-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to block a spoofed Spam with the same From and To email address using our custom policy filter



Description
How to block a spoofed Spam with the same From and To email address using our custom policy filter
Resolution
Introduction
You may find yourself receiving spoofed spam messages where the same local email address is being used for both the From: and To: fields in the message. This could also be found in the return path within the message header itself. In some cases, removing the entry from the (corprate or peruser) allowlist may not prevent the entry from readded to the allowlist. (Please refer to KB: 5585). Or if the administrator finds himself with too many users where this scenario is taking place, that it may not be the most effective process in adressing the issue as sorting through all the affected users may prove to be a lengthy process. If this is the case, it may be beneficial to leverage policy filters or dictionary policies (if you host for many domains) to help combat the spoofed spam issue you are experiencing.
(Please note: This article is to help address the spoofed spam issues only. If you have a managed server outside of your local aread network that legitimately creates inbound mail traffic where the sending address will be one of your accepted domains, you will need to create exceptions to this policy filter. This policy filter can affect remote users depending on where their managed servers sits, so proceed with caution. As long as the managed server is on the local area network, this policy should be fine).
Resolution or Workaround
Looking at the headers we would see that the message many times has this line.
Return-Path: johnsmith@domain.com
From: "Some Name" <johnsmith@domain.com>
To: "Your Name" <johnsmith@domain.com>
X-Mlf-Threat-Detailed: nothreat;none;none;list_addrbk_sender
This indicates that the user has their own email address in their allowed list.
- Under Manage | Policy & Compliance | Filters | Inbound there is an option to ADD NEW FILTER.
The sample will look as follows: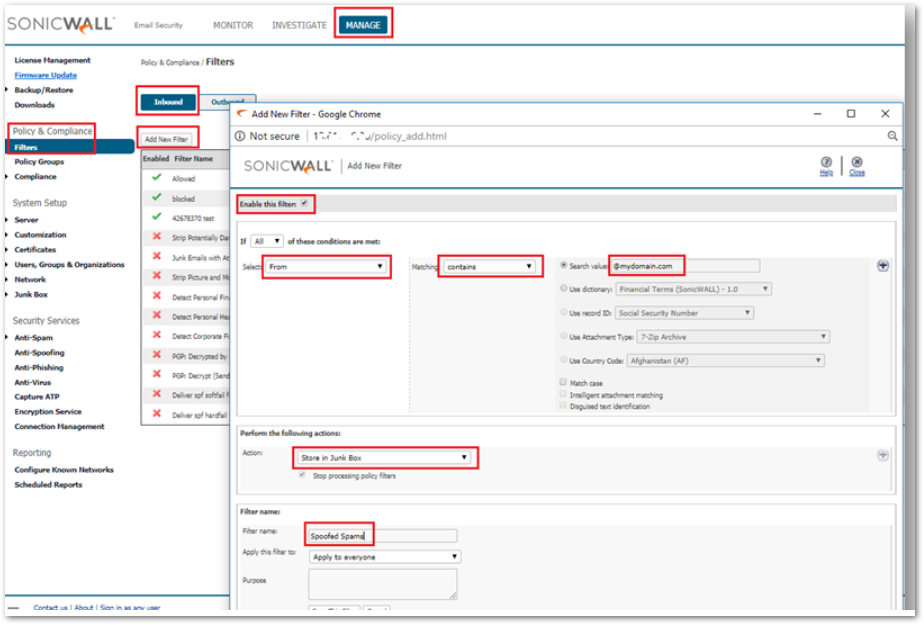
- Be sure to place this policy filter in the order of precedence desired as the filters list will process in the order listed.
 TIP: If you have multiple domains that you would like to implement this for, you may want to leverage your Dictionaries. This is only available to you if you have a current Compliance subscription enabled through your mysonicwall.com account.
