-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I configure the SonicWall to mitigate DDoS attacks?



Description
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. There are three types of DDoS attacks. Layer 3,Layer 4 DDoS attacks and Layer 7 DDoS attack.
Layer 3 / 4 DDoS attacks
The majority of DDoS attacks focus on targeting the Transport and Network Layers of the OSI Model. These types of attacks are usually comprised of volumetric floods that aim to overwhelm the target devices, denying or consuming resources until they're unreachable. In these types of DDoS attacks, malicious traffic (TCP / UDP) is used to flood the victim.
Layer 7 DDoS attacks
Application-layer DDoS attacks are some of the most difficult attacks to mitigate against because they mimic human behavior as they interact with the user interface. A sophisticated Layer 7 DDoS attack may target specific areas of a website, making it even more difficult to separate from normal traffic.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
 CAUTION: Please be aware that mitigating DDoS Attacks at the Firewall level is far less effective than at the ISP level. Once packets have made it to the Firewall, typically the network edge device, they're going to overwhelm your network such that it will be hard for traffic to get in or out. Mitigating DDoS at the firewall level will allow you to preserve and protect internal resources so that internal users may still be able to function and sensitive information isn't compromised.
CAUTION: Please be aware that mitigating DDoS Attacks at the Firewall level is far less effective than at the ISP level. Once packets have made it to the Firewall, typically the network edge device, they're going to overwhelm your network such that it will be hard for traffic to get in or out. Mitigating DDoS at the firewall level will allow you to preserve and protect internal resources so that internal users may still be able to function and sensitive information isn't compromised.
