-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to Configure Custom Policies for SonicWall Enforced Client



Description
SonicWall Enforced Kaspersky Client Anti-Virus and Anti-Spyware provides comprehensive end-point protection for desktops and laptops. The automated anti-virus and anti-spyware deployment keeps administrative overhead to a minimum, while also enforcing policy and making sure that each endpoint is protected before connecting. Kaspersky Client Anti-Virus and Anti-Spyware has the following features:
- Protects Desktops/Laptops from viruses.
- Automatically updates clients
- Enforces virus protection
- Centrally manages reporting
- Central manages policy-enforcement.
- Includes on-demand scanning
This article illustrates how to create Enforced Client AV (ECAV) policies.
Resolution
The following steps are involved in creating a new ECAV policy:
1. Accessing the Enforced Client Anti-Virus Policy & Reporting Server.
- Login the SonicWall Management GUI.
- Navigate to the Security Services | Client AV Enforcement page.
- Click on the link under the Kaspersky Client AV Status box.
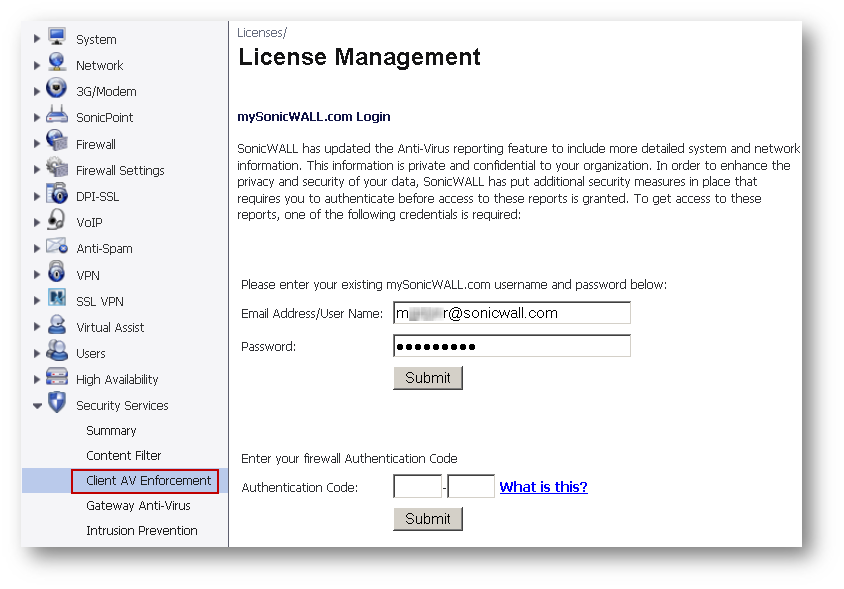
 Login using the MySonicWall.com username and password or using the appliance Authentication Code. In the SonicWall EPRS page, click on Policies.
Login using the MySonicWall.com username and password or using the appliance Authentication Code. In the SonicWall EPRS page, click on Policies.
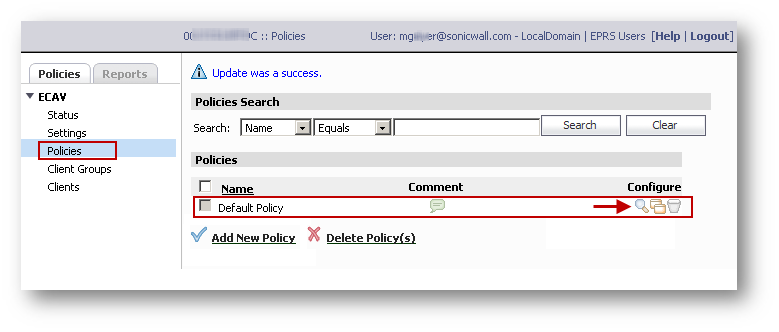
About the Default Policy
The Policies page contains a default policy called Default Policy. The Default Policy is configured to be moderately strict, and is suitable for use with most ECAV clients. It cannot be edited or deleted. All clients and client groups are assigned the default policy. To view the Default Policy settings, navigate to the ECAV | Policies page and click the View icon under Configure in the Default Policy row.


Exclusions Tab
On the Exclusions tab, filters are configured to exclude .txt and .log files from scanning.
Inclusions Tab
On the Inclusions tab, no filters are configured to include certain files or folders when scanning.
Processes Tab
On the Processes tab, no applications are configured as trusted applications with defined behaviors.
Default Manual Scan Settings
Settings Tab
On the Settings tab of the Manual Scan Settings window, the File Scan Settings are shown.
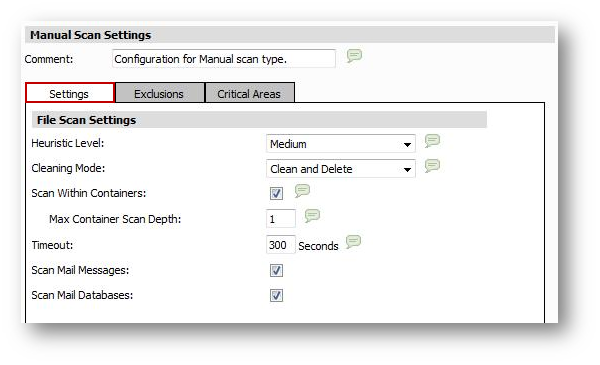
For the Default Policy, the File Scan Settings for Scheduled File Scan are set as follows:
- Heuristics Level The Heuristics Level is set to Medium. The advanced heuristic code analyzer is on, with medium scanning level. For a manual scan that only occurs when requested by the user, the Medium setting is fine and will not impact system performance.
- Cleaning Mode Currently, Clean and Delete is the only option for handling detected threats.
- Scan Within Containers This checkbox is selected to open and scan the contents of container files, such as ZIP or CAB files. The Max Container Scan Depth is set to 1, indicating that only the first level of container will be scanned, and no containers within the container are scanned.
- Timeout The maximum number of seconds that a file will be scanned is set to 300 seconds.
- Scan Mail Messages This checkbox is selected to scan email messages.
- Scan Mail Databases This checkbox is not selected, so no email databases will be scanned.
Exclusions Tab
On the Exclusions tab, filters are configured to exclude .txt and .log files from scanning.

 Schedule Tab
Schedule Tab
On the Schedule tab, a time based schedule is configured for the scan. 
 Schedule Tab
Schedule Tab
On the Schedule tab, a time based schedule is configured for the Critical Areas scheduled scan.  Adding a New Policy
Adding a New Policy
A new policy can be created by either clicking on Add New Policy or cloning the default policy. To clone, click on the Clone button at the far end of the default policy.
 General tab
General tab
Name: Enter a name for the policy.
Comment: Descriptive information about the policy.
 Kaspersky AV tab
Kaspersky AV tab
Agent Version: Stable Release
OnAccess: Pre-installed scan type to always monitor the system in the background for malware. Cannot be deleted
Manual: Pre-installed scan type to scan files, folders and removable disks when prompted to do so. Cannot be deleted
Add New Scheduled Scan: User created scan type to scan the system at a scheduled time.
 2. OnAccess Scan
2. OnAccess Scan
- Comment: Descriptive information.
- Disable: Disables OnAccess Scan
- Settings
- Exclusions
- Inclusions
- Processes

- Heuristic Level: Off / Low / Medium /High. Default = Medium
- Cleaning Mode: Clean and Delete.
- Working Mode: Smart / File Open / File Execute / Both File Read and Write. Default = Smart
- Scan Within Containers: Contents of ZIP / CAB etc will be opened and scanned. Default = Unchecked.
- Max Archive File Size: Applicable if above is checked. Default is 8 MB. 0 means no maximum size.
- Timeout = Default = 3 Seconds. 0 = No timeout.
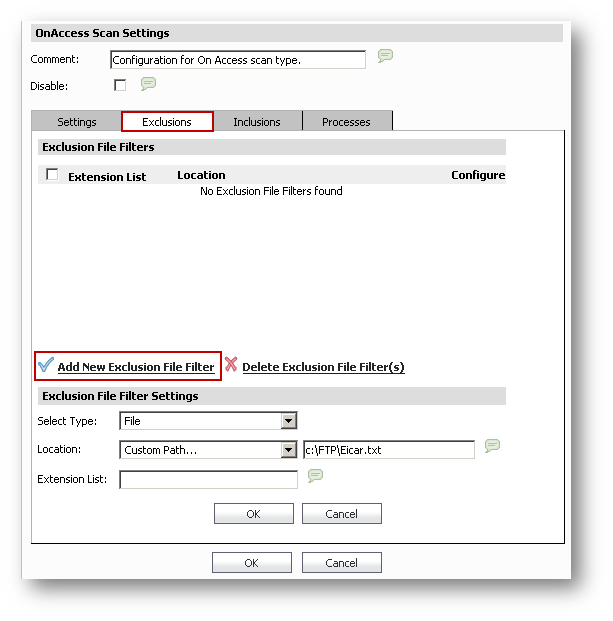
Select Type: File / Folder
Location:
- Custom Path
- Fixed and removable Disks
- All fixed disks
- All removable disks
- OS installed drive
- Documents and Settings folder
- Program Files folder
- Windows directory
- Windows system directory
Extension List: List of extensions that will be matched when searching for files to filter. Do not precede the extension with "." or "*." Wildcards are permitted at the end of an extension such as DOC XL* PPT.

Location:
- Custom Path
- Fixed and removable Disks
- All fixed disks
- All removable disks
- OS installed drive
- Documents and Settings folder
- Program Files folder
- Windows directory
- Windows system directory
Extension List: List of extensions that will be matched when searching for files to filter. Do not precede the extension with "." or "*." Wildcards are permitted at the end of an extension such as DOC XL* PPT.
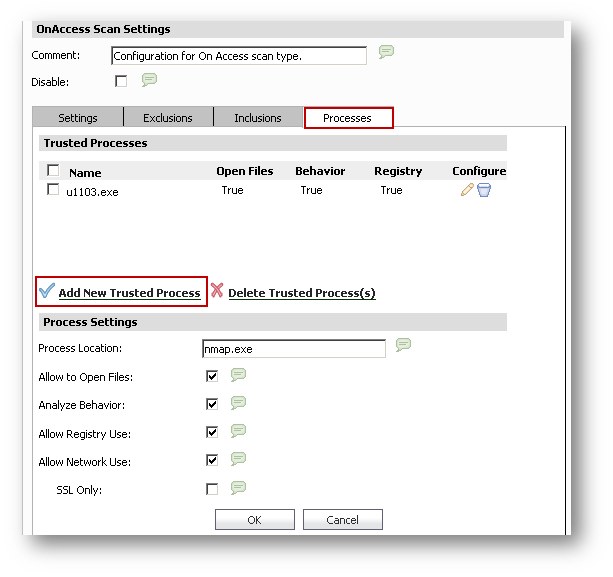
Process Location:
Allow to Open Files:
Analyze Behavior:
Allow Registry Use:
Allow Network Use:
SSL Only:
- Comment: Descriptive information.
- Settings
- Exclusions
- Critical Areas
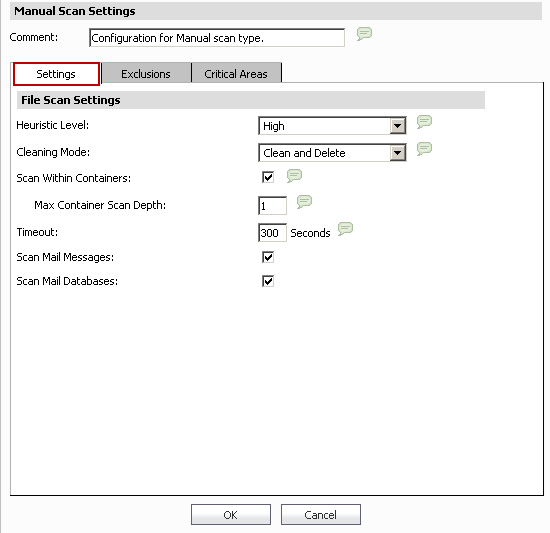
- Heuristic Level:
- Off / Low / Medium /High. Default = Medium
- Cleaning Mode: Clean and Delete.
- Scan Within Containers: Contents of ZIP / CAB etc will be opened and scanned.Default = checked.
- Max Container Scan Depth: Max level of containers within containers. For example, ZIP inside of a RAR inside of a TAR. Can be set from 1 to 10. 0 = No depth. Default = 1.
- Timeout = Default = 300 Seconds. 0 = No timeout.
- Scan Mail Messages:
- Scan Mail Databases:
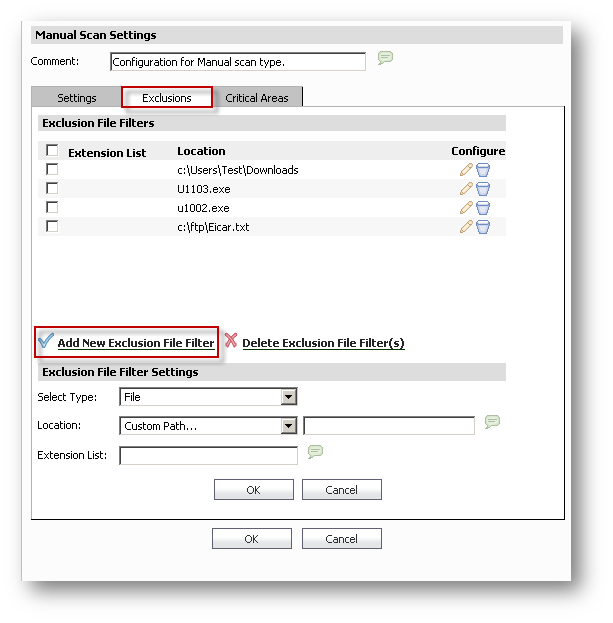
Select Type: File / Folder
Location:
- Custom Path
- Fixed and removable Disks
- All fixed disks
- All removable disks
- OS installed drive
- Documents and Settings folder
- Program Files folder
- Windows directory
- Windows system directory
Extension List: List of extensions that will be matched when searching for files to filter. Do not precede the extension with "." or "*." Wildcards are permitted at the end of an extension such as DOC XL* PPT.
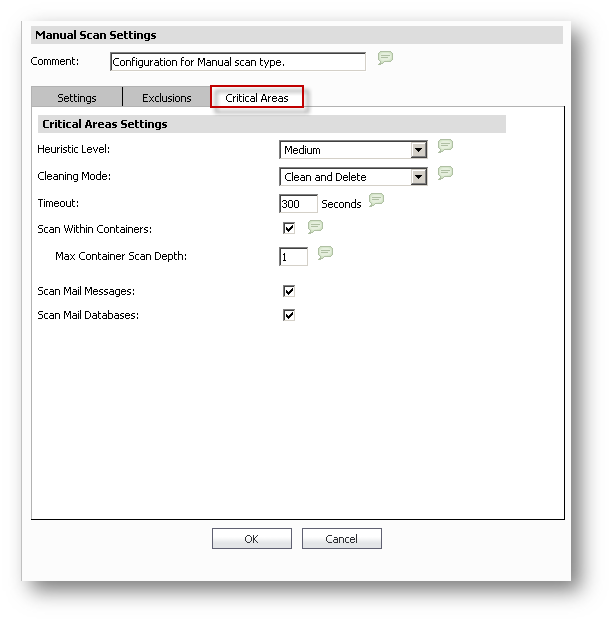
- Heuristic Level: Off / Low / Medium /High. Default = Medium
- Cleaning Mode: Clean and Delete.
- Scan Within Containers: Contents of ZIP / CAB etc will be opened and scanned.Default = checked.
- Max Container Scan Depth: Max level of containers within containers. For example, ZIP inside of a RAR inside of a TAR. Can be set from 1 to 10. 0 = No depth. Default = 1.
- Timeout: Default = 300 Seconds. 0 = No timeout.
- Scan Mail Messages:
- Scan Mail Databases:
 Settings
Settings
Exclusions Inclusions Schedule 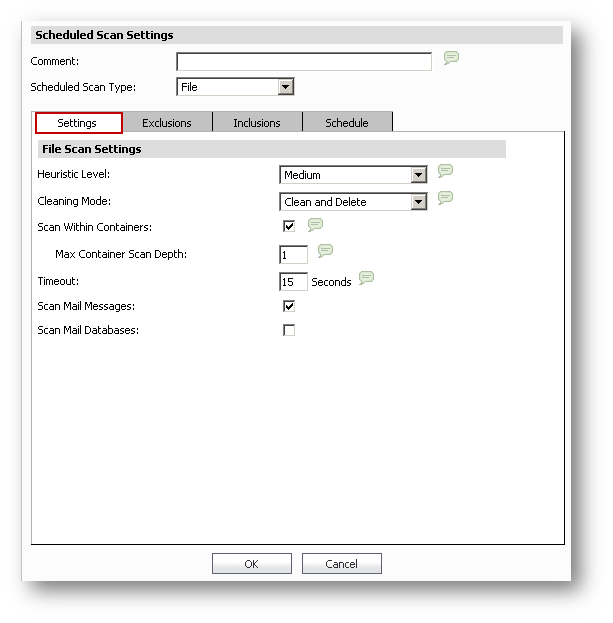
- Heuristic Level:
- Off / Low / Medium /High. Default = Medium
- Cleaning Mode: Clean and Delete.
- Scan Within Containers: Contents of ZIP / CAB etc will be opened and scanned.Default = checked.
- Max Container Scan Depth: Max level of containers within containers. For example, ZIP inside of a RAR inside of a TAR. Can be set from 1 to 10. 0 = No depth. Default = 1.
- Timeout = Default = 300 Seconds. 0 = No timeout.
