-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How does Sticky IP and Round Robin NAT Load Balancing (NLB) work



Description
This Article explains how Sticky IP and Round Robin NLB mechanisms works when connecting to Two RDP (Remote Desktop Protocol) hosts via incoming NAT policy. This article also demonstrate with help of packet monitor about Sticky IP and Round Robin NAT LB methods. NAT Methods which will be explained with Packet Monitor example are: Sticky IP – Source IP always connects to the same Destination IP (assuming it is alive). This method is best for publicly hosted sites requiring connection persistence, such as Web applications, Web forms, or shopping cart applications. This is the default mechanism, and is recommended for most deployments. Round Robin – Source IP cycles through each live load-balanced resource for each connection. This method is best for equal load distribution when persistence is not required.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- Log in to the SonicWall with your admin account.
- Select Manage | Objects | Address Objects
- Click Add and then add two RDP hosts, and then add them to a Group as shown in the screenshot below:
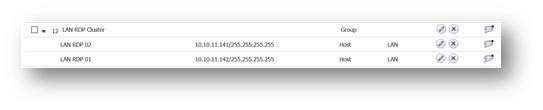
- Select Rules | Access Rules | Click Add to allow access from Any Source (Specify source if required) from WAN zone to LAN, ass shown below:

Above Access rule will allow access to the Public Virtual IP and then it will be sent to RDP hosts using the NAT LB method
- Click OK to add the Access Rule.
- Select Rules | NAT Policies | Click Add and fill the create a in bound NAT as shown below:

Note: If outbound access is required from above RDP hosts then add outbound NAT policies and access rules per requirements, as the above NAT and Access Rule will only allow inbound access, and if any of the RDP host need to initiate outbound connection, not replying an incoming request, then separate NAT/Access Rule will be needed.
- Select Advanced tab from Add NAT policy window and make sure the under "NAT Method" Sticky IP is selected, and under "High Availability" probing is enabled on the ports which are being used within the NAT policies, as show below:
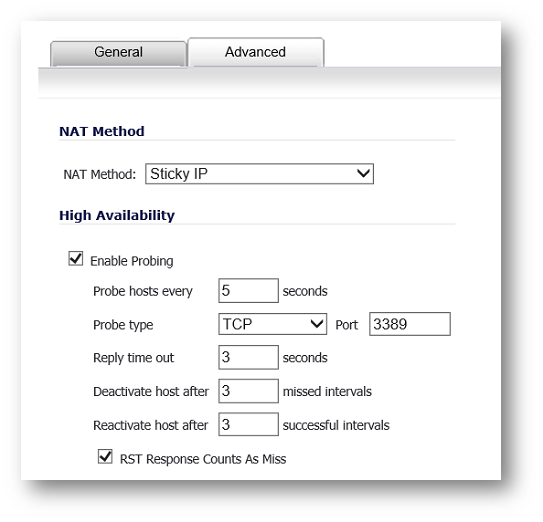
in the load-balancing group, using either a simple ICMP ping query to determine if the resource is alive, or a TCP socket open query to determine if the resource is alive. Per the configurable intervals, the SonicWall can direct traffic away from a non-responding resource, and return traffic to the resource once it has begun to respond again.
After the NAT rule has been added successfully, check the Investigate |Event Logs for the following Network Monitor logs confirming hosts are responding on Probes.
Source IPs: 10.71.254.254, 10.71.253.1 initiated two connections on destination TCP ports 3389 and their requests were load balanced onto destination hosts as shown in the "Packet Monitor" screenshot below:
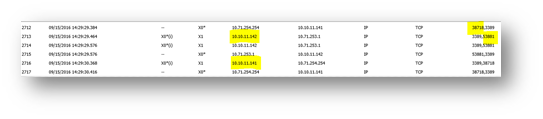
Source IP 10.71.254.254 connected to 10.10.11.141.
Source IP 10.71.253.1 connected to 10.10.11.142.
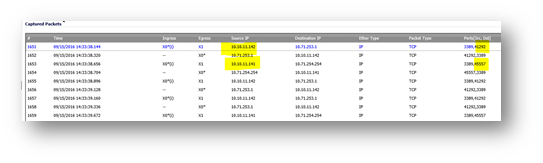
Source IP: 10.71.253.1 connect to 10.10.11.142 and Source IP: 10.71.254.254 connects to 10.10.11.141, see "Packet Monitor" below:
Example one - Mapping to a network:
Example two - Mapping to a IP address range:
Testing of Round Robin NAT LB method
Select Rules| NAT Policies | edit the same NAT policy used in the above example and change the "NAT LB" method from Sticky IP to Round Robin under Advanced tab, as shown below:
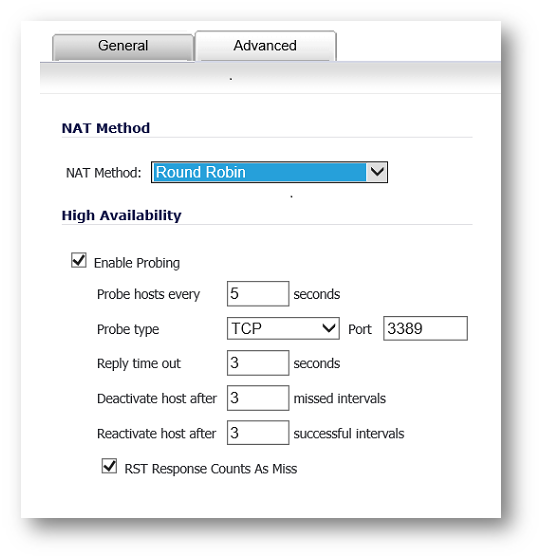
NAT LB method changed to Round Robin:
Source IPs: 10.71.254.254, 10.71.253.1 initiated two connections on destination TCP ports 3389 and their requests were load balanced onto destination hosts as shown in the "Packet Monitor" screenshot below:
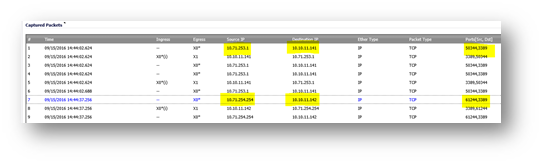
Source IP 10.71.253.1 connected to 10.10.11.141.
Source IP 10.71.254.254 connected to 10.10.11.142.
Closed current RDP sessions on both hosts and re launched Two RDP sessions to see if same how their request will be load balanced across two RDP hosts, see screenshot below:
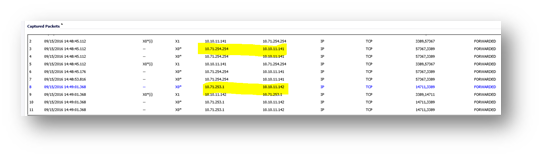
Source IP 10.71.253.1 connected to 10.10.11.142.
Source IP 10.71.254.254 connected to 10.10.11.141.
Round Robin – Source IP cycles through each live load-balanced resource for each connection. This method is best for equal load distribution when persistence is not required.
Determining the NAT LB Method to Use
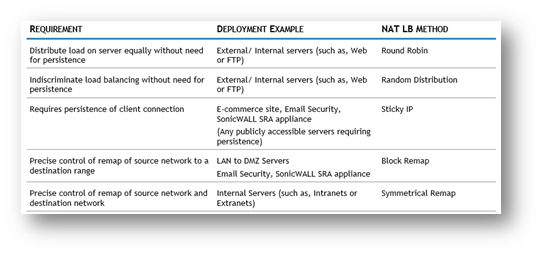
Caveats
The following are not available at present:
- Only two health-check mechanisms (ICMP ping and TCP socket open).
- No higher-layer persistence mechanisms (Sticky IP only).
- No “sorry-server” mechanism if all servers in group are not responding.
- No “round robin with persistence” mechanism.
- No “weighted round robin” mechanism.
- No method for detecting if resource is strained.
While there is no limit to the number of internal resources that the SonicWall network security appliance can load-balance to, and there no limit to the number of hosts it can monitor, abnormally large load-balancing groups (25+resources) may impact performance.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Log in to the SonicWall with your admin account.
- Select Network | Address Objects
- Click Add and then add two RDP hosts, and then add them to a Group as shown in the screenshot below:

