-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I enable client Certificate check for HTTPS management on the SonicWall?



Description
To further secure the HTTPS access of the SonicWall management GUI, in addition to the username/password authentication, system administrators can enable Client Certificate Check.
The SonicWall Client Certificate Check was developed for use with a Common Access Card (CAC). However, it can be used to enforce a client certificate on any HTTPS management request. The difference being, with a CAC the client certificate is automatically installed on the browser and without a CAC the client certificate must be manually imported into the browser.
This article describes how to enable Client Certificate Check in the SonicWall and how to import a client certificate into the web browser.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
SonicWall configuration
- Login to the SonicWall management GUI.
- Navigate to Manage | Appliance | Certificates.
- Import the certificate to be used for management.
- Navigate to Manage | Appliance | Base Settings page.
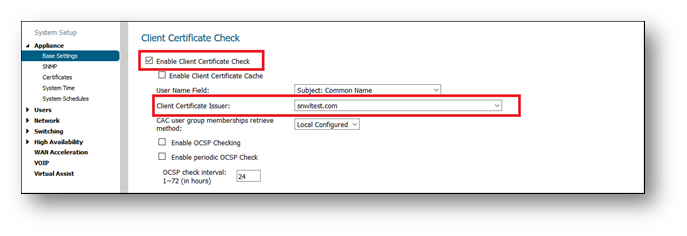
- Under Web Management settings, enable check box Enable Client Certificate check.
- The Client Certificate Issuer drop-down menu contains a list of the Certification Authority (CA) certificates that are available in the SonicWall certificate store. If the appropriate CA is not in the list, you need to import that CA into the SonicWall security appliance.\
- Enabling the Enable OCSP Checking check box enables Online Certificate Status Protocol (OCSP) to verify that the client certificate is still valid and has not been revoked.
- The OCSP Responder URL field is optional; only to be filled-in if an OCSP URL is not embedded within the certificate.
- Click Accept.
- The following screenshots show an internal CA certificate being imported before setting that certificate as Client Certificate Issuer for client certificate check.
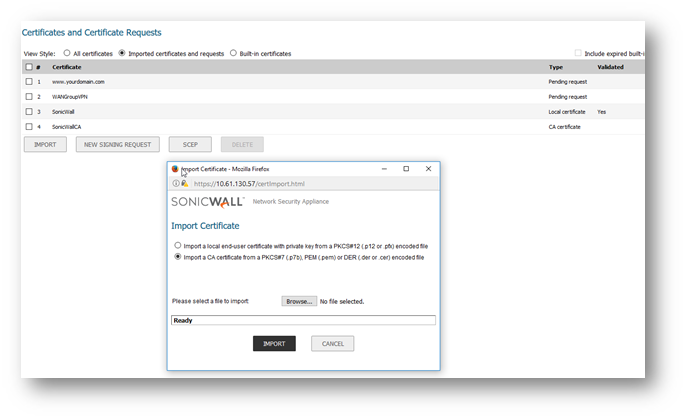
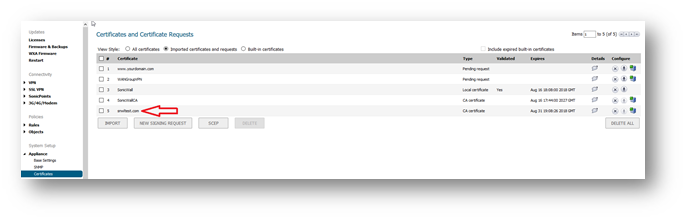
- When a web browser tries to access the SonicWall HTTPS management without an appropriate certificate, the SonicWall security appliance checks the Client Certificate Issuer to verify that the client certificate is signed by the CA. If a match is not found, the SonicWall refuses the connection and the browser displays a standard page cannot be displayed message.
 CAUTION: When using the client certificate feature, these situations can lock the user out of the SonicWall security appliance.
CAUTION: When using the client certificate feature, these situations can lock the user out of the SonicWall security appliance.
- Enable Client Certificate Check is checked, but no client certificate is installed on the browser.
- Enable Client Certificate Check is checked and a client certificate is installed on the browser, but either no Client Certificate Issuer is selected or the wrong Client Certificate Issuer is selected.
- Enable OCSP Checking is enabled, but either the OCSP server is not available or a network problem is preventing the SonicWall security appliance from accessing the OCSP server.
The following CLI commands restore access to a user who is locked out. These commands must be issued within the configuration mode and after logging into the CLI.
> administration //enter the administration console
> no web-management client-certificate-check // disable client certificate check
> commit //apply changes > exit
If the problem is due to OCSP then issue the following commands to disable OCSP checking alone, without disabling client certificate check. If client certificate check is disabled, the option to enable or disable OCSP is not available to the user.
> no web-management ocsp-check // disable OCSP checking
> commit //apply changes > exit
Import client certificate into a web browser
The following points must be kept in mind before importing the client certificate into a browser.
- The certificate must be signed by the same CA selected for client certificate checking in the SonicWall Administration page.
- The certificated must be in a container along with its private key, and optionally the CA certificate. For example, .p12 or .pfx extensions.
- If the CA certificate is not part of the container then it must be separately imported.
The following screenshots show a certificate with .pfx extension and its CA certificate being imported into the Firefox browser: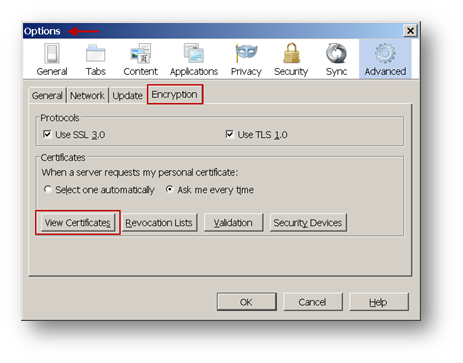
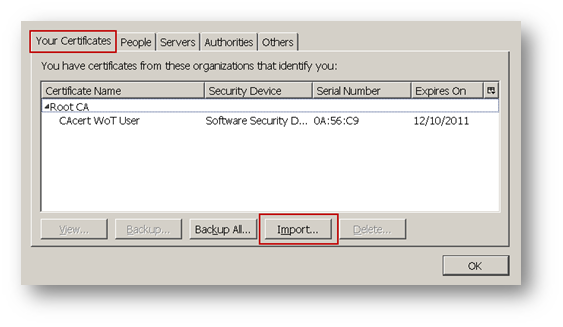
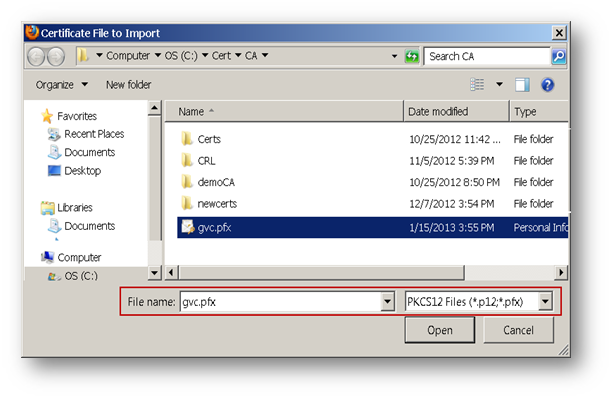
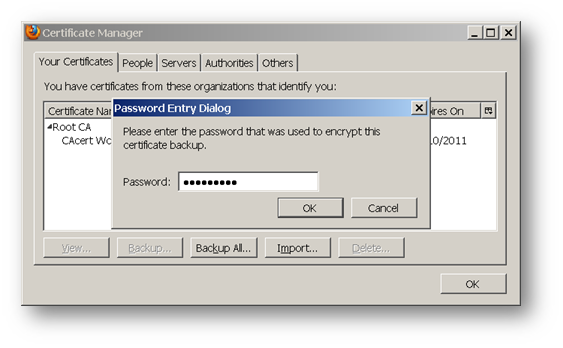
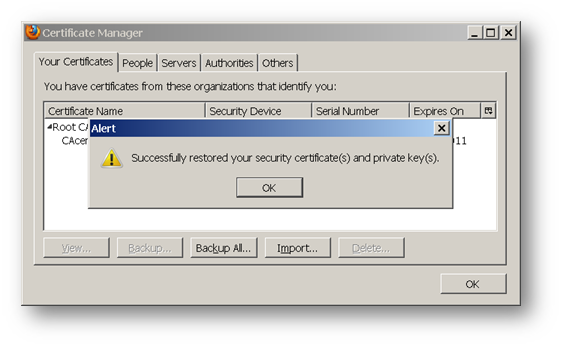
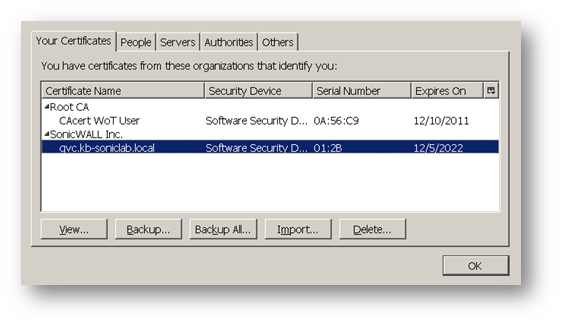
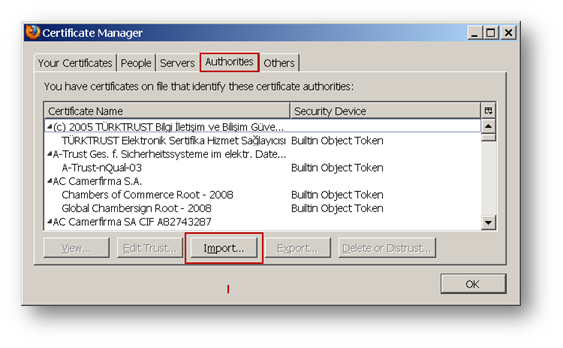
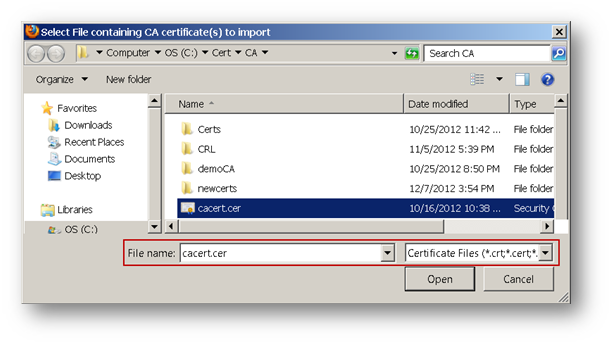
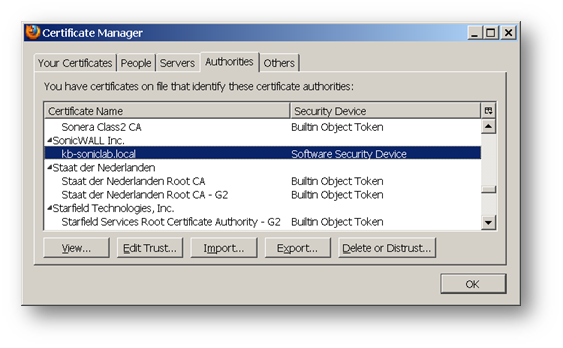
Log into the SonicWall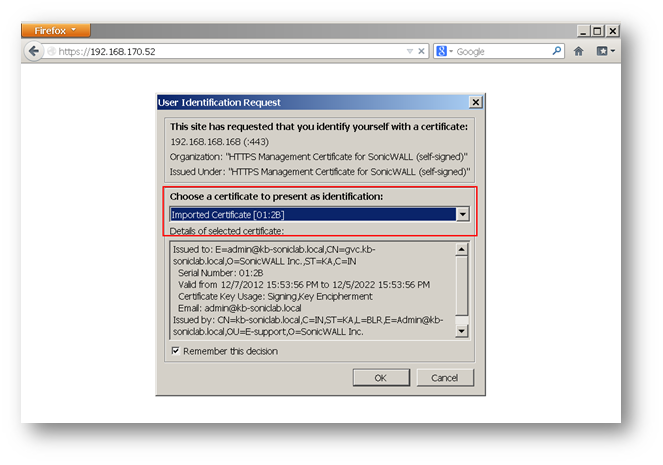

Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
SonicWall configuration
- Login to the SonicWall management GUI.