DDoS Protection Checklist
In order to help harden your network against DDoS Attacks at the firewall level, please follow the below steps. These are presented in no particular order.
Enable Intrusion Prevention
- Click on POLICY, Navigate to Security Services | Intrusion Prevention. Ensure that your settings mirror the screenshot below.
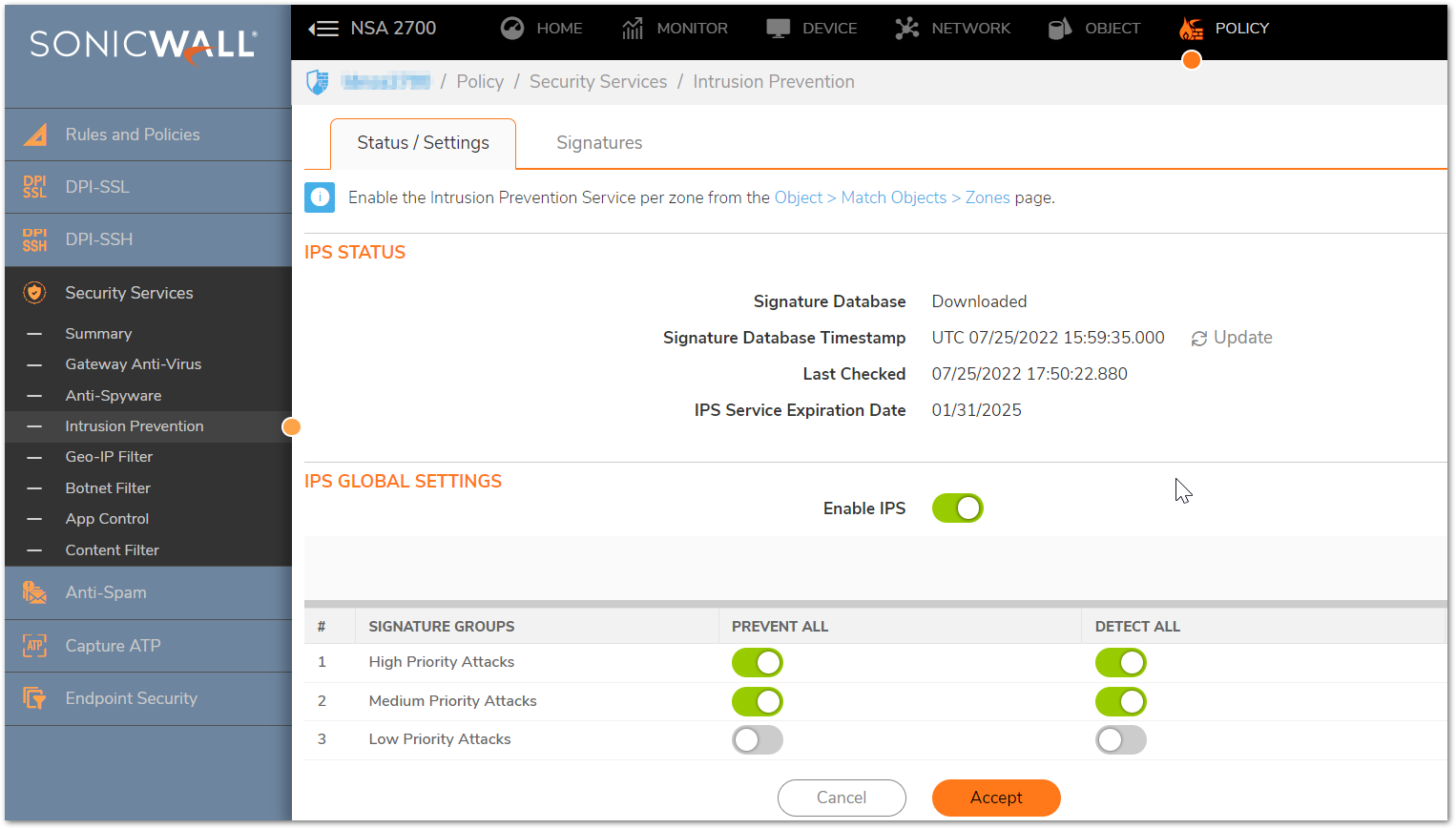
 NOTE: To enforce SonicWall IPS not only between each Network Zone and the WAN, but also between internal zones, you should also apply SonicWall IPS to zones on the OBJECT | Match Object | Zones Page .
NOTE: To enforce SonicWall IPS not only between each Network Zone and the WAN, but also between internal zones, you should also apply SonicWall IPS to zones on the OBJECT | Match Object | Zones Page .
Block unused Ports from the WAN to the Internal Network
- Navigate to POLICY | Rules and Policies > Access Rules
- Check the WAN to LAN, WAN to DMZ, WAN to WLAN, and WAN to any Custom Zones access rules.
- Ensure that any Allow rules are specified by Service (Port) as well as Source IP if possible.
Enable Flood Protection
- Navigate to NETWORK | Firewall > Flood Protection
- Enable UDP Flood Protection and ICMP Flood Protection.
- Set TCP Flood Protection to Proxy WAN Client Connections when attack is suspected. This option will be available under Layer 3 SYN Flood Protection - SYN Proxy tab
 CAUTION: Proxy WAN Connections will cause External Users who trigger the Flood Protection feature to be blocked from connecting to internal resources. If there is a chance any Users can generate a false positive for this feature it is recommended to leave TCP Flood Protection in Watch and Report mode.
