-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How do I configure a route based VPN between SonicWall and Cisco?



Description
When configuring a Route Bases VPN in SonicOS Enhanced firmware using Main Mode both the SonicWall appliances and Cisco ASA firewall (Site A and Site B) must have a routable Static WAN IP address.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
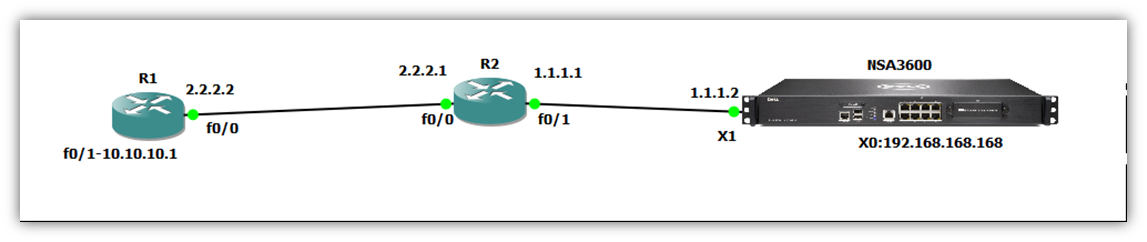
Deployment Steps:
Step 1: Configuring a VPN policy on Site A SonicWall.
Step 2: Configuring a VPN policy on Site B Cisco ASA Firewall
Step 3: How to test this scenario.
To manually configure a VPN Policy using IKE with Preshared Secret, follow the steps below:
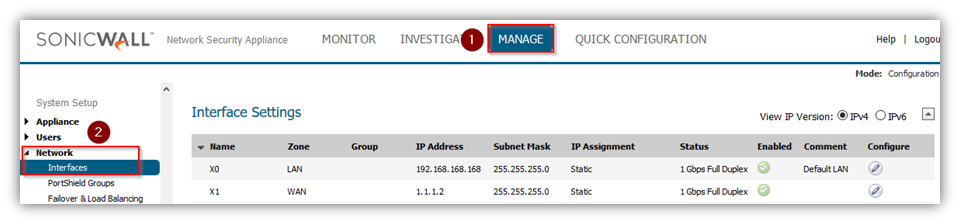
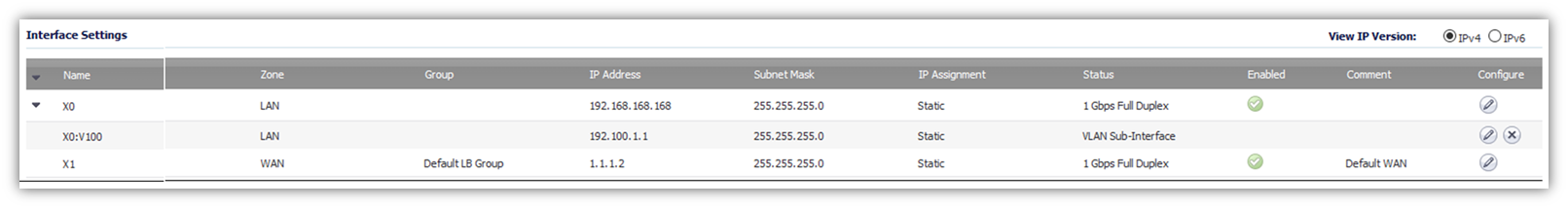
The below screen shot of SonicWall with basic configuration LAN and WAN.
Configuring a VPN policy on Site A SonicWall
Login to the SonicWall Management GUI
- Click Manage in the top navigation menu
- Navigate to VPN | Base Settings
- Enable VPN
- Click Add. The VPN Policy window is displayed.
- Click the General tab