- Navigate to the System | Administration page.
- Under Web Management settings, enable check box Enable Client Certificate Check.
- The Client Certificate Issuer drop-down menu contains a list of the Certification Authority (CA) certificates that are available in the SonicWall certificate store. If the appropriate CA is not in the list, you need to import that CA into the SonicWall security appliance.
- Enabling the Enable OCSP Checking check box enables Online Certificate Status Protocol (OCSP) to verify that the client certificate is still valid and has not been revoked.
- The OCSP Responder URL field is optional; only to be filled-in if an OCSP URL is not embedded within the certificate.
- Click Accept.
- The following screenshots show an internal CA certificate being imported before setting that certificate as Client Certificate Issuer for client certificate check.


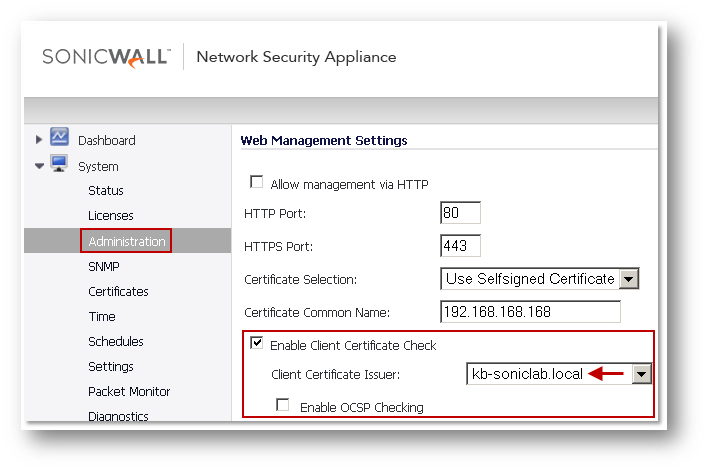
- When a web browser tries to access the SonicWall HTTPS management without an appropriate certificate, the SonicWall security appliance checks the Client Certificate Issuer to verify that the client certificate is signed by the CA. If a match is not found, the SonicWall refuses the connection and the browser displays a standard page cannot be displayed message.
 CAUTION: When using the client certificate feature, these situations can lock the user out of the SonicWall security appliance.
CAUTION: When using the client certificate feature, these situations can lock the user out of the SonicWall security appliance.
- Enable Client Certificate Check is checked, but no client certificate is installed on the browser.
- Enable Client Certificate Check is checked and a client certificate is installed on the browser, but either no Client Certificate Issuer is selected or the wrong Client Certificate Issuer is selected.
- Enable OCSP Checking is enabled, but either the OCSP server is not available or a network problem is preventing the SonicWall security appliance from accessing the OCSP server.
The following CLI commands restore access to a user who is locked out. These commands must be issued within the configuration mode and after logging into the CLI.
> administration //enter the administration console
> no web-management client-certificate-check // disable client certificate check
> commit //apply changes > exit
If the problem is due to OCSP then issue the following commands to disable OCSP checking alone, without disabling client certificate check. If client certificate check is disabled, the option to enable or disable OCSP is not available to the user.
> no web-management ocsp-check // disable OCSP checking
> commit //apply changes > exit
Import client certificate into a web browser
The following points must be kept in mind before importing the client certificate into a browser.
- The certificate must be signed by the same CA selected for client certificate checking in the SonicWall Administration page.
- The certificated must be in a container along with its private key, and optionally the CA certificate. For example, .p12 or .pfx extensions.
- If the CA certificate is not part of the container then it must be separately imported.
The following screenshots show a certificate with .pfx extension and its CA certificate being imported into the Firefox browser:








Log into the SonicWall
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Firewall Management
- Firewalls > TZ Series > Firewall Management UI
- Firewalls > NSa Series > Command Line Interface
- Firewalls > TZ Series > Command Line Interface - CLI






 YES
YES NO
NO