-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to block P2P Applications (eg. BitTorrent, eMule) using Application Control Policies



Description
The application signature databases that were previously included with SonicWall Intrusion Prevention Service (IPS) are now part of the Application Control feature. These signature databases are used to protect users from application vulnerabilities as well as worms, Trojans, peer-to-peer transfers, spyware and backdoor exploits. The extensible signature language used in SonicWall’s Deep Packet Inspection engine also provides proactive defense against newly discovered application and protocol vulnerabilities.
When configured within the Application Firewall environment, the administrator is allowed far more granular control over the configuration and actions than could previously be applied to IPS signatures. This article describes the method to block the P2P application BitTorrent using Application Control.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
To create an Application Control policy, first create a match object of type Application Category List, Application List, Application Signature List. These three types allow for selection of either general application categories, applications or individual application signatures. As we are blocking individual applications in this article, we will be creating a match object of type Application List.
Creating Match Object
- Login to the SonicWall Management GUI.
- Navigate to Manage | Objects | Match Objects
- Click on Add Match Object
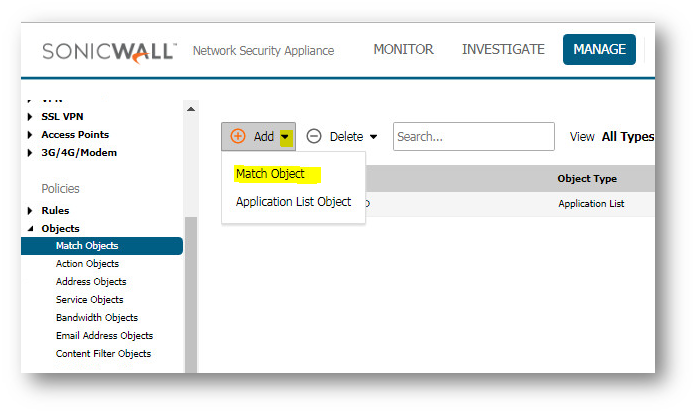
- In the Add/Edit Match Object window enter the following:
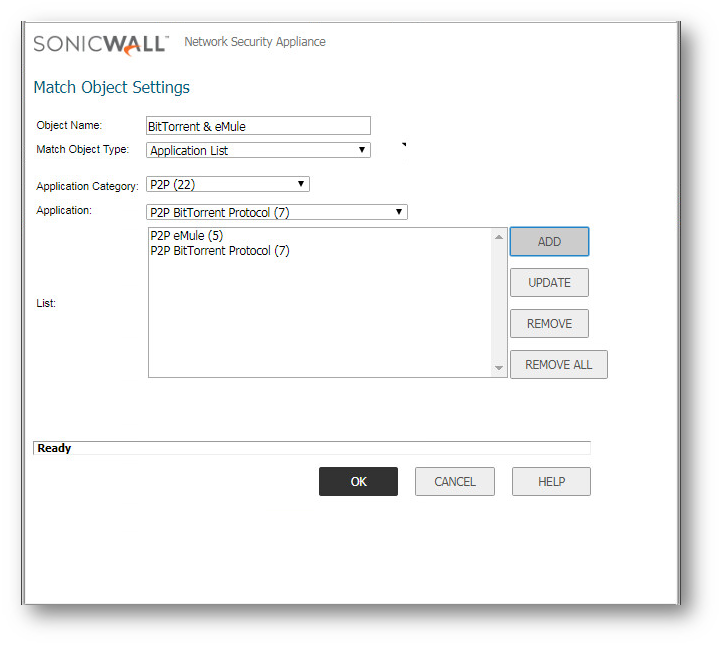
- Name: Enter a name for this match object
- Match Object Type: Select Application List from the drop-down.
- Application Category: Select P2P (22) from the drop-down.
- Application: Select P2P BitTorrent (7) & P2P eMule (5) and click on Add after each selection.
- Click on the OK button to save the changes.
Creating App Rules policy
Now that we have created a match object of what we need to block, let's create a App Rules policy to define who will be blocked.
