-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I configure a site-to-site VPN between a SonicWall and Linux Openswan?



Description
How can I configure a site-to-site VPN between a SonicWall and Linux Openswan?
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
The Linux server
On this side (or branch office) is the Linux server as the router and providing Internet for the following network.
 NOTE: The actual setup of a Linux machine to act as a network router is out of the scope of this document.
NOTE: The actual setup of a Linux machine to act as a network router is out of the scope of this document.
- WAN IP: 209.14.212.52
- Internal subnet: 192.168.0.0/24
- IP of Linux server: 192.168.0.1
- WAN Iface of Linux server: eth0
The SonicWall device
On this side (or branch office) is the SonicWall device serving as the router and providing Internet for the following network.
- WAN IP: 24.252.13.9
- Internal subnet: 10.0.0.0/24
- IP of SonicWall': 10.0.0.1
Openswan side configuration
- Kernel requirements (If you built your own kernel you're going to either have to include the following as modules or build them in)
- Transformation user configuration interface
- PF_KEY sockets
- IP: AH transformations
- IP: ESP transformations
- IP: IPComp transformations
- IP: IPsec tunnel mode
- Usually these are found under Networking | Network Options.
 NOTE: If you have not built your own kernel, chances are these are already built in.
NOTE: If you have not built your own kernel, chances are these are already built in.
Openswan config There are two configuration files you need to pay attention to:
- /etc/IPSec.conf version 2.0
config setup NOTE: Having this option off caused issues.
NOTE: Having this option off caused issues.nat_traversal=yesoe=offprotostack=netkeyfragicmp=noconn SonicWall - This is where you define your connexion to the SonicWall.
- You do not have to call it "SonicWall" you can call it what you wish.
left=209.14.212.52leftsourceip=192.168.0.1leftsubnet=192.168.0.0/24leftid=209.14.212.52right=24.252.13.9rightid=24.252.13.9keyingtries=0pfs=noaggrmode=yesauth=espesp=3des-sha1ike=3des-sha1authby=secretkeyexchange=ikerightsubnet=10.0.0.0/24 NOTE: Thisallows the VPN to come up automatically when openswan starts.
NOTE: Thisallows the VPN to come up automatically when openswan starts.auto=start
 TIP: You'll notice the rightid and the leftid above. These are what helps identify the connexion when the Openswan and the SonicWall try to talk. Usually SonicWalls want this value set to a SonicWall Identifier. Well, if you haven't noticed by now your Openswan/Linux box won't have an identifier for itself. So we use the IP instead. SonicWalls will also accept that option.
TIP: You'll notice the rightid and the leftid above. These are what helps identify the connexion when the Openswan and the SonicWall try to talk. Usually SonicWalls want this value set to a SonicWall Identifier. Well, if you haven't noticed by now your Openswan/Linux box won't have an identifier for itself. So we use the IP instead. SonicWalls will also accept that option.
- /etc/IPSec.secrets
209.14.212.52 24.252.13.9 : PSK "secretpass" NOTE: In the IPSec.secrets file make sure the IPs are correct. This will be what gives the authentication password for the VPN. If your IPs change and you have to change them in the IPSec.conf file, make sure to remember to change them here to. Otherwise you'll have errors and it won't establish a connexion.
NOTE: In the IPSec.secrets file make sure the IPs are correct. This will be what gives the authentication password for the VPN. If your IPs change and you have to change them in the IPSec.conf file, make sure to remember to change them here to. Otherwise you'll have errors and it won't establish a connexion.
iptables config
 CAUTION: If you're doing masquerading and you have other Nat rules set up in iptables it will interfere with your VPN traffic. So, you will have to set rules to allow all traffic unaffected for your VPN subnet.
CAUTION: If you're doing masquerading and you have other Nat rules set up in iptables it will interfere with your VPN traffic. So, you will have to set rules to allow all traffic unaffected for your VPN subnet.
