-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How do I configure and use the Threat API feature on my firewall?



Description
Threat API allows administrators to create/retrieve/delete lists of URLs or IP addresses to be blocked via RESTful API calls.
- Threat API settings are only available to the build-in “admin” user. It won't work with other users, even if full admin privileges are assigned.
- HTTPS management must be enabled on the interface that the Threat API call will be coming from.
- SonicOS Threat API requires that the firewall has a Content Filtering Service (CFS) license.
- Also, Content Filtering Service needs to be enabled on the firewall.
- Threat API is independent from the main SonicOS API. This is not required to be enabled to have Threat API to function.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- The Threat API feature is dependent on a valid CFS license.
- Confirm that the firewall has valid CFS license
- Confirm that CFS is enabled
- On Gen7 UTM firewalls, enabling Threat API is only possible via CLI. Enter the following command sequence after logging into the firewall via SSH or Serial Console Port.
configure terminal
content-filter
profile "CFS Default Profile"
threat-api
exit
exit
diag advanced threat-api
enforcement
commit - You can login to the firewall to confirm that the Threat API is enabled.
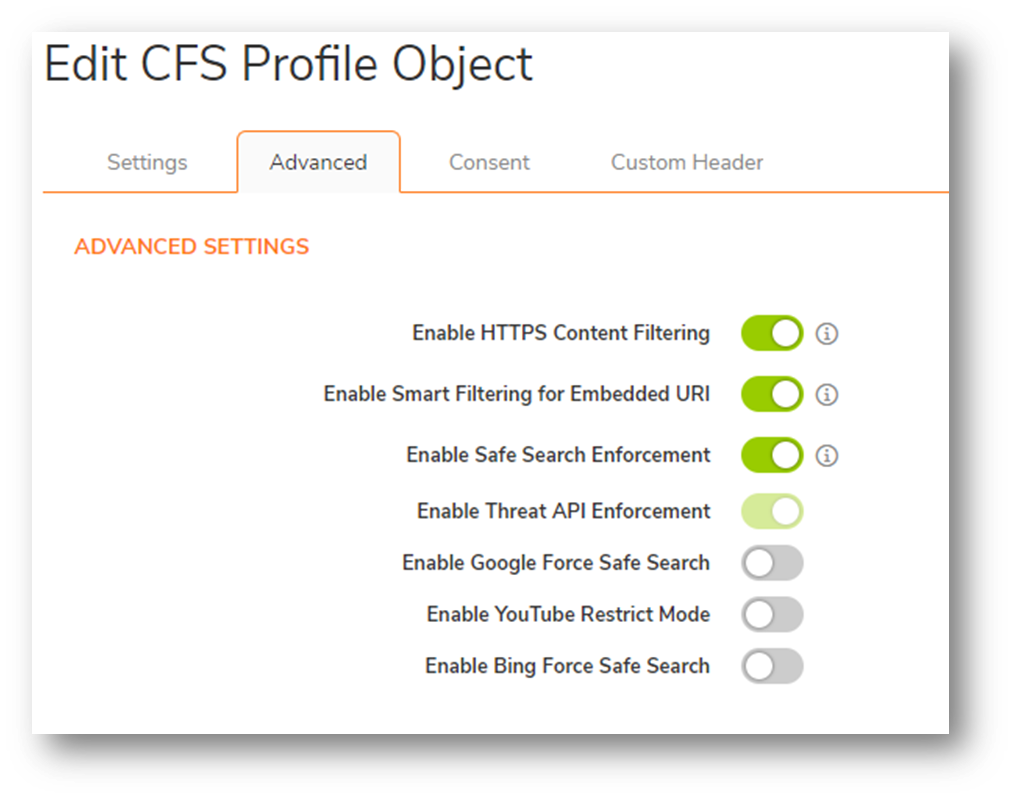
Threats can be added as URIs (eg. example.com) or IP addresses (eg. 1.1.1.2)
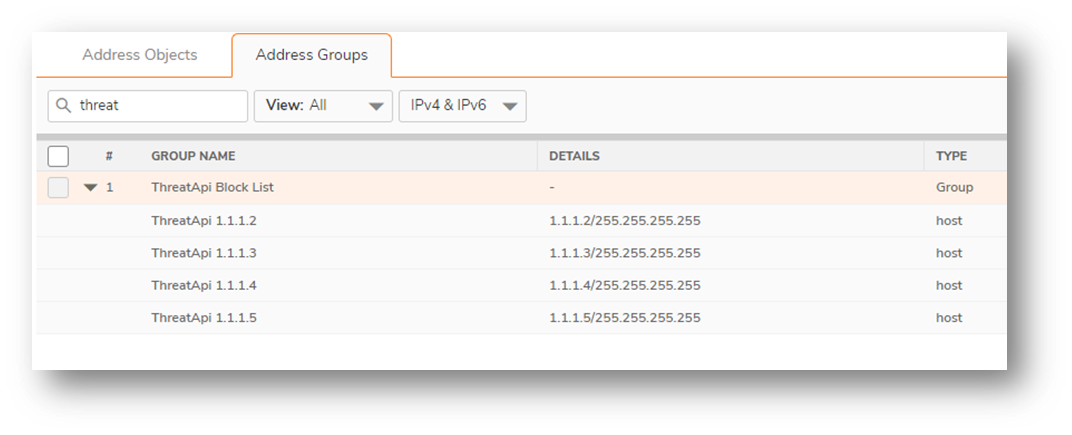
For IP addresses, SonicOS initially creates an Address Group named ThreatApiBlock List and then creates address objects (AO) for each IP address in the threat list. The SonicOS administrator needs to configure the firewall access rule that references that address group in order block those.
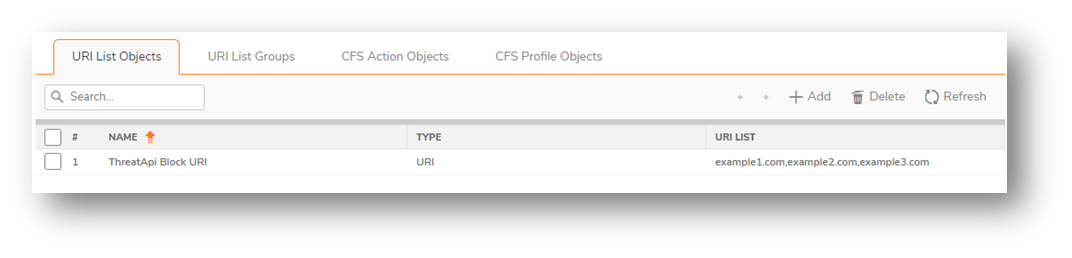