- Select Tunnel Interface from the Policy Type menu
- Select IKE using Preshared Secret from the Authentication Method menu.
- Enter a name for the policy in the Name field.
- Enter the WAN IP address of the remote connection in the IPsec Primary Gateway Name or Address field (Enter Site B's WAN IP address).
- If the Remote VPN device supports more than one endpoint, you may optionally enter a second host name or IP address of the remote connection in the IPsec Secondary Gateway Name or Address field.
Note: Secondary gateways are not supported with IKEv2. - Enter a Shared Secret password to be used to setup the Security Association the Shared Secret and Confirm Shared Secret fields. The Shared Secret must be at least 4 characters long, and should comprise both numbers and letters. Optionally, you may specify a Local IKE ID (optional) and Peer IKE ID (optional) for this Policy. By default, the IP Address (ID_IPv4_ADDR) is used for Main Mode negotiations, and the SonicWall Identifier (ID_USER_FQDN) is used for Aggressive Mode.
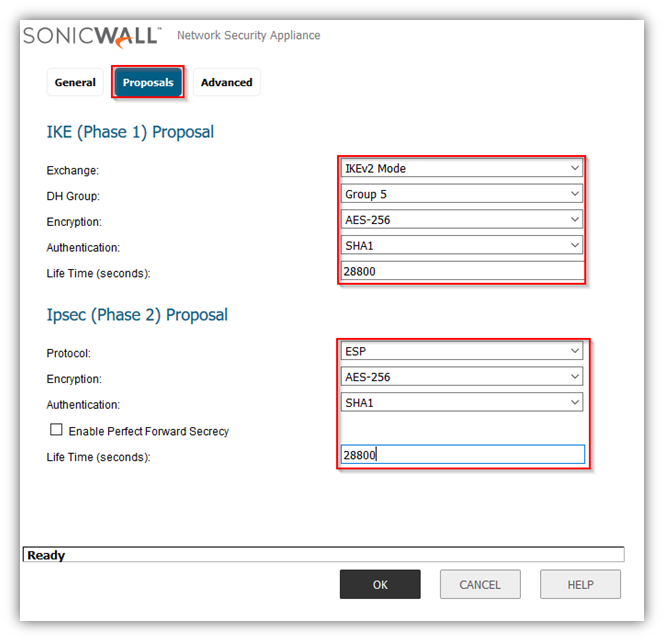
- Click the Proposal tab.
- Under IKE (Phase 1) Proposal, select Main Mode from the Exchange menu. Aggressive Mode is generally used when WAN addressing is dynamically assigned. IKEv2 causes all the negotiation to happen via IKE v2 protocols, rather than using IKE Phase 1 and Phase 2. If you use IKE v2, both ends of the VPN tunnel must use IKE v2.
- Under IKE (Phase 1) Proposal, the default values for DH Group, Encryption, Authentication, and Life Time are acceptable for most VPN configurations. Be sure the Phase 1 values on the opposite side of the tunnel are configured to match. You can also choose AES-128, AES-192, or AES-256 from the Authentication menu instead of 3DES for enhanced authentication security.
Note: The Windows 2000 L2TP client and Windows XP L2TP client can only work with DH Group 2. They are incompatible with DH Groups 1 and 5. - Under IPsec (Phase 2) Proposal, the default values for Protocol, Encryption, Authentication, Enable Perfect Forward Secrecy, DH Group, and Lifetime are acceptable for most VPN SA configurations. Be sure the Phase 2 values on the opposite side of the tunnel are configured to match.
- Click the Advanced tab