TIP: If you have multiple domains that you would like to implement this for, you may want to leverage your Dictionaries. This is only available to you if you have a current Compliance subscription enabled through your mysonicwall.com account. - First create the dictionary with the relevant domains you are currently hosting and filtering for. This can be found in Policy & Compliance | Compliance Module | Dictionaries:
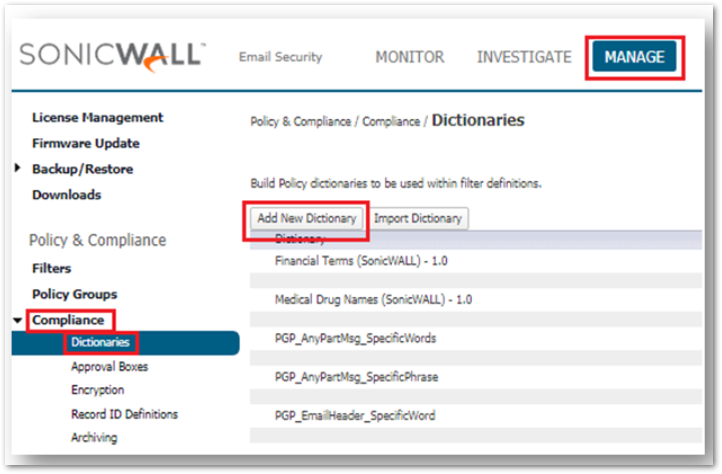
- Next, add your domains to the dictionary:
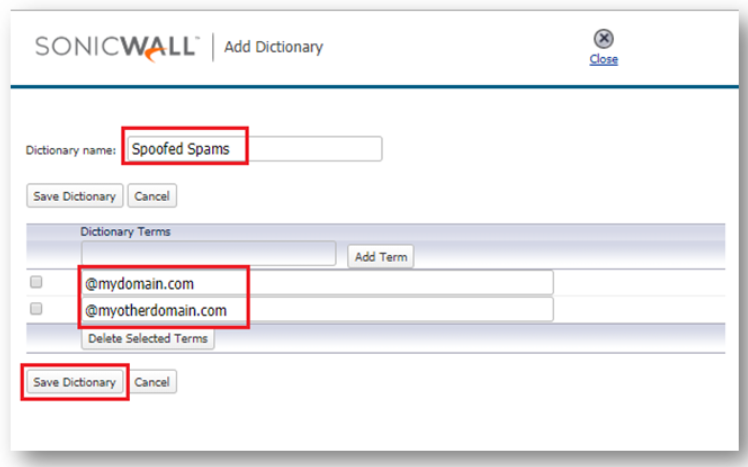
- Now go ahead and go back to the Filters to create the spoofed policy filter. It is found by going to Policy & Compliance |Filters. When configuring the filter this time, simply point it to look at the dictionary you just created.
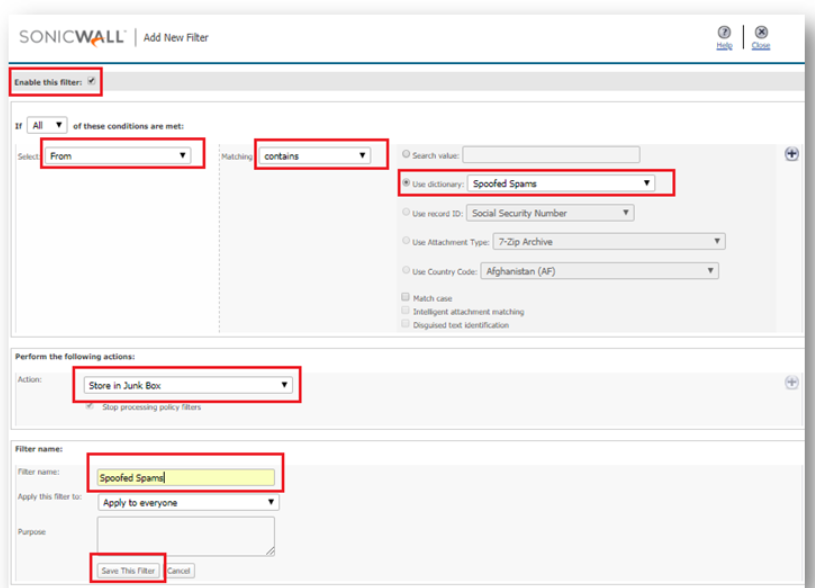
 NOTE: This article is applicable to all versions and platforms of Email Security.
NOTE: This article is applicable to all versions and platforms of Email Security.
Related Articles
- Email Security: How to download the Outlook Junk Tool?
- Configuring SonicWall Email Security to Ensure Maximum effectiveness, High Throughput
- How to exclude the domain from DHA scanning?
Categories
- Email Security > Email Security Appliance
- Email Security > Email Security Software
- Email Security > Hosted Email Security






 YES
YES NO
NO