-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I configure Application Control Advanced feature in SonicOS Enhanced?



Description
In SonicOS 5.8, the Application Firewall feature of previous SonicOS releases has been significantly enhanced with Application Control functionality. As part of this solution, the set of application relevant signatures have been extracted from the existing set of IPS signatures and placed under the realm of the Application Control feature. This change impacts the way that application control policies and dynamic objects are configured and used.
SonicOS 5.8 introduces a new user interface for application control with the new Firewall | App Control Advanced page. In some TZ models the App Control Advanced page is located under Security Services. This screen provides a simple and direct way of configuring application control rules. In SonicOS 5.8, all of the application configuration which was previously available under Security Services | Intrusion Prevention is now moved to the App Rules page, leaving IPS to handle threats and attacks. This change means that applications have their own user interface now, and you no longer have to configure them under Intrusion Prevention.
The most significant enhancement made in the configuration of application signatures is the addition of a new level configuration called Application. Hitherto, under IPS signatures were grouped under Priority, Categories and Signatures. With Application level, application signatures are grouped based on the name of the application. For eg. the 8 signatures of Google Chat have been grouped under the Application name "Google Chat" (See screenshot below). The advantage of this level of granularity is that administrators can prevent application traffic by configuring the Application rather than configure each signature. Keeping with the example above, to block Google Chat an administrator need only enable prevention of Google Chat, instead of enabling prevention on each of the 8 signatures.
You can enable prevention or detection for a whole category of applications with one click, and can easily locate and do the same for an individual application or individual signature. Once enabled, Category, Application, or Signature is blocked or logged globally.
Resolution
 TIP:Video Tutorial: Click here for the video tutorial of How to block applications using application control advanced.
TIP:Video Tutorial: Click here for the video tutorial of How to block applications using application control advanced.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
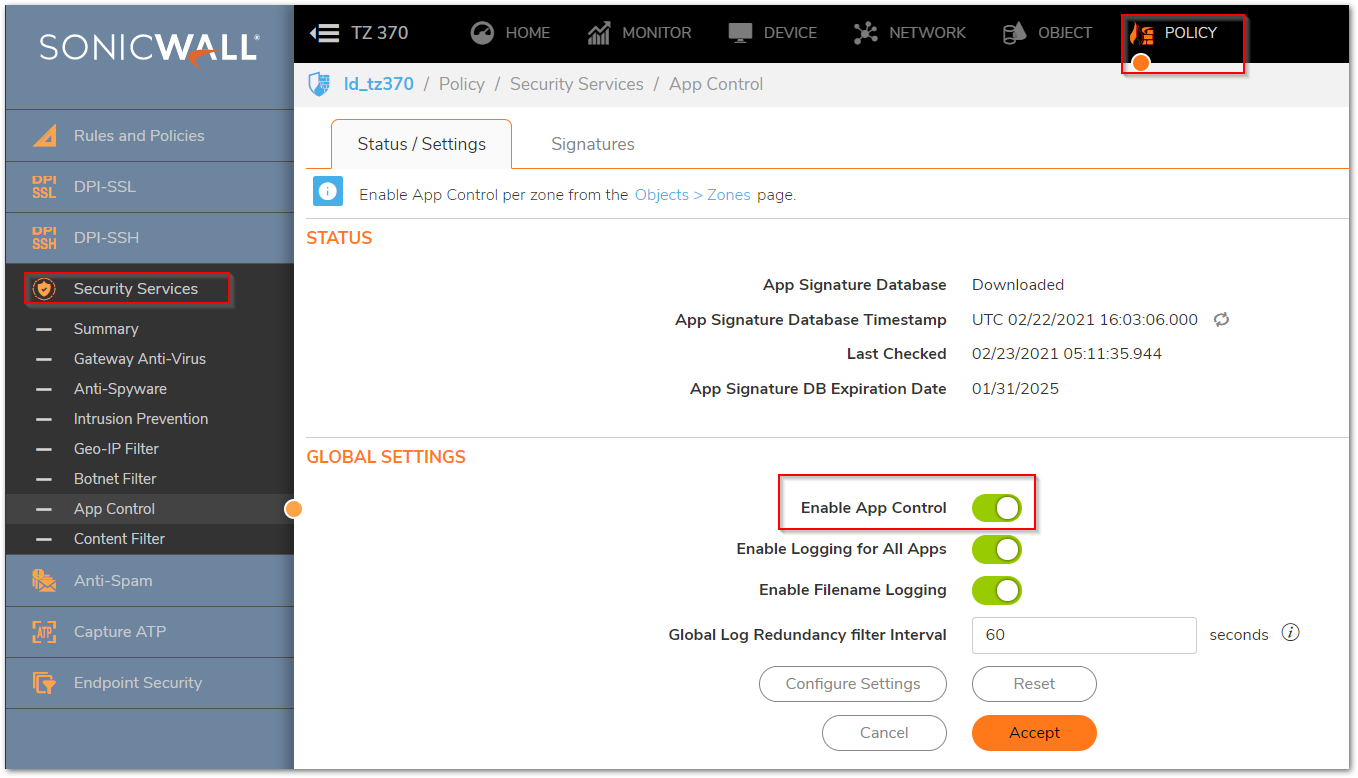
Enable Application Control
- Login to your SonicWall management page and click Policy tab on top of the page.
- Navigate to Security Services | App Control page, on right side enable Enable App Control checkbox under App Control Status / Settings section.
- Click Accept .
