-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How do I configure Sonicwaves for layer 3 management over SSLVPN?



Description
SonicWall UTM appliances running SonicOS Enhanced firmware are capable of discovering and managing Sonicwaves over SSL-VPN
- A SSL VPN connection is established between the Sonicwaves and the managing UTM appliance
- GRE / DTLS (phase II) tunnel is established between the SonicWall UTM appliance and the Sonicwaves to carry management and data traffic(Within the SSLVPN session)
Resolution
Scenario:
Discovering and managing Sonicwaves using SSLVPN over the Internet / WAN.
Please Note: The settings shown in this technote are just an example, you must substitute the settings as per your setup.
Deployment Steps:
Part 1: Configuration on the SonicWall UTM appliance
Step 2: Enable SSL VPN and Create a SSLVPN profile for Sonicwave layer3 Mgmt.
Step 3: Create a user account on the UTM for use on the Sonicwave for sslvpn login from the Sonicwave into the UTM
Part2: Configuration on the Standalone Sonicwave
Step 2: Accessing the Sonicwave Management Interface in Standalone Mode
Step 3: Configuring the SSLVPN Management Settings
Detailed configuration steps:
Part 1: Configuration on the SonicWall UTM appliance
Step 1: Creating a WLAN Tunnel Interface
- Login to the SonicWall Management Interface and go to Network > Interfaces page