- Select Enable Keep Alive to use heartbeat messages between peers on this VPN tunnel. If one end of the tunnel fails, using Keepalives will allow for the automatic renegotiation of the tunnel once both sides become available again without having to wait for the proposed Life Time to expire.
- Select Enable Windows Networking (NetBIOS) Broadcast to allow access to remote network resources by browsing the Windows Network Neighborhood.
- Select an interface or zone from the VPN Policy bound to menu. A Zone WAN is the preferred selection if you are using WAN Load Balancing and you wish to allow the VPN to use either WAN interface.
- Click OK to apply the settings.
Creating and Configuring a VPN tunnel interface.
- Click Manage in the top navigation menu
- Navigate to the Network | Interfaces page.
- Add Interface. Click on VPN Tunnel interface.
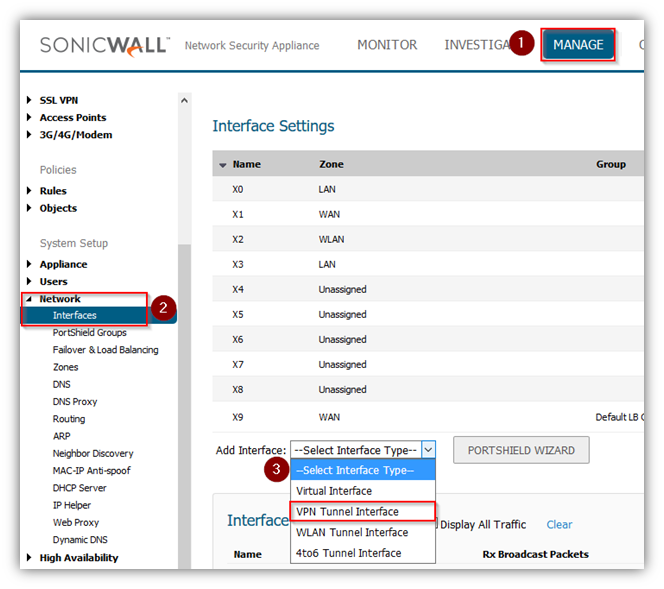
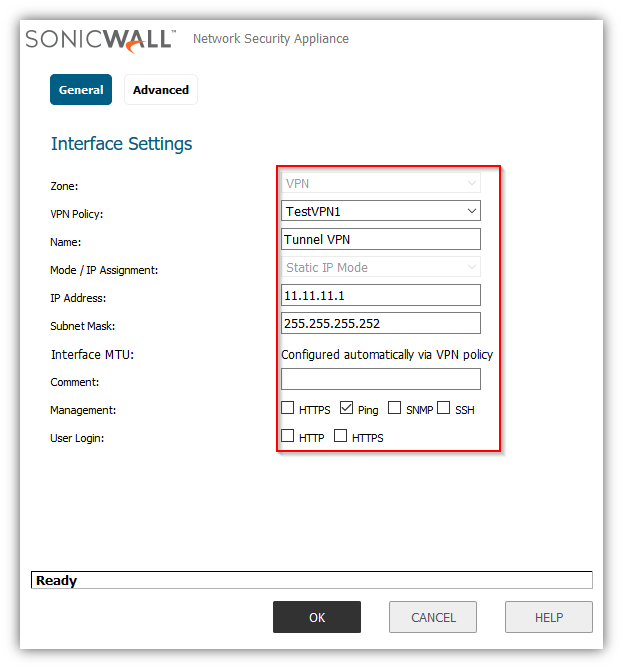
- Zone is VPN
- Select the policy Name under VPN policy dropdown menu.
- Mode/IP assignment 11.11.11.1/30 matching the same subnet on tunnel interface on Cisco device.
- Enable Ping for verifying.
Configuring a VPN policy on Site B Cisco ASA
- Login to Cisco device.
- Configure WAN and LAN. The screen shot below with WAN configured as Outside with IP 23.45.67.89 and LAN configured as LAN with IP 20.20.20.1.
Verifying the initial Configuration on Cisco ASA.
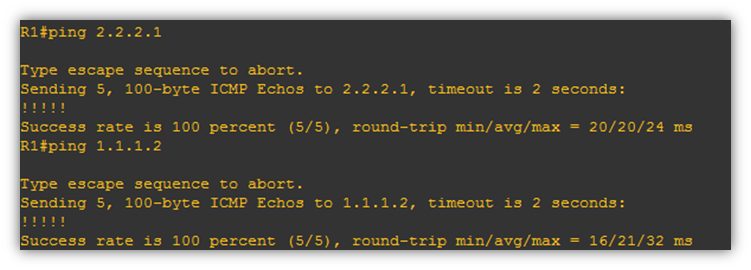
In the below screenshot we checking the connectivity to upstream modem(ISP) and also remote end SonicWall WAN IP by pinging the IP address.
First Ping to Cisco gateway- 2.2.2.1 –Passed
Second Ping to SonicWall WAN IP-1.1.1.2-Passed
Now we configure the route based VPN.
- Create a pre-shared key
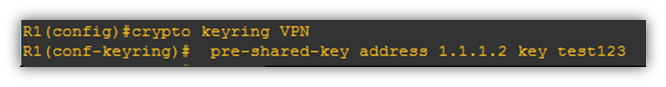
- Create a ISAKMP Policy
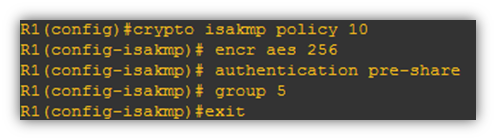
- Create a ISAKMP Profile
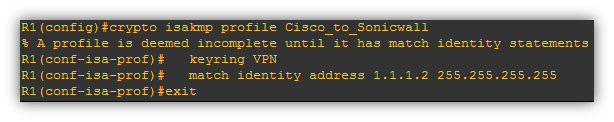
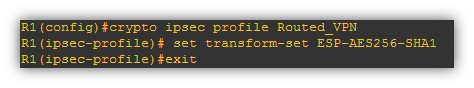
- Define an IPsec transform-set
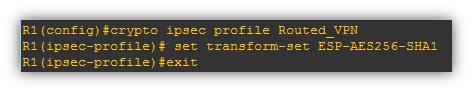
- Define an IPsec Profile
- Create a VPN Tunnel Interface
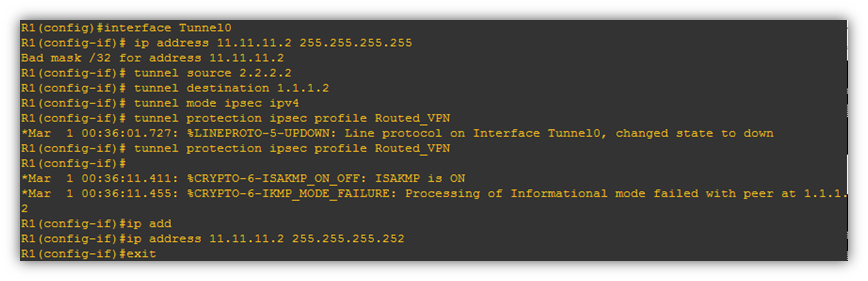
How to test this Scenario:
Find the screen shot below on SonicWall with active VPN Tunnel.
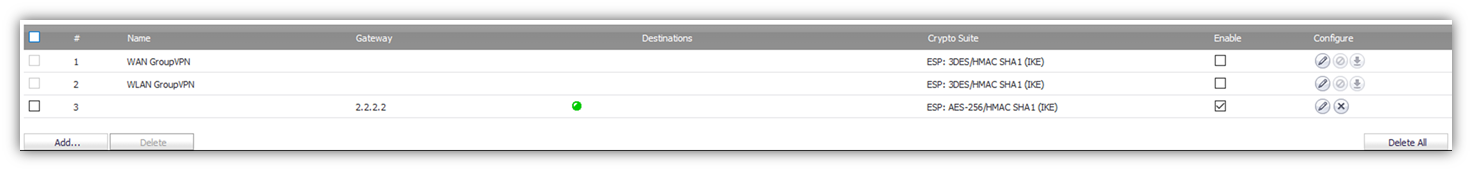
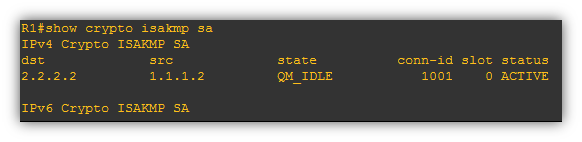
Screenshot below on Cisco with active VPN Tunnel
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
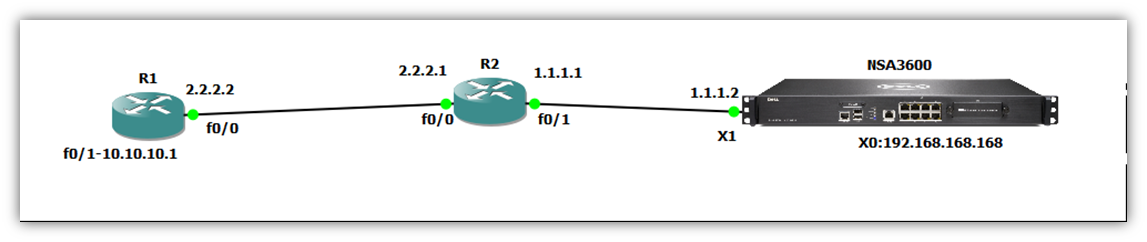
Deployment Steps:
Step 1: Configuring a VPN policy on Site A SonicWall.
Step 2: Configuring a VPN policy on Site B Cisco ASA Firewall
Step 3: How to test this scenario.
Procedure:
To manually configure a VPN Policy using IKE with Preshared Secret, follow the steps below:
The below screen shot of SonicWall with basic configuration LAN and WAN.
Configuring a VPN policy on Site A SonicWall
- Navigate to VPN | Settings page and Click Add button. The VPN Policy window is displayed.
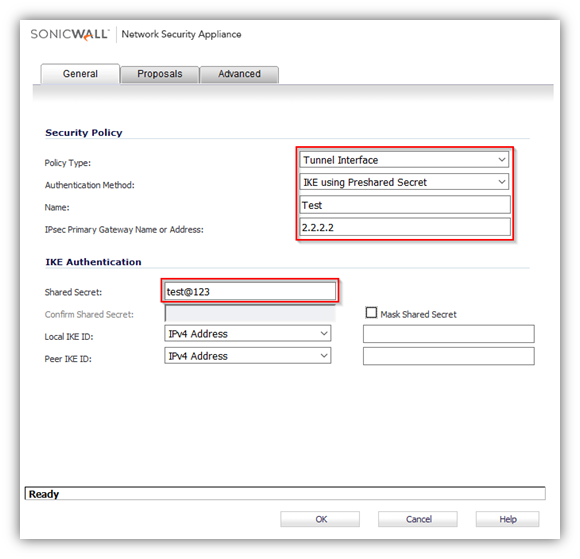
- Click the General tab
- Select Tunnel Interface from the Policy Type menu.
- Select IKE using Preshared Secret from the Authentication Method menu.
- Enter a name for the policy in the Name field.
- Enter the WAN IP address of the remote connection in the IPsec Primary Gateway Name or Address field (Enter Site B's WAN IP address).
- If the Remote VPN device supports more than one endpoint, you may optionally enter a second host name or IP address of the remote connection in the IPsec Secondary Gateway Name or Address field.
Note: Secondary gateways are not supported with IKEv2. - Enter a Shared Secret password to be used to setup the Security Association the Shared Secret and Confirm Shared Secret fields. The Shared Secret must be at least 4 characters long, and should comprise both numbers and letters. Optionally, you may specify a Local IKE ID (optional) and Peer IKE ID (optional) for this Policy. By default, the IP Address (ID_IPv4_ADDR) is used for Main Mode negotiations, and the SonicWall Identifier (ID_USER_FQDN) is used for Aggressive Mode.
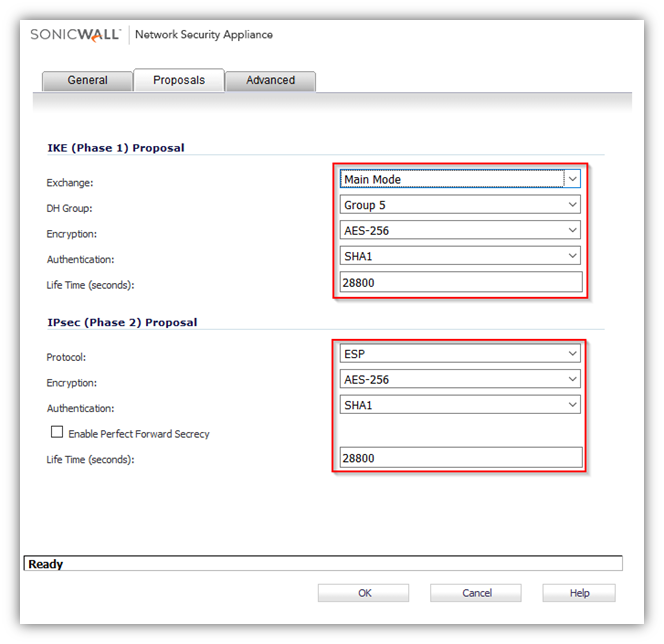
- Click the Proposals tab.
- Under IKE (Phase 1) Proposal, select Main Mode from the Exchange menu. Aggressive Mode is generally used when WAN addressing is dynamically assigned. IKEv2 causes all the negotiation to happen via IKE v2 protocols, rather than using IKE Phase 1 and Phase 2. If you use IKE v2, both ends of the VPN tunnel must use IKE v2.
- Under IKE (Phase 1) Proposal, the default values for DH Group, Encryption, Authentication, and Life Time are acceptable for most VPN configurations. Be sure the Phase 1 values on the opposite side of the tunnel are configured to match. You can also choose AES-128, AES-192, or AES-256 from the Authentication menu instead of 3DES for enhanced authentication security.
Note: The Windows 2000 L2TP client and Windows XP L2TP client can only work with DH Group 2. They are incompatible with DH Groups 1 and 5. - Under IPsec (Phase 2) Proposal, the default values for Protocol, Encryption, Authentication, Enable Perfect Forward Secrecy, DH Group, and Lifetime are acceptable for most VPN SA configurations. Be sure the Phase 2 values on the opposite side of the tunnel are configured to match.
- Click the Advanced tab

- Select Enable Keep Alive to use heartbeat messages between peers on this VPN tunnel. If one end of the tunnel fails, using Keepalives will allow for the automatic renegotiation of the tunnel once both sides become available again without having to wait for the proposed Life Time to expire.
- Select Enable Windows Networking (NetBIOS) Broadcast to allow access to remote network resources by browsing the Windows® Network Neighborhood.
- Select an interface or zone from the VPN Policy bound to menu. A Zone WAN is the preferred selection if you are using WAN Load Balancing and you wish to allow the VPN to use either WAN interface.
- Click OK to apply the settings.
Creating and Configuring a VPN tunnel interface.
- Navigate to Network | Interfaces. Select VPN Tunnel Interface under Add Interface.
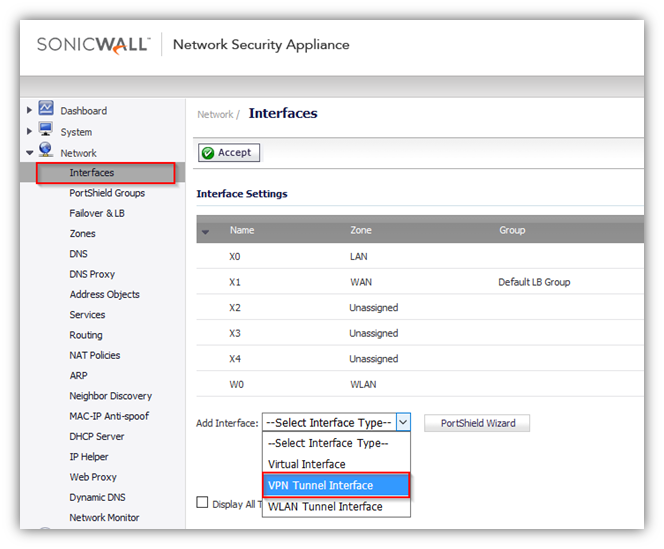

- Zone is VPN
- Select the policy Name under VPN policy dropdown menu.
- Mode/IP assignment 11.11.11.1/30 matching the same subnet on tunnel interface on Cisco device.
- Enable Ping for verifying.
Configuring a VPN policy on Site B Cisco ASA
- Login to Cisco device.
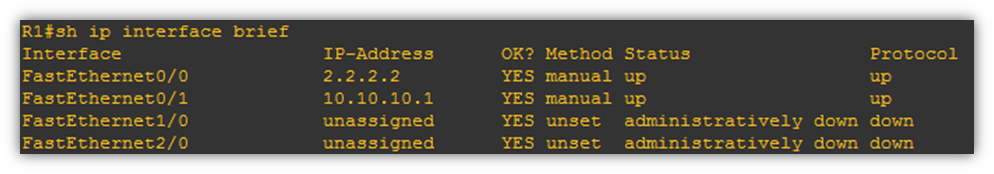
- Configure WAN and LAN. The screen shot below with WAN configured as Outside with IP 23.45.67.89 and LAN configured as LAN with IP 20.20.20.1.

Verifying the initial Configuration on Cisco ASA.
In the below screenshot we checking the connectivity to upstream modem(ISP) and also remote end SonicWall WAN IP by pinging the IP address.
First Ping to Cisco gateway- 2.2.2.1 –Passed
Second Ping to SonicWall WAN IP-1.1.1.2-Passed

Now we configure the route based VPN.
- Create a pre-shared key

- Create a ISAKMP Policy

- Create a ISAKMP Profile

- Define an IPsec transform-set

- Define an IPsec Profile

- Create a VPN Tunnel Interface

How to test this Scenario:
Find the screen shot below on SonicWall with active VPN Tunnel.

Screenshot below on Cisco with active VPN Tunnel

Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO