-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to Configure Wire / Tap mode in SonicOS



Description
Wire Mode is a deployment option where the SonicWall appliance can be deployed as a Bump in the Wire. It provides a least-intrusive way to deploy the appliance in a network.
Wire Mode is very well suited for deploying behind a pre-existing Stateful Packet Inspection (SPI) Firewall. Wire Mode is a simplified form of Layer 2 Bridge Mode. A Wire Mode interface does not take any IP address and it is typically configured as a bridge between a pair of interfaces. None of the packets received on a Wire Mode interface are destined to the firewall, but are only bridged to the other interface.
Wire Mode operates in one of 4 different modes
Bypass Mode | Bypass Mode allows for the quick and relatively non-interruptive introduction of firewall hardware into a network. Upon selecting a point of insertion into a network (e.g. between a core switch and a perimeter firewall, in front of a VM server farm, at a transition point between data classification domains), the firewall is inserted into the physical data path, requiring a very short maintenance window. One or more pairs of switch ports on the firewall are used to forward all packets across segments at full line rates, with all the packets remaining on the firewall's 112 Gbps switch fabric rather than getting passed up to the multi-core inspection and enforcement path. While Bypass Mode does not offer any inspection or firewalling, this mode allows the administrator to physically introduce the firewall into the network with a minimum of downtime and risk, and to obtain a level of comfort with the newly inserted component of the networking and security infrastructure. The administrator can then transition from Bypass Mode to Inspect or Secure Mode instantaneously through a simple user-interface driven reconfiguration. |
Inspect Mode | Inspect Mode extends Bypass Mode without functionally altering the low-risk, zero latency packet path. Packets continue to pass through the firewall's switch fabric, but they are also mirrored to the multi-core RF-DPI engine for the purposes of passive inspection, classification, and flow reporting. This reveals the firewall's Application Intelligence and threat detection capabilities without any actual intermediate processing. |
Secure Mode | Secure Mode is the progression of Inspect Mode, actively interposing the firewall's multi-core processors into the packet processing path. This unleashes the inspection and policy engines' full-set of capabilities, including Application Intelligence and Control, Intrusion Prevention Services, Gateway and Cloud-based Anti-Virus, Anti-Spyware, and Content Filtering. Secure Mode affords the same level of visibility and enforcement as conventional NAT or L2 Bridged Mode deployments, but without any L3/L4 transformations, and with no alterations of ARP or routing behavior. Secure Mode thus provides an incrementally attainable NGFW deployment requiring no logical and only minimal physical changes to existing network designs. |
Tap Mode | Tap Mode provides the same visibility as Inspect Mode, but differs from the latter in that it ingests a mirrored packet stream via a single switch port on the firewall, eliminating the need for physically intermediated insertion. Tap Mode is designed for use in environments employing network taps, smart taps, port mirrors, or SPAN ports to deliver packets to external devices for inspection or collection. Like all other forms of Wire Mode, Tap Mode can operate on multiple concurrent port instances, supporting discrete streams from multiple taps. |
The following table summarizes the key functional differences between modes of interface configuration:
Bypass Mode | Inspect Mode | Secure Mode | Tap Mode | L2 Bridge, Transparent, NAT, Route Modes | |
| ARP/Routing/NAT a | No | No | No | No | Yes |
| Comprehensive Anti-Spam Service a | No | No | No | No | Yes |
| Content Filtering | No | No | Yes | No | Yes |
| DHCP Server a | No | No | No | No | Yes b |
| DPI Detection | No | Yes | Yes | Yes | Yes |
DPI Prevention | No | No | Yes | No | Yes |
| DPI-SSL a | No | No | Yes e | No | Yes |
| High-Availability | Yes | Yes | Yes | Yes | Yes |
| Link-State Propagation c | Yes | Yes | Yes | No | No |
| SPI | No | Yes | Yes | Yes | Yes |
| TCP Handshake Enforcement d | No | No | No | No | Yes |
| Virtual Groups a | No | No | No | No | Yes |
- a. These functions or services are unavailable on interfaces configured in Wire Mode, but remain available on a system-wide level
for any interfaces configured in other compatible modes of operation. - b. Not available in L2 Bridged Mode.
- c. Link State Propagation is a feature whereby interfaces in a Wire Mode pair will mirror the link-state triggered by transitions of
their partners. This is essential to proper operations in redundant path networks. - d. Disabled by design in Wire Mode to allow for failover events occurring elsewhere on the network to be supported
- e. Wire mode supports DPI-SSL in SonicOS 6.2.1.x
Note: When operating in Wire Mode, the firewall's dedicated Management interface will be used for local management. To enable remote management and dynamic security services and application intelligence updates, a WAN interface (separate from the Wire Mode interfaces)
must be configured for Internet connectivity. This is easily done given that SonicOS supports interfaces in mixed-modes of almost any combination.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
To configure an interface for Wire Mode, perform the following steps:
- Click Manage in the top navigation menu and then Network | Interfaces. Click the Configure button for the interface you want to configure for Wire Mode.
- In the Zone pull-down menu, select any zone type except WLAN.
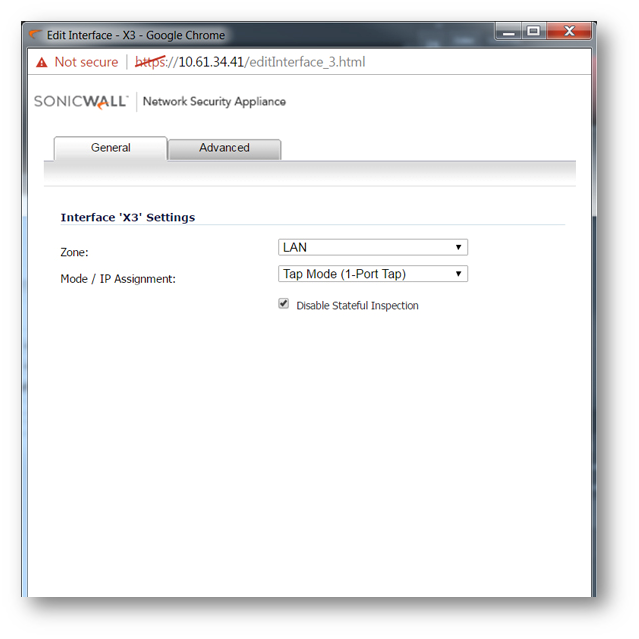
- To configure the Interface for Tap Mode, in the Mode / IP Assignment pull-down menu, select Tap Mode (1-Port Tap).
- To configure the Interface for Wire Mode, in the Mode / IP Assignment pull-down menu, select Wire Mode (2-Port Wire).
- In the Wire Mode Type pull-down menu, select the appropriate mode:
- Bypass (via Internal Switch/Relay)
- Inspect (Passive DPI of Mirrored Traffic)
- Secure (Active DPI of Inline Traffic)
- In the Paired Interface pull-down menu, select the interface that will connect to the upstream firewall. The paired interfaces must be of the same type (two 1 GB interfaces or two 10 GB interfaces).
Note: Only unassigned interfaces are available in the Paired Interface pull-down menu. To make an interface unassigned, click on the Configure button for it, and in the Zone pull-down menu, select Unassigned.
- Click OK.
- Wire Mode can be configured on WAN, LAN, DMZ, and custom zones (except wireless zones). Wire Mode is a simplified form of Layer 2 Bridged Mode, and is configured as a pair of interfaces. In Wire Mode, the destination zone is the Paired Interface Zone. Access rules are applied to the Wire Mode pair based on the direction of traffic between the source Zone and its Paired Interface Zone. For example, if the source Zone is WAN and the Paired Interface Zone is LAN, then WAN to LAN and LAN to WAN rules are applied, depending on the direction of the traffic.
- In Wire Mode, administrators can enable Link State Propagation, which propagates the link status of an interface to its paired interface. If an interface goes down, its paired interface is forced down to mirror the link status of the first interface. Both interfaces in a Wire Mode pair always have the same link status.
- In Wire Mode, administrators can Disable Stateful Inspection. When Disable Stateful Inspection is selected, Stateful Packet Inspection (SPI) is turned off. When Disable Stateful Inspection is not selected, new connections can be established without enforcing a 3-way TCP handshake. Disable Stateful Inspection must be selected if asymmetrical routes are deployed.