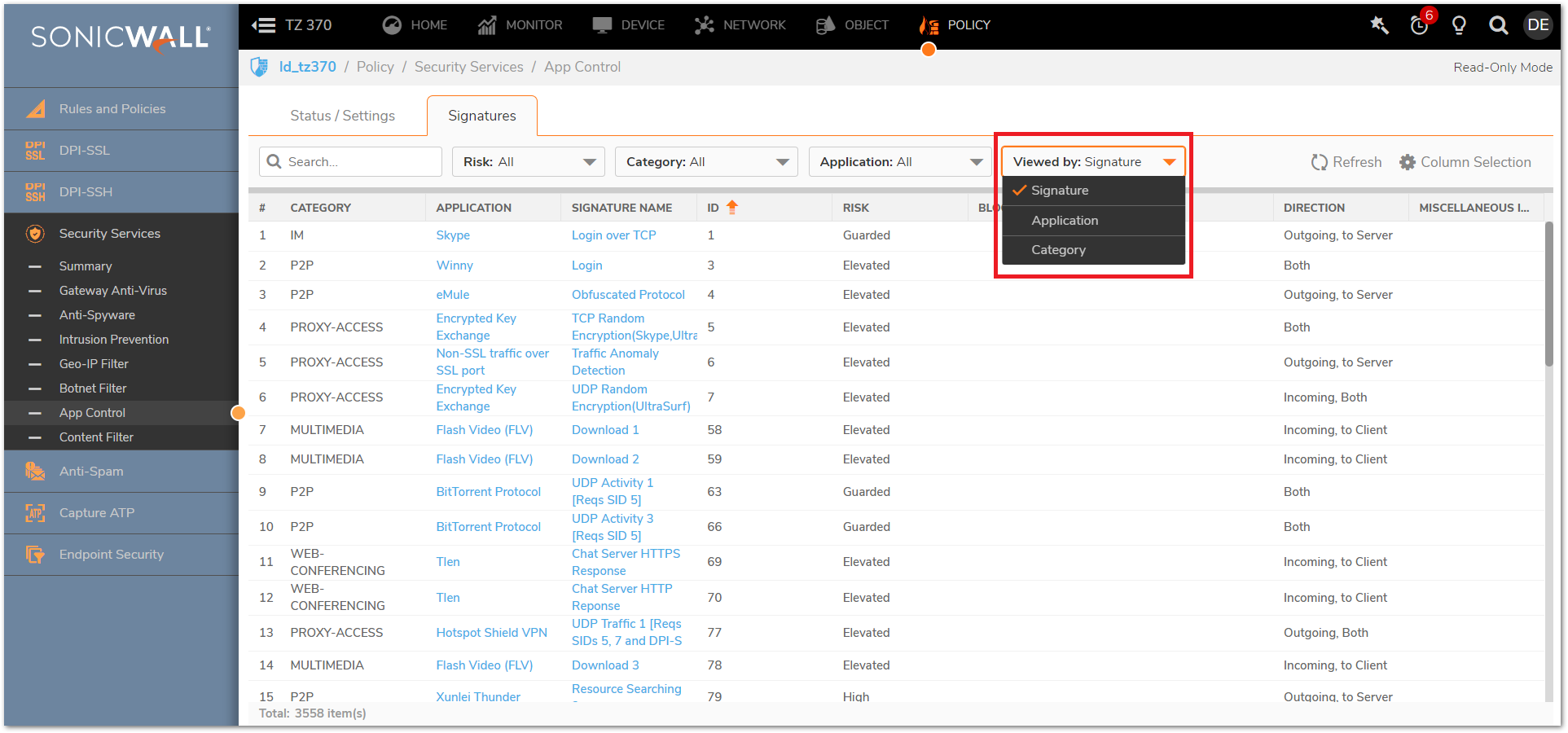
- Application Control signatures can be viewed by Category, Application and Signature.
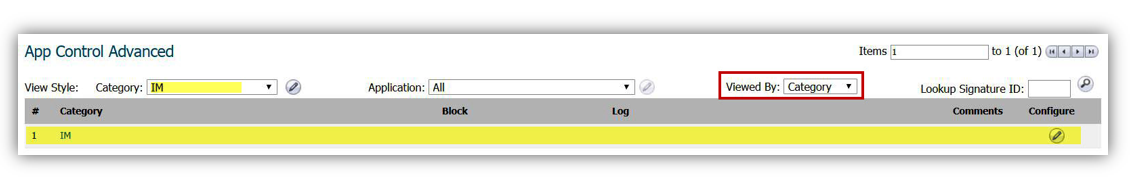
- To view the App Control option by Category, Select Category in the Viewed by drop down menu.
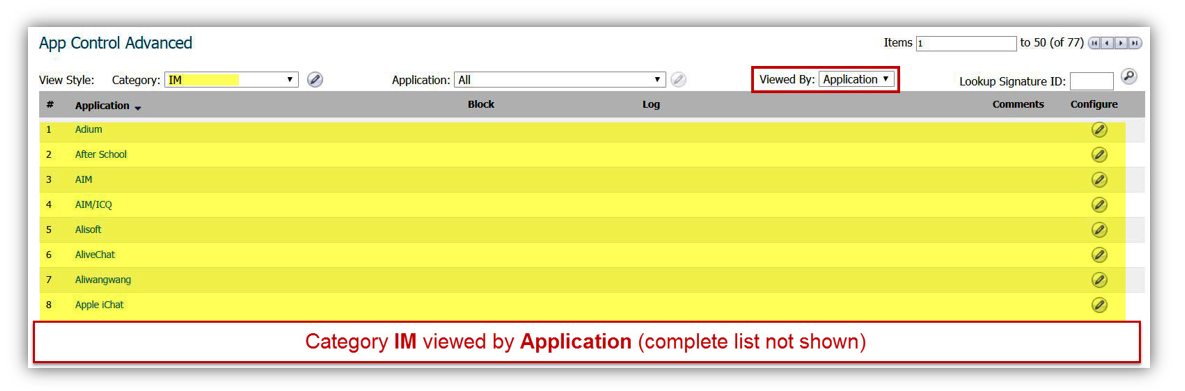
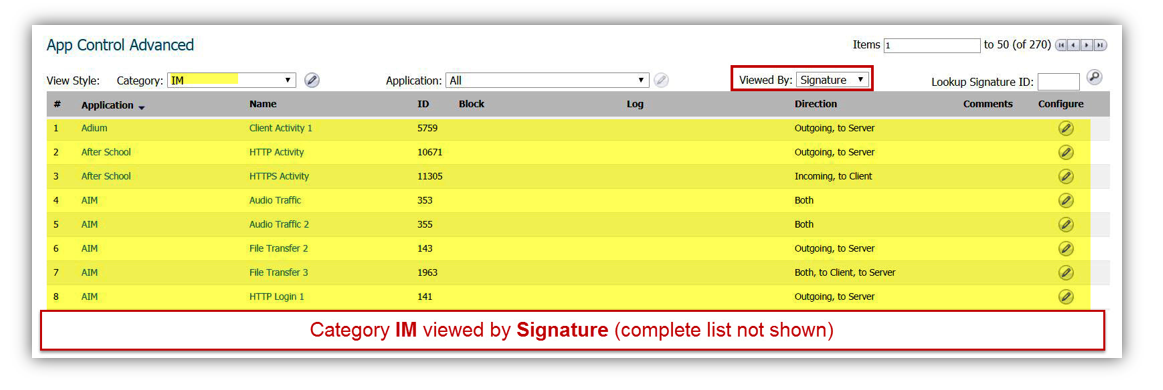
- The same drop down menu can be used to view the App Control options of Application and Signature.
Category based Application Control
|
Blocking an application while allowing the category.
