-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How do I integrate Cisco ISE while using a SonicWall firewall?



Description
This articles applies to organizations using Cisco ISE. Identity Services Engine (ISE) is a network administration product that enables the creation and enforcement of security and access policies for endpoint devices connected to the company's routers and switches. The purpose is to simplify identity management across diverse devices and applications.
Resolution
Because an ISE solution relies on the RADIUS protocol we can configure the SonicWall to act as a RADIUS accounting proxy. This provides a convenient integration for existing ISE solutions. For example, if we have two wireless controllers we can send the RADIUS authentication packets directly to the ISE solution and send the RADIUS accounting packets to a SonicWall firewall to proxy to the ISE solution. This will allow the firewall to use user based roles and policies to enforce traffic while providing seamless reporting from the ISE.
The new RADIUS packet flow will look like:
- Authentication: NAS -> ISE
- Accounting: NAS -> SonicWall -> ISE
Stated anotherway:
- Typical ISE solution:
Wireless Controller = send to radius Server A and B - Provided SonicWall solution:
Wireless Controller = send to SonicWall
SonicWall = Send to Radius Server A and B
In the following example we will setup RADIUS proxy on a SonicWall firewall using 6.5 firmware:
- Four wireless controllers - 10.248.0.5/6/7/8.
- Four RADIUS servers - 10.248.0.25/26/27/28.
Please perform the following:
- Enable RADIUS proxy by logging into the firewall and navigating to Users | Settings.
- Enable SSO and select the RADIUS Accounting tab.
- Add each of the wireless controllers (clients). While configuring the client click the Forwarding tab to specify where to forward the RADIUS packets. In our case those servers are: 10.248.0.25/26/27/28.
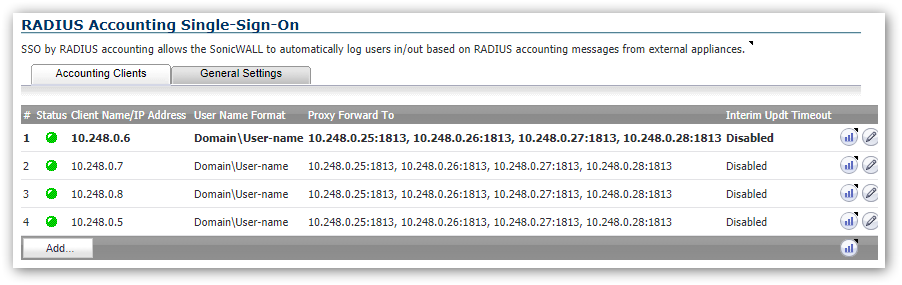
The above example handles Windows wireless (you can NOT send the domain portion when a machine has been joined to the domain). We can then add the following to support non-domain clients while configuring each client. This feature is located under the RADIUS tab:
After performing these steps, the firewall will successfully track user information (to be used for network enforcement) while also providing seamless integration with the ISE solution.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > User Login
- Firewalls > SonicWall NSA Series > User Login
- Firewalls > TZ Series > User Login






 YES
YES NO
NO