-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to Block HTTP Downloads or Uploads of Specific File Extensions Using App Rules



Description
At times it may be necessary to block entire File Extensions from entering or leaving your network. Blocking file extensions from emails and other communication is a common practice to help prevent CryptoLocker attacks, leaking sensitive company data, and other intrusions or violation of network policy.
The SonicWall can block downloads for any File Extension going over HTTP, FTP, and other unencrypted Protocols. This is performed using the App Rules Feature as demonstrated below.
 CAUTION: By default the SonicWall cannot block File Extensions over HTTPS or other Encrypted Protocols. This is because the SonicWall cannot examine encrypted payloads, to get around this DPI-SSL is required as a Feature on the SonicWall.
CAUTION: By default the SonicWall cannot block File Extensions over HTTPS or other Encrypted Protocols. This is because the SonicWall cannot examine encrypted payloads, to get around this DPI-SSL is required as a Feature on the SonicWall.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Log in to the SonicWall Management GUI.
- Click on Object | Match Objects | Match Objectsand click on "Add".
- Set Match Object Typeto "HTTP URI Content".
- Add all File Extensions that you would like to block (".ZIP", ".RAR" and ".EXE" in this example).
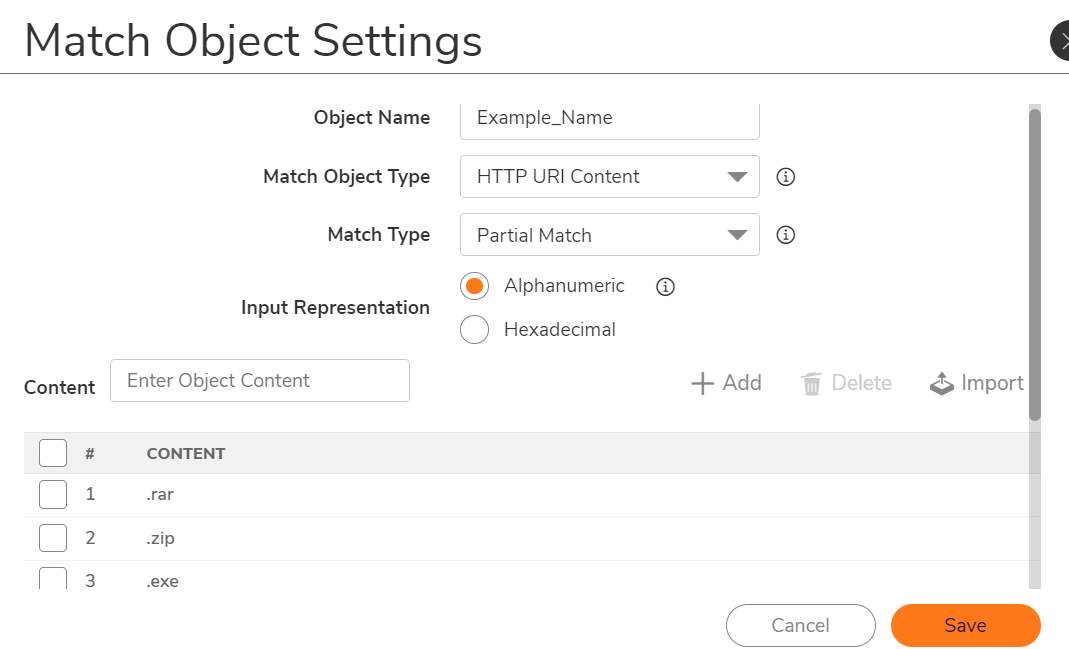
- Navigate to Policy | Rules and Policies | App Rules and click on "Add". Enter a Friendly Name under "Policy Name".
- Set Policy Type to "HTTP Client, SMTP Client, FTP Client, or POP3 Client" depending on which Protocol you're attempting to block. Specify Source or Destination Address if needed, Any will apply to all traffic.
TIP: It's possible to block a wide range or Protocols depending on the Policy Type. Custom Policies are Protocol neutral and block by Match Object.
- Set "Match Object" to the one that you've already created.
- Set Action Object to Reset/Drop.
- Set Users/GroupsIncluded or Excluded as required.
