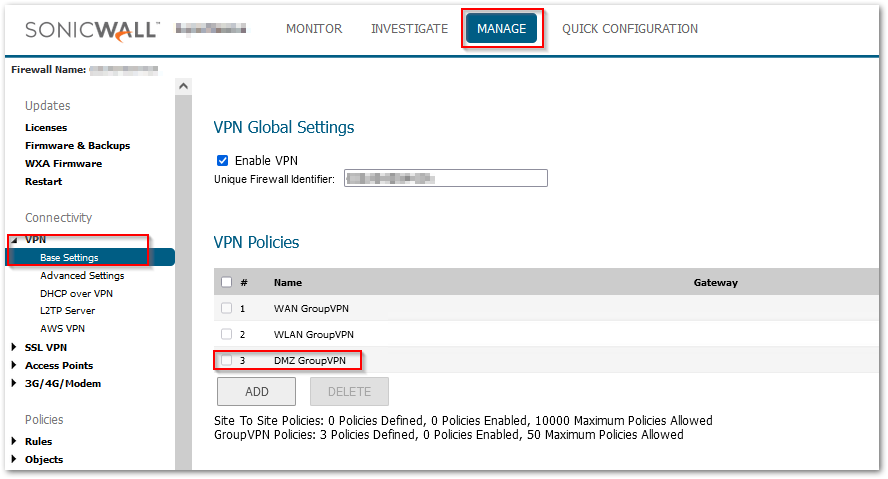
- Enable the checkbox on the right-hand side and then click on Configure on the GroupVPN.
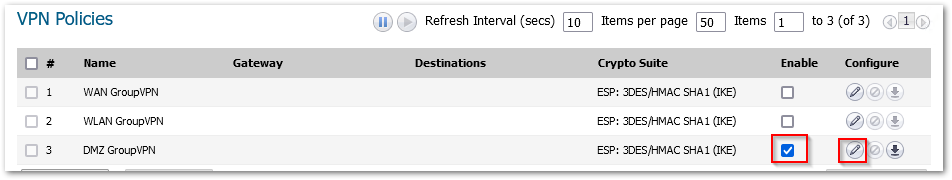
- The VPN Policy Window is displayed. In the General tab, IKE using Preshared Secret is the default setting for Authentication Method. Add the desired Shared Secret Key in the Shared Secret field.
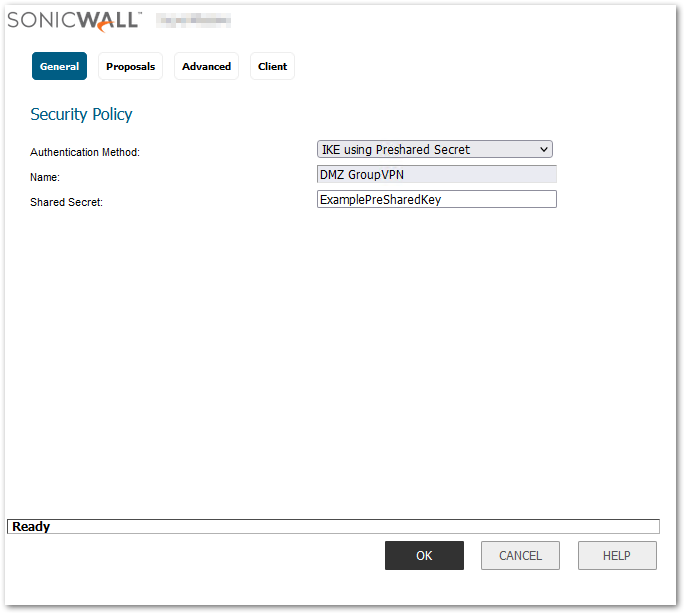
- Click on the Proposals tab, use the default settings, or choose the desired Encryption and Authentication options for Phase 1 and Phase 2 proposals.
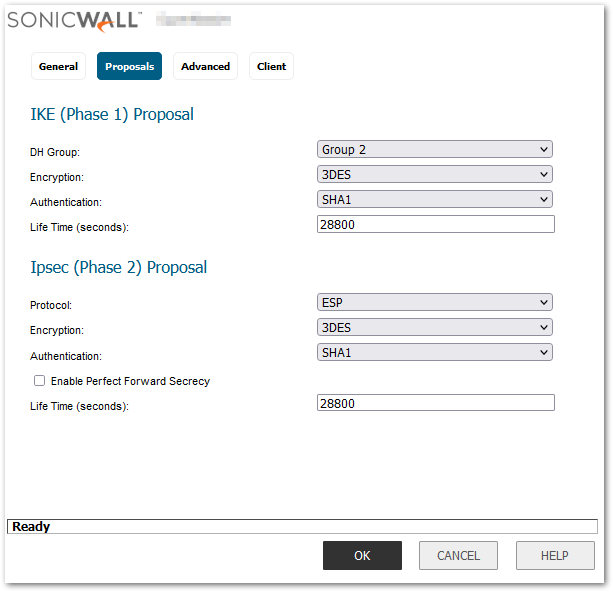
- Click on the Advanced tab and leave the configurations as Default.
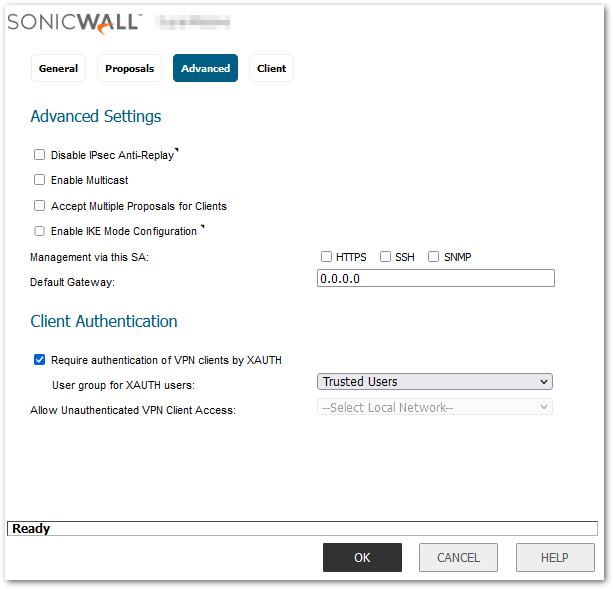
- Click the Client tab, select the following settings as in the image below, and click on OK.
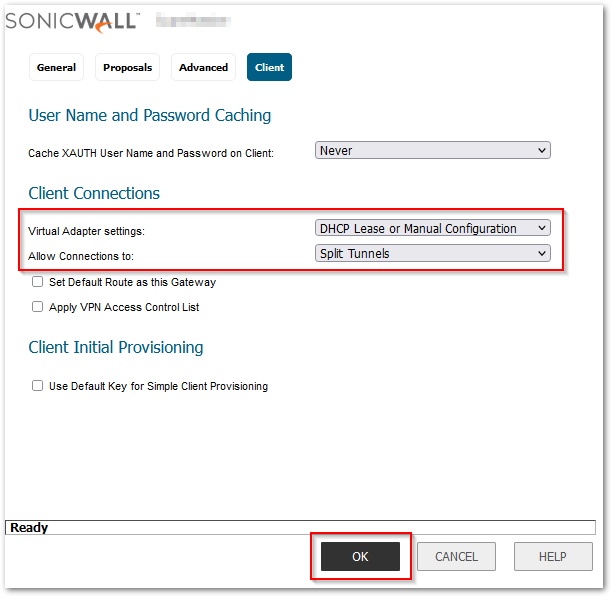
Configure DHCP over VPN
- Navigate to MANAGE | VPN > DHCP over VPN. Under the Dropdown, select Central Gateway.
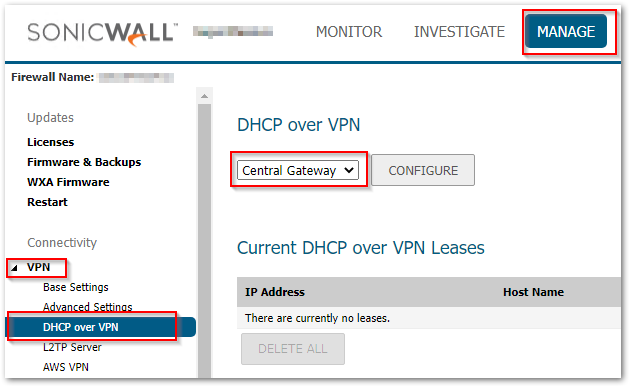
Click Configure and the DHCP over VPN Configuration window is displayed. Select the appropriate options for your configuration. Refer to the information below for more details:
Use Internal DHCP Server
Enables the SonicWall to be the DHCP server for either the Global VPN client connections to this SonicWall or for Remote firewall connections via VPN. For this example, we would only be concerned with the Global VPN client (GVC).