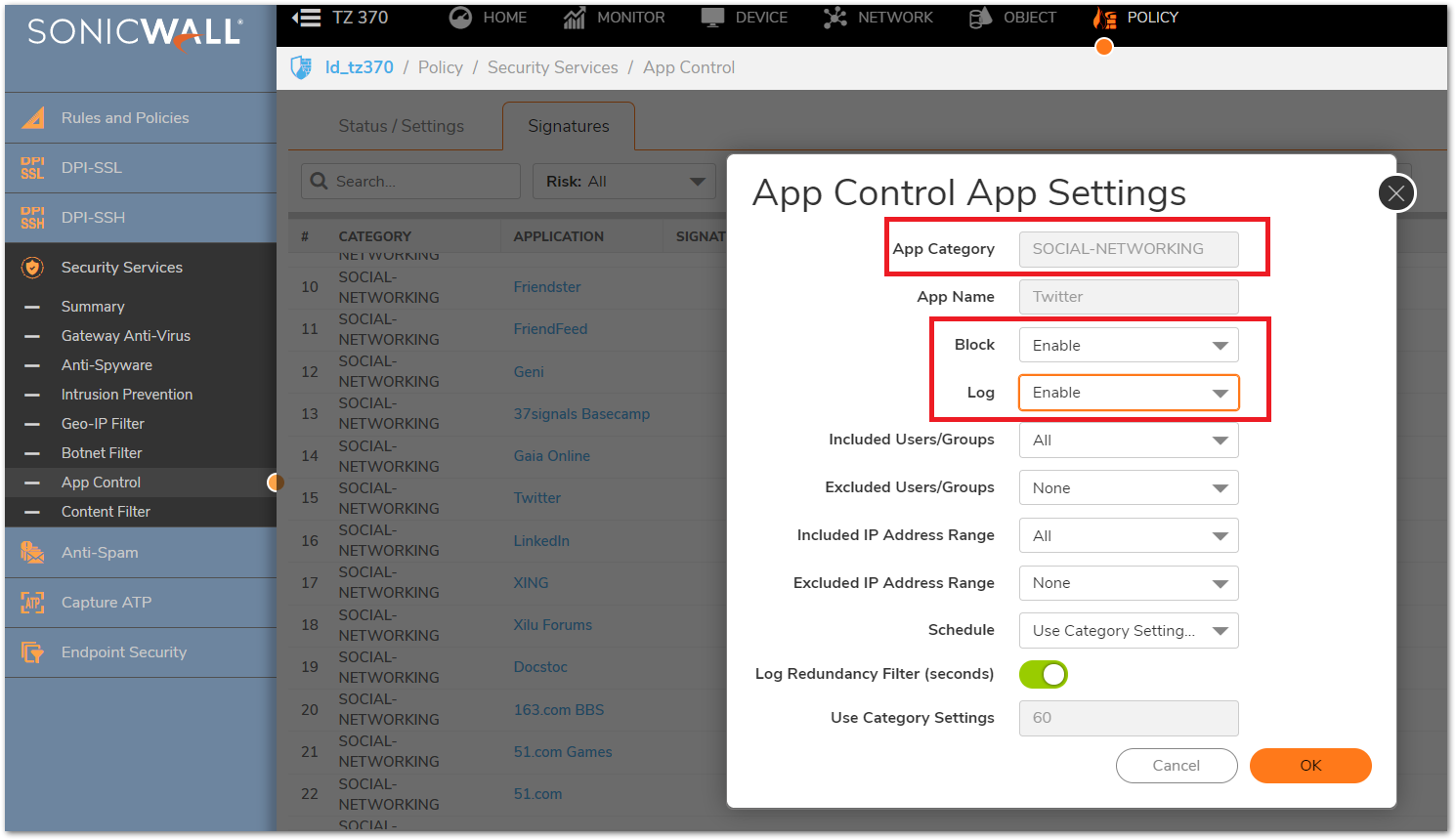
In this example we configure the application Twitter to be blocked although the parent category Social-Networking is set to Allow.
|
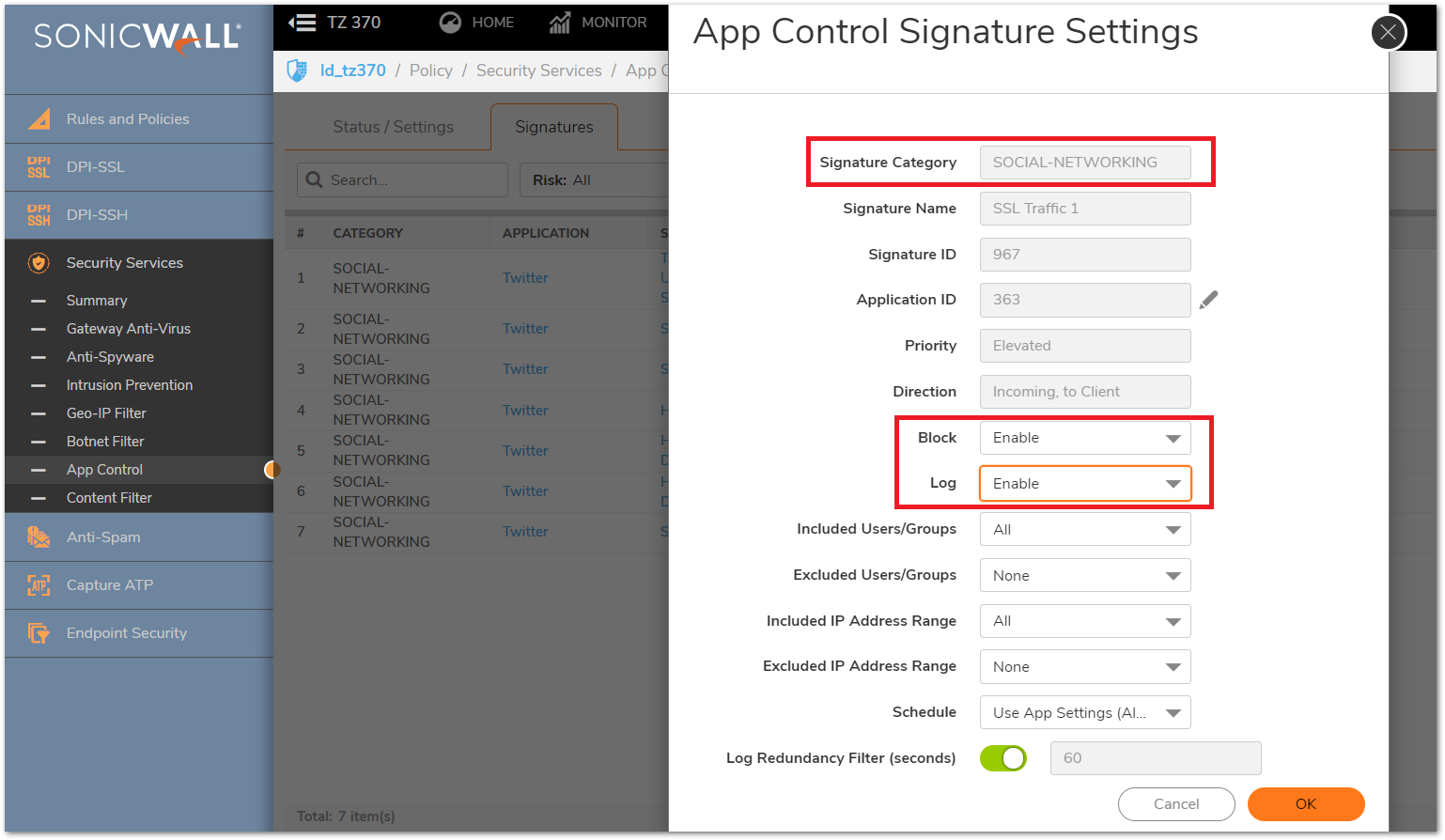
Signature based Application Control
|
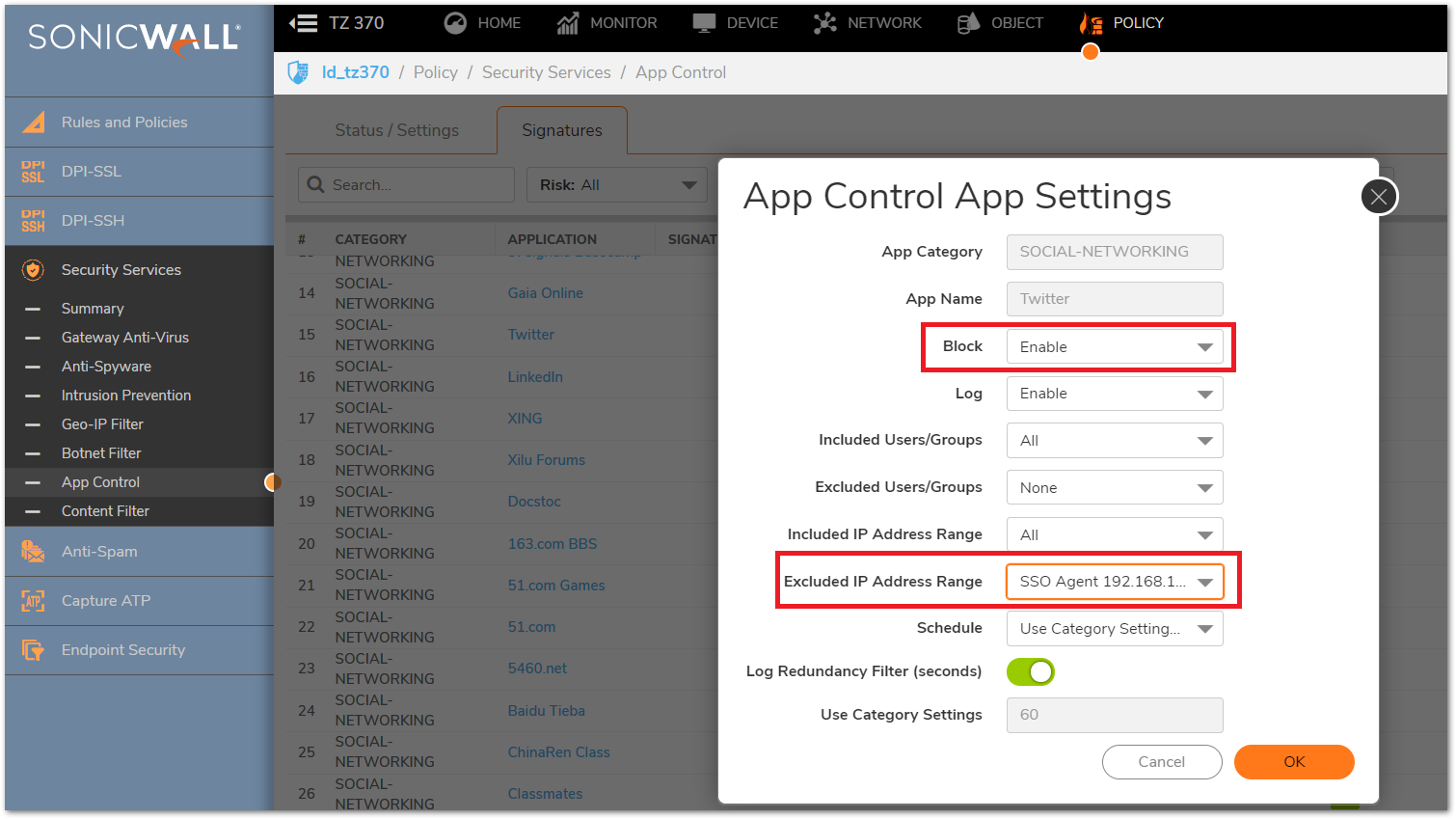
Including / Excluding IP Address Range
- When an object is selected on each layer of configuring App Control the following options are there to include or exclude IP addresses.