- Select WLAN tunnel interface in the Add Interface drop-down menu and configure it as per your setup
Tunnel ID: 0 (zero)
Tunnel Source Interface: X0 / LAN
Mode / IP Assignment: Static
IP Address: 172.16.35.1
Subnet Mask: 255.255.255.0


Step 2: Enable SSL VPN and Create a SSLVPN profile for Sonicwave Layer-3 Management
- Enable SSLVPN on the WAN zone
- Ensure HTTPS mgmt is enabled on the wan interface.
- Create an address object for SSL VPN IP Pool. Network | Address Object | Create a new Address object with the Address type as range/network for SSL VPN IP POOL (refer to the note)
- Goto SSLVPN ----->Client settings and configure the "SonicPoint/sonicwave L3 Management Default Device Profile" as below
 NOTE: The SSLNEW NW is a range address object having an unused IP range from the X0 subnet (LAN) (the interface to which the WT0 is bound to)
NOTE: The SSLNEW NW is a range address object having an unused IP range from the X0 subnet (LAN) (the interface to which the WT0 is bound to)
This object must be assigned with the zone SSLVPN
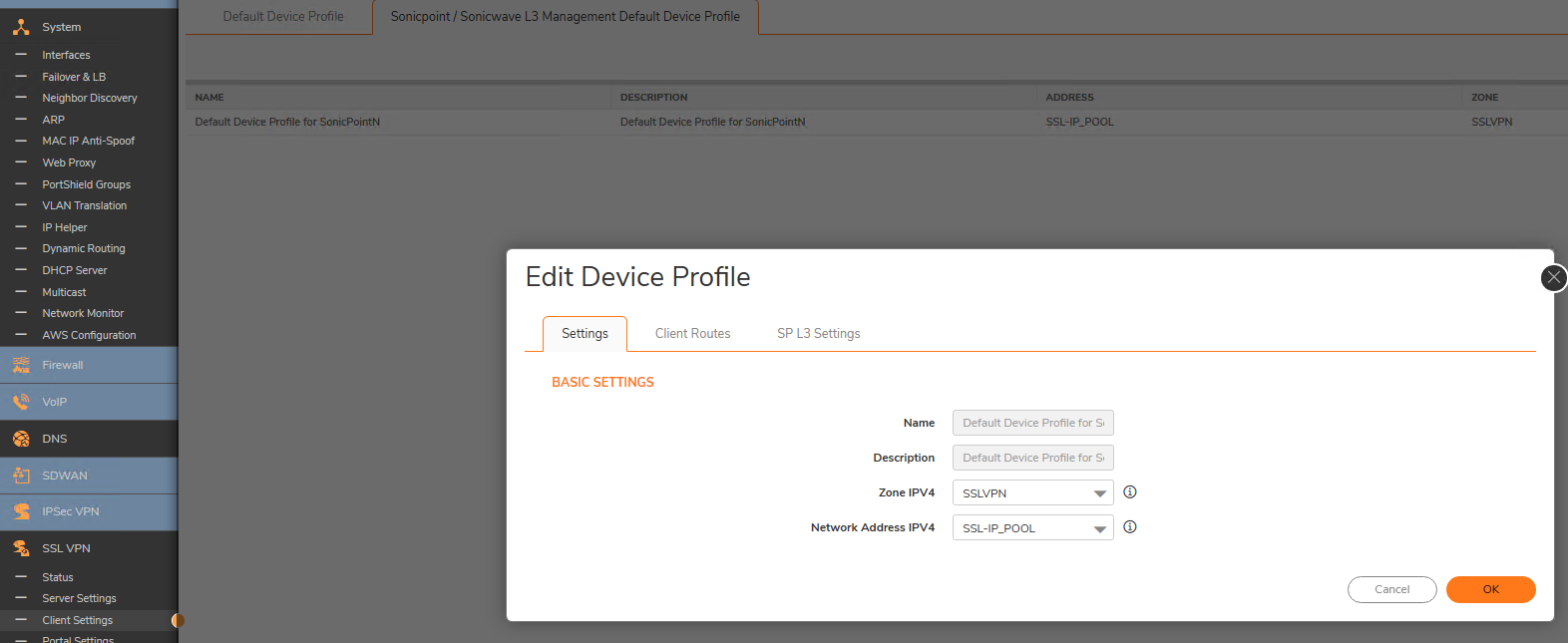
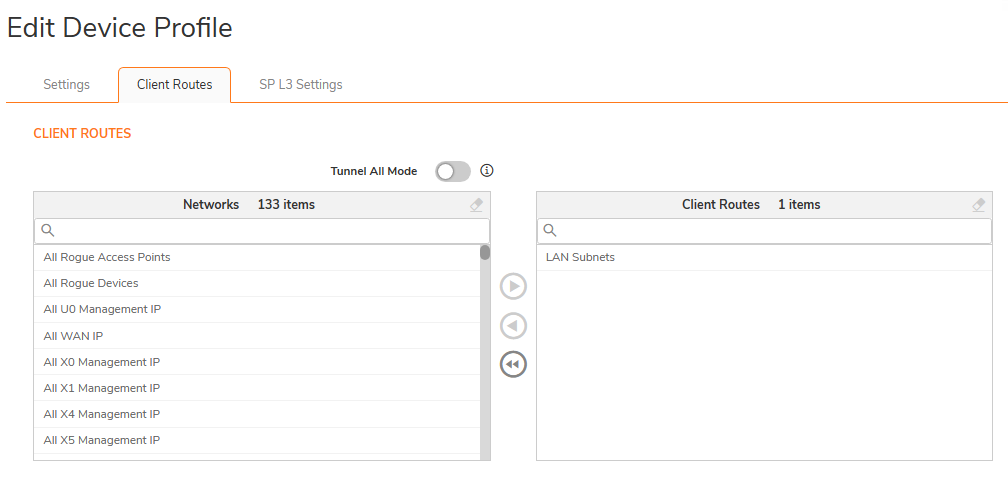
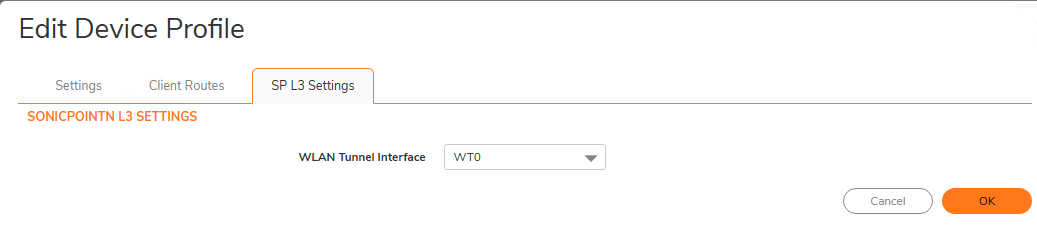
Step 3: Create a user account on the UTM for use on the Sonicwave for SSLVPN login from the Sonicwave into the UTM
Create a local user account on the firewall and ensure that the user is a member of the SSLVPN services group
Also, add X0 subnet and WLAN subnets to the VPN access list.