CAUTION: Proxy WAN Connections will cause External Users who trigger the Flood Protection feature to be blocked from connecting to internal resources. If there is a chance any Users can generate a false positive for this feature it is recommended to leave TCP Flood Protection in Watch and Report mode. 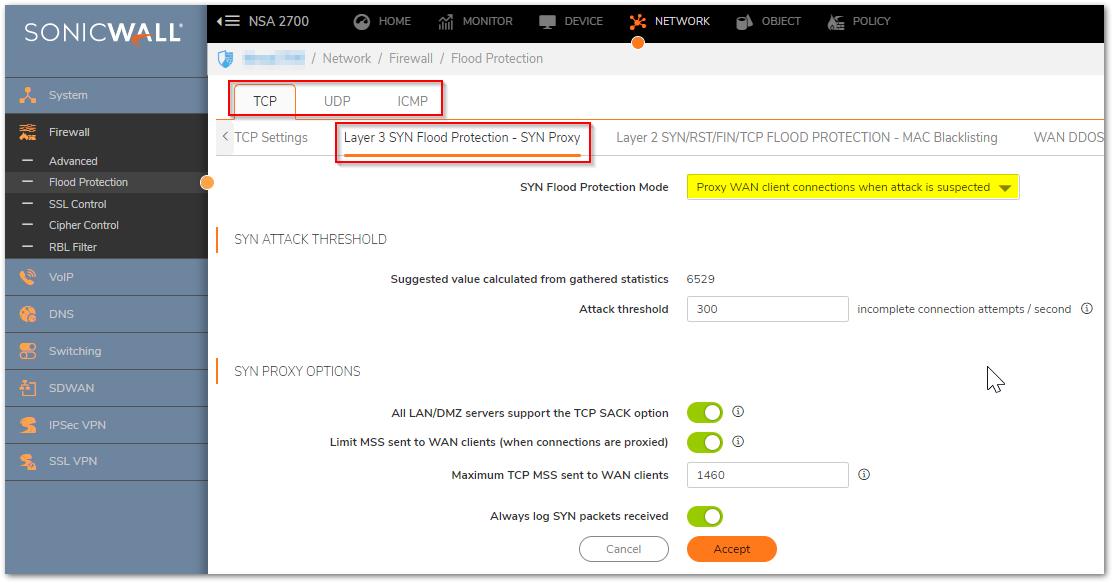
Enable Geo-IP Filter and Botnet Filter
Many DDoS attacks occur when infected machines under the control of a few individuals are all directed at one target. Often these attacks come from certain Countries and do not have their IP Addresses obfuscated. By using the Geo-IP Filter and Botnet Filter on the SonicWall it is possible to drop these packets as they attempt to enter your network which can aid the SonicWall in keeping your network reachable.
- Navigate to POLICY | Security Services > Geo-IP Filter
- In the Settings Tab, Enable Block connections to/from countries selected in the Countries tab.
- Select the countries you'd like to block from the table provided under the Countries - Allowed Countries tab, you can Drag and Drop the Countries name to move them under the Blocked Countries.
- Click Accept at the bottom.
 CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure SonicWall Geo-IP Filter using Firewall Access Rules.
CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure SonicWall Geo-IP Filter using Firewall Access Rules. 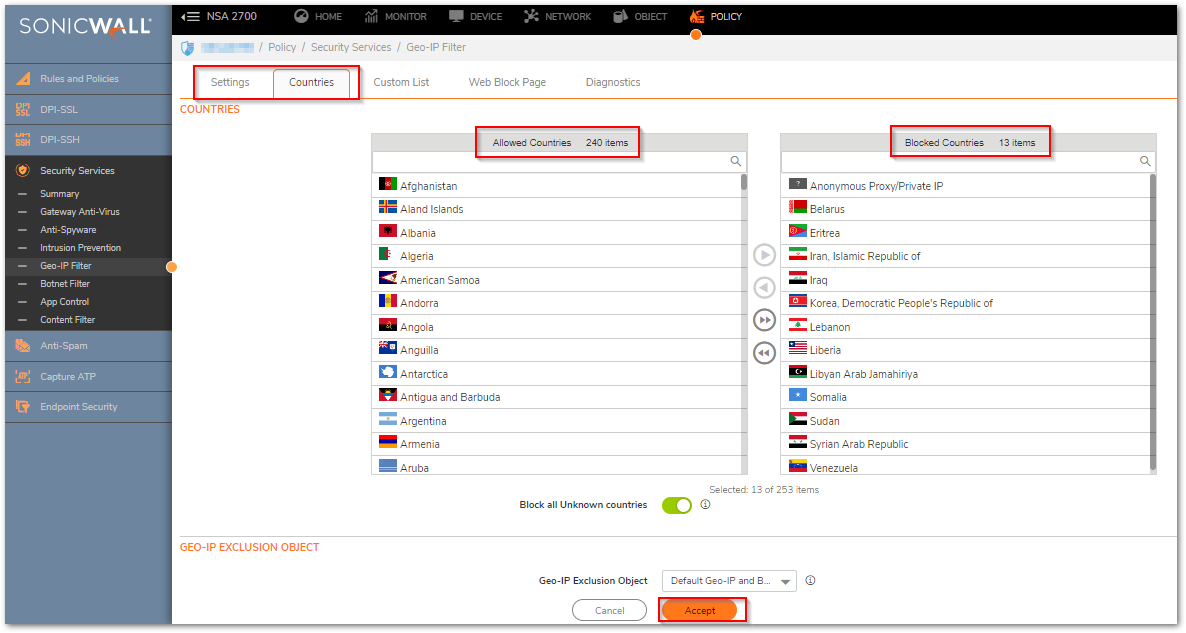
 NOTE: Botnet IP addresses are maintained by SonicWall for internal use. If you'd like to test a Domain/IP for possibly being flagged as a Botnet, navigate to POLICY | Security Services | Botnet Filter | Diagnostics and enter the desired IP Address in the Lookup IP Tool.
NOTE: Botnet IP addresses are maintained by SonicWall for internal use. If you'd like to test a Domain/IP for possibly being flagged as a Botnet, navigate to POLICY | Security Services | Botnet Filter | Diagnostics and enter the desired IP Address in the Lookup IP Tool.
 CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country.
CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country.
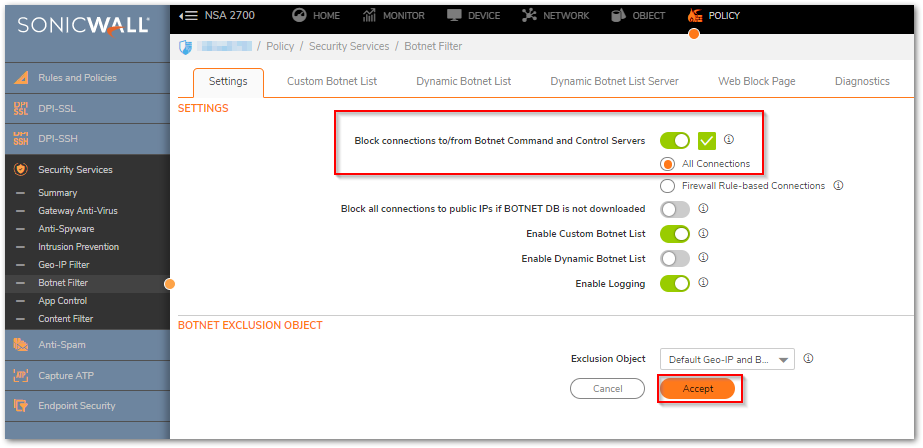
- Navigate to POLICY | Security Services | Botnet Filter
- In the Settings tab, Enable Block connections to/from Botnet Command and Control Servers
- Click on Accept
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
CAUTION: Please be aware that mitigating DDoS Attacks at the Firewall level is far less effective than at the ISP level. Once packets have made it to the Firewall, typically the network edge device, they're going to overwhelm your network such that it will be hard for traffic to get in or out. Mitigating DDoS at the firewall level will allow you to preserve and protect internal resources so that internal users may still be able to function and sensitive information isn't compromised.
DDoS Protection Checklist
In order to help harden your network against DDoS Attacks at the firewall level, please follow the below steps. These are presented in no particular order.
Enable Intrusion Prevention
- Click on MANAGE , navigate to Security Services | IPS. Ensure that your settings mirror the screenshot below.
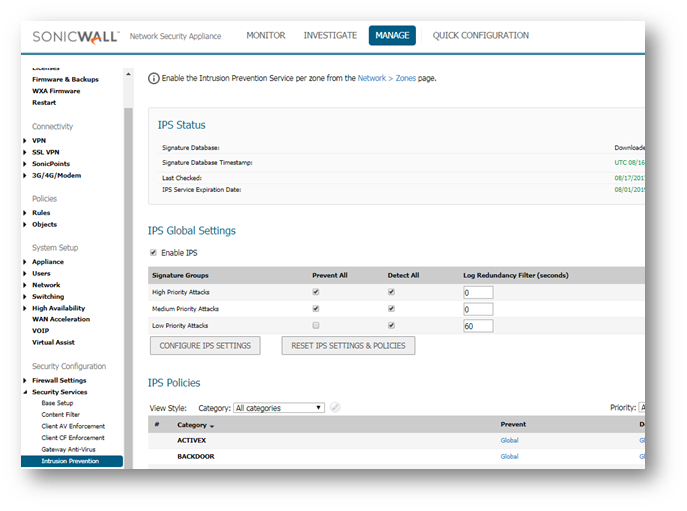
 NOTE: To enforce SonicWall IPS not only between each Network Zone and the WAN, but also between internal zones, you should also apply SonicWall IPS to zones on the Network | Zones Page .
NOTE: To enforce SonicWall IPS not only between each Network Zone and the WAN, but also between internal zones, you should also apply SonicWall IPS to zones on the Network | Zones Page .
Block unused Ports from the WAN to the Internal Network
- Navigate to Rules | Access Rules.
- Check the WAN to LAN, WAN to DMZ, WAN to WLAN, and WAN to any Custom Zones access rules.
- Ensure that any Allow rules are specified by Service (Port) as well as Source IP if possible.
Enable Flood Protection
- Navigate to Firewall Settings | Flood Protection.
- Enable UDP Flood Protection and ICMP Flood Protection.
- Set TCP Flood Protection to Proxy WAN Client Connections when attack is suspected.
 CAUTION: Proxy WAN Connections will cause External Users who trigger the Flood Protection feature to be blocked from connecting to internal resources. If there is a chance any Users can generate a false positive for this feature it is recommended to leave TCP Flood Protection in Watch and Report mode.
CAUTION: Proxy WAN Connections will cause External Users who trigger the Flood Protection feature to be blocked from connecting to internal resources. If there is a chance any Users can generate a false positive for this feature it is recommended to leave TCP Flood Protection in Watch and Report mode.
Enable Geo-IP Filter and Botnet Filter
Many DDoS attacks occur when infected machines under the control of a few individuals are all directed at one target. Often these attacks come from certain Countries and do not have their IP Addresses obfuscated. By using the Geo-IP Filter and Botnet Filter on the SonicWall it is possible to drop these packets as they attempt to enter your network which can aid the SonicWall in keeping your network reachable.
- Navigate to Security Services | Geo-IP Filter.
- Enable both Block connections to/from countries selected in the Countries tab.
- Select the countries you'd like to block from the table provided under the Countries tab, you can Drag and Drop the Countries name to move them under the Selected Country List.
- Click Accept at the bottom.
 CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to set up Geo-IP Filter for a more granular block please reference How to configure SonicWall Geo-IP Filter using Firewall Access Rules.
CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to set up Geo-IP Filter for a more granular block please reference How to configure SonicWall Geo-IP Filter using Firewall Access Rules.
 NOTE: Botnet IP addresses are maintained by SonicWall for internal use. If you'd like to test a Domain/IP for possibly being flagged as a Botnet, navigate to Security Services | Botnet Filter | Diagnostics and enter the desired IP Address in the Lookup IP Tool.
NOTE: Botnet IP addresses are maintained by SonicWall for internal use. If you'd like to test a Domain/IP for possibly being flagged as a Botnet, navigate to Security Services | Botnet Filter | Diagnostics and enter the desired IP Address in the Lookup IP Tool. CAUTION:This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure Botnet Filtering with Firewall Access Rules.
CAUTION:This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure Botnet Filtering with Firewall Access Rules. - Navigate to Security Services | Botnet Filter > Settings
- Enable Block connections to/from Botnet Command and Control Servers
- Click on Accept

Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
 CAUTION: Please be aware that mitigating DDoS Attacks at the Firewall level is far less effective than at the ISP level. Once packets have made it to the Firewall, typically the network edge device, they're going to overwhelm your network such that it will be hard for traffic to get in or out. Mitigating DDoS at the Firewall level will allow you to preserve and protect internal resources so that internal Users may still be able to function and sensitive information isn't compromised.
CAUTION: Please be aware that mitigating DDoS Attacks at the Firewall level is far less effective than at the ISP level. Once packets have made it to the Firewall, typically the network edge device, they're going to overwhelm your network such that it will be hard for traffic to get in or out. Mitigating DDoS at the Firewall level will allow you to preserve and protect internal resources so that internal Users may still be able to function and sensitive information isn't compromised.
DDoS Protection Checklist
In order to help harden your network against DDoS Attacks at the firewall level, please follow the below steps. These are presented in no particular order.
Enable Intrusion Prevention
- Navigate to Security Services | IPS. Ensure that your settings mirror the screenshot below.
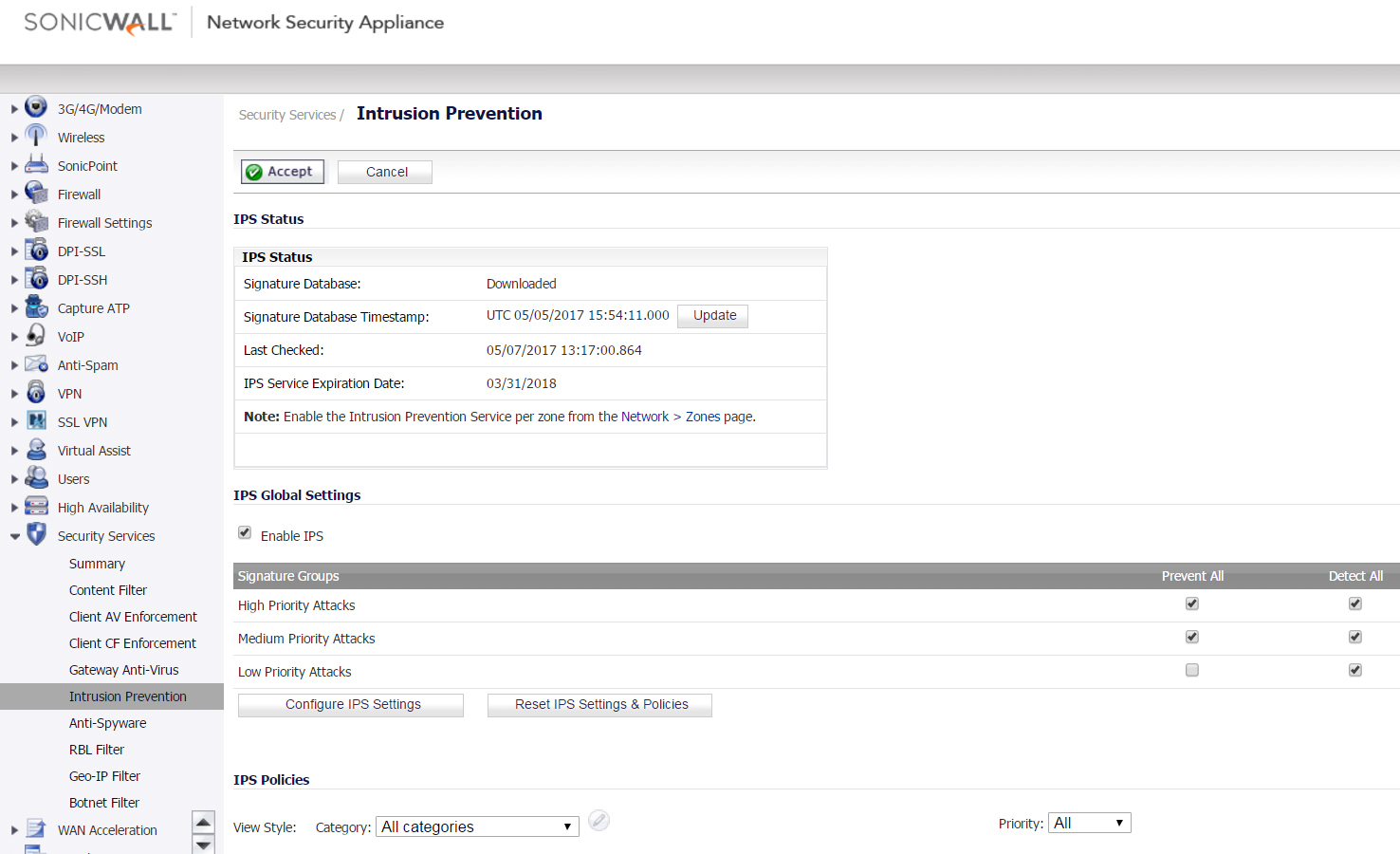
 NOTE: To enforce SonicWall IPS not only between each Network Zone and the WAN, but also between internal Zones, you should also apply SonicWall IPS to Zones on the Network | Zones Page .
NOTE: To enforce SonicWall IPS not only between each Network Zone and the WAN, but also between internal Zones, you should also apply SonicWall IPS to Zones on the Network | Zones Page .
Block unused Ports from the WAN to the Internal Network
- Navigate to Firewall | Access Rules.
- Check the WAN to LAN, WAN to DMZ, WAN to WLAN, and WAN to any Custom Zones access rules.
- Ensure that any Allow rules are specified by Service (Port) as well as Source IP if possible.
Enable Flood Protection
- Navigate to Firewall Settings | Flood Protection.
- Enable UDP Flood Protection and ICMP Flood Protection.
- Set TCP Flood Protection to Proxy WAN Client Connections when attack is suspected.
 CAUTION: Proxy WAN Connections will cause External Users who trigger the Flood Protection feature to be blocked from connecting to internal resources. If there is a chance any Users can generate a false positive for this feature it is recommended to leave TCP Flood Protection in Watch and Report mode.
CAUTION: Proxy WAN Connections will cause External Users who trigger the Flood Protection feature to be blocked from connecting to internal resources. If there is a chance any Users can generate a false positive for this feature it is recommended to leave TCP Flood Protection in Watch and Report mode.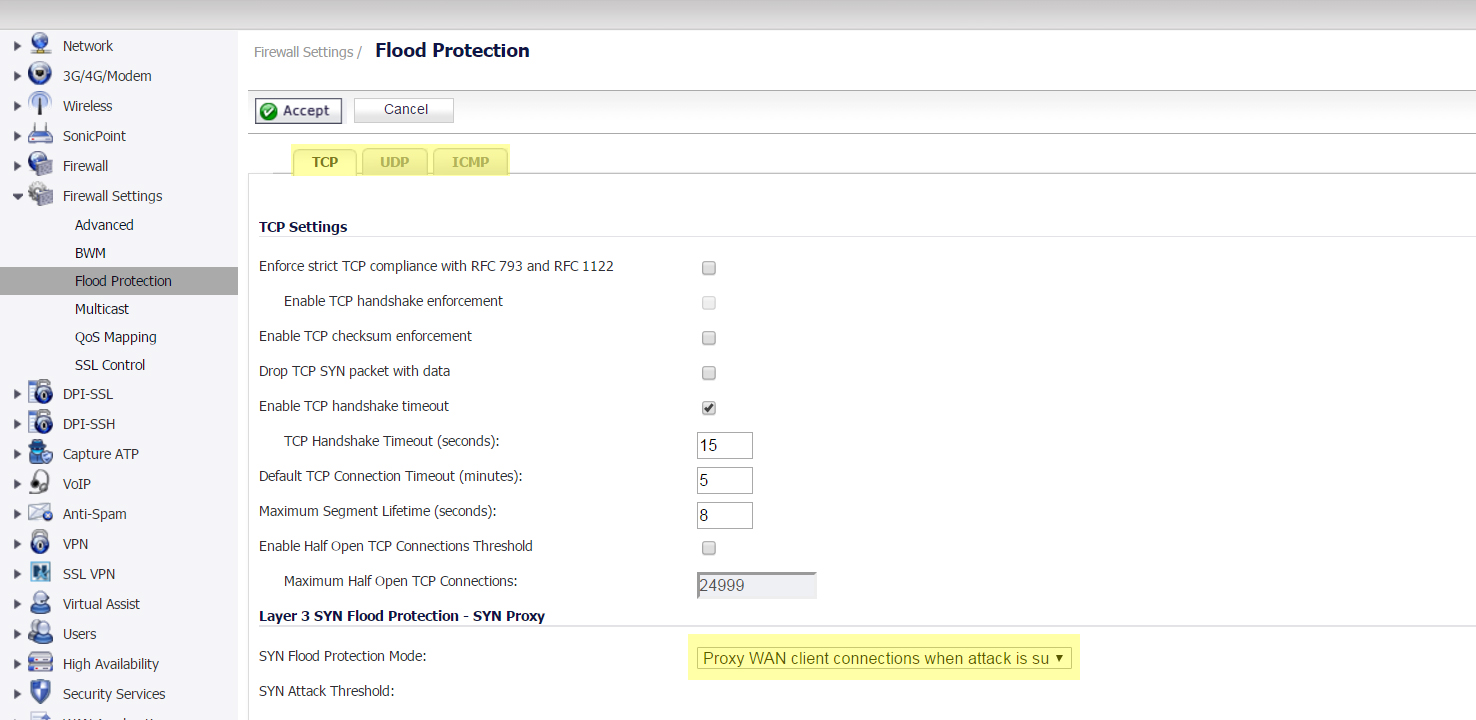
Enable Geo-IP Filter and Botnet Filter
Many DDoS attacks occur when infected machines under the control of a few individuals are all directed at one target. Often these attacks come from certain Countries and do not have their IP Addresses obfuscated. By using the Geo-IP Filter and Botnet Filter on the SonicWall it is possible to drop these packets as they attempt to enter your network which can aid the SonicWall in keeping your network reachable.
