-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I send Syslogs to a Analyzer server through a Site to Site VPN Tunnel?



Description
Analyzer: How to Send Syslogs to a Analyzer Server through a Site to Site VPN Tunnel (5.9 & above).
Sending Syslogs to a Analyzer Server through Site to Site VPN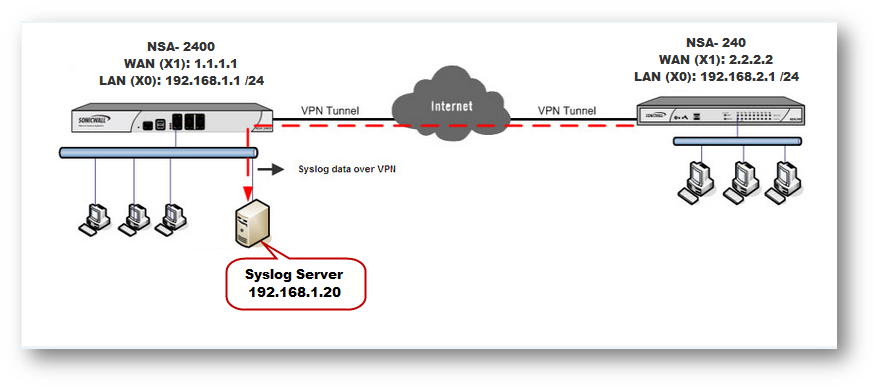
NSA 2400
LAN Interface (X0): 192.168.1.1 Mask: 255.255.255.0
Analyzer Server IP Address: 192.168.1.20
NSA 240
LAN Interface (X0):192.168.2.1 Mask: 255.255.255.0
Scenario:
In this scenario we will add two units in the Analyzer server.
- A local SonicWall NSA 2400 UTM device.
- A remote SonicWall NSA 240 UTM device connected over a site to site VPN between the NSA 240 and NSA 2400.
Requirements:
Before beginning the configuration, ensure the following are in place:
- Thesite to site VPN tunnel is upand you are able to reach the analyzer server from NSA 240 device.
- Both of the units are licensed for analyzer
- HTTPand / or HTTPS Management is enabled on the LAN interface of NSA 2400 device
- HTTP and / or HTTPS Management is enabled on the VPN policy
Resolution
NSA 2400 configuration
- Navigate to Network | Address Objects, Click on Custom Address objects radio button at top of the screen in View Style.
- Click on Add button under Address Objects, to get Add Address Object Window. Create address object for Syslog server IP address as below
Name: Syslog Server Any Friendly Name you would like to give)
Zone : LAN
Type : Host
IP Address: 192.168.1.20 (IP Address of Syslog Server)
Click Add button after typing the information to create object.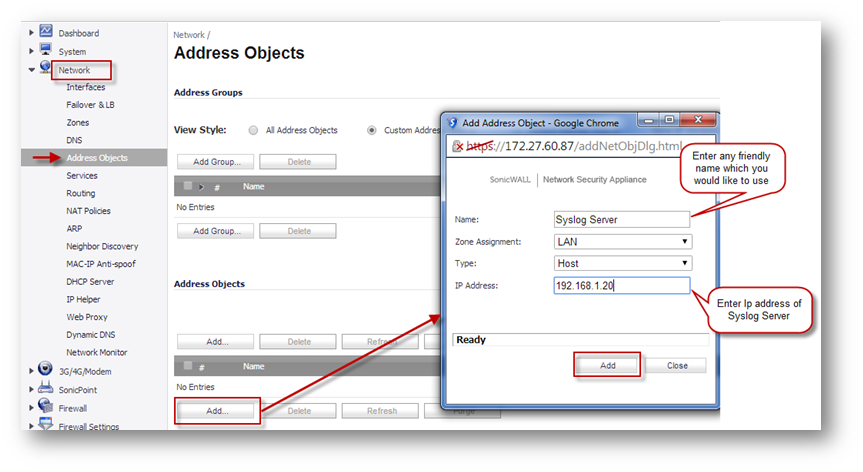
- Navigate to Logs | Syslog page.
- Click on Add under syslog server and enter the following information.
Name or IP address: Select Syslog server from drop down list (Address Object which is created for syslog server)
Port: 514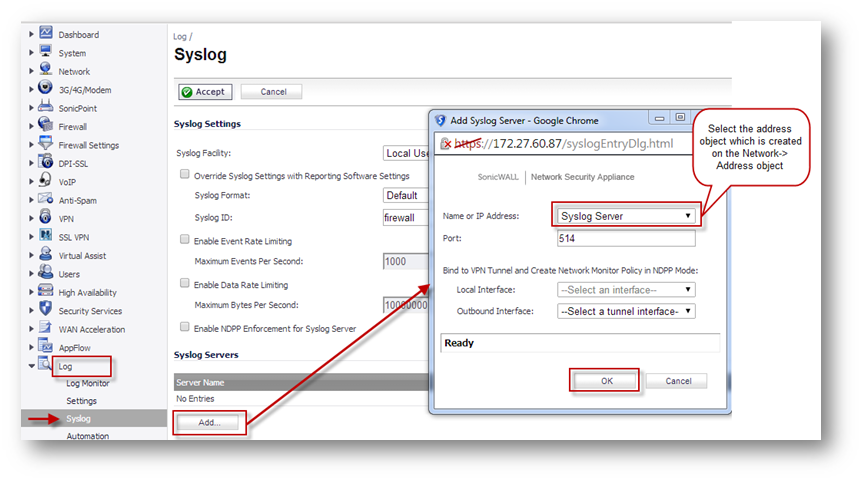
- Navigate to the Log-|Settings.
- Select the Logging level to Inform (recommended) or Debug from the drop down list.
- In order to send syslogs for all the categories, change this syslog option to full green.
- To send syslogs for specific categories, manually enable the syslog logging.

- Then click on Apply to save these settings.
NSA 240 configuration
- Login to the SonicWall management GUI.
- Navigate to the VPN | Settings page.
- Click the Configure button to edit the VPN Policy already created.
- In the Advanced tab of the VPN Policy window, enable HTTP and / or HTTPS under Management via this SA.
- Click on OK to save.
 NOTE: This may re-negotiate the tunnel.
NOTE: This may re-negotiate the tunnel.
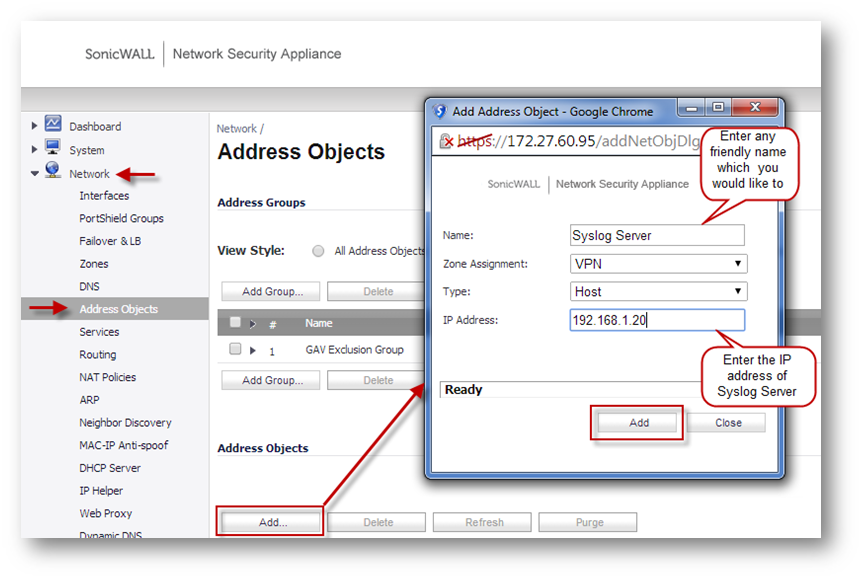
- Navigate to Network | Address Objects, Click on Custom Address objects radio button at top of the screen in View Style.
- Click on Add button under Address Objects, to get Add Address Object Window. Create address object for Syslog server IP address as below.
Name: Syslog Server (Any Friendly Name you would like to give)
Zone: VPN
Type: Host
IP Address : 192.168.1.20 (IP Address of Syslog Server Which is on remote Site) - Click Add button after typing the information to create object.

- Navigate to Logs | Syslog page.
- Click on Add under syslog server and enter the following information.
Name or IP address: Select Syslog server from drop down list (Address Object Which is created for syslog server)
Port: 514
Local interface: X0
Outbound Interface: Select the Site to Site VPN tunnel name
Analyzer Configuration:
- Login to the Analyzer server and add the NSA 2400 and NSA 240 units as under:
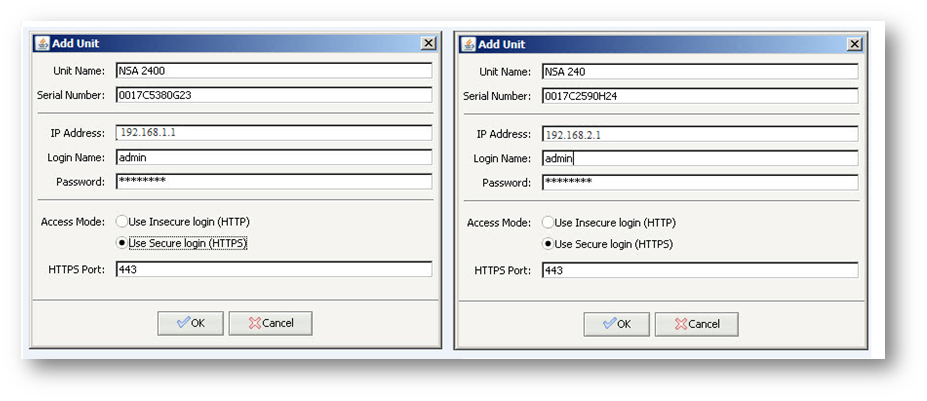
Troubleshooting:
- Do a packet capture on each SonicWall with the destination IP address as 192.168.1.20 and the destination port as 514. If able to see outgoing traffic, then the units are configured properly.
- If unable to see outgoing Syslog traffic, check the following:
- In the Log | Syslog page of both the devices, check whether the Server IP is correct. Make sure Server port is 514.
- In the the Log | Settings page of each unit, make sure the Logging Level is set to Inform (recommended) or Debug. Make sure all necessary Syslogs categories are checked.
- Make sure HTTP / HTTPS Management is enabled on the LAN interface of each unit.
- In the NSA 240 make sure HTTP / HTTPS is checked under Management via this SA in the Advanced tab of the VPN Policy.
- Make sure there are no Access Rules or Security Services blocking UDP port 514.
If able to see outgoing Syslog traffic in the UTM devices but the Analyzer server is not able to synchronize with the units or create reports, check the following:
- Make sure there are no intermediate devices between the SonicWalls and the Analyzer server blocking traffic.
- Make sure the units added under Analyzer have the correct Serial Number, IP Address, Login Name, Password and HTTPS Port number.
- Disable (or add appropriate exception in) Windows Firewall or any other security application which could possibly block Syslog traffic
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > VPN
- Firewalls > SonicWall NSA Series > VPN
- Firewalls > TZ Series > VPN
- Management and Reporting > Analyzer > Syslog






 YES
YES NO
NO