| Category layer | All: This applies to all hosts behind the SonicWall. Custom and default address objects and groups: Can either use the default objects like LAN Subnets, or create a custom address object for individual IP addresses, range of IP addresses. |
| Application layer | Use Category Settings: Selecting this option would inherit the settings configured in the parent Category. All: This applies to all hosts behind the SonicWall. Custom and default address objects and groups: Can either use the default objects like LAN Subnets, or create a custom address object for individual IP addresses, range of IP addresses. |
| Signature layer | Use App Settings: Selecting this option would inherit the settings configured in the parent Application. All: This applies to all hosts behind the SonicWall. Custom and default address objects and groups: Can either use the default objects like LAN Subnets, or create a custom address object for individual IP addresses, range of IP addresses. |
- In the example below, the Category Social-Networking has been blocked for all hosts behind the SonicWall except address object labeled SSO Agent 192,168.1.2
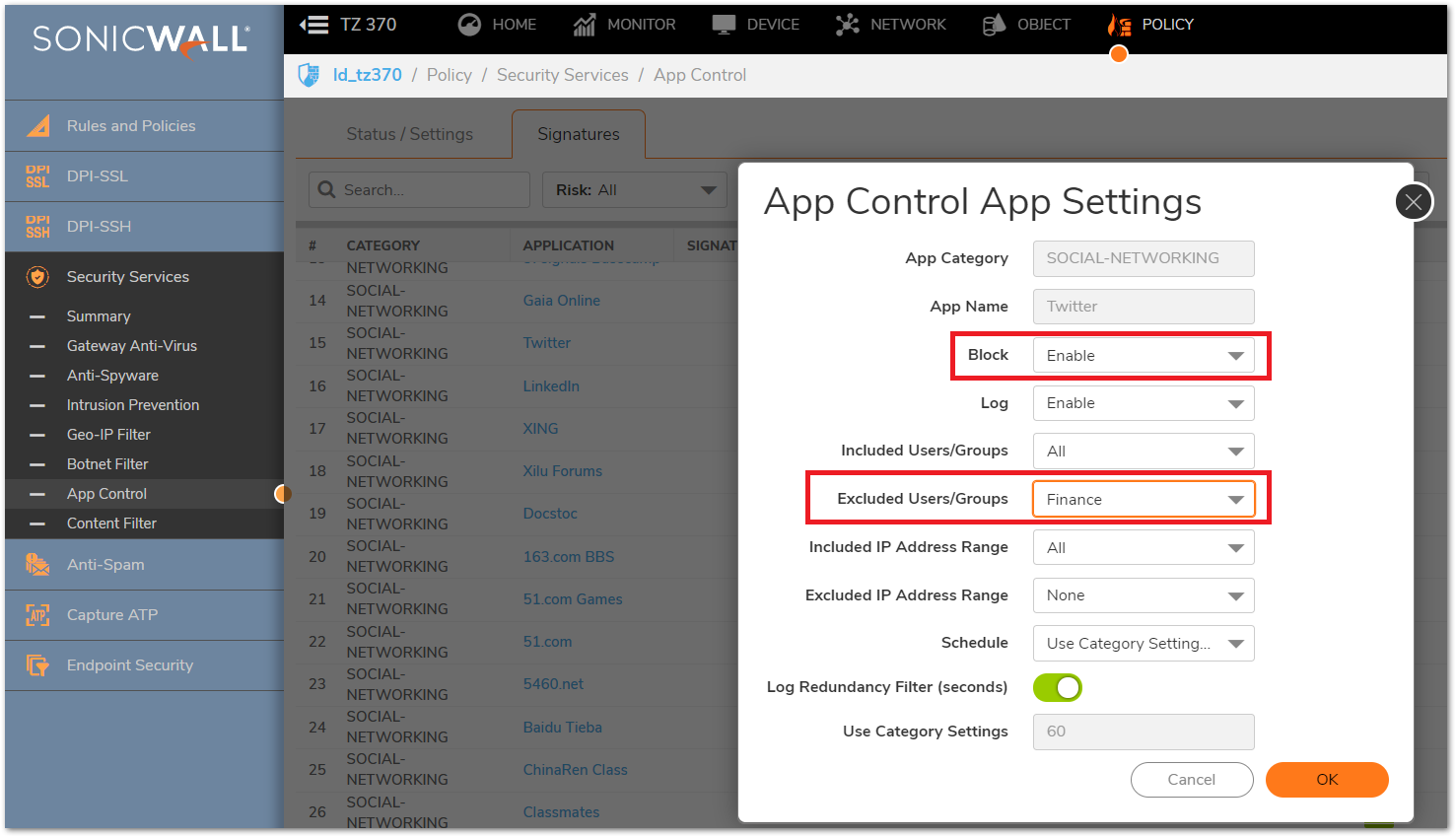
Including / Excluding Users / User Groups
- Similar to including or excluding IP addresses, inclusion / exclusion of Users or User groups on each layer of App Control can be configured in the following manner.
| Category layer | All: This applies to all users behind the SonicWall. Custom and default user objects and groups: Can either use the default user objects like Everyone, Trusted Users etc. or create a local user. |
| Application layer | Use Category Settings: Selecting this option would inherit the settings configured in the parent Category. All: This applies to all users behind the SonicWall. Custom and default user objects and groups: Can either use the default user objects like Everyone, Trusted Users etc. or create a local user. |
| Signature layer | Use App Settings: Selecting this option would inherit the settings configured in the parent Application. All: This applies to all users behind the SonicWall. Custom and default user objects and groups: Can either use the default user objects like Everyone, Trusted Users etc. or create a local user. |
- In the example below, the Category Social-Networking has been blocked for all users behind the SonicWall except user group labeled Finance
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Enable Application Control
- Login to your SonicWall management page and click Manage tab on top of the page.
- Navigate to Rules | Advanced Application Control page, on right side enable Enable App Control checkbox under App Control Global Settings section.
- Click Accept .
 NOTE: Enable App Control per zone by checking the box under Enable App Control Service on each zone.
NOTE: Enable App Control per zone by checking the box under Enable App Control Service on each zone.
App Control view style
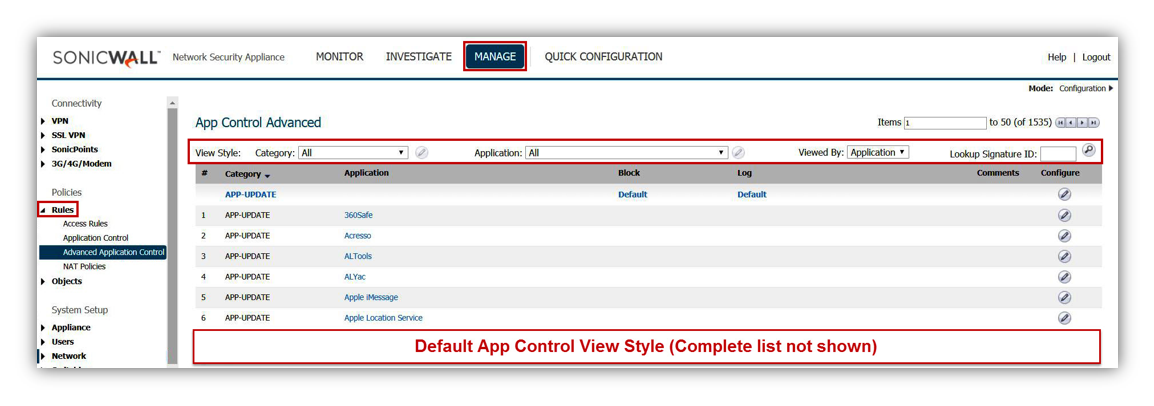
- Application Control signatures can be viewed by Category, Application and Signature..
- View by Category with Category set to All and Application set to All = All Categories will be listed without either Application or Signatures listed.
- View by Application with Category set to All and Application set to All = All Categories with their corresponding Application will be listed without listing Signatures.
- View by Signatures with Category set to All and Application set to All = All Categories with their corresponding Application and Signatures will be listed.