- IPSec ports for opening
iptables -A INPUT -p ah -j ACCEPTiptables -A INPUT -p esp -j ACCEPTiptables -A INPUT -p udp -i eth0 --dport 500 -j ACCEPTiptables -A INPUT -p udp -i eth0 --dport 4500 -j ACCEPTiptables -A INPUT -p udp -i eth0 --dport 50:58 -j ACCEPTiptables -A INPUT -p TCP -i eth0 --dport 50:58 -j ACCEPT
- Allow all traffic from our SonicWall side of the VPN in
iptables -A INPUT -j ACCEPT --source 10.0.0.0/255.255.255.0 - Put a rule in to cancel out any MASQ rules that might try to take effect
iptables -t Nat -A POSTROUTING -j ACCEPT --destination 10.0.0.0/255.255.255.0 - Cancel out any forward rules that might be trying to take effect
iptables -t Nat -A PREROUTING -j ACCEPT --source 10.0.0.0/255.255.255.0
The point of the above commands is that they are placed before any other firewall rules take place that may interfere with traffic either bound to or coming from the SonicWall VPN network. In a default scenario without any restrictions we want to leave those packets untouched. If you find your VPN traffic is still being interfered with, check your other chains to see that they aren't mangling your VPN traffic.
If you need to insert the rule above another rule, for example above a MASQ rule, use the -I command instead.
 EXAMPLE:
EXAMPLE: iptables -t Nat -I POSTROUTING 1 -j ACCEPT --destination 10.0.0.0/255.255.255.0
To put the rule first in the chain.
SonicWall side configuration The screenshots below are from the web interface for the SonicWall NSA .
- Navigate to Manage | VPN | Base settings lists to add another VPN (Usually VPN|Settings on the menu).
- Under VPN Policies, Add a new VPN connection.
General Tab
Network Tab
 NOTE:For the above you'll need to configure address objects for the Local Networks and Remote Networks. When configuring the Remote Networks address object make sure it's the same subnet as the Left (or Openswan/Linux) side. Otherwise you will get errors.
NOTE:For the above you'll need to configure address objects for the Local Networks and Remote Networks. When configuring the Remote Networks address object make sure it's the same subnet as the Left (or Openswan/Linux) side. Otherwise you will get errors.
Proposals Tab
Advanced Tab
 NOTE: The XAUTH option was checked in one of the articles I did see. However, this will make Openswan prompt you for another password and you won't be able to establish the VPN without it. Also, if you do not want SMB traffic to pass through the VPN Uncheck the NetBIOS flag.
NOTE: The XAUTH option was checked in one of the articles I did see. However, this will make Openswan prompt you for another password and you won't be able to establish the VPN without it. Also, if you do not want SMB traffic to pass through the VPN Uncheck the NetBIOS flag. - Click OK .
Bringing up the VPN
- On the SonicWall side, in the VPN settings where it lists the VPN just make sure the Enable checkbox is checked.
- On the Openswan/Linux side, run the command.
/etc/init.d/IPSec restart - If everything was done correctly you should see the little green dot on the SonicWall's VPN list indicating that everything is okay.
- Some ping tests should show that you have connectivity across the VPN.
Debugging
- Check the system log file and grep out messages from pluto. This will give you a real time update on the progress of your IPSec connexions.
- Check the SonicWall log system.
- Make sure none of your iptables rules are blocking VPN traffic.
Multiple subnets across the VPN
- So your SonicWall side has multiple subnets that you want to be able to reach. This is easy with Openswan. On your SonicWall side of course configure the proper Address Objects. Then on your Openswan config do the following.
- /etc/IPSec.conf version 2.0
config setupnat_traversal=yesoe=offprotostack=netkeyfragicmp=noconn SonicWallleft=209.14.212.52leftsourceip=192.168.0.1leftsubnet=192.168.0.0/24leftid=209.14.212.52right=24.252.13.9rightid=24.252.13.9keyingtries=0pfs=noaggrmode=yesauth=espesp=3des-sha1ike=3des-sha1authby=secretkeyexchange=ikeconn SonicWall-0network# Include the other configalso=SonicWall# Our default subnetrightsubnet=10.0.0.0/24# Make sure this one autostartsauto=startconn SonicWall-1networkalso=SonicWallrightsubnet=10.0.1.0/24auto=start NOTE: Given that 10.0.1.0/24 is the other subnet behind the SonicWall on some VLAN or something. Make sure you put in the proper firewall rules to allow all traffic to and from the second subnet as well.
NOTE: Given that 10.0.1.0/24 is the other subnet behind the SonicWall on some VLAN or something. Make sure you put in the proper firewall rules to allow all traffic to and from the second subnet as well.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
The Linux server
On this side (or branch office) is the Linux server as the router and providing Internet for the following network.
 NOTE: The actual setup of a Linux machine to act as a network router is out of the scope of this document.
NOTE: The actual setup of a Linux machine to act as a network router is out of the scope of this document.