- Navigate to Manage | Rules| Application Control
- Check the settings button near Filter and Refres button to Enable App Rules, if not done already.
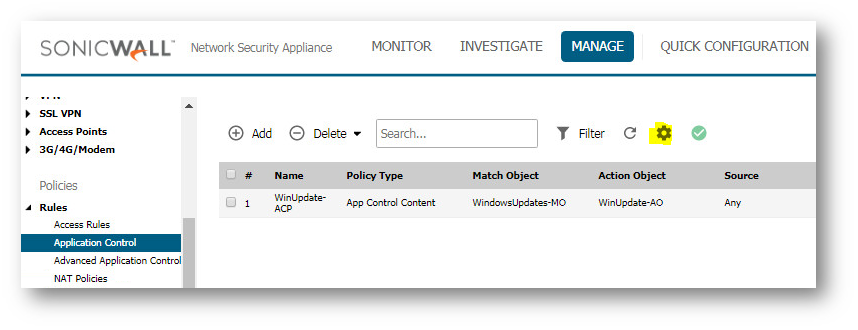
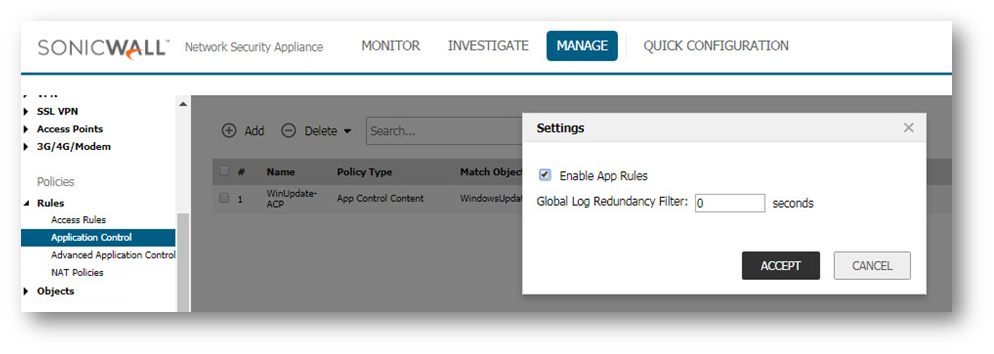
- Click on Add to create the following policy:
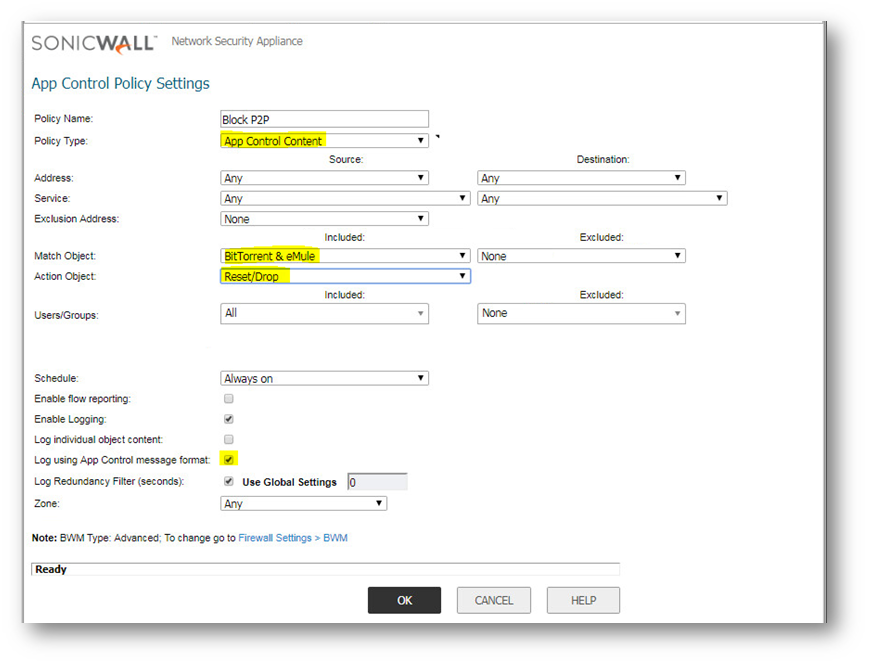
App Control policies can be made more specific by:
- Applying policies to specific internal IP addresses under the Addresses field
- Excluding internal IP adddresses from a particular policy by adding them under the Exclusion Addresses field.