For URLs SonicOS adds the URIs to its ThreatApi Block URI list object. This list object can be used to be blocked within one of the CFS Profile Objects. When a threat is blocked by CFS, the user will see a block message in their browser.
The following API endpoints are available to retrieve, create and delete URIs.
• GET /threat/block/uri/ – Retrieves the URI blocklist.
• POST /threat/block/uri/ – Creates the URI blocklist.
• DELETE /threat/block/uri/ – Deletes the URI blocklist.
The following API endpoints are available to retrieve, create and delete IP addresses.
• GET /threat/block/ip/ – Retrieves list of IP addresses.
• POST /threat/block/ip/ – Creates the IP address.
• DELETE /threat/block/ip/ – Deletes the IP address.
To create the IP address and the address object:curl -k -i -u admin:password -X POST -d "1.1.1.2" https://192.168.1.254/threat/block/ip/
To delete the IP address and the address object:
curl -k -i -u admin:password -X DELETE -d "1.1.1.2" https://192.168.1.254/threat/block/ip/
To get all the IP addresses that are part of the ThreatApiBlock List
curl -k -i -u admin:password -X GET https://192.168.1.254/threat/block/ip/
To instantiate a URI block lists with a single/multiple entry:curl -k -i -u admin:password -X POST -d "example1.com" https://192.168.1.254/threat/block/uri/
curl -k -i -u admin:password -X POST -d "example2.com,example3.com" https://192.168.1.254/threat/block/uri/
Delete URI entries:
curl -k -i -u admin:password -X DELETE https://192.168.1.254/threat/block/uri/
To get all the URIs that are part of the ThreatApiBlock URI
>curl -k -i -u admin:password -X GET https://192.168.1.254/threat/block/ip/
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- The Threat API feature is dependent on a valid CFS license.
- Confirm that the firewall has valid CFS license
- Confirm that CFS is enabled
Enable Threat API by going to the internal settings of the firewall which is accessible via the diag.html page.