- Select Firewall | Access Rules | Click Add to allow access from Any Source (Specify source if required) from WAN zone to LAN, ass shown below:
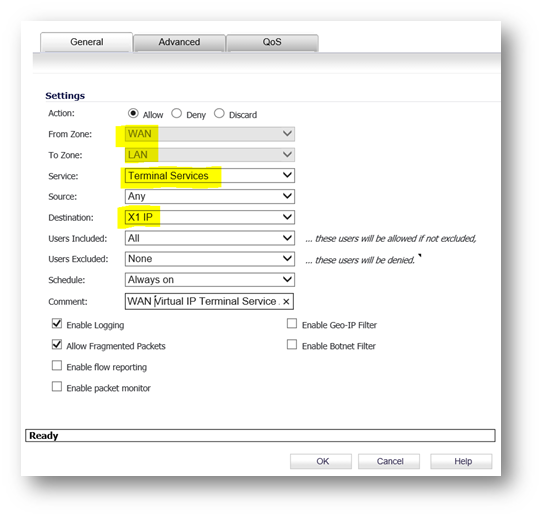
Above Access rule will allow access to the Public Virtual IP and then it will be sent to RDP hosts using the NAT LB method
- Click OK to add the Access Rule.
- Select Network | NAT Policies | Click Add and fill the create a in bound NAT as shown below:
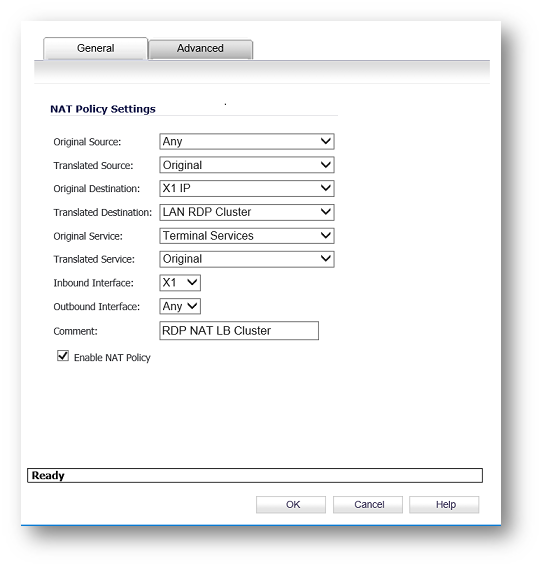
Note: If outbound access is required from above RDP hosts then add outbound NAT policies and access rules per requirements, as the above NAT and Access Rule will only allow inbound access, and if any of the RDP host need to initiate outbound connection, not replying an incoming request, then separate NAT/Access Rule will be needed.
- Select Advanced tab from Add NAT policy window and make sure the under "NAT Method" Sticky IP is selected, and under "High Availability" probing is enabled on the ports which are being used within the NAT policies, as show below:

in the load-balancing group, using either a simple ICMP ping query to determine if the resource is alive, or a TCP socket open query to determine if the resource is alive. Per the configurable intervals, the SonicWall can direct traffic away from a non-responding resource, and return traffic to the resource once it has begun to respond again.
After the NAT rule has been added successfully, check the Log | View for the following Network Monitor logs confirming hosts are responding on Probes, and this can further be monitored under Network | Network Monitor.
Source IPs: 10.71.254.254, 10.71.253.1 initiated two connections on destination TCP ports 3389 and their requests were load balanced onto destination hosts as shown in the "Packet Monitor" screenshot below:

Source IP 10.71.254.254 connected to 10.10.11.141.
Source IP 10.71.253.1 connected to 10.10.11.142.
Source IP: 10.71.253.1 connect to 10.10.11.142 and Source IP: 10.71.254.254 connects to 10.10.11.141, see "Packet Monitor" below:

Example one - Mapping to a network:
Example two - Mapping to a IP address range:
Testing of Round Robin NAT LB method
Select Network | NAT Policies | edit the same NAT policy used in the above example and change the "NAT LB" method from Sticky IP to Round Robin under Advanced tab, as shown below:

NAT LB method changed to Round Robin:
Source IPs: 10.71.254.254, 10.71.253.1 initiated two connections on destination TCP ports 3389 and their requests were load balanced onto destination hosts as shown in the "Packet Monitor" screenshot below:

Source IP 10.71.253.1 connected to 10.10.11.141.
Source IP 10.71.254.254 connected to 10.10.11.142.
Closed current RDP sessions on both hosts and re launched Two RDP sessions to see if same how their request will be load balanced across two RDP hosts, see screenshot below:

Source IP 10.71.253.1 connected to 10.10.11.142.
Source IP 10.71.254.254 connected to 10.10.11.141.
Round Robin – Source IP cycles through each live load-balanced resource for each connection. This method is best for equal load distribution when persistence is not required.
Determining the NAT LB Method to Use

Caveats
The following are not available at present:
- Only two health-check mechanisms (ICMP ping and TCP socket open).
- No higher-layer persistence mechanisms (Sticky IP only).
- No “sorry-server” mechanism if all servers in group are not responding.
- No “round robin with persistence” mechanism.
- No “weighted round robin” mechanism.
- No method for detecting if resource is strained.
While there is no limit to the number of internal resources that the SonicWall network security appliance can load-balance to, and there no limit to the number of hosts it can monitor, abnormally large load-balancing groups (25+resources) may impact performance.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall NSA Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > TZ Series






 YES
YES NO
NO