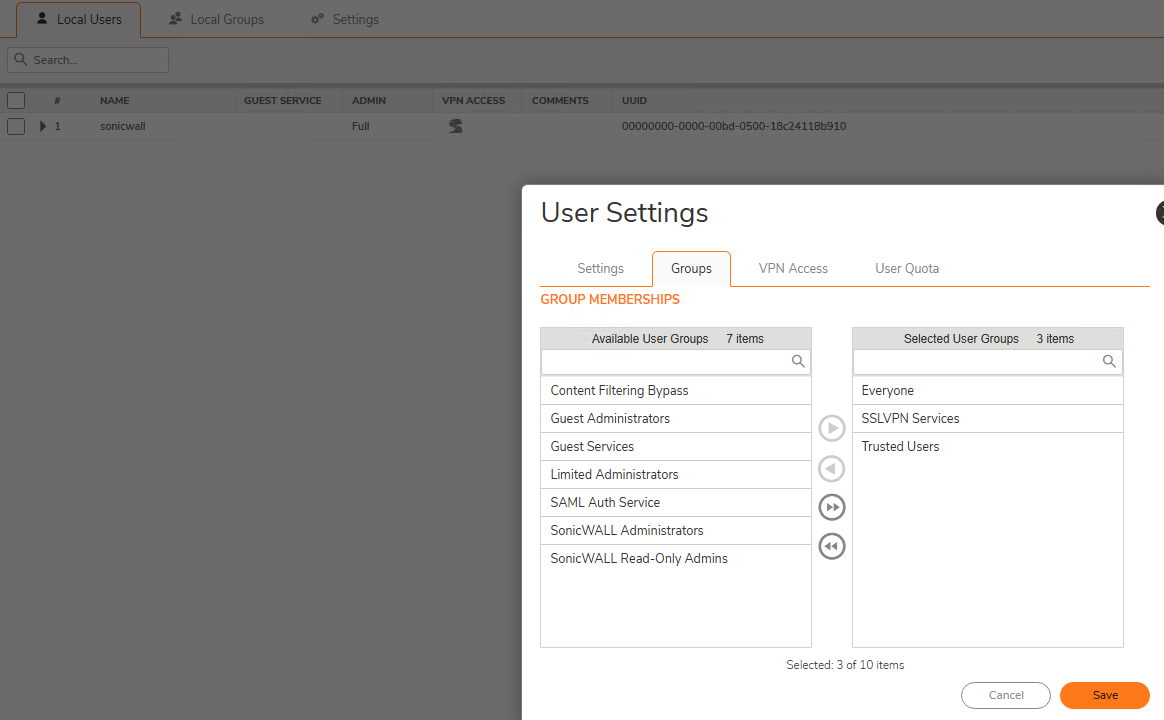
Part 2: Configuration on the Sonicwave
Step 1: Downloading and uploading the SonicOS 9.*.4.7-7o firmware for Sonicwaves
Method 1: Connecting Sonicwaves to SonicWall UTM appliance running SonicOS 7.0.1 and above
When the Sonicwaves are connected to a SonicWall UTM appliance's WLAN interface/Zone running SonicOS 7.0.1 and above, they will be automatically updated with the latest firmware.
Step 2: Accessing the Sonicwave Management Interface in Standalone Mode:
- The default management interface of the SonicPoint is 192.168.1.20
- If you are connecting to the LAN port on the Sonicwave directly from a PC or through only the PoE injector, you need to configure the Local Area Connection on the PC to be in the same subnet as the Sonicwave.
- IP address: 192.168.1.100.
- Netmask: 255.255.255.0.
- Connect directly to the LAN port of the Sonicwave with a crossover cable or regular cat. 5 Ethernet cable.
- Connect to the LAN port of the SonicPoint through the PoE injector with a regular cat. 5 Ethernet cable.
- If the Sonicwave is connected to a port in a SonicWall security appliance and the port is not in a Wireless zone, you can connect to it through the security appliance provided there are rules to allow HTTP management traffic between the zone your management station is in and the zone the Sonicwave is in.
- Start your Web browser and direct it to the default management IP address for the Sonicwave, 192.168.1.20
Troubleshooting Tip: If you are unable to access the Sonicwaveyou may press the Reset Button to access it in SafeMode and then follow the above step
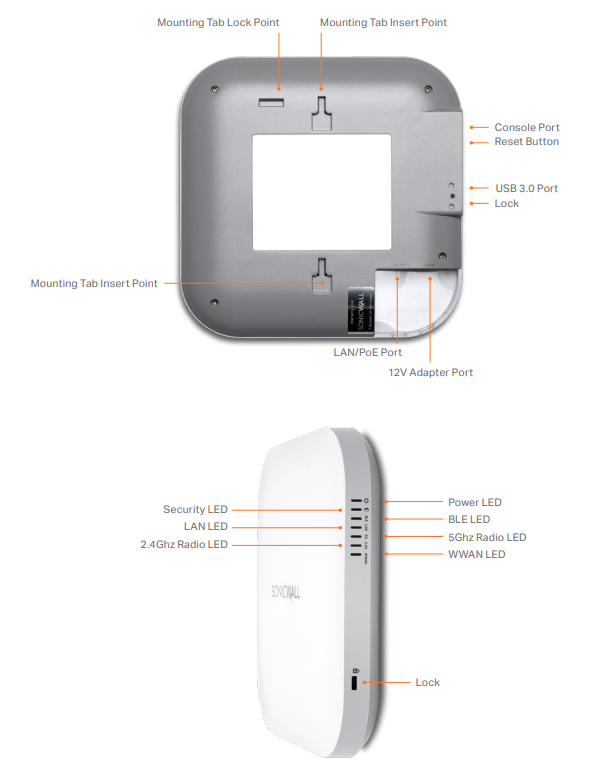
- Start your Web browser and direct it to the default management IP address for the Sonicwave, 192.168.1.20
- Login to the Sonicwave management interface with the default username "admin" and default password "password".
Step 4: Configuring the L3 Management Settings
- Navigate to Sonicwave Network > SSL-VPN page
- Enter the WAN ip-address of the UTM along with the SSLVPN port number
- Enter the SSLVPN user credentials, enable the Auto-Reconnect checkbox,
- Enable "Enable SSL-VPN based Layer3 Management"
- Click on the Save button on the bottom and click connect
- You will get a prompt at the Top to Restart the Sonicwave, click on Restart and restart the appliance.

-
Please Note: After the reboot the Sonicwave will try to establish a SSLVPN connection with the UTM and a GRE/DTLS tunnel would be setup within this SSLVPN connection to complete the Sonicwave provisioning. Sonicwave might reboot and SSL VPN user logout several times before Sonicwave shows up as operational because of the provisioning process that the Sonicwave goes through.
How to Test
Go to Sonicwave > Network >SSL-VPN page, you must see the client ip from Firewall.
Related Articles
- Wireless: SNR, RSSI and Noise basics of wireless troubleshooting
- What happens when a SonicWave's license expires?
- SonicWall deprecates support for WEP and TKIP encryption on SonicOS 8.0.0
Categories
- Secure Wireless > SonicWave 200 Series
- Secure Wireless > SonicWave 400 Series
- Secure Wireless > SonicWave 600 Series






 YES
YES NO
NO