-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I set up a WireGuard tunnel using a Docker Container?



Description
Docker enables more efficient use of system resources, enables application portability, shines for microservices architecture etc. This article helps to setting up WireGuard tunnel using a docker container. The WireGuard tunnel over docker container is able to support any system
capable of running Docker. The basic Docker container for wireGuard can run its own container. We download our Cloud Edge peer configuration file for WireGuard and mount it on a shared folder to its location on the Docker host in order to share it with the Docker container. This will bring the connectivity of Docker containers to Cloud Edge and we can securely access resources of docker container via Cloud Edge.
Resolution
- Install Docker on your OS.Get the Docker , Install and configure Docker on your OS
- Create a barebones config YAML file for your docker container "docker-compose.yaml” as per OS type and copy to the location as per mentioned in the script “Volumes” below
Linux Version:
---
version: "2.1"
services:
wireguard:
image: ghcr.io/linuxserver/wireguard
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE
environment:
- PUID=1000
- PGID=1000
- TZ=America/New_York
volumes:
- /var/tmp/config:/config
- /lib/modules:/lib/modules
ports:
- 8000:8000/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stopped NOTE: You can change the Time Zone (TZ) as per your docker container, by default this script will set to America/New York. Similarly set the volumes as per your location of the this YAML
NOTE: You can change the Time Zone (TZ) as per your docker container, by default this script will set to America/New York. Similarly set the volumes as per your location of the this YAML
config on your OS.
Windows Version:
---
version: "2.1"
services:
wireguard:
image: ghcr.io/linuxserver/wireguard
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE
environment:
- PUID=1000
- PGID=1000
- TZ=America/New_York
volumes:
- C://wgConfig:/config
- /lib/modules:/lib/modules
ports:
- 8000:8000/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stopped - Create a “wg0.conf” file using the Cloud Edge peer wireguard and copy the file as per the location mentioned in the volumes as step #2.
- Login to Cloud Edge as admin and configure WireGuard connector to the desired network
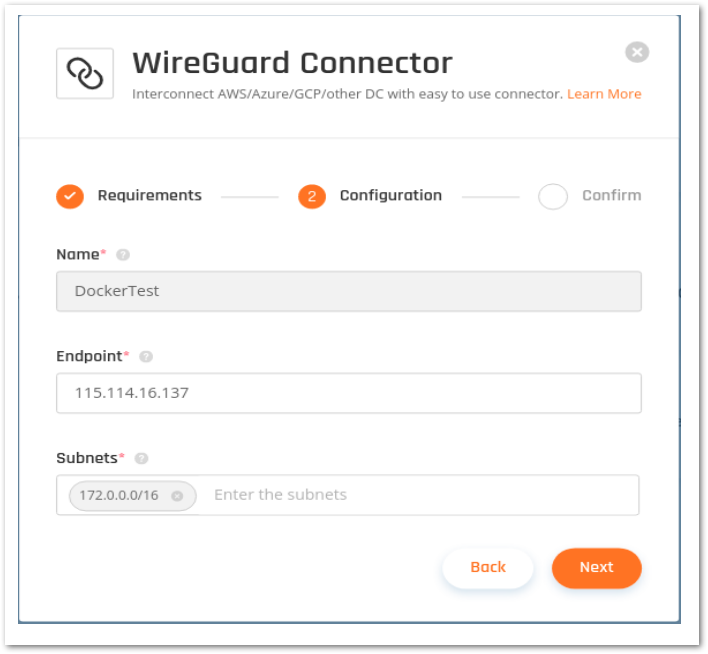
- Copy the URL in the configuration tab of the WireGuard connector on Cloud Edge.
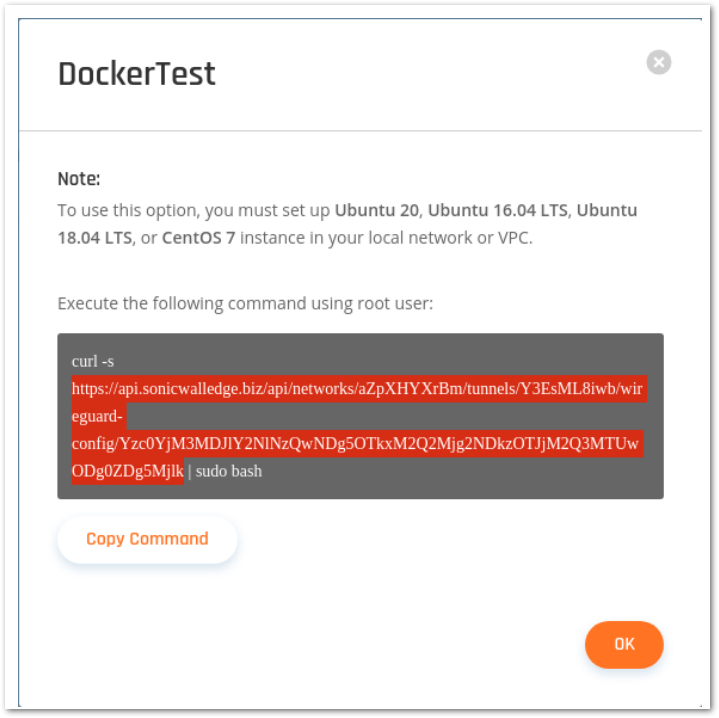
 NOTE: Don't copy the command from this article - each tunnel will have adifferent URL and configuration file
NOTE: Don't copy the command from this article - each tunnel will have adifferent URL and configuration file - Paste the URL into a web browser. This will immediately be followed by a file download. Download the config file
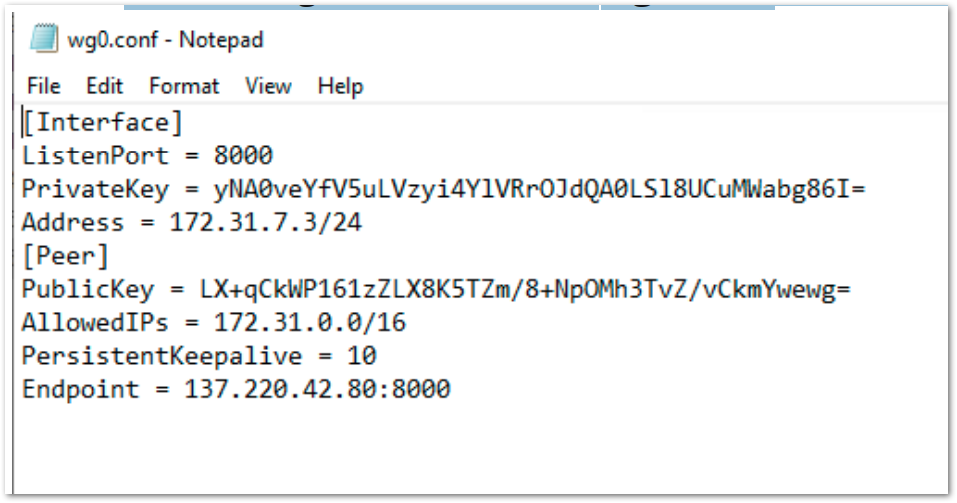
- Open the config and copy the Interface information as highlighted in the screen shot below. Copy & paste the code to the wg0.conf file
[Interface]
ListenPort = ${CONFIG_port}
PrivateKey = ${CONFIG_privateKey}
Address = ${CONFIG_address}
[Peer]
PublicKey = ${CONFIG_pubKey}
AllowedIPs = ${CONFIG_allowedIP}
PersistentKeepalive = 10
Endpoint = ${CONFIG_endpoint}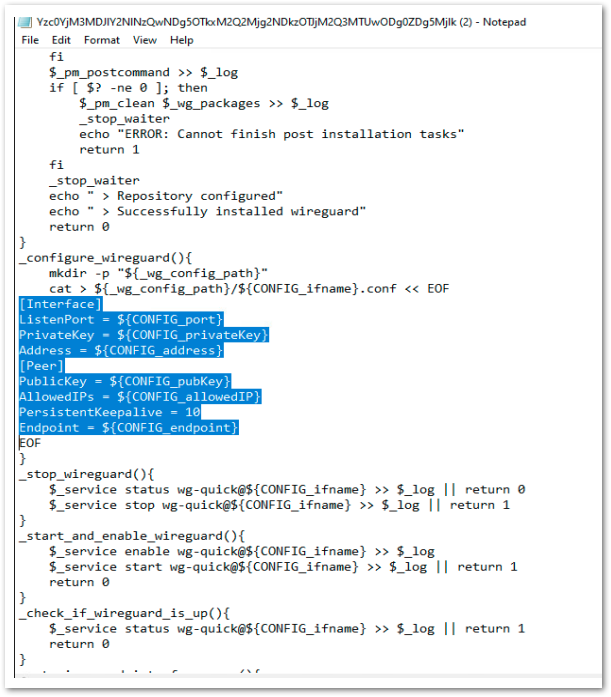
- Copy the Cloud Edge peer for wireguard from the configuration file. It starts with ‘CONFIG_ ‘ see the screen shot of the config file and fill the details to the wg0.conf file
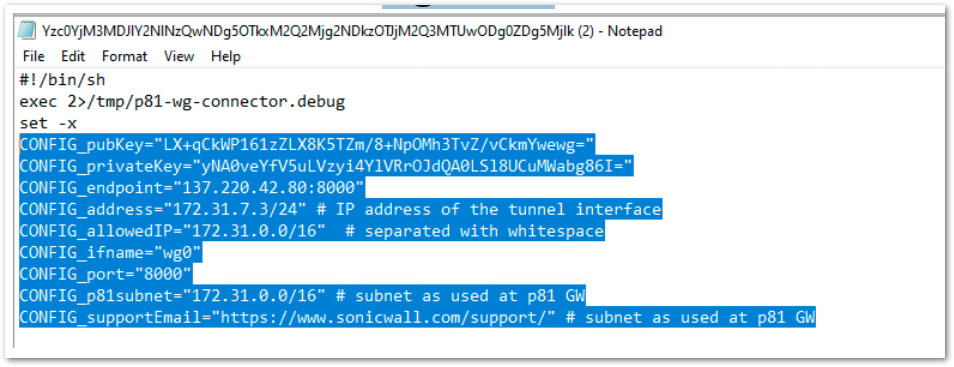
- After filling all data to the "wg0.conf" file, this will look like below
- Login to Cloud Edge as admin and configure WireGuard connector to the desired network
- Run the following command from command prompt or terminal (as admin). Make sure to run this from the directory where dockercompose.yaml resides
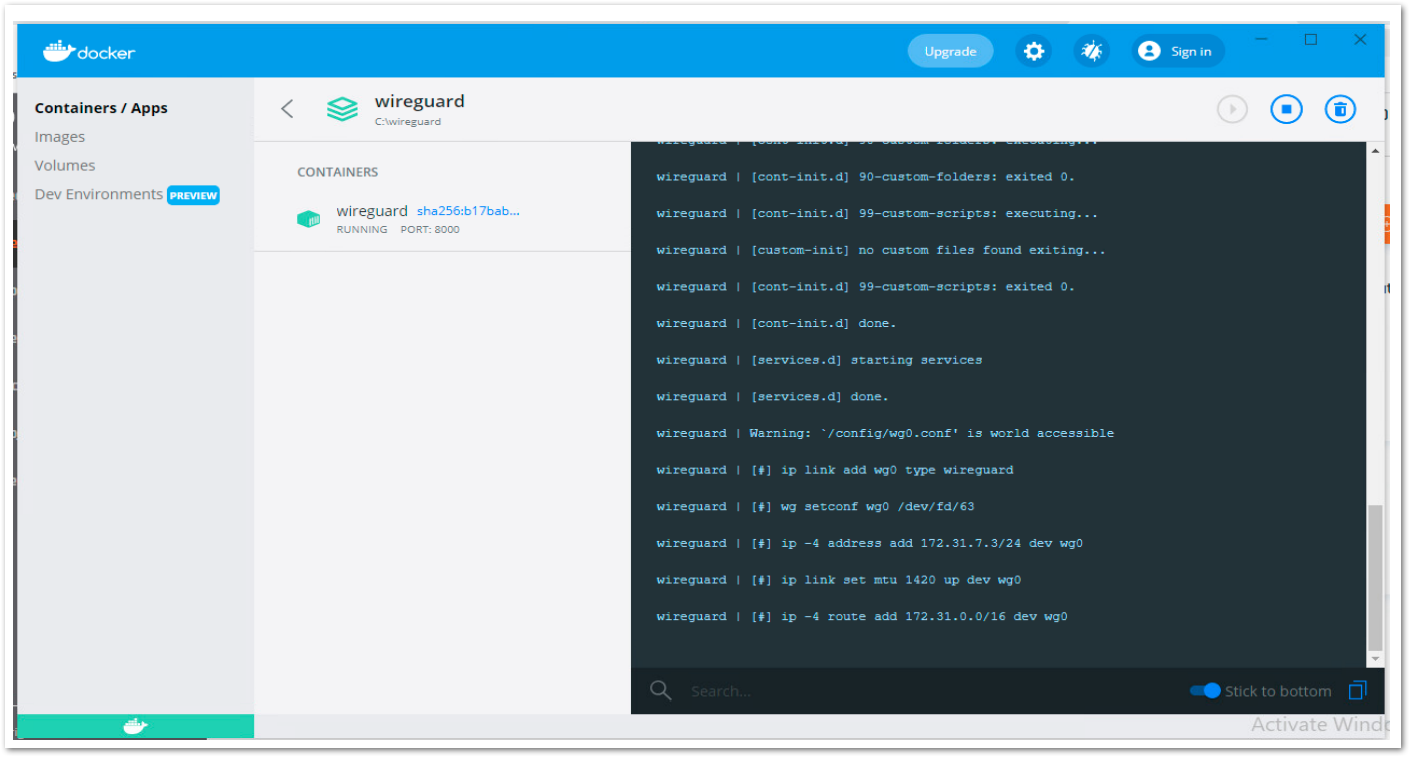
Docker-compose up –d
- Docker container is up and running with wireguard configuration.
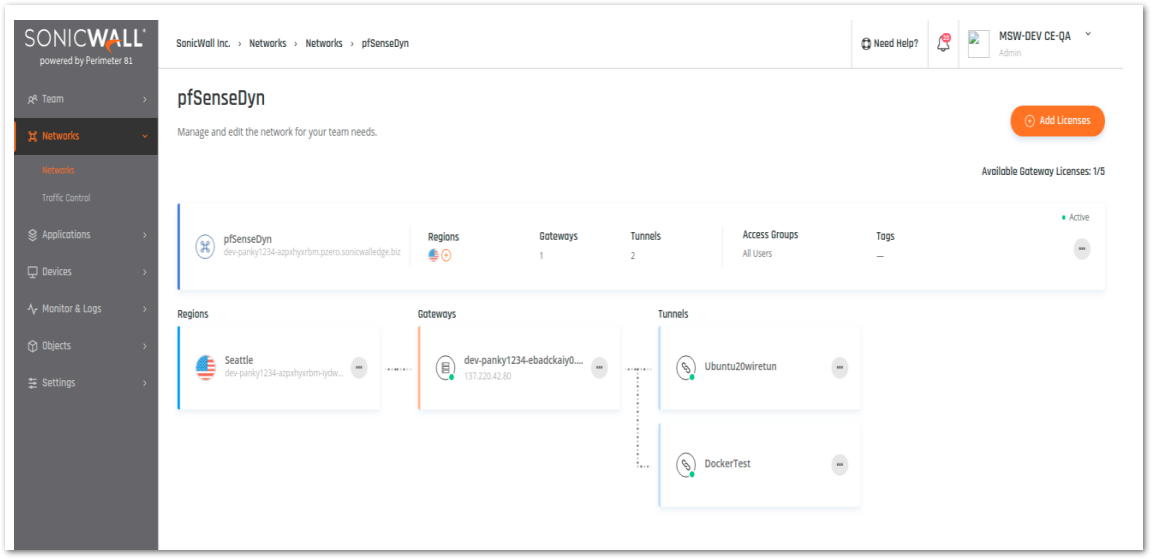
- We can verify the Wireguard tunnel status from the Cloud Edge
Troubleshooting:
- Connect to your Cloud Edge VPN agent or with the ZTNA application(s) (you can do it on any machine).
- Open the terminal and run the following command:
ping XXX.XXX.XXX.XXX - internal resource! - If the ping command fails, please make sure that port UDP/8000 is not blocked in your docker container, and that you went through all the steps.
- Make sure the received bytes field fluctuates and increases. Wireguard will only communicate to an authenticated neighbor
- Ping the other side of the tunnel interface, if that works, its most likely your local firewall settings on the docker container
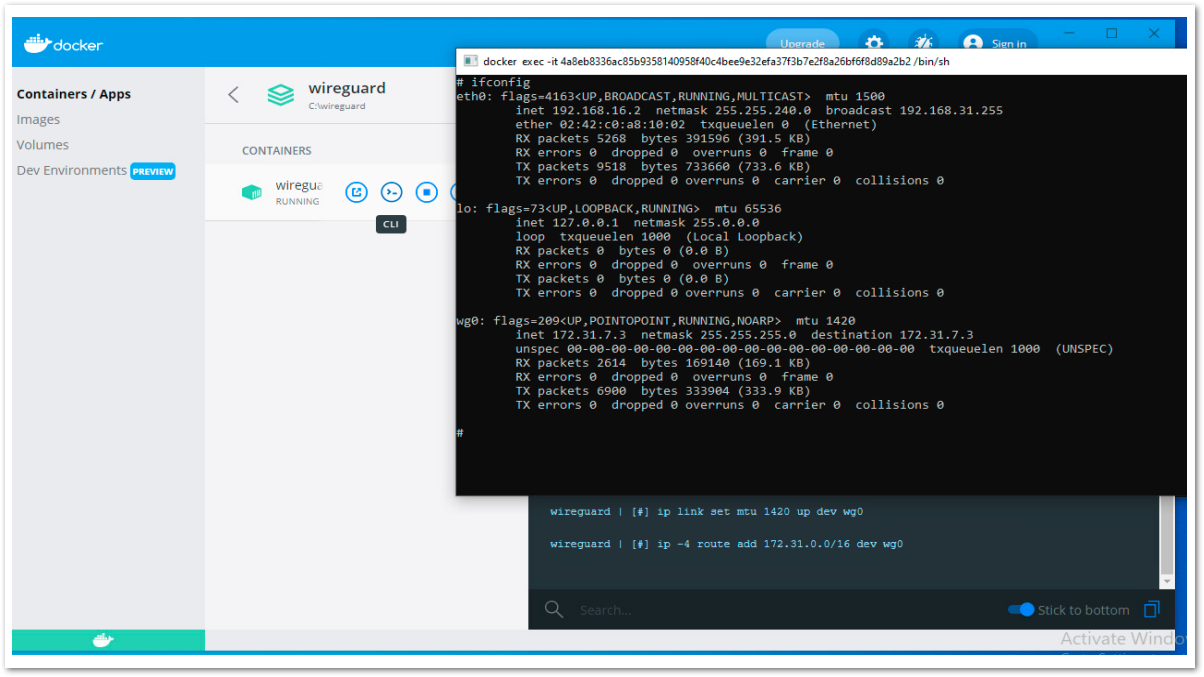
- You can edit the WireGuard network settings (endpoint and subnet) later for restrict the specific network subnet or resources from your docker container. You can find the subnet/network details of the docker container by going to CLI.
Related Articles
- Converting Cloud App Security licenses from annual to monthly
- Cloud Application Security FAQs
- Cloud Edge License Provisioning and Management through MSSP Monthly






 YES
YES NO
NO