-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I configure SSL VPN/NetExtender for clients with overlapping subnet?



Description
SSL VPN or NetExtender enables us to access the corporate SonicWall LAN subnets over the Internet with secure VPN tunnel. Sometimes the SonicWall LAN subnet and the client's IP on which the NetExtender is installed overlap and in such scenario accessing SonicWall LAN resources is not possible.
This article explains one of the ways to get over this problem. The solution includes configuring a virtual or dummy subnet with same subnet mask as that of SonicWall LAN subnet, which would do one to one mapping (NATing) of virtual IP addresses to the SonicWall LAN IP address.
 EXAMPLE: Let's consider the following IP scheme for the purpose of article.
EXAMPLE: Let's consider the following IP scheme for the purpose of article.
- SonicWall LAN subnet 192.168.1.0 mask 255.255.255.0.
- LAN subnet of the computer where NetExtender/Mobile connect is installed 192.168.1.0 mask 255.255.255.0.
- SSLVPN IP Pool used for NetExtender virtual adapter 10.1.1.0 mask 255.255.255.0
- Virtual or dummy subnet used to send traffic on 10.10.10.0 mask 255.255.255.0
 NOTE: Please refer the article How Do I Configure The SSL-VPN Feature For Use With NetExtender Or Mobile Connect? for SSL-VPN configuration.
NOTE: Please refer the article How Do I Configure The SSL-VPN Feature For Use With NetExtender Or Mobile Connect? for SSL-VPN configuration.
Cause
IP subnet overlap between SonicWall LAN and client computer IP scheme.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Creating address object for SSL VPN IP pool
The IP range used for SSLVPN IP Pool should not conflict with IP scheme present on either SonicWall or client side. The subnet used here is 10.1.1.0/24.
- Login to the SonicWall UTM appliance.
- Navigate to OBJECT| Match Objects | Addresses. Click Add to create an address object for SSL VPN IP Pool.
- Name: SSLVPN Ip Pool (Any Friendly Name as you wish but need to select that while configuring SSLVPN )
- Zone: SSLVPN
- Type: Network
- Network: 10.1.1.0
- Netmask/Prefix Length: 255.255.255.0
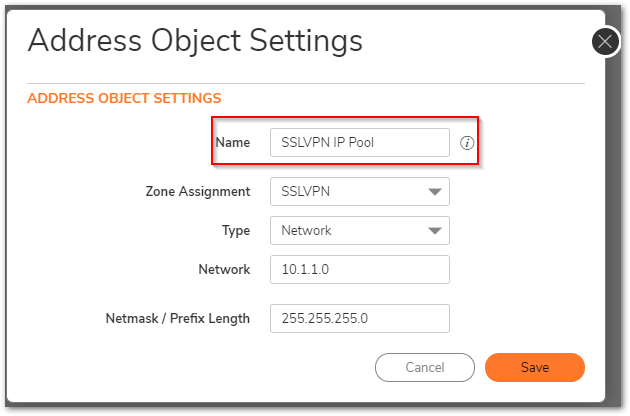
Specify the address object in SSLVPN client setting as follows
- Navigate to NETWORK | SSL VPN | Client setting, click Edit.
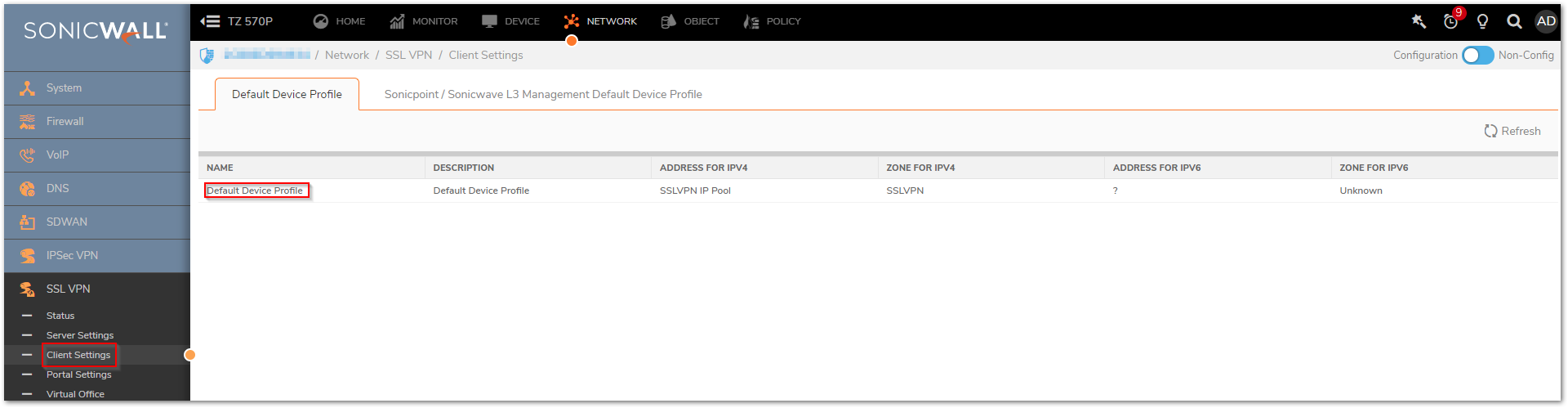
- Specify the address object in the Network Address IPv4 option on the Setting tab.
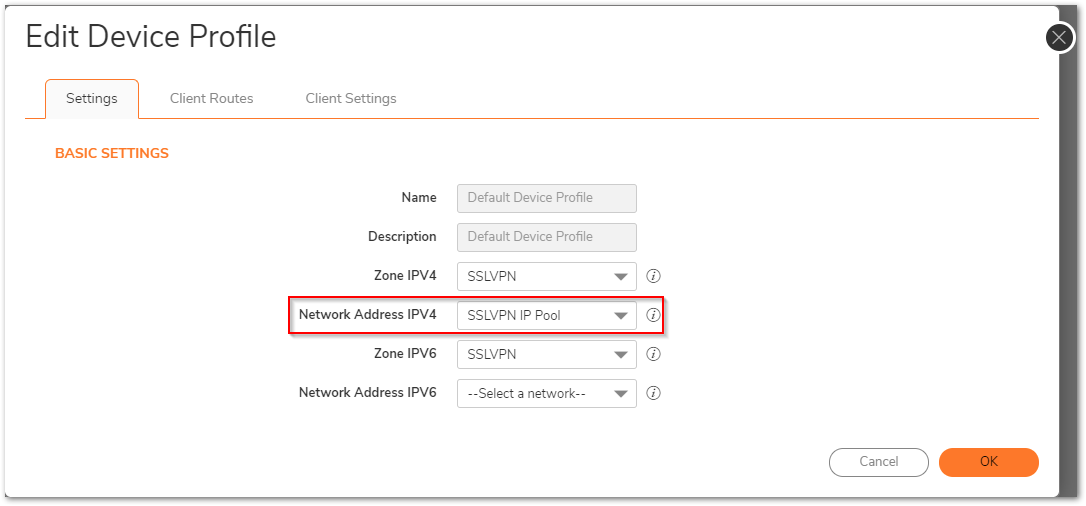
- Create Virtual LAN Subnet address object with zone being LAN.
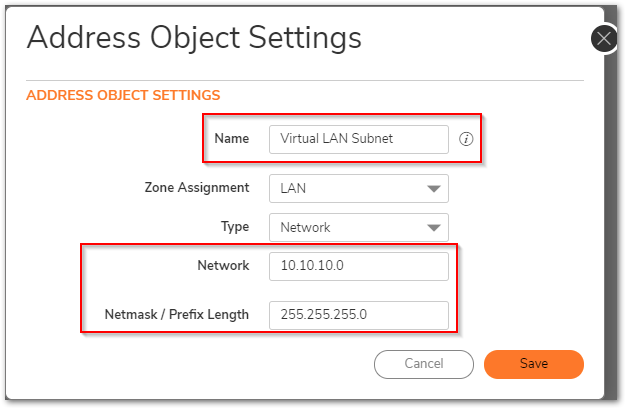
- Specify Virtual LAN Subnet address object in the SSL VPN Client routes
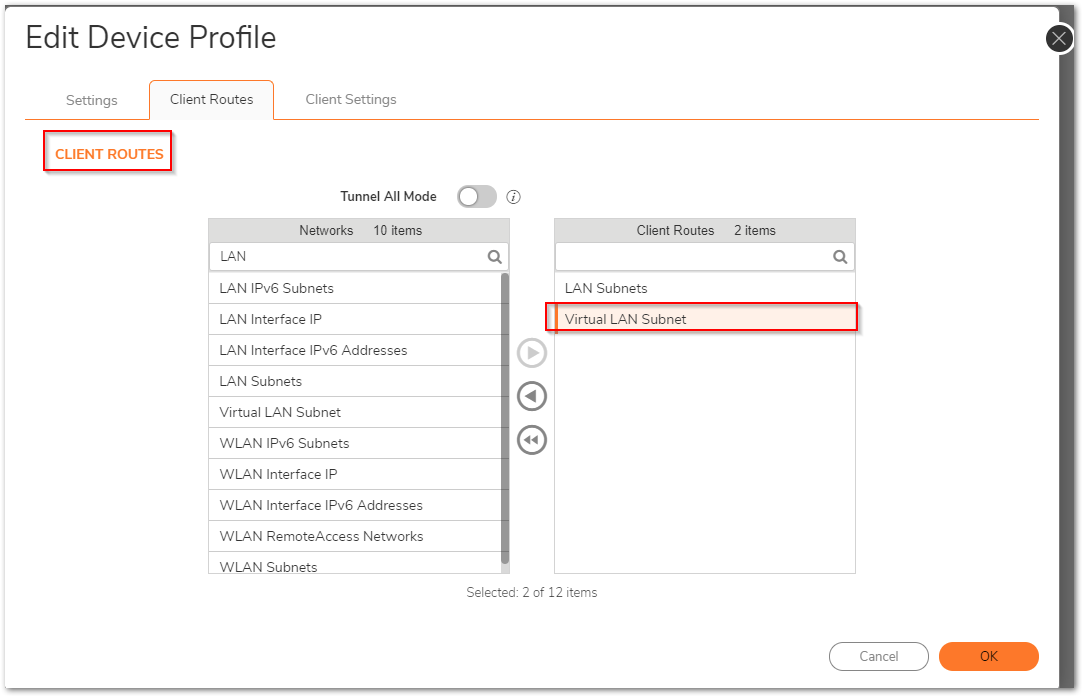
Add the Virtual LAN Subnet address object in VPN access of SSLVPN Services Local group.
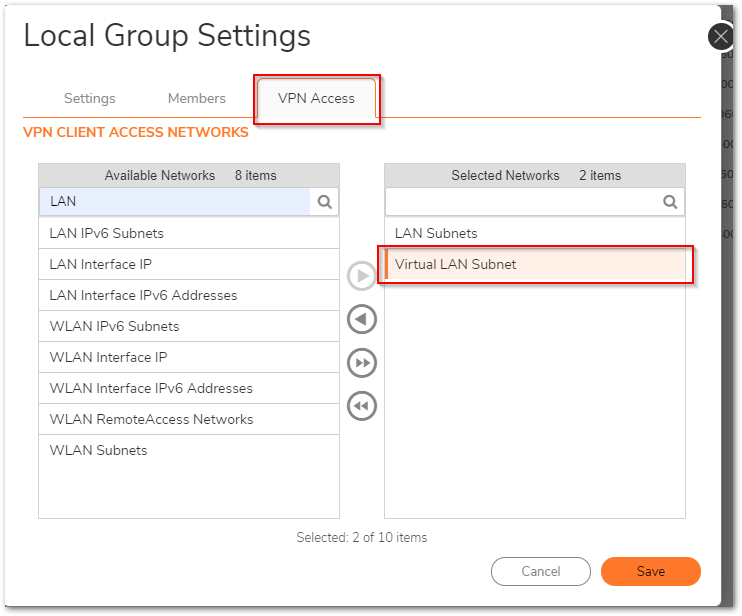
- Navigate to DEVICE | Users| Local groups| SSLVPN services and the address object in the VPN access of this group.
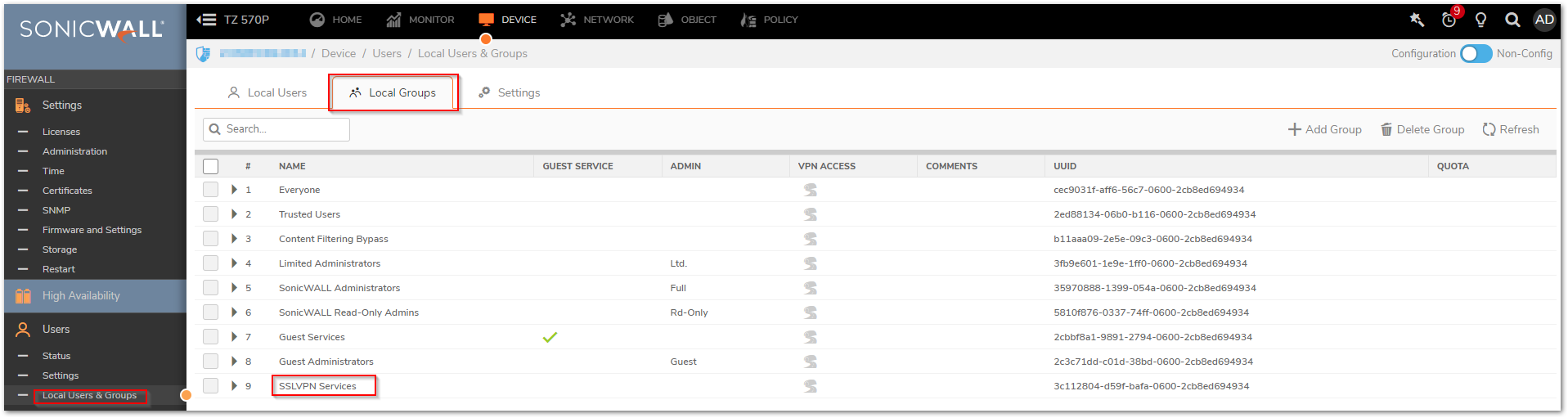
- In order for the client computer to have route and access to the virtual subnet this step is essential.
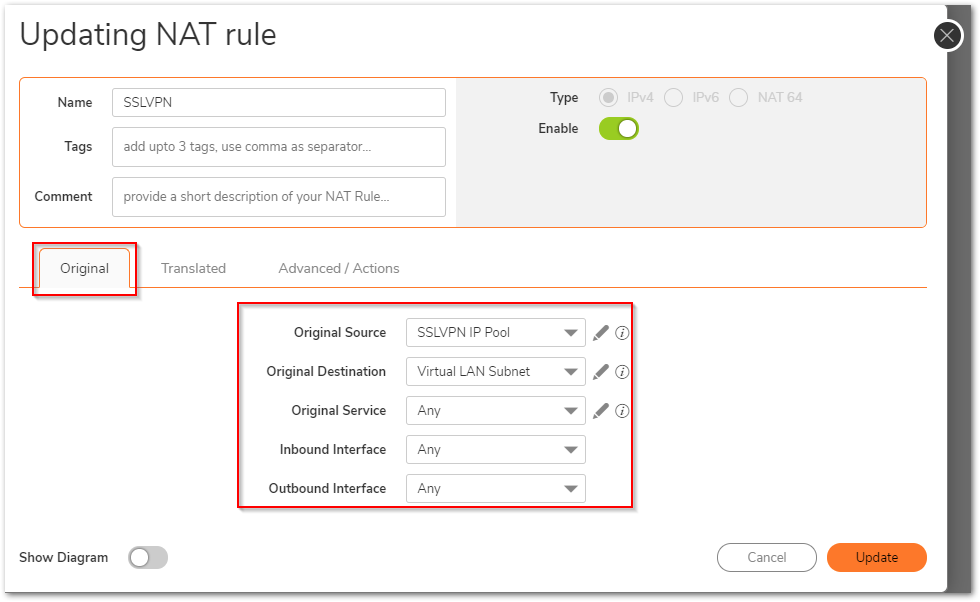
Creating a NAT policy.
- Navigate to POLICY | Rules and Policies | NAT Rules. Click Add.
- This Nat policy allows the translation of the virtual/dummy network to the actual SonicWall LAN network.

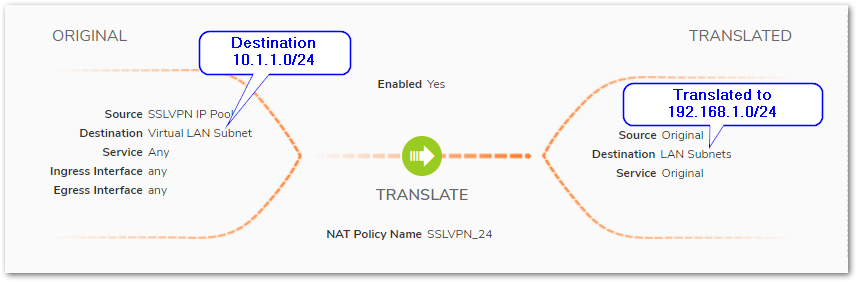
Creating an Access rule.
- Navigate to POLICY | Rules and Policies | Access Rules.
- Under SSLVPN to LAN page and create the following access rule.
- SSLVPN> LAN
- Source: SSLVPN IP Pool
- Destination: Virtual LAN Subnet
- Service: Any
- Action : Allow
How to test
- When the NetExtender/ Mobile Connect users with overlapping network will try to access the SonicWall LAN they must use an IP address from the virtual/dummy IP subnet. For example Client computer with NetExtender IP- 10.1.1.1 trying to access a server using virtual IP 10.10.10.65. This traffic when reaches SonicWall device it translates the destination IP from 10.10.10.65 to 192.168.1.65(actual LAN IP) and access rule allows traffic from SSLVPN to LAN zone.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Creating address object for SSL VPN IP pool
The IP range used for SSLVPN IP Pool should not conflict with IP scheme present on either SonicWall or client side. The subnet used here is 10.1.1.0/24.
- Login to the SonicWall UTM appliance,
- Navigate to Manage | Objects | Address Objects. Click Add to create an address object for SSL VPN IP Pool.
- Name: SSLVPN Ip Pool (Any Friendly Name as you wish but need to select that while configuring SSLVPN )
- Zone: SSLVPN
- Type: Network
- Network: 10.1.1.0
- Netmask/Prefix Length: 255.255.255.0
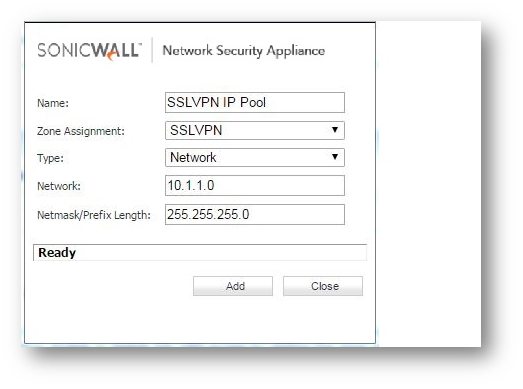
Specify the address object in SSLVPN client setting as follows
- Navigate to Manage |Connectivity | SSL VPN | Client setting, click Configure.
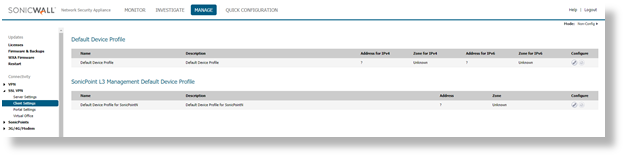
- Specify the address object in the Network Address IPv4 option on the Setting tab.
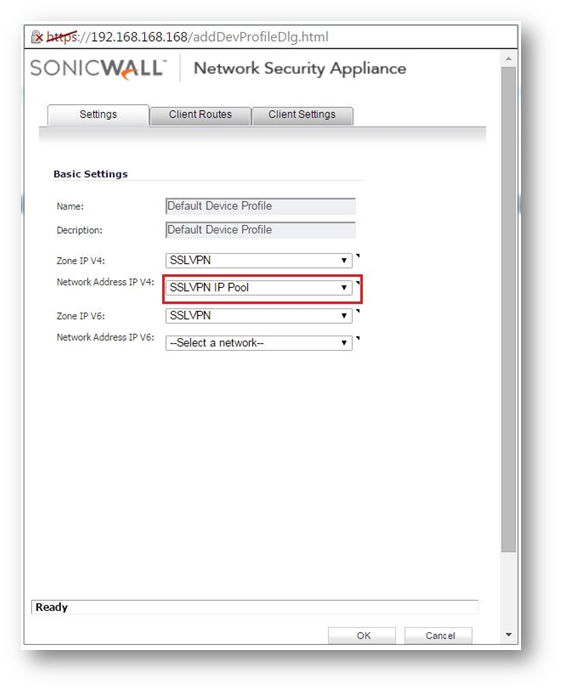
- Create Virtual LAN Subnet address object with zone being LAN.
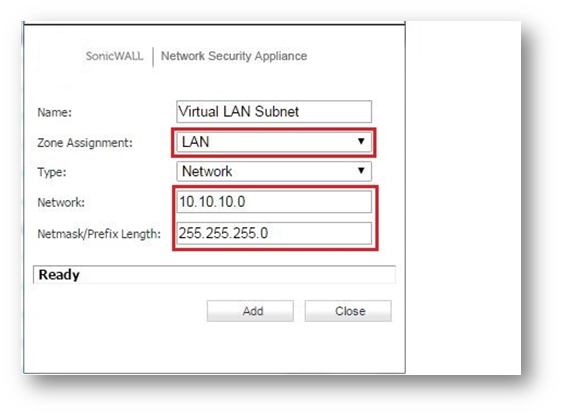
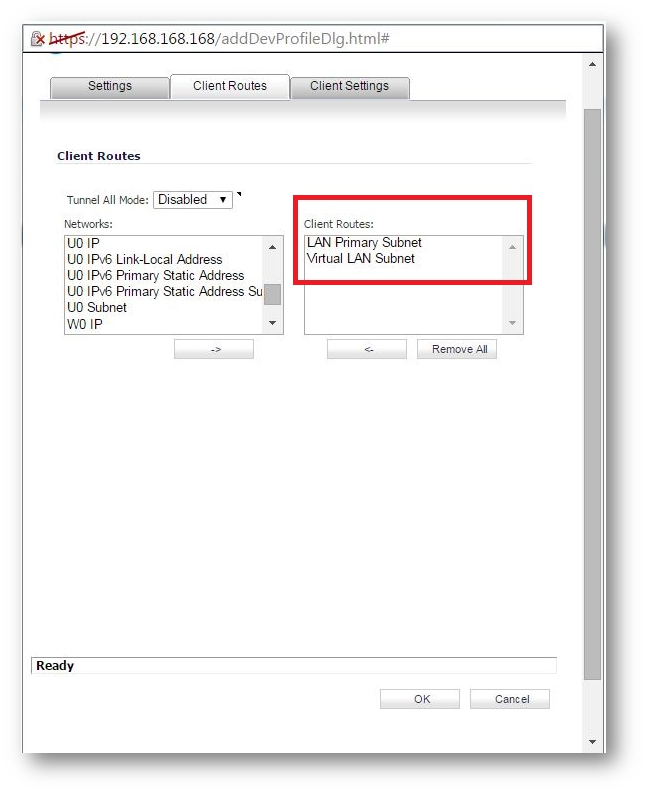
Specify Virtual LAN Subnet address object in the SSL VPN Client routes
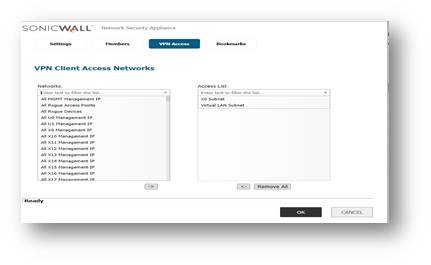
Add the Virtual LAN Subnet address object in VPN access of SSLVPN Services Local group.
- Navigate to Manage | Users| Local groups| SSLVPN services and the address object in the VPN access of this group.
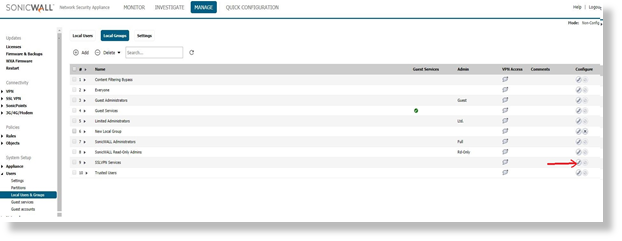
- In order for the client computer to have route and access to the virtual subnet this step is essential.
Creating a NAT policy.
- Navigate to Manage | Policies | Rules | NAT Policies. Click Add.
- This Nat policy allows the translation of the virtual/dummy network to the actual SonicWall LAN network.
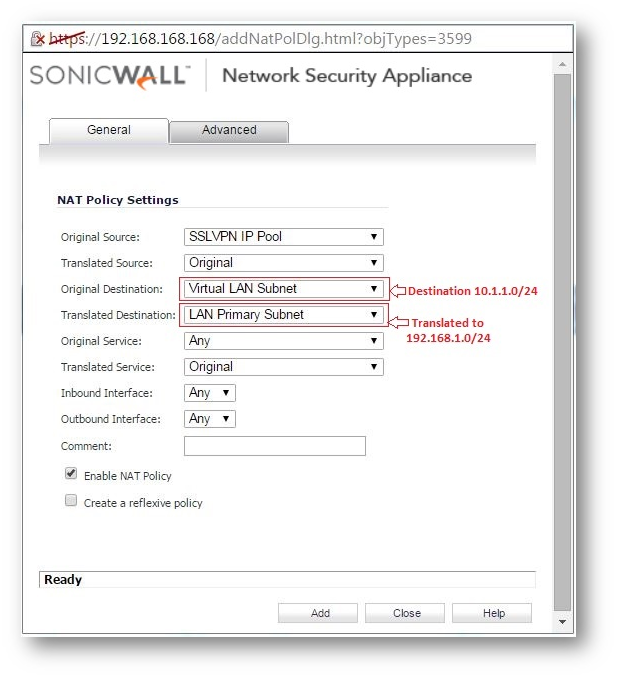
Creating an Access rule.
- Navigate to Manage | Policies | Rules | Access Rules.
- Under SSLVPN to LAN page and create the following access rule.
- SSLVPN> LAN
- Source: SSLVPN IP Pool
- Destination: Virtual LAN Subnet
- Service: Any
- Action : Allow
How to test
- When the NetExtender/ Mobile Connect users with overlapping network will try to access the SonicWall LAN they must use an IP address from the virtual/dummy IP subnet. For example Client computer with NetExtender IP- 10.1.1.1 trying to access a server using virtual IP 10.10.10.65. This traffic when reaches SonicWall device it translates the destination IP from 10.10.10.65 to 192.168.1.65(actual LAN IP) and access rule allows traffic from SSLVPN to LAN zone.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > NSa Series > SSLVPN
- Firewalls > NSv Series > SSLVPN
- Firewalls > TZ Series > SSLVPN
- Firewalls > NSa Series > Networking
- Firewalls > TZ Series > Networking






 YES
YES NO
NO