TIP: Users/Groups provide a powerful way to exclude or include only specific Users in the App Rules Policy. App Rules can make use of LDAP Groups or Local Groups.
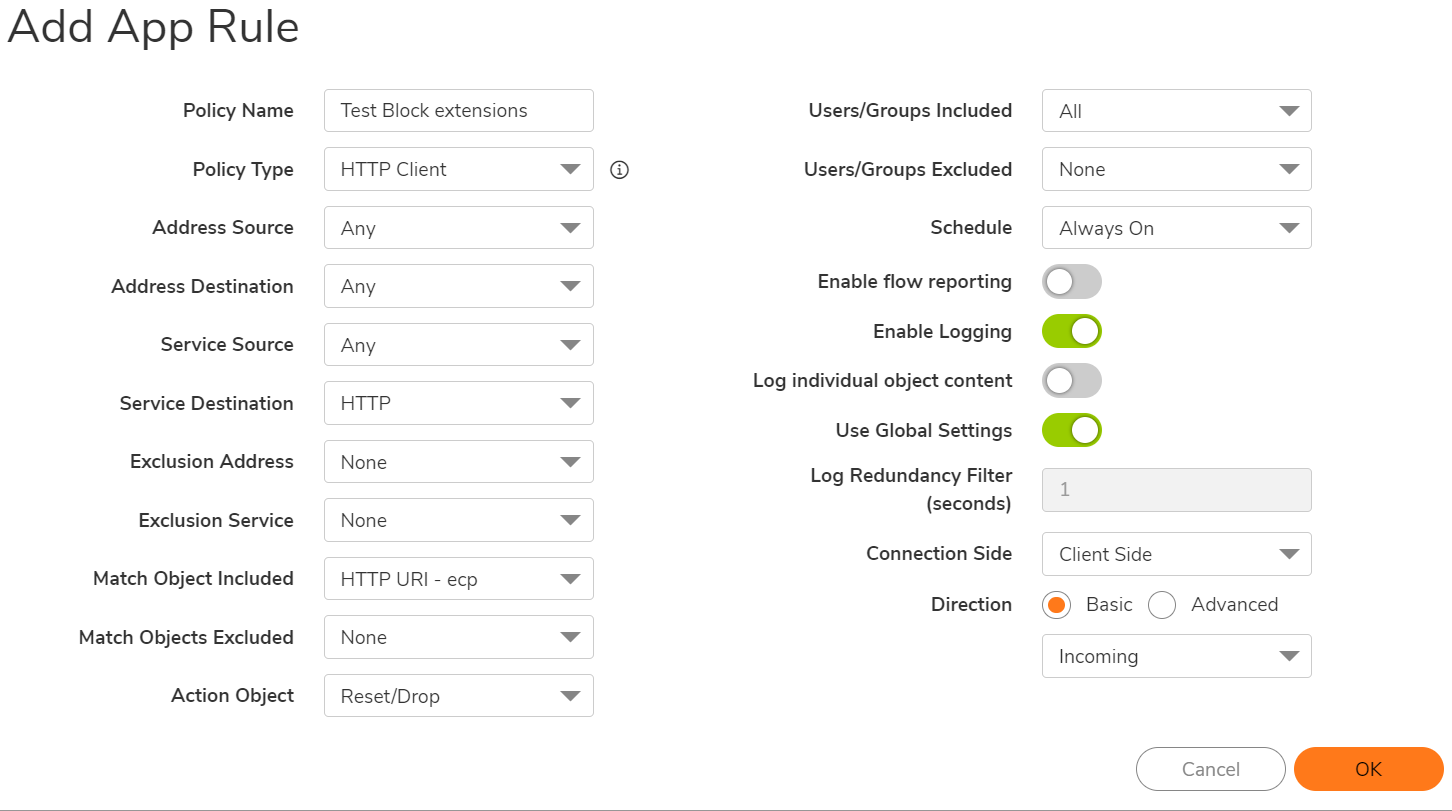
TIP: It is possible to set additional fields, such as Schedule and Direction, to further specify when and where a Policy should be applied.
CAUTION: Once again, App Rules cannot block HTTPS Content without DPI-SSL setup on the SonicWall.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
1. Login to the SonicWall Management GUI.
2. Click on MANAGE ,Navigate to Objects | Match Objects and click on "Add New Match Object".
3. Set Match Object Type to "HTTP URI Content".
4. Add all File Extensions that you would like to block (".ZIP", ".RAR" and ".EXE" in this example).
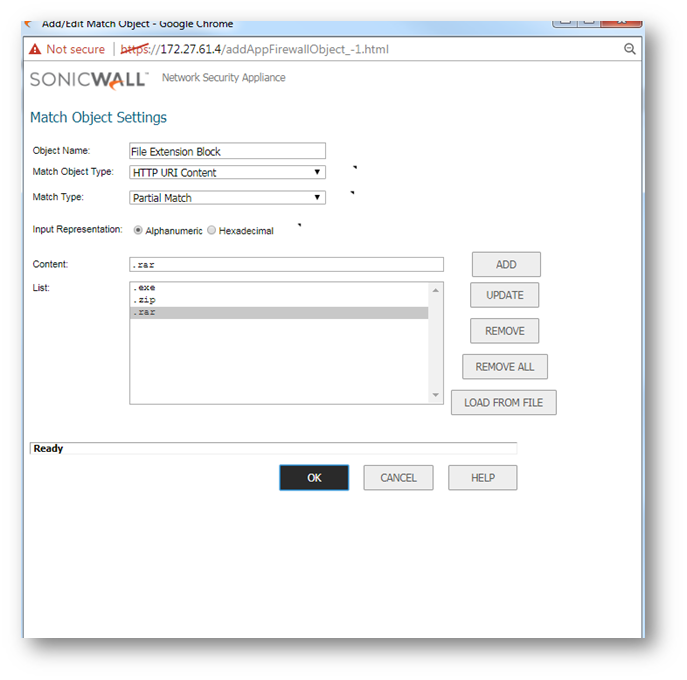
5. Navigate to Rules | App Rules and click on "Add New Policy". Enter a Friendly Name under "Policy Name".
6. Set Policy Type to "HTTP Client, SMTP Client, FTP Client, or POP3 Client" depending on which Protocol you're attempting to block. Specify Source or Destination Address if needed, Any will apply to all traffic.
 TIP: It's possible to block a wide range or Protocols depending on the Policy Type. Custom Policies are Protocol neutral and block by Match Object.
TIP: It's possible to block a wide range or Protocols depending on the Policy Type. Custom Policies are Protocol neutral and block by Match Object.
7. Set "Match Object" to the one that you've already created.
8. Set Action Object to Reset/Drop.
9. Set Users/Groups Included or Excluded as required.
 TIP: Users/Groups provides a powerful way to exclude or include only specific Users in the App Rules Policy. App Rules can make use of LDAP Groups or Local Groups.
TIP: Users/Groups provides a powerful way to exclude or include only specific Users in the App Rules Policy. App Rules can make use of LDAP Groups or Local Groups.

 TIP: It is possible to set additional fields, such as Schedule and Direction, to further specify when and where a Policy should be applied.
TIP: It is possible to set additional fields, such as Schedule and Direction, to further specify when and where a Policy should be applied.
 CAUTION: Once again, App Rules cannot block HTTPS Content without DPI-SSL setup on the SonicWall.
CAUTION: Once again, App Rules cannot block HTTPS Content without DPI-SSL setup on the SonicWall.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
1. Login to the SonicWall Management GUI.
2. Navigate to Firewall | Match Objects and click on "Add New Match Object".
3. Set Match Object Type to "HTTP URI Content".
4. Add all File Extensions that you would like to block (".ZIP", ".RAR" and ".EXE" in this example).
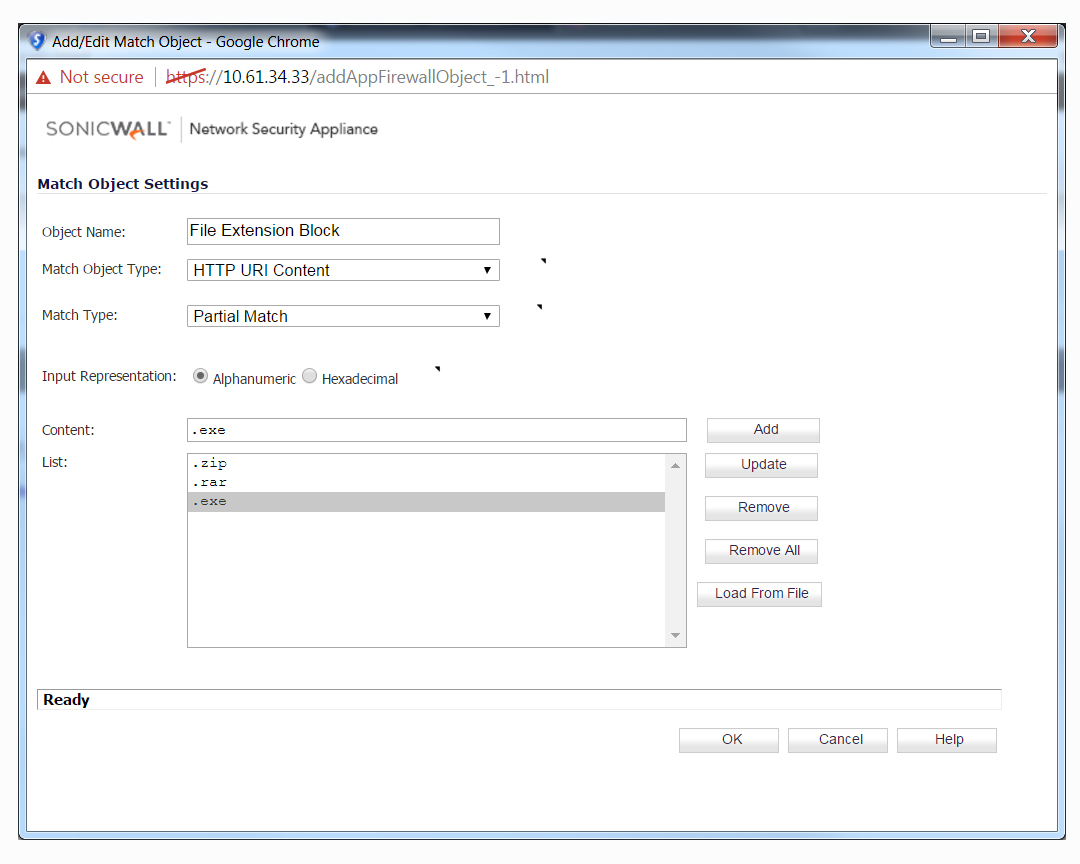
5. Navigate to Firewall | App Rules and click on "Add New Policy". Enter a Friendly Name under "Policy Name".
6. Set Policy Type to "HTTP Client, SMTP Client, FTP Client, or POP3 Client" depending on which Protocol you're attempting to block. Specify Source or Destination Address if needed, Any will apply to all traffic.
 TIP: It's possible to block a wide range or Protocols depending on the Policy Type. Custom Policies are Protocol neutral and block by Match Object.
TIP: It's possible to block a wide range or Protocols depending on the Policy Type. Custom Policies are Protocol neutral and block by Match Object.
7. Set "Match Object" to the one that you've already created.
8. Set Action Object to Reset/Drop.
9. Set Users/Groups Included or Excluded as required.
 TIP: Users/Groups provides a powerful way to exclude or include only specific Users in the App Rules Policy. App Rules can make use of LDAP Groups or Local Groups.
TIP: Users/Groups provides a powerful way to exclude or include only specific Users in the App Rules Policy. App Rules can make use of LDAP Groups or Local Groups.

 TIP: It is possible to set additional fields, such as Schedule and Direction, to further specify when and where a Policy should be applied.
TIP: It is possible to set additional fields, such as Schedule and Direction, to further specify when and where a Policy should be applied.
 CAUTION: Once again, App Rules cannot block HTTPS Content without DPI-SSL setup on the SonicWall.
CAUTION: Once again, App Rules cannot block HTTPS Content without DPI-SSL setup on the SonicWall.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall NSA Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall SuperMassive E10000 Series






 YES
YES NO
NO