-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to Block UltraSurf (From 11.03 onwards) using Application Control Advanced and DPI-SSL



Description
Ultrasurf allows end users to circumvent gateway security devices like web filters and secure web gateways in order to surf the Internet without restrictions.
Resolution
This article describes how to block UltraSurf versons 11.03 and above using App Control Advanced signatures.
Please Note: SID 7 is a firmware-based App Control signature and requires SonicOS 5.8.1.8-57o and above
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
This article describes how to block UltraSurf versons 11.03 and above using App Control Advanced signatures.
Summary of configuration required to effectively block UltraSurf
- Enable DPI-SSL Client Inspection (CI)
- Enable Application Firewall under DPI-SSL CI
- Enable App Control Advanced signatures (see list below)
The following table lists the application group or the signature IDs used to block UltraSurf:
| Category | Application Name | Signature Name | Signature ID |
| PROXY-ACCCESS | Encrypted Key Exchange | Random Encryption(Skype,UltraSurf,Emule) | 5 |
| PROXY-ACCCESS | Encrypted Key Exchange | UDP Random Encryption(UltraSurf) | 7 |
| PROXY-ACCCESS | Non-SSL Traffic over SSL Port | Traffic Anomaly Detection | 6 |
| PROXY-ACCCESS | UltraSurf | UltraSurf Application Group | |
| PROXY-ACCCESS | HTTP Proxy | HTTP Proxy Application Group |
NOTE
Enabling the above signatures has the unintended consequence of blocking outbound encrypted UDP packets which includes Skype traffic, SonicWall GVC connections and/or encrypted Syslog traffic to a GMS server. This is due to SID # 7 which blocks encrypted UDP packets. In the case of GVC connections this shouldn't be considered a drawback. Instead, it's a way to control unauthorised outbound VPN connections. Administrators can exclude remote gateway IP addresses and/or GMS server IP address from SID # 7.
This article illustrates how to enable the above signatures and how to exclude IP addresses from SID # 7.
Procedure:
Enabling DPI-SSL Client Inspection
NOTE:
Enabling DPI-SSL Client Inspection would entail a restart of the appliance; thereafter, DPI-SSL would re-sign all SSL/TLS connections passing through it. This could cause disruption in the network. Read the following article before enabling DPI-SSL CI : How to Configure Client DPI-SSL (Video Tutorial and KB Article)
- Login to the SonicWall Management GUI.
- Click Manage in the top navigation menu.
- Navigate to Security Configuration | Deep packet Inspection | SSL Client Deployment
- Under General tab, enable the check box Enable SSL Client Inspection
- Enable the check box against Application Firewall
- Click on Accept at the top to save the changes
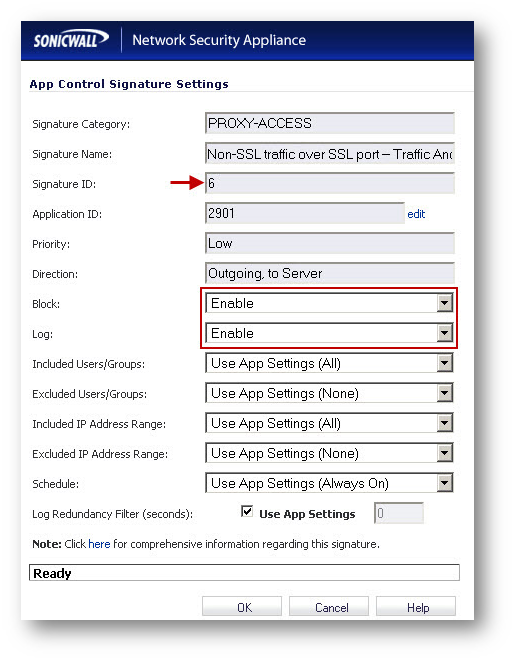
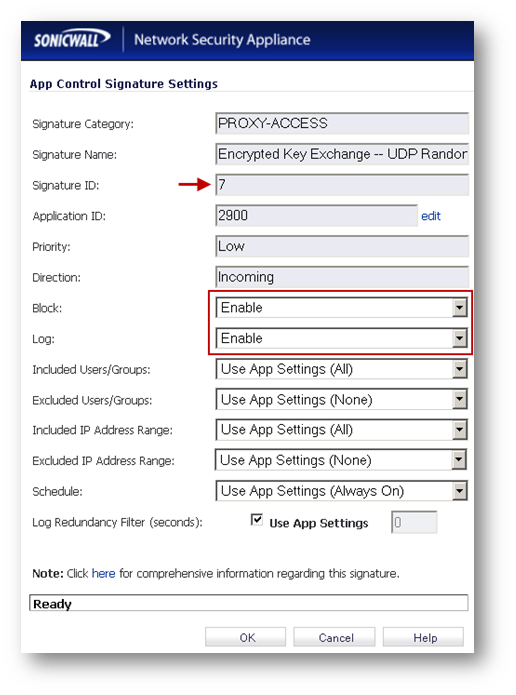
Enabling Signature ID 5,6 & 7.
- Click Manage in the top navigation menu.
- Navigate to the Policies | Rules | Advanced Application Control
- Check the box against Enable App Control
- Under Lookup Signature ID, enter 5, 6 and 7 one after another and click on the configure button for each signature.
- In the Edit App Control Signature window, set Block and Log to Enable.
- Click on OK to save the settings.
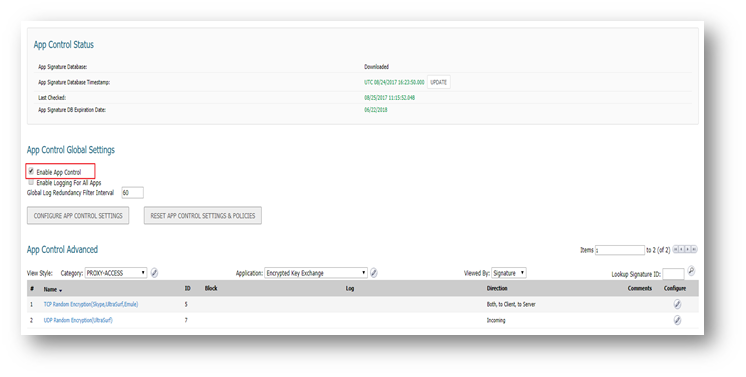
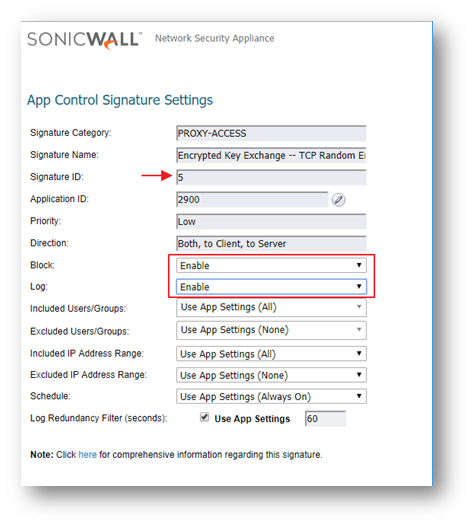
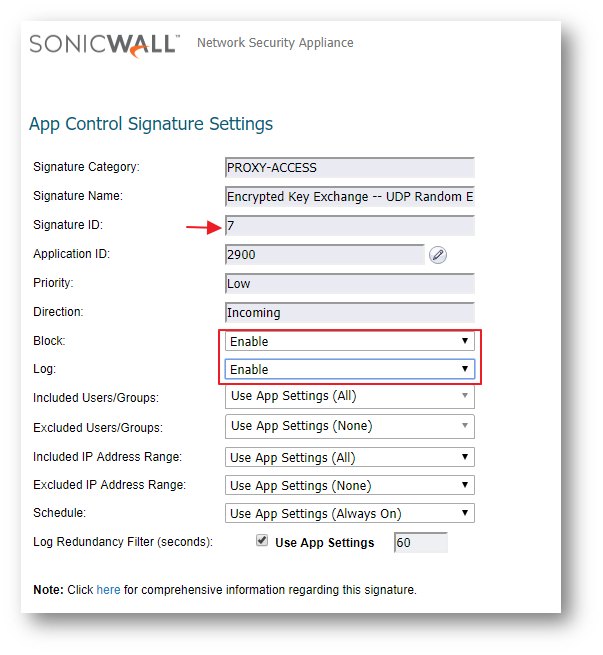
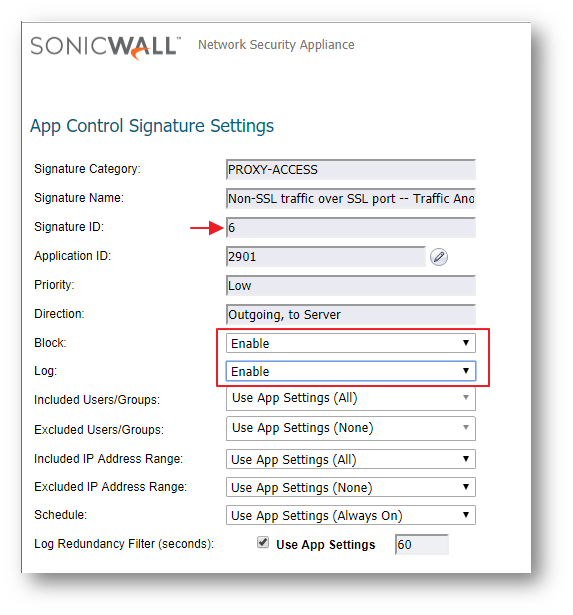
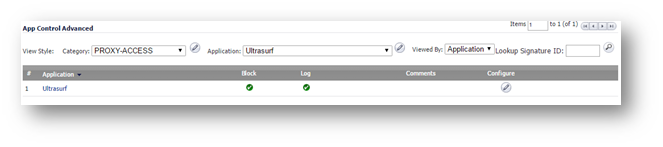
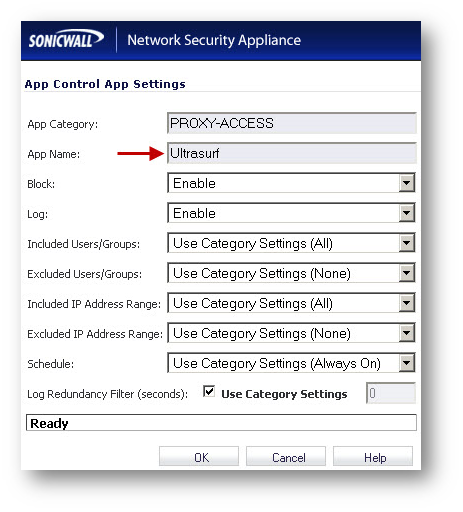
Enabling Application Block - UltraSurf
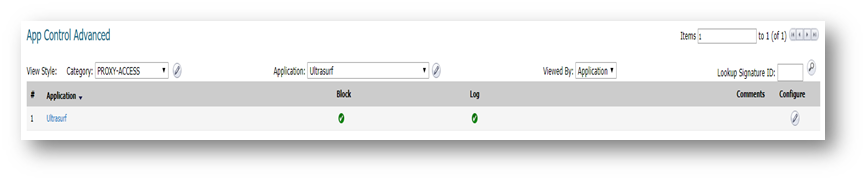
- On the App Control Advanced page, select Category as PROXY-ACCESS
- Select Ultrasurf under Application
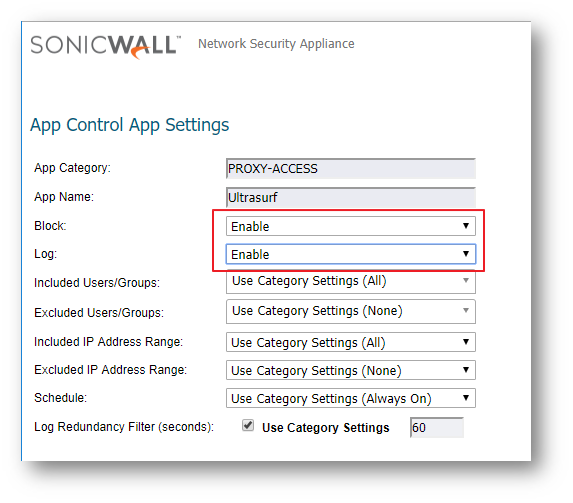
- Click on the configure button to bring up the Edit App Control App window.
- Select Enable under Block and Log.
- Click on OK to save.
Enabling Application Signature Group - HTTP Proxy
- On the App Control Advanced page, select Category as PROXY-ACCESS
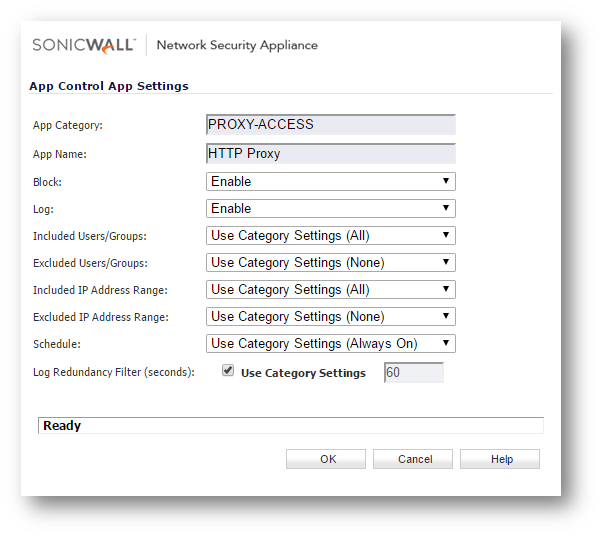
- Select HTTP Proxy under Application
- Click on the configure button to bring up the Edit App Control App window.
- Select Enable under Block and Log.
- Click on OK to save.
Enabling Application Control on LAN zone
- Click Manage in the top navigation menu.
- Navigate to System Setup | Network | Zones
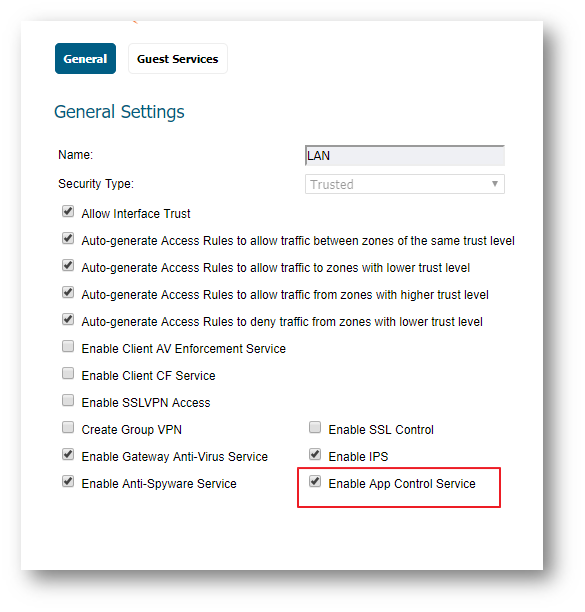
- Click on the configure button under the zone where you want enable App Control.
- Check Enable App Control Service.
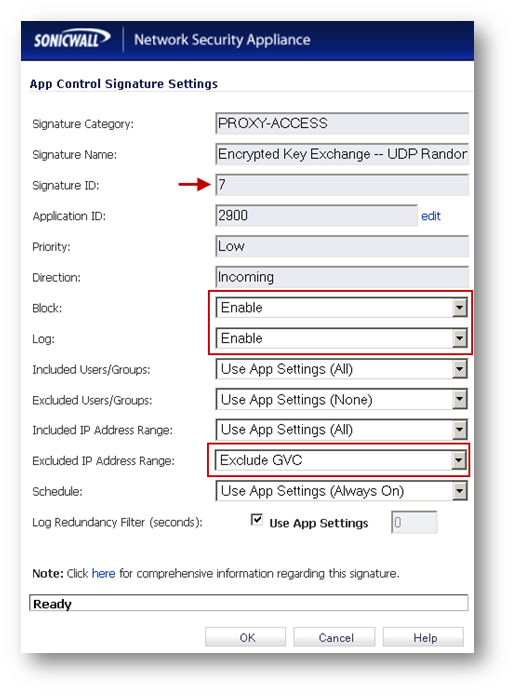
Excluding gateway IP addresses of SonicWall GVC from SID # 7
Signature ID 7 blocks encrypted UDP packets. SonicWall GVC connection uses UDP 4500 & 500. To allow GVC connections, exclude the gateway IP addresses of the GVC connection from SID # 7.
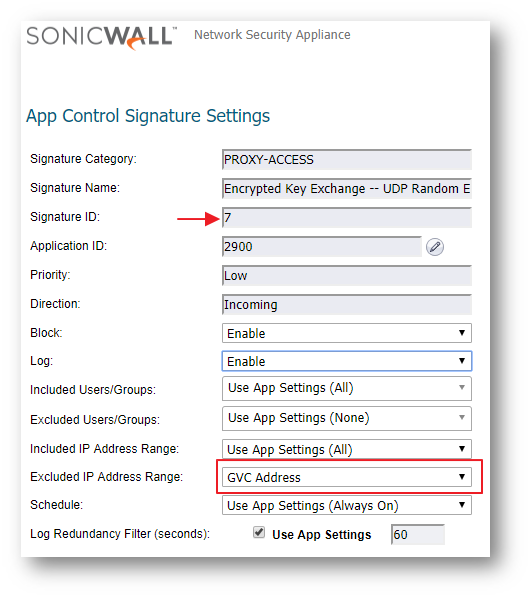
How to Test:
From a host behind the SonicWall start UltraSurf. UltraSurf will try to contact its servers and eventually fail.
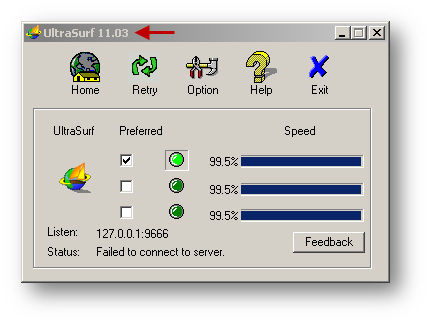
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Summary of configuration required to effectively block UltraSurf
- Enable DPI-SSL Client Inspection (CI)
- Enable Application Firewall under DPI-SSL CI
- Enable App Control Advanced signatures (see list below)
The following table lists the application group or the signature IDs used to block UltraSurf:
| Category | Application Name | Signature Name | Signature ID |
| PROXY-ACCCESS | Encrypted Key Exchange | Random Encryption(Skype,UltraSurf,Emule) | 5 |
| PROXY-ACCCESS | Encrypted Key Exchange | UDP Random Encryption(UltraSurf) | 7 |
| PROXY-ACCCESS | Non-SSL Traffic over SSL Port | Traffic Anomaly Detection | 6 |
| PROXY-ACCCESS | UltraSurf | UltraSurf Application Group | |
| PROXY-ACCCESS | HTTP Proxy | HTTP Proxy Application Group |
NOTE
Enabling the above signatures has the unintended consequence of blocking outbound encrypted UDP packets which includes Skype traffic, SonicWall GVC connections and/or encrypted Syslog traffic to a GMS server. This is due to SID # 7 which blocks encrypted UDP packets. In the case of GVC connections this shouldn't be considered a drawback. Instead, it's a way to control unauthorised outbound VPN connections. Administrators can exclude remote gateway IP addresses and/or GMS server IP address from SID # 7.
This article illustrates how to enable the above signatures and how to exclude IP addresses from SID # 7.
Procedure:
Enabling DPI-SSL Client Inspection
NOTE:
Enabling DPI-SSL Client Inspection would entail a restart of the appliance; thereafter, DPI-SSL would re-sign all SSL/TLS connections passing through it. This could cause disruption in the network. Read the following article before enabling DPI-SSL CI : How to Configure Client DPI-SSL (Video Tutorial and Article)
- Login to the SonicWall Management GUI.
- Navigate to the DPI-SSL | Client SSL page.
- Under General settings, enable the check box Enable SSL Client Inspection
- Enable the check box against Application Firewall
- Click on Accept at the top to save the changes
Enabling Signature ID 5,6 & 7.
- Navigate to the Firewall | App Control Advanced page.
- Check the box against Enable App Control.
- Under Lookup Signature ID, enter 5, 6 and 7 one after another and click on the configure button for each signature.
- In the Edit App Control Signature window, set Block and Log to Enable.
- Click on OK to save the settings.