Send DHCP requests to the server addresses listed below
Enables the SonicWall to forward DHCP requests to the server indicated below in the IP Address Field. NOTE: You will need to separately add the DHCP server using the Add button.
NOTE: You will need to separately add the DHCP server using the Add button.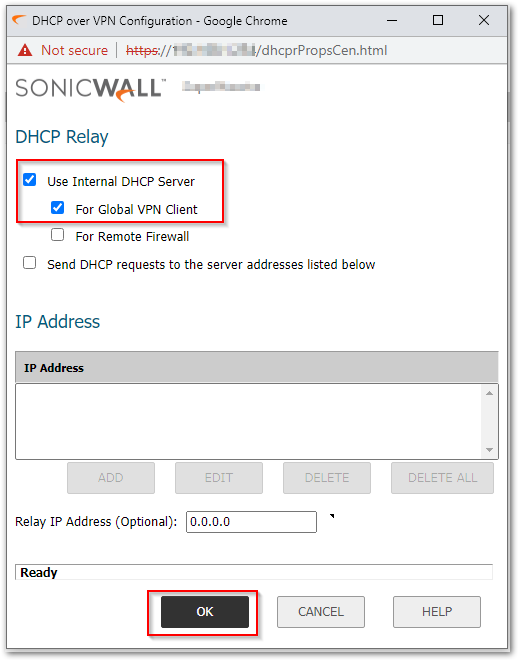
- Click OK.
Configure User Accounts
- Navigate to MANAGE | Users > Local Users and Groups - Local Users. Click Add.
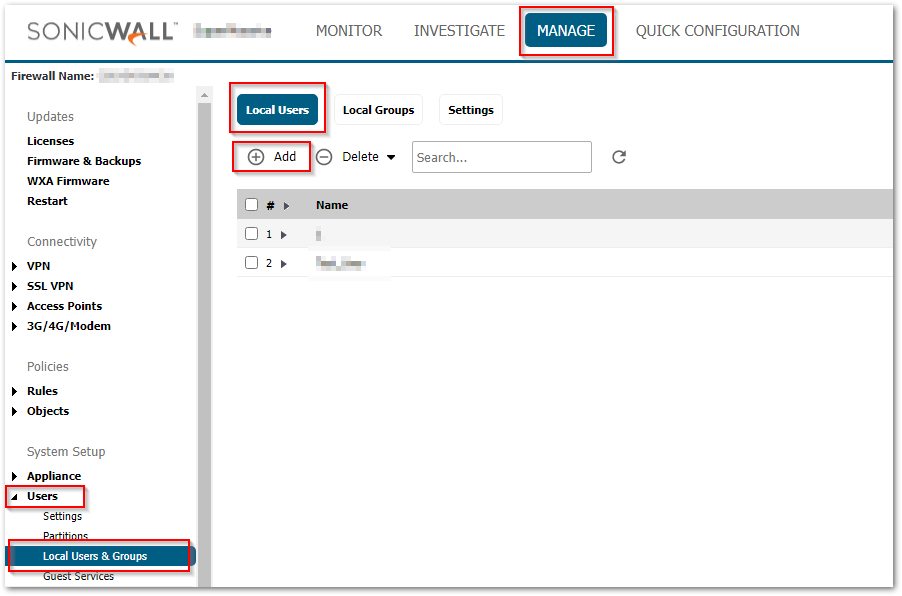
- Under the Settings tab, enter the desired Name and Password.
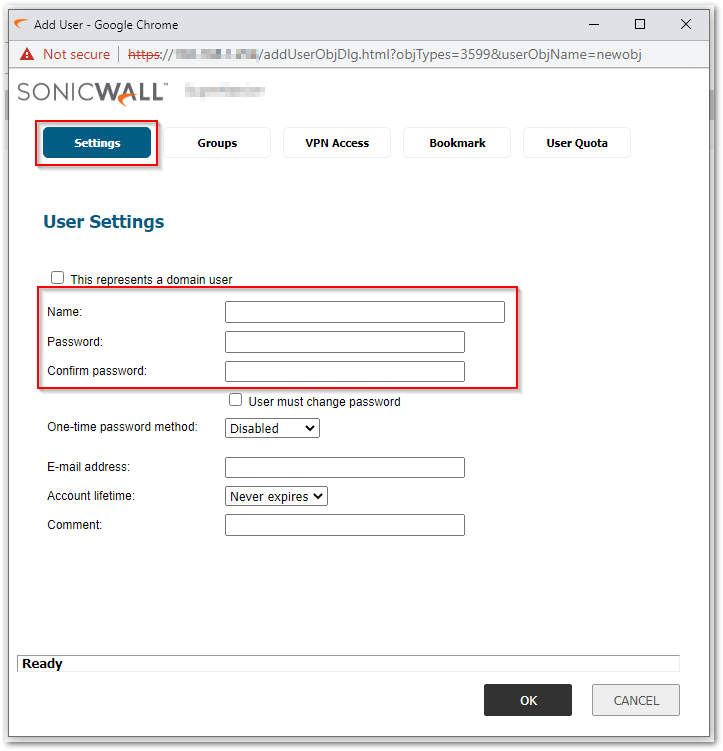
- On the VPN Access tab, select the Address Objects or Address Groups that the user needs access to and add to the user's access list using the Right Arrow Icon and then click on OK.
GVC Settings
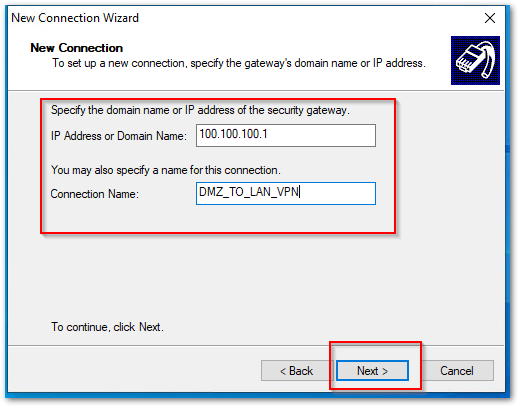
- When setting up a new connection for Connection to an Internal Zone, Enter the IP address of the Internal Zone Interface from where you are trying to connect in the IP Address or Domain Name field and click Next. [For my example I used DMZ(X6), I am going to use my X6 IP in the IP Address or Domain Name field.]
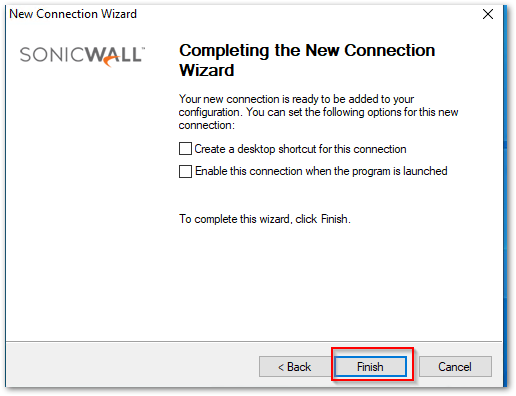
- On the Completing the New Connection Wizard, enable the checkboxes as per your preference and click Finish.
- Enable the connection on the GVC to connect to the DMZ_TO_LAN_VPN. You will get a prompt to enter the Pre-Shared key. [Pre Shared Key is the same that was configured in Step 6 under Enable and Configure GroupVPN section above.]
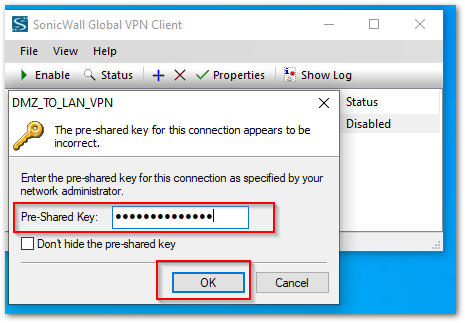
- After this, you will get a Prompt to enter the credentials for the user account. Use the Username and Password for the User that was created above and Click OK.
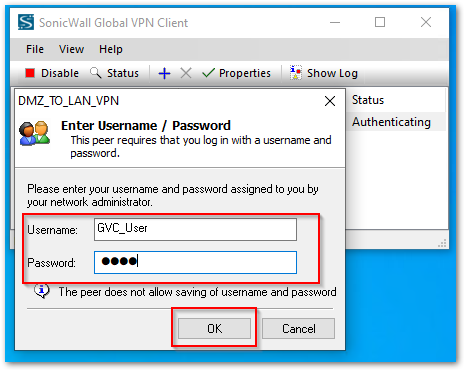
- The User will be connected after that and you will be able to access the Internal Network resources from a less secure Internal Zone.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > GVC/L2TP
- Firewalls > TZ Series > GVC/L2TP
- Firewalls > NSsp Series > GVC/L2TP
- Firewalls > NSv Series > GVC/L2TP
- Firewalls > SonicWall NSA Series > GVC/L2TP






 YES
YES NO
NO