- Scan Mail Messages:
- Scan Mail Databases:
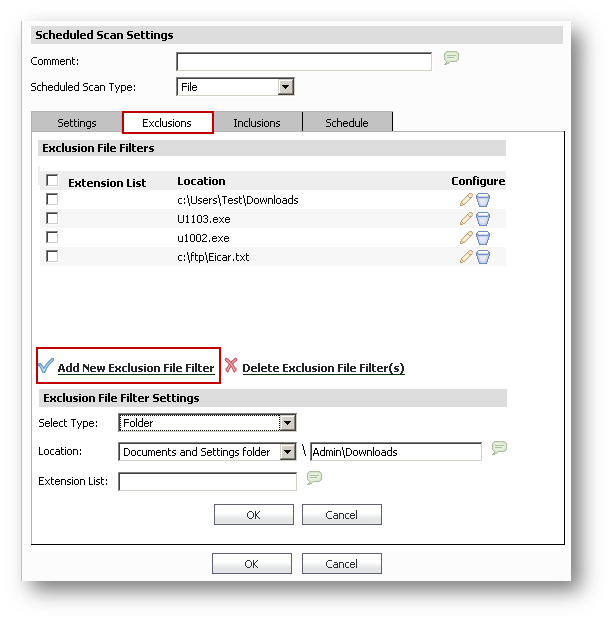
Exclusion File Filter Settings
Select Type: File / Folder
Location:
- Custom Path
- Fixed and removable Disks
- All fixed disks
- All removable disks
- OS installed drive
- Documents and Settings folder
- Program Files folder
- Windows directory
- Windows system directory
Extension List: List of extensions that will be matched when searching for files to filter. Do not precede the extension with "." or "*." Wildcards are permitted at the end of an extension such as DOC XL* PPT.
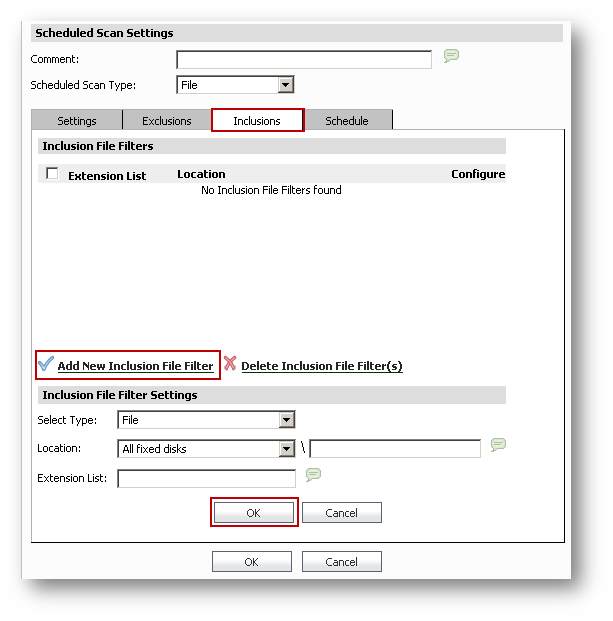
Select Type: File / Folder
Location:
- Custom Path
- Fixed and removable Disks
- All fixed disks
- All removable disks
- OS installed drive
- Documents and Settings folder
- Program Files folder
- Windows directory
- Windows system directory
Extension List: List of extensions that will be matched when searching for files to filter. Do not precede the extension with "." or "*." Wildcards are permitted at the end of an extension such as DOC XL* PPT.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series
Not Finding Your Answers?
ASK THE COMMUNITY
Was This Article Helpful?

 Schedule Tab
Schedule TabOn the Schedule tab, a time based schedule is configured for the Critical Areas scheduled scan.
 Adding a New Policy
Adding a New Policy
A new policy can be created by either clicking on Add New Policy or cloning the default policy. To clone, click on the Clone button at the far end of the default policy.
 General tab
General tab
Name: Enter a name for the policy.
Comment: Descriptive information about the policy.
 Kaspersky AV tab
Kaspersky AV tab
Agent Version: Stable Release
OnAccess: Pre-installed scan type to always monitor the system in the background for malware. Cannot be deleted
Manual: Pre-installed scan type to scan files, folders and removable disks when prompted to do so. Cannot be deleted
Add New Scheduled Scan: User created scan type to scan the system at a scheduled time.
 2. OnAccess Scan
2. OnAccess Scan
- Comment: Descriptive information.
- Disable: Disables OnAccess Scan
- Settings
- Exclusions
- Inclusions
- Processes

|
 | Select Type: File / Folder Location:
|
 | Location:
|
 | Process Location: Allow to Open Files: Analyze Behavior: Allow Registry Use: Allow Network Use: SSL Only: |
- Comment: Descriptive information.
- Settings
- Exclusions
- Critical Areas
 |
|
 | Select Type: File / Folder Location:
|
 |
|
 Settings
Settings
 |
|
 | Exclusion File Filter Settings Select Type: File / Folder Location:
|
 | Select Type: File / Folder Location:
|
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series







 YES
YES NO
NO