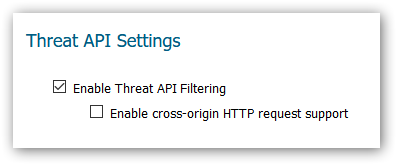
Threats can be added as URIs (eg. example.com) or IP addresses (eg. 1.1.1.2)
For IP addresses in the threat list, SonicOS initially creates a default Threat API address group and then creates an address object (AO) for each IP address in the threat list. The SonicOS administrator configures firewall access rules that reference that address group and block the IP addresses.
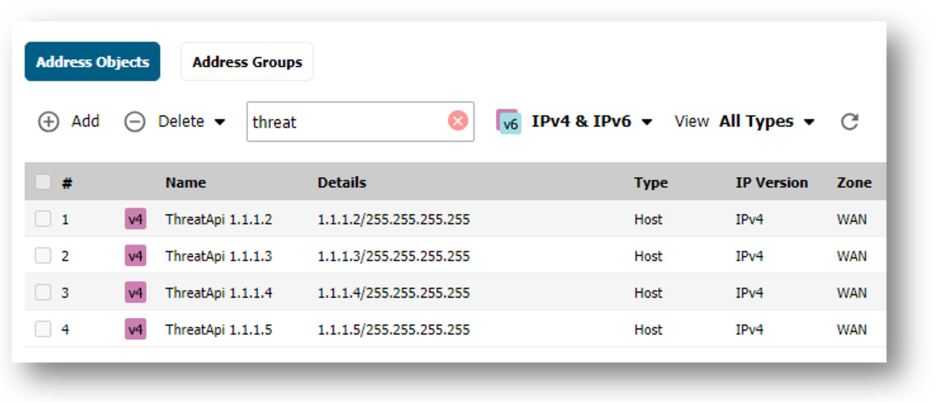
For URLs SonicOS adds the URIs to its ThreatApi Block URI list object. This list object can be used to be blocked within one of the CFS Profile Objects. When a threat is blocked by CFS, the user will see a block message in their browser..
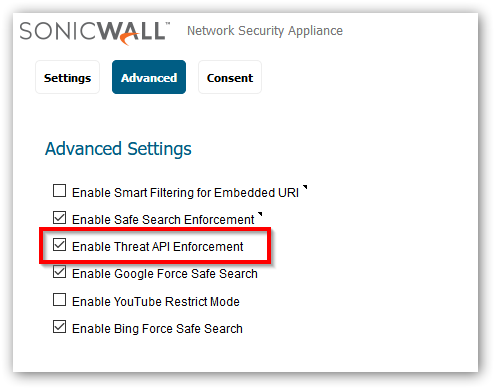
The following API endpoints are available to retrieve, create and delete URIs.
• GET /threat/block/uri/ – Returns URI blocklist.
• POST /threat/block/uri/ – Instantiates the URI blocklist.
• DELETE /threat/block/uri/ – Deletes the URI blocklist.
The following API endpoints are available to retrieve, create and delete IP addresses.
• GET /threat/block/ip/ – Returns list of IP addresses.
• POST /threat/block/ip/ – Creates the IP address.
• DELETE /threat/block/ip/ – Deletes the IP address.
To create the IP address and the address object:curl -k -i -u admin:password -X POST -d "1.1.1.2" https://192.168.1.254/threat/block/ip/
To delete the IP address and the address object:
curl -k -i -u admin:password -X DELETE -d "1.1.1.2" https://192.168.1.254/threat/block/ip/
To get all the IP addresses that are part of the ThreatApiBlock List
curl -k -i -u admin:password -X GET https://192.168.1.254/threat/block/ip/
To instantiate a URI block lists with a single/multiple entry:curl -k -i -u admin:password -X POST -d "example1.com" https://192.168.1.254/threat/block/uri/
curl -k -i -u admin:password -X POST -d "example2.com,example3.com" https://192.168.1.254/threat/block/uri/
Delete URI entries:
curl -k -i -u admin:password -X DELETE https://192.168.1.254/threat/block/uri/
To get all the URIs that are part of the ThreatApiBlock URI
>curl -k -i -u admin:password -X GET https://192.168.1.254/threat/block/ip/
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > Content Filtering Service
- Firewalls > SonicWall NSA Series > Content Filtering Service
- Firewalls > TZ Series > Content Filtering Service
- Firewalls > NSa Series > Content Filtering Service
- Firewalls > NSv Series > Firmware






 YES
YES NO
NO