-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to add multiple domains for LDAP User Authentication.



Description
This article illustrates how to add multiple and different domains for LDAP Authentication.
In this scenario, the network has two domains - Domain A: hal-2010.local and Domain B: hal.local. The requirement is to authenticate AD users of both the domains through the SonicWall.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Before beginning the configuration the following requires to be in-place
- Two Active Directory Domains: For the purpose of this article we use Windows Server 2008 (Domain A) and Windows Server 2003 (Domain B).
- One-Way Trust created from Domain A to B. One-Way Trust allows users from Domain A (outgoing) get access to Domain B (incoming) but Domain B does not have access to Domain A.) For more information on creating Trust, check the following article: Create a Forest Trust
- Create a user in both domains with identical username and password.
Navigate to the Manage | User | Settings page.
Click on Configure LDAP after selecting LDAP + Local Users under Authentication method for login.
- Add a new LDAP Server
- In the Name or IP address field enter the FQDN or IP address of the LDAP server (Domain A - in this example hal-2010.local) against which you wish to authenticate. If using a name, be certain that it can be resolved by your DNS server.
- In the Port Number field, the default LDAP over TLS port number is TCP 636. The default LDAP (unencrypted) port number is TCP 389. If you are using a custom listening port on your LDAP server, specify it here
- Under Login/Bind specify a username that has rights to log in to the LDAP directory of both domains. The login name will automatically be presented to the LDAP server in full ‘dn’ notation. This can be any account with LDAP read privileges (essentially any user account) – Administrative privileges are not required. Note that this is the user’s name, not their login ID (e.g. Jones Smith rather than jsmith).