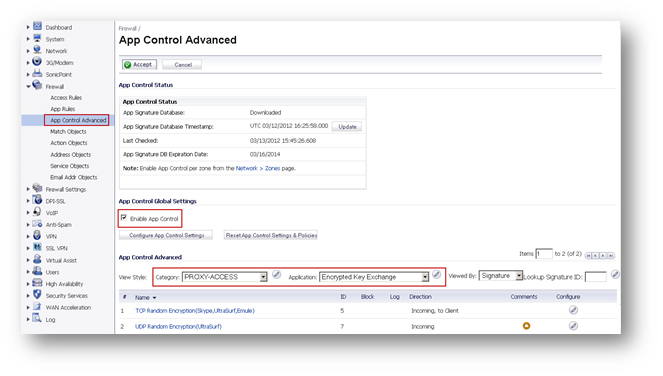
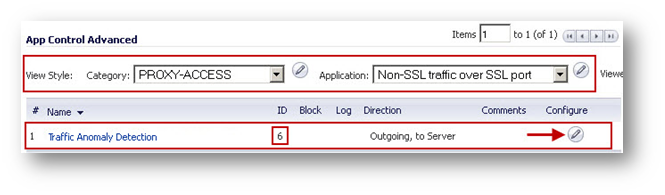

Enabling Application Signature Group - UltraSurf
- On the App Control Advanced page, select Category as PROXY-ACCESS
- Select Ultrasurf under Application
- Click on the configure button to bring up the Edit App Control App window.
- Select Enable under Block and Log.
- Click on OK to save.
Enabling Application Signature Group - HTTP Proxy
- On the App Control Advanced page, select Category as PROXY-ACCESS
- Select HTTP Proxy under Application
- Click on the configure button to bring up the Edit App Control App window.
- Select Enable under Block and Log.
- Click on OK to save.

Enabling Application Control on LAN zone
- Navigate to Network | Zones
- Click on the configure button under the zone where you want enable App Control.
- Check Enable App Control Service.
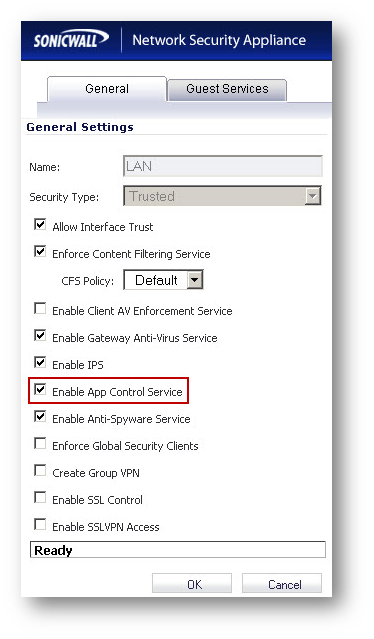
Excluding gateway IP addresses of SonicWall GVC from SID # 7
Signature ID 7 blocks encrypted UDP packets. SonicWall GVC connection uses UDP 4500 & 500. To allow GVC connections, exclude the gateway IP addresses of the GVC connection from SID # 7.
How to Test:
From a host behind the SonicWall start UltraSurf. UltraSurf will try to contact its servers and eventually fail.

The following App Control messages will be logged under Log | View when UltraSurf traffic is detected and blocked: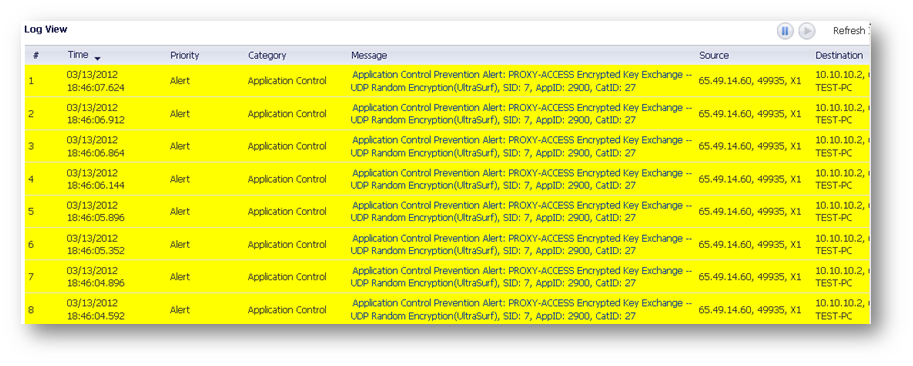
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall NSA Series > Application Firewall
- Firewalls > TZ Series > Application Firewall
- Firewalls > SonicWall SuperMassive 9000 Series > Application Firewall






 YES
YES NO
NO