- Excluding or including users from a particular policy by adding users or user groups object under Included / Excluded Users/Groups. For this to work user authentication needs to be enabled.
- Applying schedules to a policy by adding schedule objects under the Schedule field.
- Selecting a zone under the Zone field.
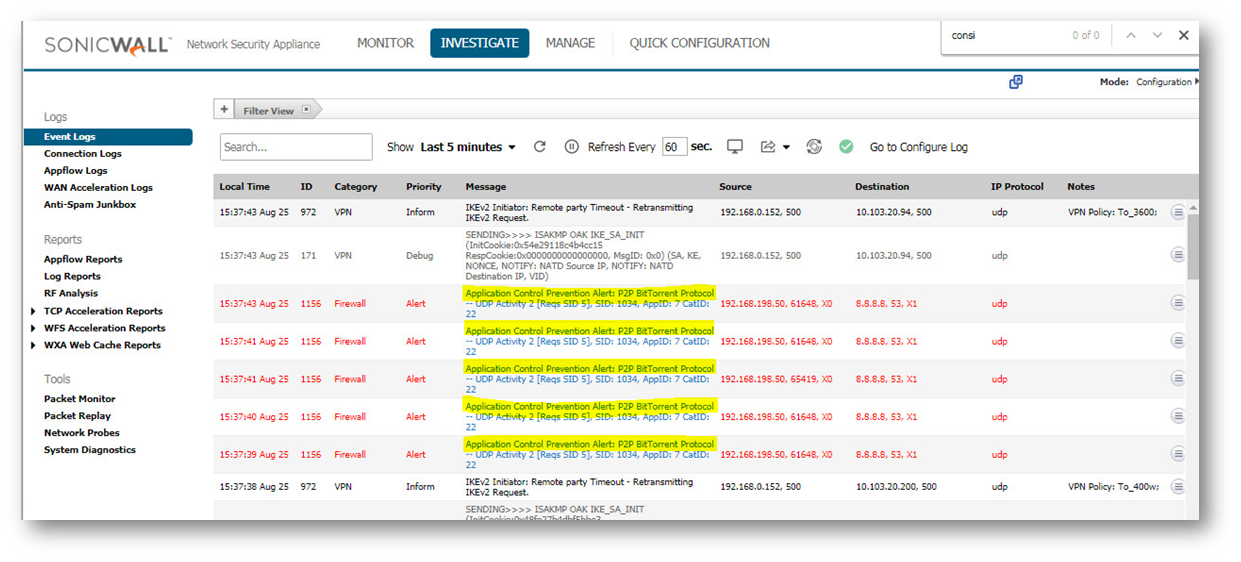
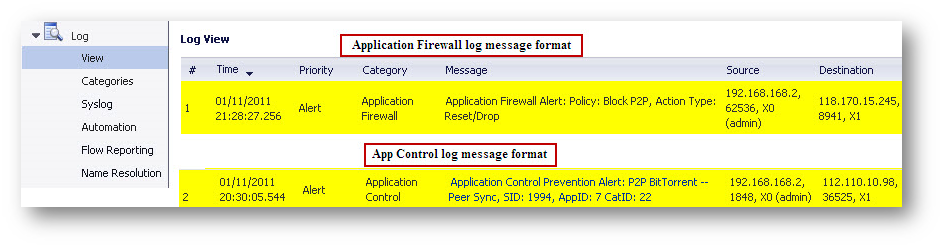
Log Messages
When hosts behind the SonicWall get blocked or when their action triggers a policy based on the App Control policies, SonicWall will log them in either of the following formats, depending on whether Log using App Control message format is checked or not:
Go to Investigate | Logs | Event Logs:
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
To create an Application Control policy, first create a match object of type Application Category List, Application List, Application Signature List. These three types allow for selection of either general application categories, applications or individual application signatures. As we are blocking individual applications in this article, we will be creating a match object of type Application List.
Creating Match Object
- Login to the SonicWall Management GUI.
- Navigate to Firewall | Match Objects
- Click on Add New Match Object
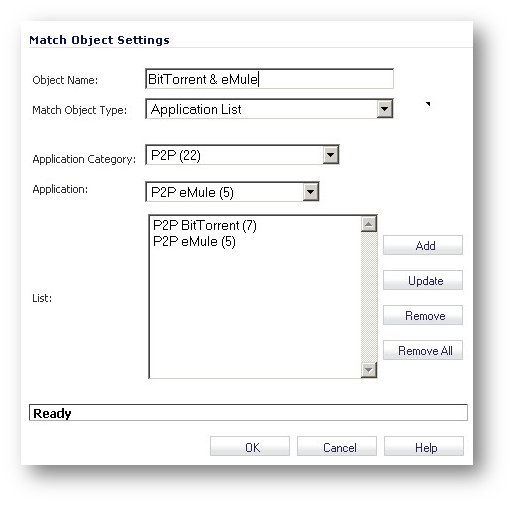
- In the Add/Edit Match Object window enter the following:
- Name: Enter a name for this match object
- Match Object Type: Select Application List from the drop-down.
- Application Category: Select P2P (22) from the drop-down.
- Application: Select P2P BitTorrent (7) & P2P eMule (5) and click on Add after each selection.
- Click on the OK button to save the changes.
Creating App Rules policy
Now that we have created a match object of what we need to block, let's create a App Rules policy to define who will be blocked.
- Navigate to Firewall | App Rules
- Check the box under Enable App Rules, if not done already.
- Click on Add New Policy to create the following policy:
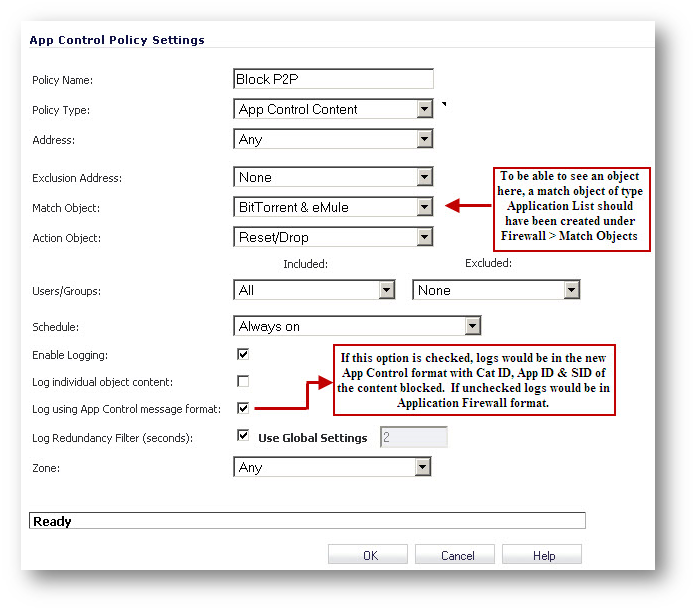
App Control policies can be made more specific by:
- Applying policies to specific internal IP addresses under the Addresses field
- Excluding internal IP adddresses from a particular policy by adding them under the Exclusion Addresses field.
- Excluding or including users from a particular policy by adding users or user groups object under Included / Excluded Users/Groups. For this to work user authentication needs to be enabled.
- Applying schedules to a policy by adding schedule objects under the Schedule field.
- Selecting a zone under the Zone field.
Log Messages
When hosts behind the SonicWall get blocked or when their action triggers a policy based on the App Control policies, SonicWall will log them in either of the following formats, depending on whether Log using App Control message format is checked or not:
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO