-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How do I enable FIPS Mode?



Description
A Federal Information Processing Standard (FIPS) is a publicly announced standardization developed by the United States federal government for use in computer systems by all non-military government agencies and by government contractors, when properly invoked and tailored on a contract.
The 140 series of Federal Information Processing Standards (FIPS) are U.S. government computer security standards that specify requirements for cryptography modules.
SonicWall UTM appliances are FIPS 140-2 certified. The overall FIPS validation level for SonicWall UTM appliances is Security Level 2. A special FIPS SonicOS firmware, SonicOS 5.5.1.2-fips_4o, is available for download at mysonicwall.com. The SonicOS 5.5.1.2 FIPS/CC release is certified for Level 3 Cryptographic Module Specification and Level 3 Design Assurance and is supported in NSA 3500 and above. For more information, refer to the SonicOS_5.5.1.2_FIPS_CC_Release_Notes.
When operating in FIPS (Federal Information Processing Standard) Mode, the SonicWall security appliance supports FIPS 140-2 Compliant security. Among the FIPS-compliant features of the SonicWall security appliance include PRNG (Psuedo Random Number Generator) based on SHA-1 and only FIPS approved algorithms are supported (DES, 3DES, and AES with SHA-1).
SonicWall UTM appliances are not configured to operate in FIPS-mode by default. This article describes the steps that must be taken to enable FIPS-mode operation.
Resolution
FIPS-mode Operation
SonicWall UTM appliances are not configured to operate in FIPS-mode by default. The following steps must be taken to enable FIPS-mode operation.
- Minimum password length in the Administration settings can not be less than 8
- Admin or Users password can not be less than 8 characters
- LDAP can not be enabled in FIPS mode without being protected by TLS
- LDAP can not be enabled in FIPS mode without selecting 'Require valid certificate from server'
- LDAP can not be enabled in FIPS mode without a valid local certificate for TLS
- RADIUS can not be enabled with a shared secret shorter than 8 characters
- RADIUS can not be enabled without being protected by IPSEC VPN
- When creating VPN tunnels, ensure ESP is enabled for IPSec.
- VPN Policy pre-shared key length must be longer than 8 characters.
- Use FIPS-approved encryption and authentication algorithms when creating VPN tunnels. The SonicWall UTM appliance supports the following FIPS-approved cryptographic algorithms:
- AES (128, 192, and 256-bit) in CBC mode (Cert. #1200)
- Triple-DES in CBC mode (Cert. #868)
- SHA-1 (Cert. #1105)
- DSA (Cert. #398)
- RNG (Cert. #664)
- RSA (Cert. #577)
- HMAC-SHA-1 (Cert. #697)
- Only support IKE DH Group 14, 19, 20, 21 in FIPS mode
- Only support AES CBC for IKE Phase 1/2 Encryption in FIPS mode
- Only SHA-256 Authentication or higher is allowed in FIPS mode
- IKEv2 Dynamic Client Proposal in VPN advanced settings requires SHA-256 or higher
- IKEv2 Dynamic Client Proposal in VPN advanced settings requires AES
- IKEv2 Dynamic Client Proposal in VPN advanced settings requires DH Group 14, 19, 20, 21
- HTTP, SSH, and SNMP Management are not allowed in FIPS Mode.
- Do not enable Advanced Routing Services.
- Management via Group VPN is not allowed in FIPS mode.
- Bandwidth Management has to be on.
When configured to operate in FIPS mode, the SonicWall UTM appliance provides only FIPS 140-2 compliant services.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
To enable FIPS mode, navigate to Device | Settings | Firmware & Settings | Settings | FIPS/NDPP. On the pop-up window scroll down to FIPS, then check Enable FIPS Mode and click Apply. The FIPS mode configuration can be determined by checking the state of the Enable FIPS Mode checkbox and verification of the preceding steps. If the Enable FIPS Mode checkbox is enabled, the module is running in the FIPS Approved mode of operation.
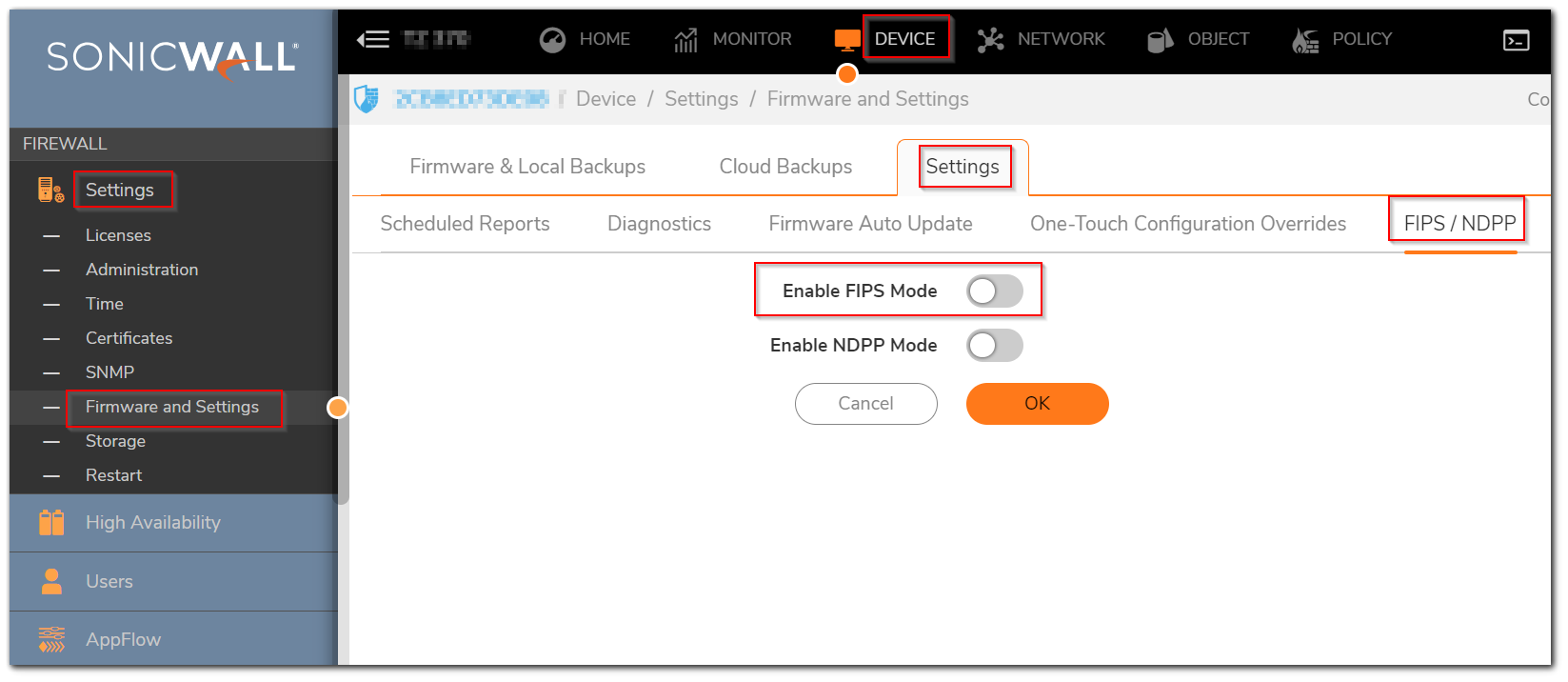
Enabling FIPS Mode
Select Enable FIPS Mode to enable the SonicWall UTM appliance to comply with FIPS. When you check this setting, a dialog box is displayed with the following message:
Warning! Modifying the FIPS mode will disconnect all users and restart the device. Click OK to proceed.
Click OK to reboot the SonicWall in FIPS mode. A second warning displays. Click Yes to continue rebooting. To return to normal operation, Uncheck the Enable FIPS Mode check box and reboot the SonicWall UTM appliance into non-FIPS mode.
 CAUTION: When using the SonicWall UTM appliance for FIPS-compliant operation, the tamper-evident sticker that is affixed to the SonicWall UTM appliance must remain in place and untouched.
CAUTION: When using the SonicWall UTM appliance for FIPS-compliant operation, the tamper-evident sticker that is affixed to the SonicWall UTM appliance must remain in place and untouched.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
To enable FIPS mode, navigate to Manage | Firmware & Backups | Settings. On the pop-up window scroll down to FIPS, then check Enable FIPS Mode and click Apply. The FIPS mode configuration can be determined by checking the state of the Enable FIPS Mode checkbox and verification of the preceding steps. If the Enable FIPS Mode checkbox is enabled, the module is running in the FIPS Approved mode of operation.
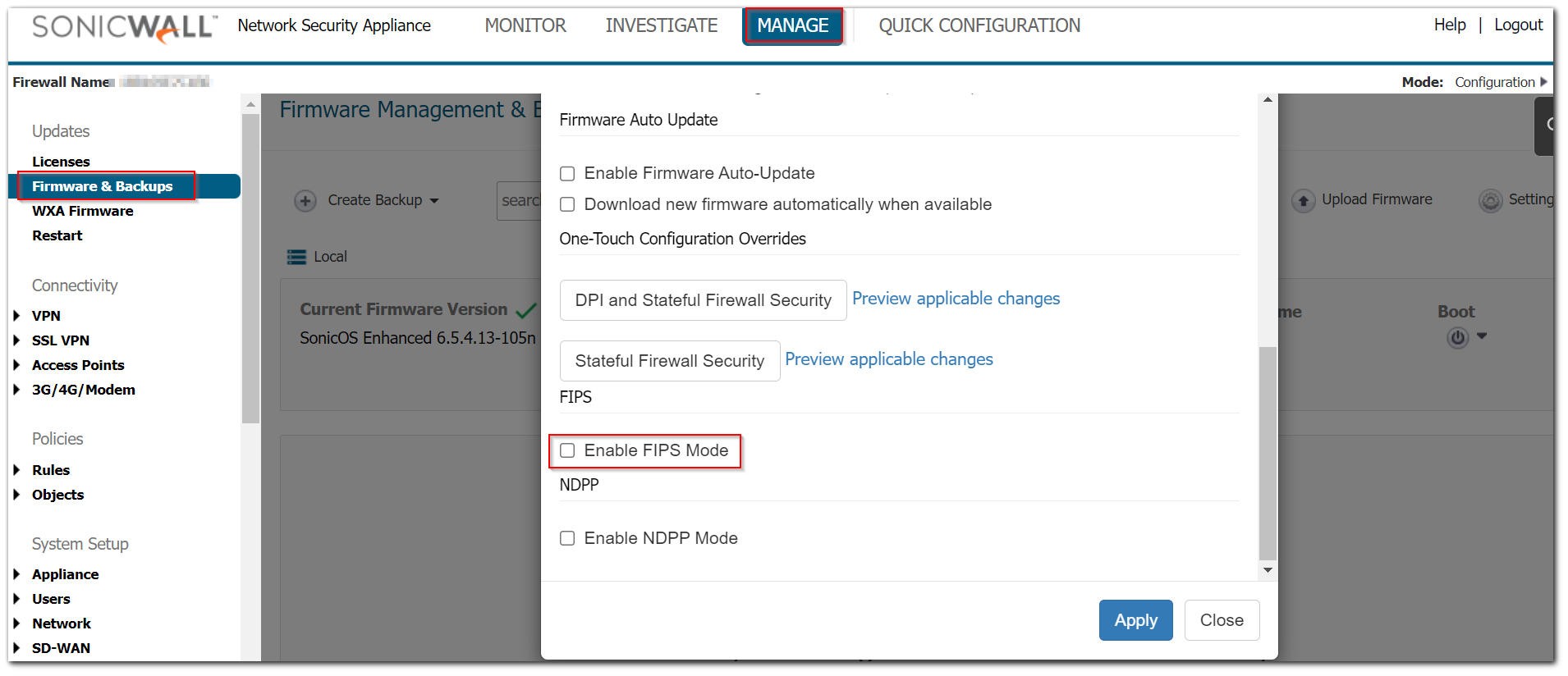
Enabling FIPS Mode
Select Enable FIPS Mode to enable the SonicWall UTM appliance to comply with FIPS. When you check this setting, a dialog box is displayed with the following message:
Warning! Modifying the FIPS mode will disconnect all users and restart the device. Click OK to proceed.
Click OK to reboot the SonicWall in FIPS mode. A second warning displays. Click Yes to continue rebooting. To return to normal operation, Uncheck the Enable FIPS Mode check box and reboot the SonicWall UTM appliance into non-FIPS mode.
 CAUTION: When using the SonicWall UTM appliance for FIPS-compliant operation, the tamper-evident sticker that is affixed to the SonicWall UTM appliance must remain in place and untouched.
CAUTION: When using the SonicWall UTM appliance for FIPS-compliant operation, the tamper-evident sticker that is affixed to the SonicWall UTM appliance must remain in place and untouched.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > NSa Series > System
- Firewalls > NSsp Series > System
- Firewalls > NSv Series






 YES
YES NO
NO