Configure for Bypass Mode
Bypass Mode allows for the quick and relatively non-interruptive introduction of the SonicWall into a network. Bypass Mode can be configured between a pair of interfaces. All traffic received is bridged to the paired interface. While Bypass Mode does not offer any inspection or firewalling, this mode allows the administrator to physically introduce the firewall into the network with a minimum of downtime and risk, and to obtain a level of comfort with the newly inserted component of the networking and security infrastructure.
How to configure:
- Login to the SonicWall Management GUI
- Navigate to Manage | Network | Interfaces page.
- Click on Configure on any one interface.
- Choose zone as LAN.
- Set Mode / IP Assignment as Wire Mode (2-Port Wire)
- Set Wire Mode Setting to Bypass Mode (via Internal Switch / Relay)
- Choose an unassigned interface under Set Paired Interface.
- The paired Interfaces must be of the same type. For example two 1 GB interfaces or two 10 GB interfces.
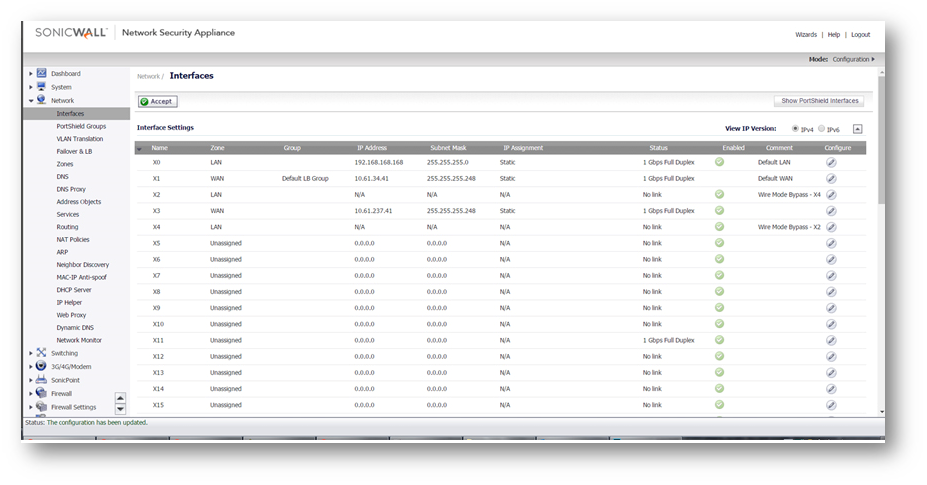
In the screenshot below, X4 Interface has been configured in Bypass Mode and paired with X3 Interface.
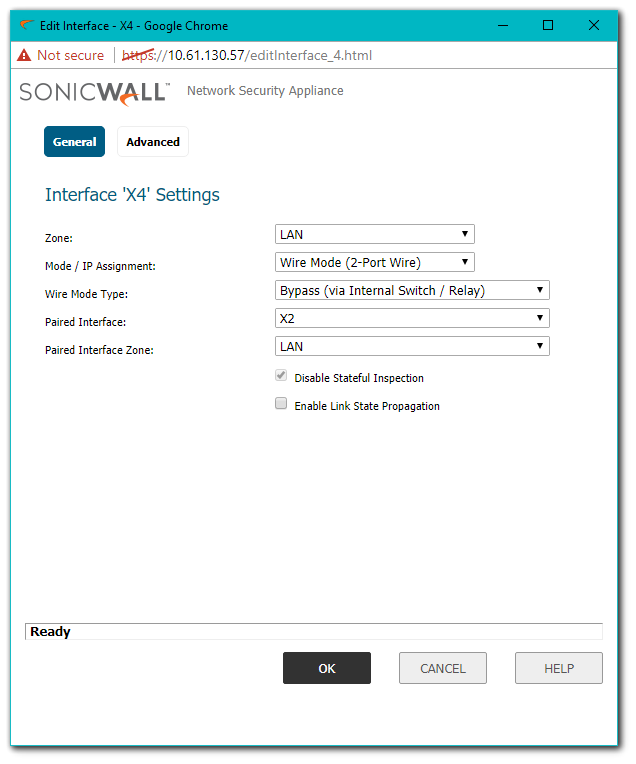
- In the screenshot below the X0 (LAN) Interface is in the 192.168.168.0 /24 Subnet.
- The X1 (WAN) is connected to an ISP router.
- The X3 & X4 are paired Interfaces in Wire + Bypass Mode.
- With such a configuration in place, hosts behind X0 will be able to go online through the X1 Interface.
- Now assuming another ISP router with an IP of 10.61.130.57 is connected to X3, hosts connected to X4, if configured with IP addresses in the subnet 10.61.130.57, go online through the X3 router.
Inspect Mode
Inspect Mode can be configured between a pair of interfaces. Packets continue to pass through the SonicWall to the paired interface, but they are also mirrored to the DPI engine for the purposes of passive inspection, classification, logging and flow reporting. There is full application threat detection and visualization, but no application control in Inspect Mode.
How to configure:
- Login to the SonicWall Management GUI
- Navigate to Manage | Network | Interfaces page.
- Click on Configure on any one interface.
- Choose zone as LAN.
- Set Mode / IP Assignment as Wire Mode (2-Port Wire)
- Set Wire Mode Setting to Inspect Mode (Passive DPI of Mirrored Traffic)
- Choose an unassigned interface under Set Paired Interface.
- The paired interfaces must be of the same type. For example two 1 GB interfaces or two 10 GB interfces.
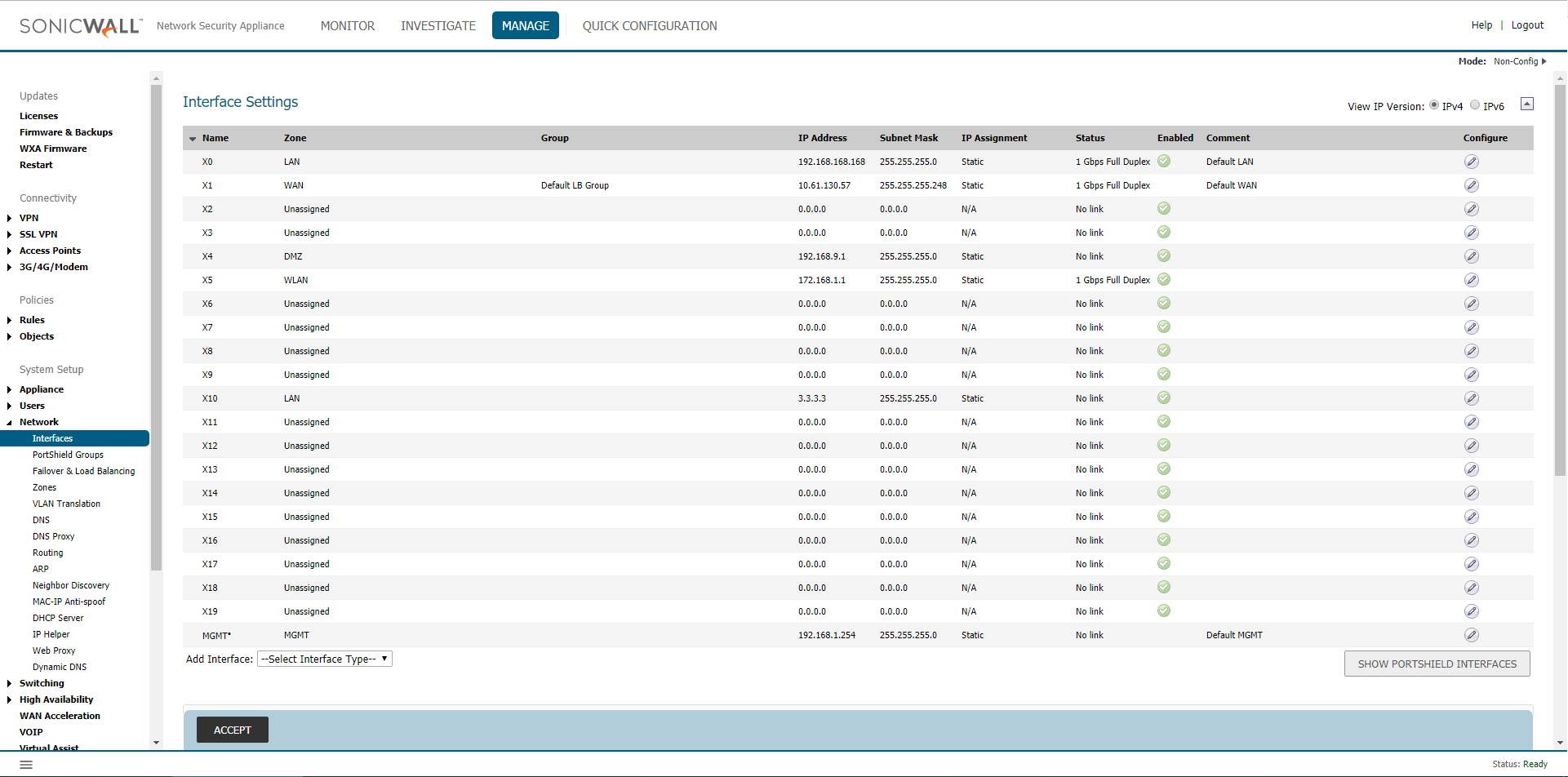
In the screenshot below, X2 Interface has been configured in Inspect Mode and paired with X6 Interface.
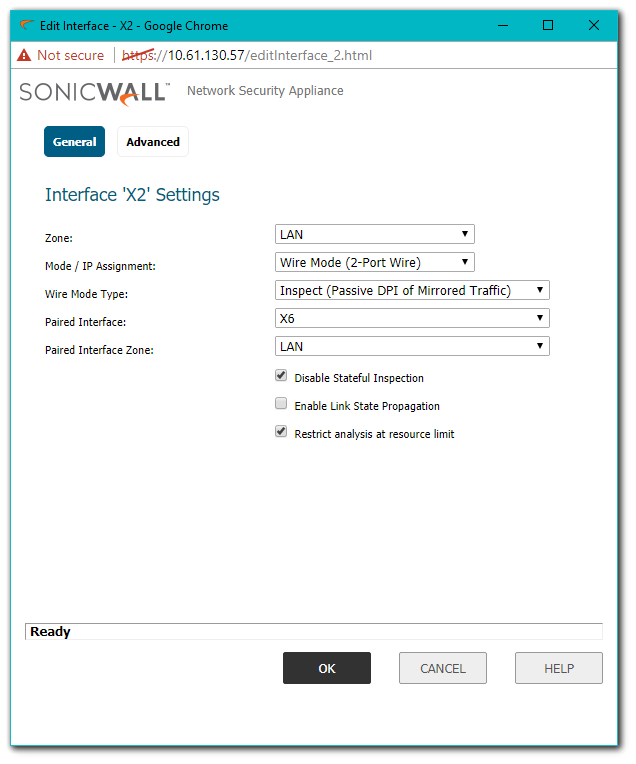
In Inspect Mode interesting traffic will be logged. For eg. if CFS or IPS Policies are defined to prevent specific traffic, the SonicWall will log them as blocked or prevented without actually doing so.
Secure Mode
Secure Mode is the progression of Inspect Mode, actively applying SonicWall Application Intelligence and Control, Intrusion Prevention Service, Gateway and Cloud-based Anti-Virus, Anti-Spyware and Content Filtering. Secure Mode affords the same level of visibility and enforcement as conventional NAT or L2 Bridge mode deployments, but without any L3/L4 transformations, and with no alterations of ARP or routing behavior. Secure Mode requires no logical, and only minimal physical, changes to existing network designs.
Secure Mode can be configured between a pair of interfaces. All traffic received is fully processed by the firewall. There is full application visualization and control in Secure Mode.
How to configure:
- Login to the SonicWall Management GUI
- Navigate to the Manage | Network | Interfaces page.
- Click on Configure on any one interface.
- Choose zone as LAN.
- Set Mode / IP Assignment as Wire Mode (2-Port Wire)
- Set Wire Mode Setting to Secure Mode (Active DPI of Inline Traffic)
- Choose an unassigned interface under Set Paired Interface.
- The paired interfaces must be of the same type. For example two 1 GB interfaces or two 10 GB interfces.
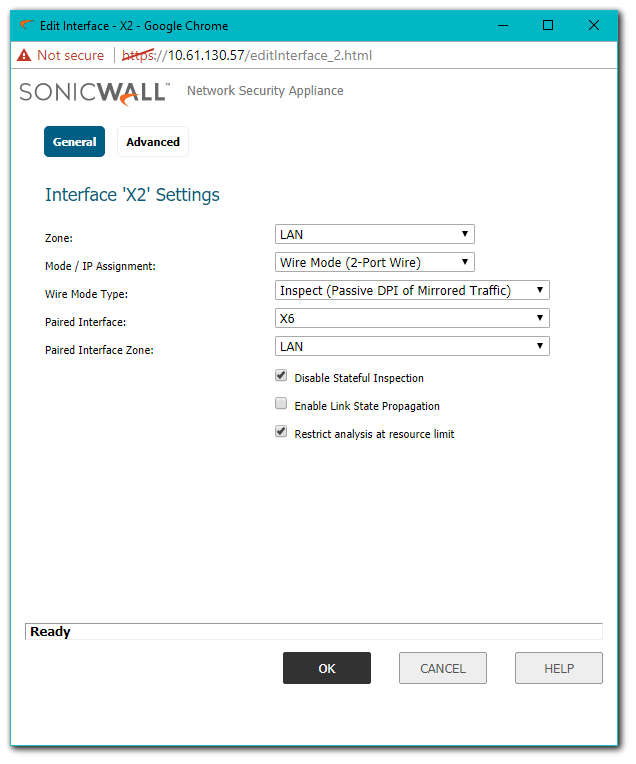
In the screenshot below, X2 Interface has been configured in Secure Mode and paired with X6 Interface.
Tap Mode
Tap Mode can be configured for a single interface. All traffic received is never sent out of the firewall, but the firewall performs full SPI and DPI processing. There is full application visualization, but no application control in Tap Mode. Typically, a mirror port is set up on the switch to mirror the network traffic to the firewall. Tap Mode provides the same visibility as Inspect Mode, but differs from the latter in that it ingests a mirrored packet stream via a single switch port on the SonicWall eliminating the need for physically intermediated insertion. Tap Mode is designed for use in environments employing network taps, smart taps, port mirrors, or SPAN ports to deliver packets to external devices for inspection or collection. Like all other forms of Wire Mode, Tap Mode can operate on multiple concurrent port instances, supporting discrete streams from multiple taps.
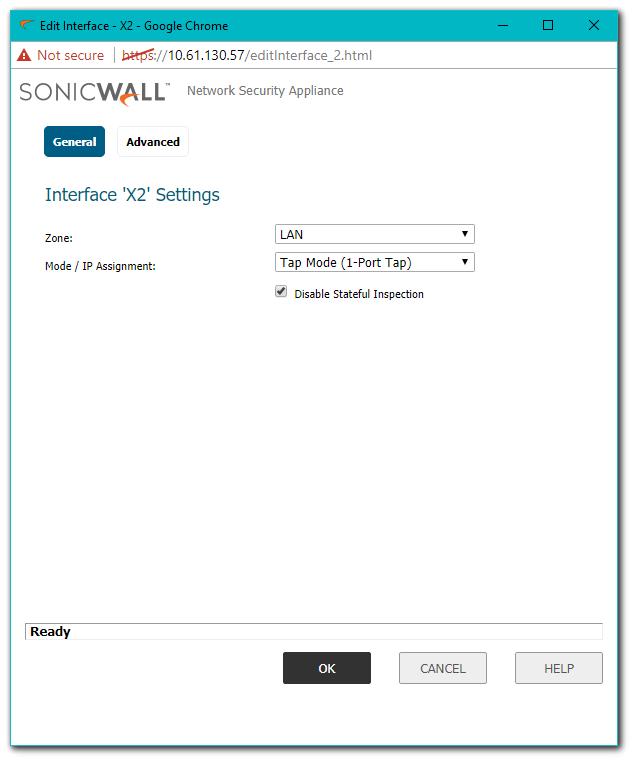
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
To configure an interface for Wire Mode, perform the following steps:
- On the Network | Interfaces page, click the Configure button for the interface you want to configure for Wire Mode.
- In the Zone pull-down menu, select any zone type except WLAN.
- To configure the Interface for Tap Mode, in the Mode / IP Assignment pull-down menu, select Tap Mode (1-Port Tap).
- To configure the Interface for Wire Mode, in the Mode / IP Assignment pull-down menu, select Wire Mode (2-Port Wire).
- In the Wire Mode Type pull-down menu, select the appropriate mode:
- Bypass (via Internal Switch/Relay)
- Inspect (Passive DPI of Mirrored Traffic)
- Secure (Active DPI of Inline Traffic)
- In the Paired Interface pull-down menu, select the interface that will connect to the upstream firewall. The paired interfaces must be of the same type (two 1 GB interfaces or two 10 GB interfaces).
Note: Only unassigned interfaces are available in the Paired Interface pull-down menu. To make an interface unassigned, click on the Configure button for it, and in the Zone pull-down menu, select Unassigned.
- Click OK.
- Wire Mode can be configured on WAN, LAN, DMZ, and custom zones (except wireless zones). Wire Mode is a simplified form of Layer 2 Bridged Mode, and is configured as a pair of interfaces. In Wire Mode, the destination zone is the Paired Interface Zone. Access rules are applied to the Wire Mode pair based on the direction of traffic between the source Zone and its Paired Interface Zone. For example, if the source Zone is WAN and the Paired Interface Zone is LAN, then WAN to LAN and LAN to WAN rules are applied, depending on the direction of the traffic.
- In Wire Mode, administrators can enable Link State Propagation, which propagates the link status of an interface to its paired interface. If an interface goes down, its paired interface is forced down to mirror the link status of the first interface. Both interfaces in a Wire Mode pair always have the same link status.
- In Wire Mode, administrators can Disable Stateful Inspection. When Disable Stateful Inspection is selected, Stateful Packet Inspection (SPI) is turned off. When Disable Stateful Inspection is not selected, new connections can be established without enforcing a 3-way TCP handshake. Disable Stateful Inspection must be selected if asymmetrical routes are deployed.
Configure for Bypass Mode
Bypass Mode allows for the quick and relatively non-interruptive introduction of the SonicWall into a network. Bypass Mode can be configured between a pair of interfaces. All traffic received is bridged to the paired interface. While Bypass Mode does not offer any inspection or firewalling, this mode allows the administrator to physically introduce the firewall into the network with a minimum of downtime and risk, and to obtain a level of comfort with the newly inserted component of the networking and security infrastructure.
How to configure:
- Login to the SonicWall Management GUI
- Navigate to the Network | Interfaces page.
- Click on Configure on any one interface.
- Choose zone as LAN.
- Set Mode / IP Assignment as Wire Mode (2-Port Wire)
- Set Wire Mode Setting to Bypass Mode (via Internal Switch / Relay)
- Choose an unassigned interface under Set Paired Interface.
- The paired interfaces must be of the same type. For example two 1 GB interfaces or two 10 GB interfces.
In the screenshot below, X3 interface has been configured in Bypass Mode and paired with X4 interface.
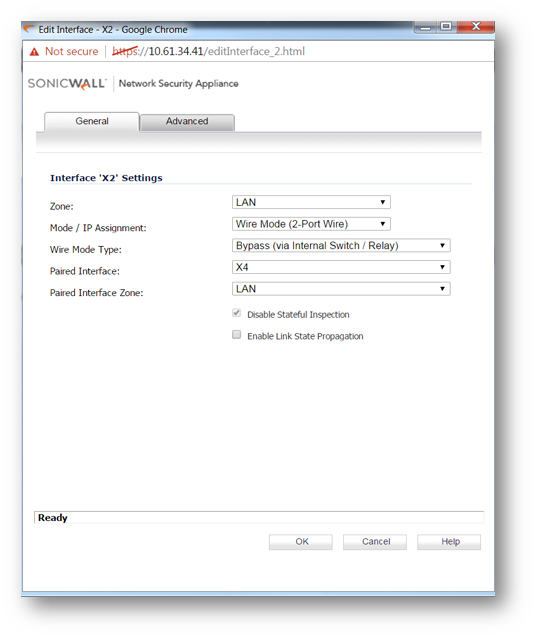
- In the screenshot below the X0 (LAN) interface is in the 192.168.168.0/24 subnet.
- The X1 (WAN) is connected to an ISP router.
- The X3 & X4 are paired interfaces in Wire + Bypass Mode.
- With such a configuration in place, hosts behind X0 will be able to go online through the X1 interface.
- Now assuming another ISP router with an IP of 1.1.1/24 is connected to X3, hosts connected to X4, if configured with IP addresses in the subnet 1.1.1.0/24, go online through the X3 router.
Inspect Mode
Inspect Mode can be configured between a pair of interfaces. Packets continue to pass through the SonicWall to the paired interface, but they are also mirrored to the DPI engine for the purposes of passive inspection, classification, logging and flow reporting. There is full application threat detection and visualization, but no application control in Inspect Mode.
How to configure:
- Login to the SonicWall Management GUI
- Navigate to the Network | Interfaces page.
- Click on Configure on any one interface.
- Choose zone as LAN.
- Set Mode / IP Assignment as Wire Mode (2-Port Wire)
- Set Wire Mode Setting to Inspect Mode (Passive DPI of Mirrored Traffic)
- Choose an unassigned interface under Set Paired Interface.
- The paired interfaces must be of the same type. For example two 1 GB interfaces or two 10 GB interfces.
In the screenshot below, X3 interface has been configured in Inspect Mode and paired with X4 interface.
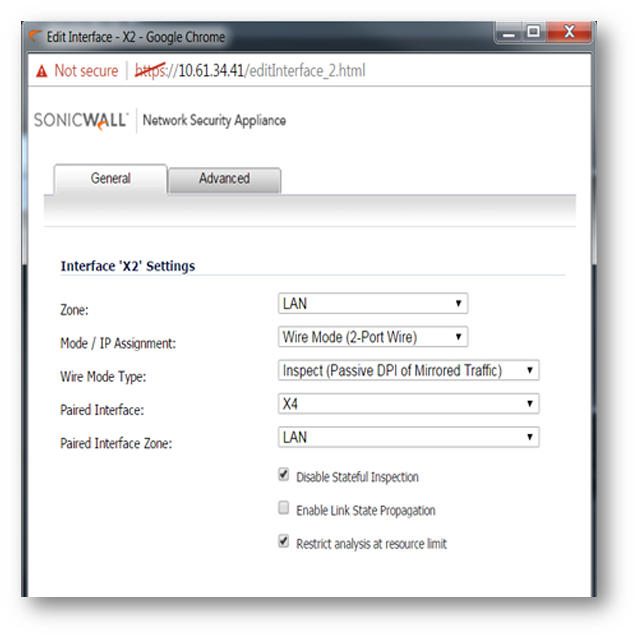
In Inspect Mode interesting traffic will be logged. For eg. if CFS or IPS Policies are defined to prevent specific traffic, the SonicWall will log them as blocked or prevented without actually doing so.
Secure Mode
Secure Mode is the progression of Inspect Mode, actively applying SonicWall Application Intelligence and Control, Intrusion Prevention Service, Gateway and Cloud-based Anti-Virus, Anti-Spyware and Content Filtering. Secure Mode affords the same level of visibility and enforcement as conventional NAT or L2 Bridge mode deployments, but without any L3/L4 transformations, and with no alterations of ARP or routing behavior. Secure Mode requires no logical, and only minimal physical, changes to existing network designs.
Secure Mode can be configured between a pair of interfaces. All traffic received is fully processed by the firewall. There is full application visualization and control in Secure Mode.
How to configure:
- Login to the SonicWall Management GUI
- Navigate to the Network | Interfaces page.
- Click on Configure on any one interface.
- Choose zone as LAN.
- Set Mode / IP Assignment as Wire Mode (2-Port Wire)
- Set Wire Mode Setting to Secure Mode (Active DPI of Inline Traffic)
- Choose an unassigned interface under Set Paired Interface.
- The paired interfaces must be of the same type. For example two 1 GB interfaces or two 10 GB interfces.
In the screenshot below, X3 interface has been configured in Secure Mode and paired with X4 interface.

Tap Mode
Tap Mode can be configured for a single interface. All traffic received is never sent out of the firewall, but the firewall performs full SPI and DPI processing. There is full application visualization, but no application control in Tap Mode. Typically, a mirror port is set up on the switch to mirror the network traffic to the firewall. Tap Mode provides the same visibility as Inspect Mode, but differs from the latter in that it ingests a mirrored packet stream via a single switch port on the SonicWall eliminating the need for physically intermediated insertion. Tap Mode is designed for use in environments employing network taps, smart taps, port mirrors, or SPAN ports to deliver packets to external devices for inspection or collection. Like all other forms of Wire Mode, Tap Mode can operate on multiple concurrent port instances, supporting discrete streams from multiple taps.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > Networking
- Firewalls > SonicWall NSA Series > Networking
- Firewalls > TZ Series > Networking






 YES
YES NO
NO