- Navigate to Security Services | Geo-IP Filter.
- Enable both Block connections to/from countries listed in the table below and Enable Logging.
- Select the countries you'd like to block from the table provided.
 CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure SonicWall Geo-IP Filter using Firewall Access Rules.
CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure SonicWall Geo-IP Filter using Firewall Access Rules.
- Navigate to Security Services | Botnet Filter.
- Enable both Block connections to/from Botnet Command and Control Servers and Enable Logging.
 NOTE: Botnet IP Addresses are maintained by SonicWall for internal use. If you'd like to test a Domain/IP for possibly being flagged as a Botnet, go to Security Services | Botnet Filter | Diagnostics and enter the desired IP address in the Lookup ID Tool.
NOTE: Botnet IP Addresses are maintained by SonicWall for internal use. If you'd like to test a Domain/IP for possibly being flagged as a Botnet, go to Security Services | Botnet Filter | Diagnostics and enter the desired IP address in the Lookup ID Tool. CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure Botnet Filtering with Firewall Access Rules.
CAUTION: This feature will block Outbound Connections to any device that has a Public IP Address associated with the selected country. If you'd like to setup Geo-IP Filter for a more granular block please reference How to configure Botnet Filtering with Firewall Access Rules.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Networking
- Firewalls > NSv Series > Networking
- Firewalls > TZ Series > Networking






 YES
YES NO
NO