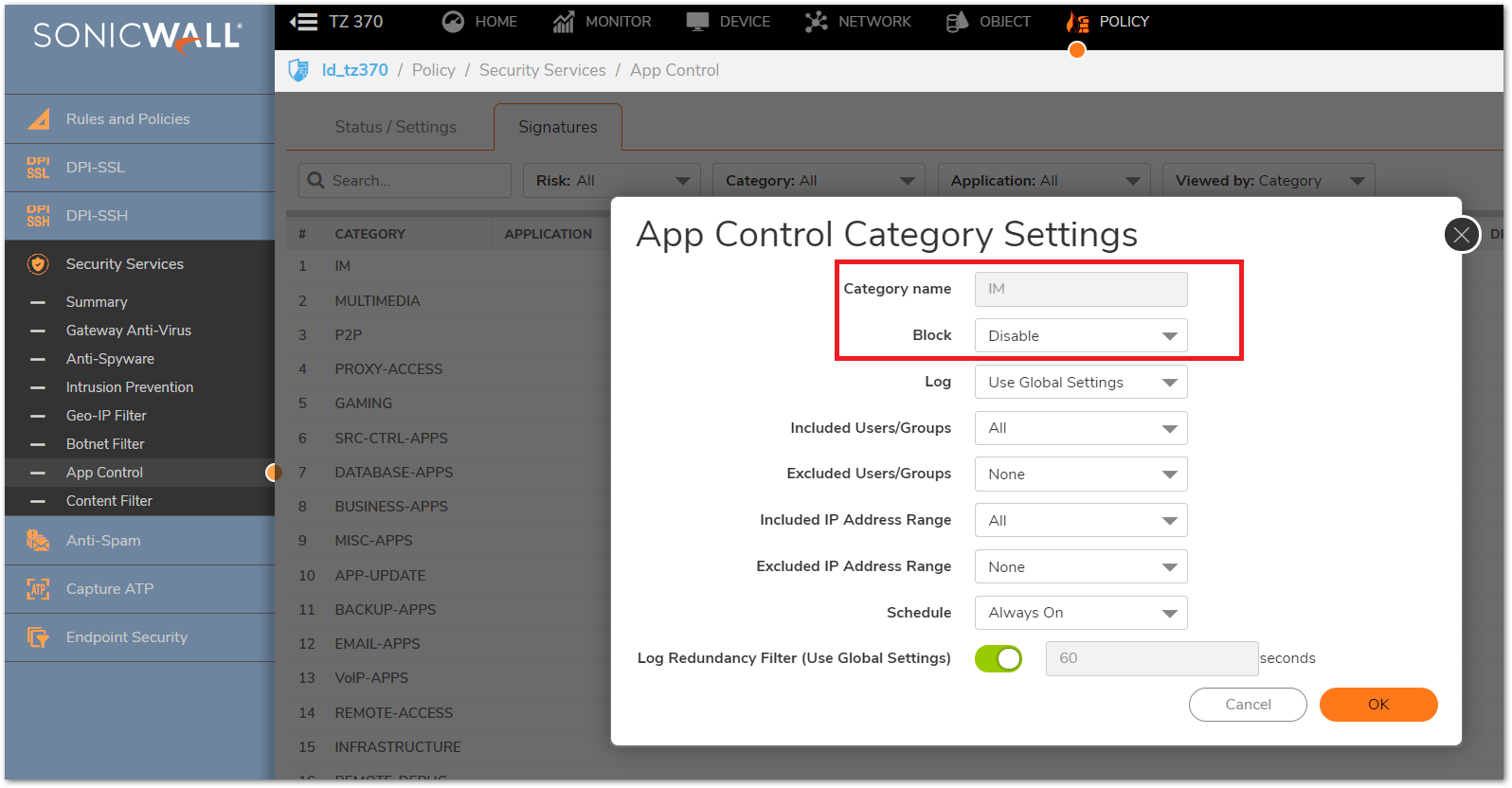
 EXAMPLE: By selecting category IM with the following Viewed By settings will get the following.
EXAMPLE: By selecting category IM with the following Viewed By settings will get the following.
|
 |
|
 |
|
 |
Category based Application Control
|
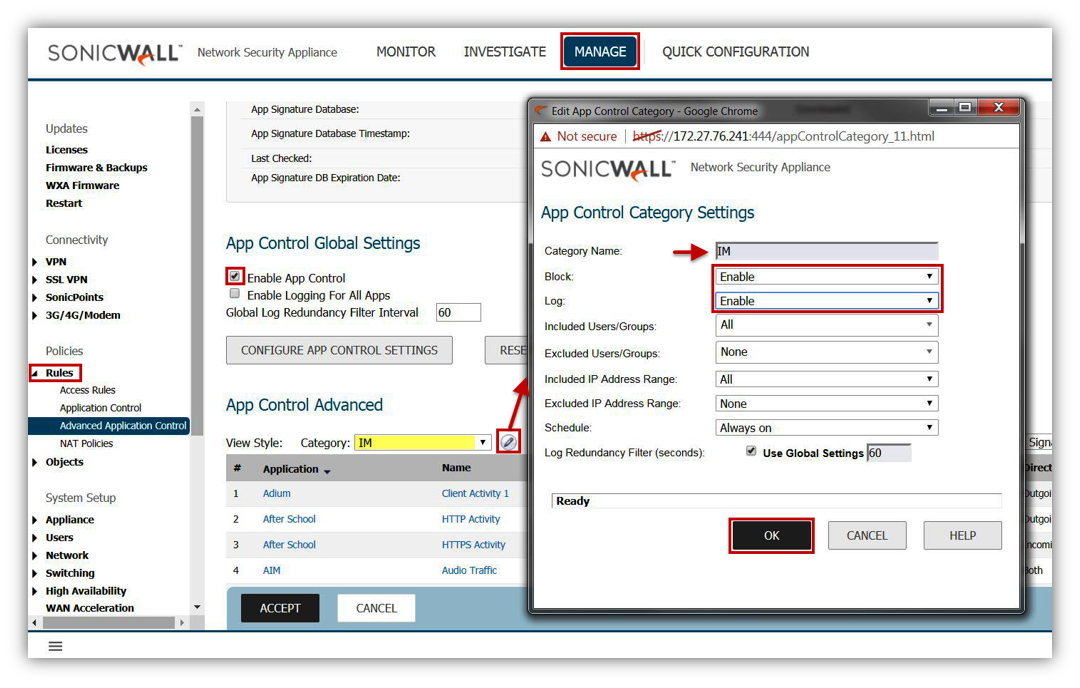 |
Blocking a category while allowing an application within the category.
In this example we configure the application Kakao Talk to be allowed although the parent category IM is set to Block.
|
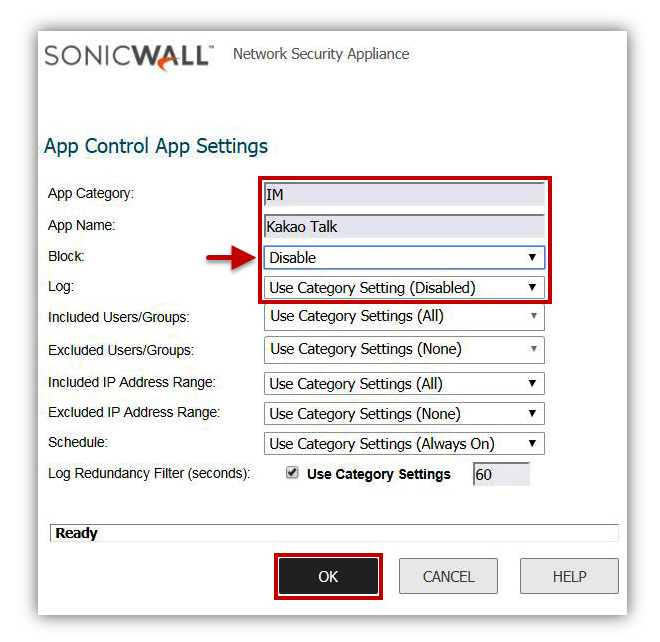 |
Blocking a signature while allowing the parent application
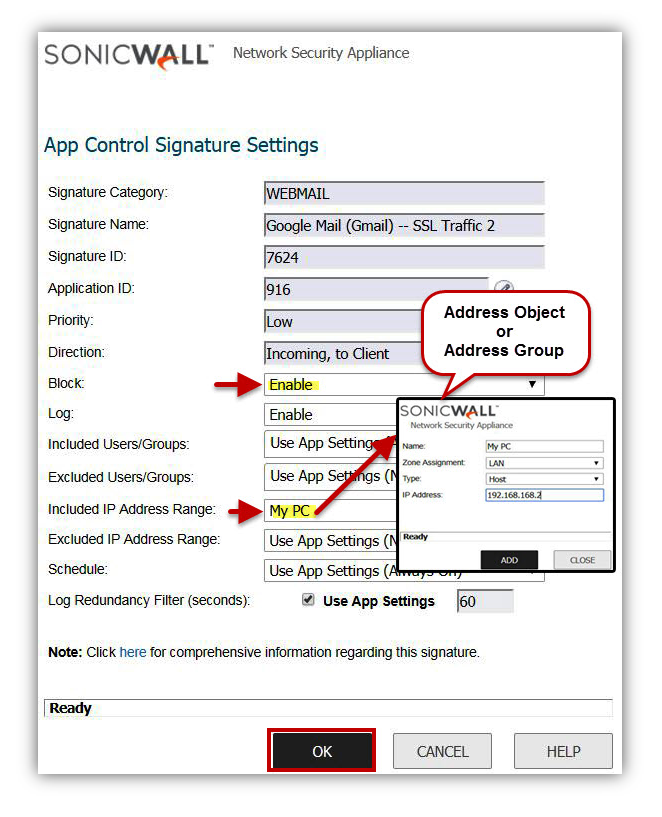
- In this example we block the category Webmail, allow mail.google.com (Gmail.com) but block embedded chat in Gmail.
- On the App Control Advanced page, select Webmail from the Category drop-down list.
- Select Google Mail (Gmail) from the Application drop-down list.
- Setting Viewed By to Signature will list signatures for Gmail.
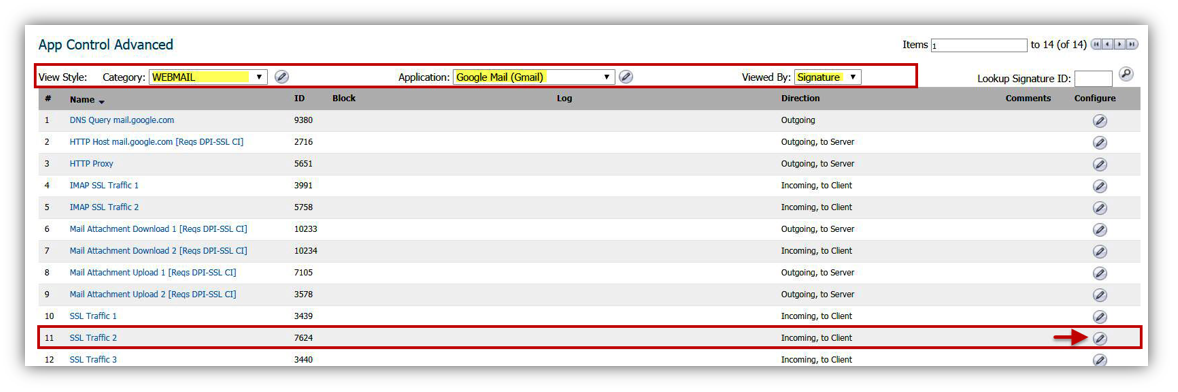
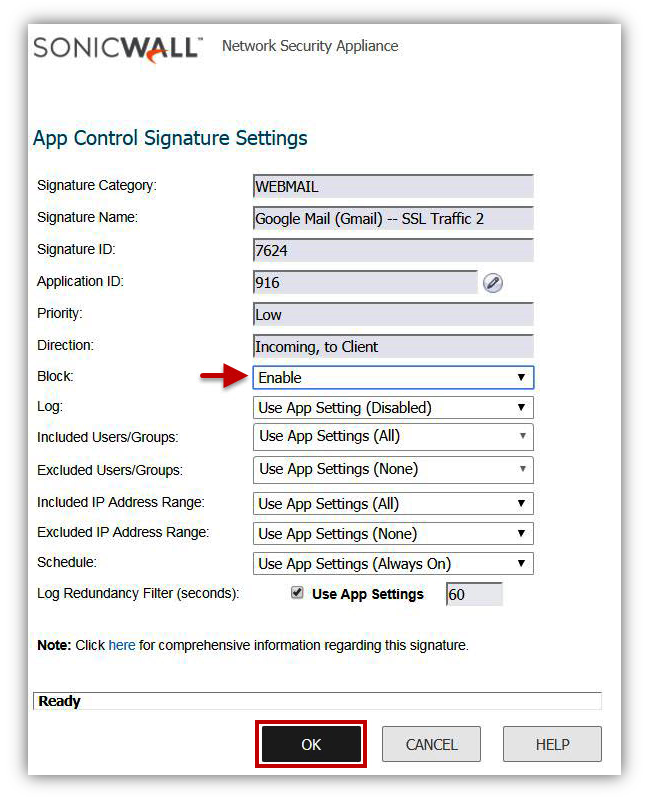
- To block the embedded Chat within Gmail, click on the configure button alongside Signature ID 7624(SSL Traffic 2), to bring up the Edit App Control App window.
- Select Disable under Block. Log could be set to either use Category Settings, Enable or Disable.
- Click OK.
Including / Excluding IP Address Range
- When an object (
 EXAMPLE: IM) is selected on each layer of configuring App Control the following options are there to include or exclude IP addresses.
EXAMPLE: IM) is selected on each layer of configuring App Control the following options are there to include or exclude IP addresses.
| Category layer | All: This applies to all hosts behind the SonicWall. Custom and default address objects and groups: Can either use the default objects like LAN Subnets, or create a custom address object for individual IP addresses, range of IP addresses. |
| Application layer | Use Category Settings: Selecting this option would inherit the settings configured in the parent Category. All: This applies to all hosts behind the SonicWall. Custom and default address objects and groups: Can either use the default objects like LAN Subnets, or create a custom address object for individual IP addresses, range of IP addresses. |
| Signature layer | Use App Settings: Selecting this option would inherit the settings configured in the parent Application. All: This applies to all hosts behind the SonicWall. Custom and default address objects and groups: Can either use the default objects like LAN Subnets, or create a custom address object for individual IP addresses, range of IP addresses. |
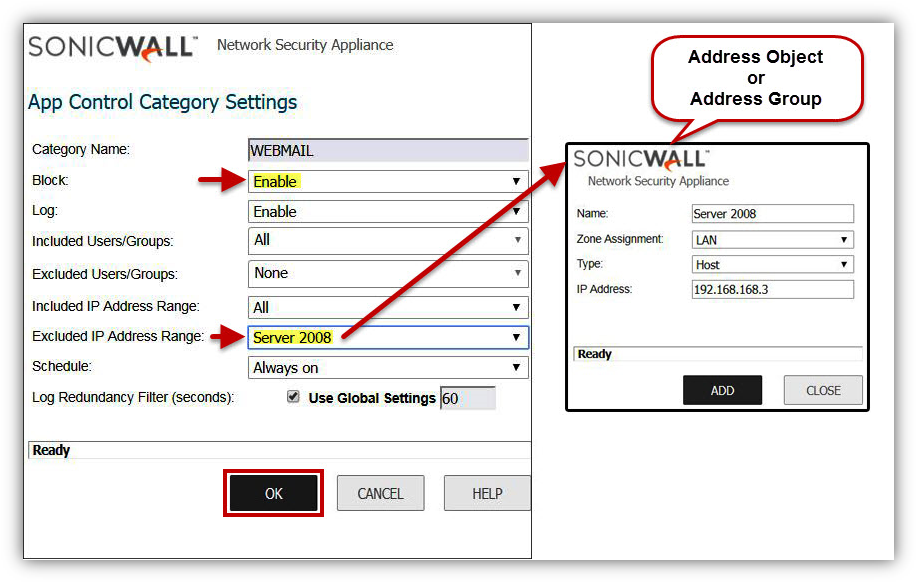
- In the example below, the Category IM has been blocked for all hosts behind the SonicWall except IP address 192.168.168.3.
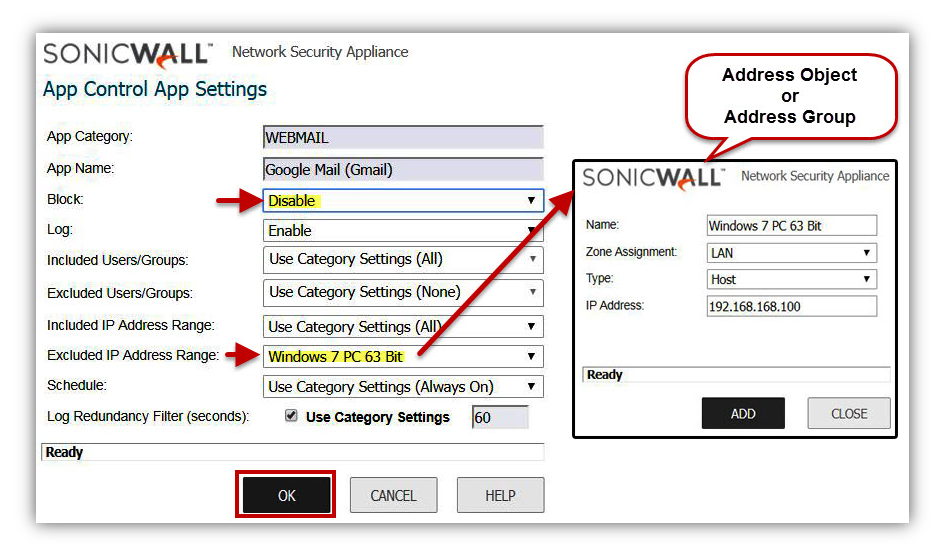
- In the example below, the Application Gmail (Google Mail) is allowed for all hosts except the IP address, 192.168.168.100.
- In the example below, the Signature SSL Traffic 2 under Application Gmail (Google Mail) is blocked for the IP address, 192.168.168.2.
Including / Excluding Users / User Groups
- Similar to including or excluding IP addresses, inclusion / exclusion of Users or User groups on each layer of App Control can be configured in the following manner.
| Category layer | All: This applies to all users behind the SonicWall. Custom and default user objects and groups: Can either use the default user objects like Everyone, Trusted Users etc. or create a local user. |
| Application layer | Use Category Settings: Selecting this option would inherit the settings configured in the parent Category. All: This applies to all users behind the SonicWall. Custom and default user objects and groups: Can either use the default user objects like Everyone, Trusted Users etc. or create a local user. |
| Signature layer | Use App Settings: Selecting this option would inherit the settings configured in the parent Application. All: This applies to all users behind the SonicWall. Custom and default user objects and groups: Can either use the default user objects like Everyone, Trusted Users etc. or create a local user. |
App Control Logs
When a category, application or a signature is blocked, logs similar to the ones below can be seen under the Investigate tab | Event Logs.To be able to see Application Control logs make sure the following are true:
- The log category Application Control is checked for logging under Manage tab Log Settings | Base Settings page| Categories.
- When configuring a category, application or a signature, make sure the option Log is set to Enable.

Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Application Firewall
- Firewalls > NSv Series > Application Firewall
- Firewalls > TZ Series > Application Firewall






 YES
YES NO
NO