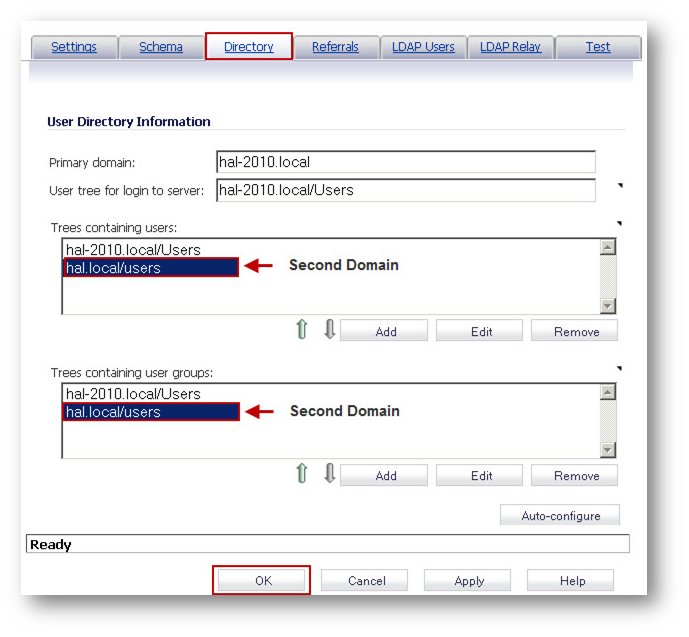
Click on the Directory tab and configure the following fields:
- Enter the domain name of Domain A under Primary domain.
- The field User tree for login to server and the boxes Trees containing users and Trees containing user groups will be auto-populated.
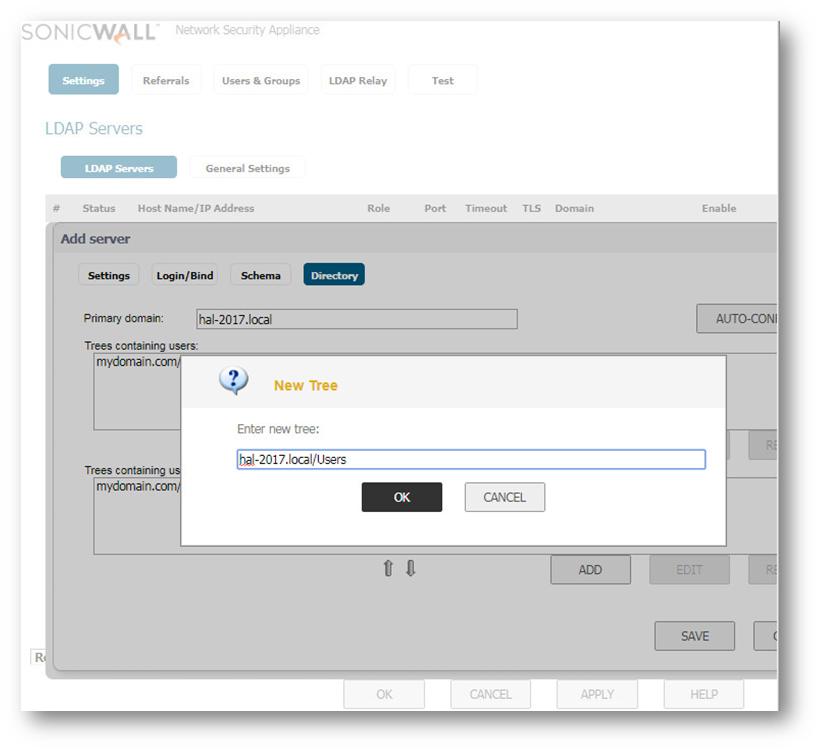
- Click on Add under Trees containing users and Trees containing user groups and enter the DN of Domain B followed by the directory name. In this example hal.local/users.
- Click on OK to save.
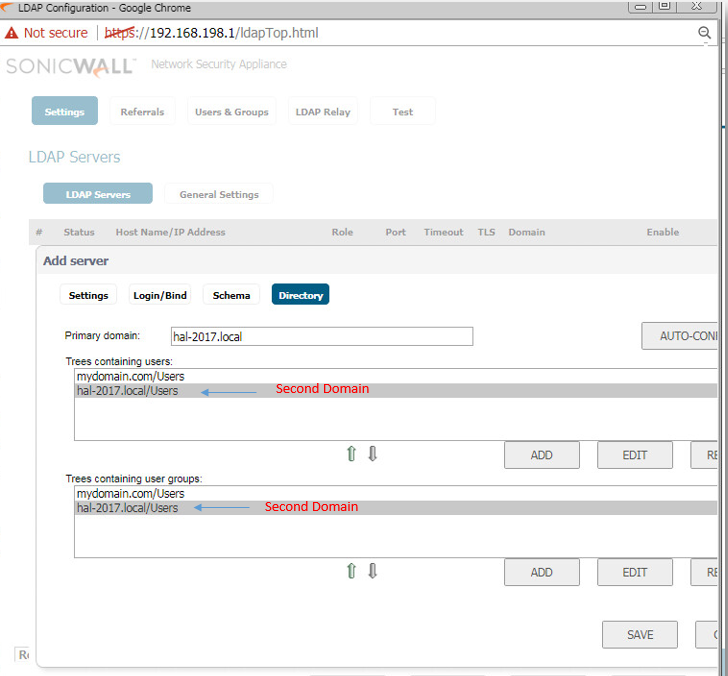
Save the changes and then c lick on the Referrals tab and configure the following fields:
- Allow referrals – Select this option for SonicWall to search user information located on Domain B LDAP server.
- Allow continuation references during user authentication – Select this option any time that individual directory trees have been manually configured to span multiple LDAP servers.
- Allow continuation references during directory auto-configuration – Select this option to allow the trees to be read from multiple LDAP servers in a single operation.
- Allow continuation references in domain searches – Select this option when using single-sign-on with users in multiple sub-domains having separate LDAP servers.

Testing
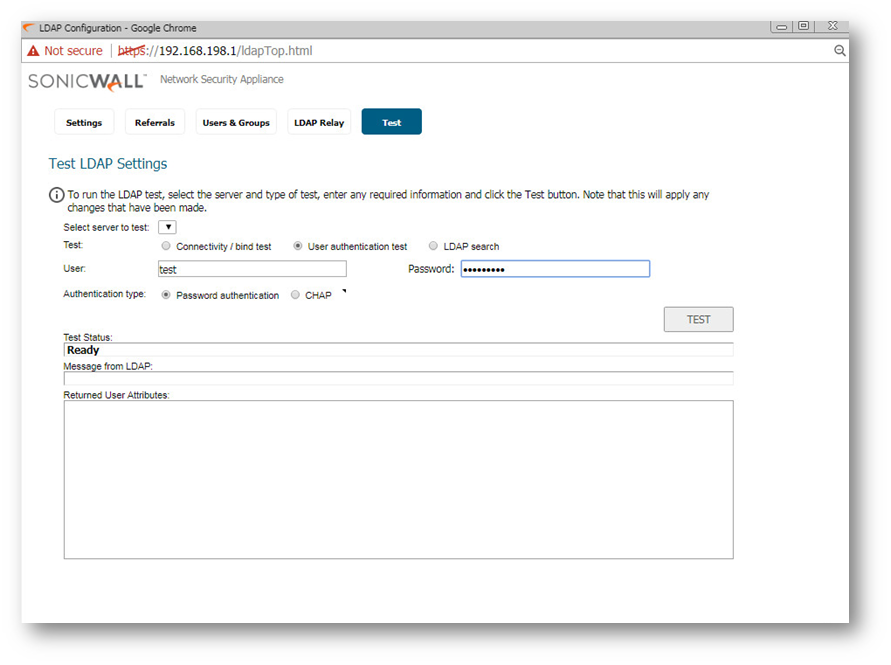
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Before beginning the configuration the following requires to be in-place
- Two Active Directory Domains: For the purpose of this article we use Windows Server 2008 (Domain A) and Windows Server 2003 (Domain B).
- One-Way Trust created from Domain A to B. One-Way Trust allows users from Domain A (outgoing) get access to Domain B (incoming) but Domain B does not have access to Domain A.) For more information on creating Trust, check the following article: Create a Forest Trust
- Create a user in both domains with identical username and password.
Navigate to the User | Settings page.
Click on Configure after selecting LDAP + Local Users under Authentication method for login.
- In the Name or IP address field enter the FQDN or IP address of the LDAP server (Domain A - in this example hal-2010.local) against which you wish to authenticate. If using a name, be certain that it can be resolved by your DNS server.
- In the Port Number field, the default LDAP over TLS port number is TCP 636. The default LDAP (unencrypted) port number is TCP 389. If you are using a custom listening port on your LDAP server, specify it here
- Under Login user name specify a username that has rights to log in to the LDAP directory of both domains. The login name will automatically be presented to the LDAP server in full ‘dn’ notation. This can be any account with LDAP read privileges (essentially any user account) – Administrative privileges are not required. Note that this is the user’s name, not their login ID (e.g. Jones Smith rather than jsmith).

Click on the Directory tab and configure the following fields:
- Enter the domain name of Domain A under Primary domain.
- The field User tree for login to server and the boxes Trees containing users and Trees containing user groups will be auto-populated.
- Click on Add under Trees containing users and Trees containing user groups and enter the DN of Domain B followed by the directory name. In this example hal.local/users.
- Click on OK to save.
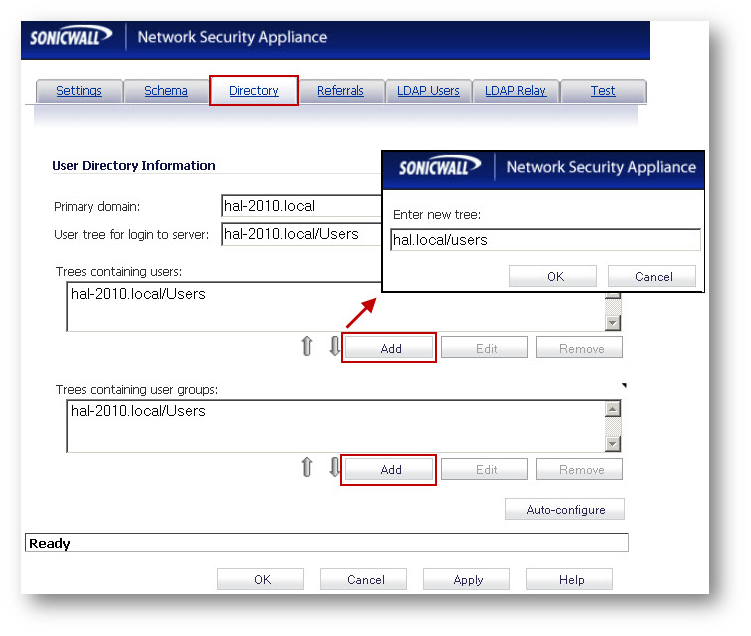
Click on the Referrals tab and configure the following fields:
- Allow referrals – Select this option for SonicWall to search user information located on Domain B LDAP server.
- Allow continuation references during user authentication – Select this option any time that individual directory trees have been manually configured to span multiple LDAP servers.
- Allow continuation references during directory auto-configuration – Select this option to allow the trees to be read from multiple LDAP servers in a single operation.
- Allow continuation references in domain searches – Select this option when using single-sign-on with users in multiple sub-domains having separate LDAP servers.

Testing


Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO