-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to configure DMARC reporting on SonicWall Email Security version 8.0 and higher



Description
What is DMARC:
Resolution
How to configure email security to receive DMRAC reports:
In order to receive DMRAC reports you should be having valid DKIM and SPF/TXT records created for your domain.
To Learn more visit:
To enable/utilize DMARC reporting for incoming threats on SonicWall Email Security (Version 8.0 onwards) SPF and DKIM both features should be enabled.
Configuring Inbound DMARC Settings:
Domain-based Message Authentication, Reporting & Conformance (DMARC) is a policy that works in tandem with SPF and DKIM to fully authenticate incoming and outgoing email
messages. A DMARC policy allows a sender to indicate that his emails are protected by SPF and/or DKIM, and also tells a receiver what to do if neither of those authentication methods passes, such as junk or reject the message.
To configure DMARC settings, navigate to the Anti-Spoofing | Inbound page, and click the
Enable DMARC Policy Enforcement for incoming messages checkbox.![]() Note - To use DMARC, you must also have DKIM and SPF enabled.
Note - To use DMARC, you must also have DKIM and SPF enabled. Configure the following settings for DMARC:
Configure the following settings for DMARC:
- Exclude these sender domains Enter any sender domains (for example, SonicWall.com or Gmail.com) you want excluded from DMARC policy enforcement in the space provided. Multiple domains can be entered, separated by a comma.
- Enable DMARC Outgoing Reports By default, this feature is enabled when the Enable DMARC checkbox is also enabled. Select the checkbox to disable the sending of DMARC reports to outside domains.
Once DMARC is enabled, outgoing reports are automatically sent. The following settings can be configured if you are attempting to override reporting attributes for a specific domain:
- Domain Enter the domain name to send DMARC reports to. You have the option of using * as a value for the domain field. A few considerations:
If the domain is not provided, DMARC will use configuration settings from the * domain.
If no * domain is added, then a hard-coded default value, such as postmaster@domain, will be used as the Sender ID.
- Override DNS RUA Email Address Click the checkbox to override reports being sent to the RUA email address specified in the DNS record. An example from the DNS record is rua=mailto:aggrep@yourcompany.com .
- RUA Email Address If you selected the Override DNS RUA Email Address, specify the RUA Email Address you would like the reports sent to.
![]() Note- The RUA is the aggregated report for domains with published domain records. Reports are sent daily.
Note- The RUA is the aggregated report for domains with published domain records. Reports are sent daily. DMARC Incoming Reports:
DMARC Incoming Reports:
You can configure DMARC Incoming Report settings by clicking the Add Domain button in the DMARC Incoming Reports Settings section. DMARC Incoming Reports will be collected and processed only for the domains added.
In the Add Domain window that displays, enter the following information:
Domain Enter the domain name to add for DMARC incoming reports.
Override DNS RUA Email Address Click the checkbox to override reports being sent to the RUA email address specified in the DNS record. An example from the DNS record is rua=mailto:aggrep@yourcompany.com .
RUA Email Address If you selected the Override DNS RUA Email Address, specify the RUA Email Address to which the reports are being sent.![]() Note - The RUA is the aggregated report for domains with published domain records. Reports are sent daily.
Note - The RUA is the aggregated report for domains with published domain records. Reports are sent daily. DMARC Reporting:
DMARC Reporting:
The following report types are available in the DMARC Reports section of the Email Security management interface: DMARC Reports and Configure Known Networks.
DMARC Reports:
When the Email Security Mail Server plays the role as email sender and RUA receiver, it extracts and aggregates daily RUA files from the email receiver and from RUA providers, such as Google, Yahoo, etc. The DMARC Reporting Scheduler then imports the RUA files hourly into its database.
Based on date range and data filter, you can obtain five different types of reports: One report is graphic chart. The other four are tabulated reports.
The Reports include:
- DMARC Statistic Report (Graphic Chart)
- DMARC Master Detail Report
- Source IP Aggregation Report
- Provider Aggregation Report
- Source IP and Provider Aggregation Report
All five reports are able to be rendered in HTML format and downloadable PDF file. (HTML reports allow you to mouse over 'Alignment' value to see alignment reason description.)
SonicWall recommends that the administrator enters the IP addresses of 'my server' on the 'Configure Known Networks' page before users (admin or manager role) view DMARC Reports because it retrieves reports data associated with those IP addresses by default.
Select Date Range:
Last x days Click the radio button for Last and select from the drop-down list of values. Last x days means the number of day(s) before the latest date of imported data.
Start Date and End Date Click the radio button to specify the dates. If no RUA data is in the database, the pop-up calendar displays the current date. If RUA data exists in the database, the calendar dates before the minimum date and after the maximum date display. Only data available on those available dates can be selected.
Set Filter:
- Filter???Click this button to create a new filter. If a filter already exists, clicking this button allows you to edit the filter. See the Set Filter page for more information.
- Save???After creating a new filter, click this button to save the newly configured settings.
- Clear???Clears all settings of the current filter.
- Apply Filter???Select from a drop-down list of the available filters. When selected, its bulleted settings display in the Filter section.
- Delete???To delete a filter, select it from the Apply Filter drop-down list and click this button.
- Bullet icons???Each bullet icon represents a filter condition. Click the condition to open the Set Filter dialog box, or click the small 'x' symbol on bullet to delete the condition from the filter.
- Select Report list???Select a type of report from the drop-down list. The available reports include: DMARC Statistic Report, DMARC Master Detail Report, Source IP Aggregation Report,Provider Aggregation Report, Source IP and Provider Aggragation Report.
- Generate???After selecting a report from the drop-down list, click this button to generate a report. Note: Some reports may take a few minutes to generate.
Reports will be shown in a window below the 'Set Filters' section.
For the statistic report, it will display either horizontally or vertically, depending on the date range. If days of selected date range are less than 15 days, three (3) bar charts will be
horizontally display. If the date range is greater than 15 days, the bar charts will vertically display. For tabulated reports, scrolling the mouse over the 'Alignment' value displays the
Alignment Reason. For example, if the 'Alignment' is 'No', moving the mouse over this 'No' makes the Title Box show: "No DKIM and SPF is passed, On SPF Relaxed, SPF Organization
Domain(sina.com) Not Matched From Header Domain(SonicWall.com)" This message will be useful for DMARC troubleshooting.
Download PDF Report???Click the button to download a PDF report once the HTML report is generated. The PDF report name includes the Report Name and a time stamp.
Configure Known Networks:
There are two types of Known Networks you can configure: My Servers and External Trusted Servers.
My Servers:
- This is usually the list of company-owned IP addresses, labeled in the server group as 'my servers.'
- When setting the filter to generate a DMARC report, you have the option to select My Servers from the Known Network group. By default, all the IP addresses in the My Servers group are Included for the filter. Select Exclude to exclude the IP addresses in the My Servers group.
- If you choose not to use My Servers, you can set the filter to Source IP, and will have to manually enter the Source IP addresses to include in the report.
External trusted servers:
This is the list of IP addresses of company-trusted external servers and customers, labelled as 'external trusted servers.'
Note that this is not a default condition. When setting the filter to generate a DMARC report, you can select External trusted servers from the Known Network group. Using include or exclude, you can select which IP addresses to view for the filter.
??? Add???Add a new server group and its respective IP addresses. You can add either 'My servers' or 'External trusted servers.'
??? Edit???Edit the Server Group label and its respective IP addresses.
??? Delete???Delete the Server Group label and its respective IP addresses.
Example of DMARC reports:
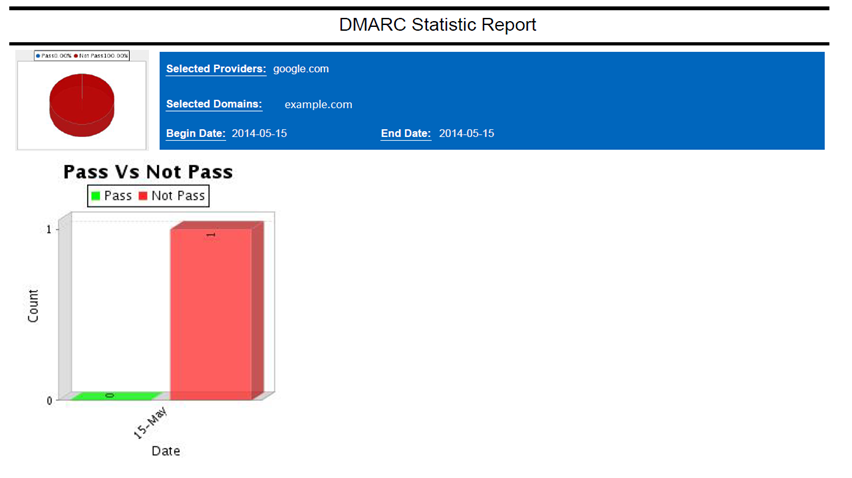

Related Articles
- Email Security: How to download the Outlook Junk Tool?
- Configuring SonicWall Email Security to Ensure Maximum effectiveness, High Throughput
- How to exclude the domain from DHA scanning?
Categories
- Email Security > Email Security Appliance
- Email Security > Email Security Software
- Email Security > Hosted Email Security






 YES
YES NO
NO