- WAN IP: 209.14.212.52
- Internal subnet: 192.168.0.0/24
- IP of Linux server: 192.168.0.1
- WAN Iface of Linux server: eth0
The SonicWall device
On this side (or branch office) is the SonicWall device serving as the router and providing Internet for the following network.
- WAN IP: 24.252.13.9
- Internal subnet: 10.0.0.0/24
- IP of SonicWall': 10.0.0.1
Openswan side configuration
- Kernel requirements (If you built your own kernel you're going to either have to include the following as modules or build them in)
- Transformation user configuration interface
- PF_KEY sockets
- IP: AH transformations
- IP: ESP transformations
- IP: IPComp transformations
- IP: IPsec tunnel mode
- Usually these are found under Networking | Network Options.
 NOTE: If you have not built your own kernel, chances are these are already built in.
NOTE: If you have not built your own kernel, chances are these are already built in.
Openswan config There are two configuration files you need to pay attention to:
- /etc/IPSec.conf version 2.0
config setup NOTE: Having this option off caused issues.
NOTE: Having this option off caused issues.nat_traversal=yesoe=offprotostack=netkeyfragicmp=noconn SonicWall - This is where you define your connexion to the SonicWall.
- You do not have to call it "SonicWall" you can call it what you wish.
left=209.14.212.52leftsourceip=192.168.0.1leftsubnet=192.168.0.0/24leftid=209.14.212.52right=24.252.13.9rightid=24.252.13.9keyingtries=0pfs=noaggrmode=yesauth=espesp=3des-sha1ike=3des-sha1authby=secretkeyexchange=ikerightsubnet=10.0.0.0/24 NOTE:This allows the VPN to come up automatically when openswan starts.
NOTE:This allows the VPN to come up automatically when openswan starts.
auto=start
 TIP: You'll notice the rightid and the leftid above. These are what helps identify the connexion when the Openswan and the SonicWall try to talk. Usually SonicWalls want this value set to a SonicWall Identifier. Well, if you haven't noticed by now your Openswan/Linux box won't have an identifier for itself. So we use the IP instead. SonicWalls will also accept that option.
TIP: You'll notice the rightid and the leftid above. These are what helps identify the connexion when the Openswan and the SonicWall try to talk. Usually SonicWalls want this value set to a SonicWall Identifier. Well, if you haven't noticed by now your Openswan/Linux box won't have an identifier for itself. So we use the IP instead. SonicWalls will also accept that option.
- /etc/IPSec.secrets
209.14.212.52 24.252.13.9 : PSK "secretpass" NOTE: In the IPSec.secrets file make sure the IPs are correct. This will be what gives the authentication password for the VPN. If your IPs change and you have to change them in the IPSec.conf file, make sure to remember to change them here to. Otherwise you'll have errors and it won't establish a connexion.
NOTE: In the IPSec.secrets file make sure the IPs are correct. This will be what gives the authentication password for the VPN. If your IPs change and you have to change them in the IPSec.conf file, make sure to remember to change them here to. Otherwise you'll have errors and it won't establish a connexion.
iptables config
 CAUTION: If you're doing masquerading and you have other Nat rules set up in iptables it will interfere with your VPN traffic. So, you will have to set rules to allow all traffic unaffected for your VPN subnet.
CAUTION: If you're doing masquerading and you have other Nat rules set up in iptables it will interfere with your VPN traffic. So, you will have to set rules to allow all traffic unaffected for your VPN subnet.
- IPSec ports for opening
iptables -A INPUT -p ah -j ACCEPTiptables -A INPUT -p esp -j ACCEPTiptables -A INPUT -p udp -i eth0 --dport 500 -j ACCEPTiptables -A INPUT -p udp -i eth0 --dport 4500 -j ACCEPTiptables -A INPUT -p udp -i eth0 --dport 50:58 -j ACCEPTiptables -A INPUT -p TCP -i eth0 --dport 50:58 -j ACCEPT
- Allow all traffic from our SonicWall side of the VPN in
iptables -A INPUT -j ACCEPT --source 10.0.0.0/255.255.255.0 - Put a rule in to cancel out any MASQ rules that might try to take effect
iptables -t Nat -A POSTROUTING -j ACCEPT --destination 10.0.0.0/255.255.255.0 - Cancel out any forward rules that might be trying to take effect
iptables -t Nat -A PREROUTING -j ACCEPT --source 10.0.0.0/255.255.255.0
The point of the above commands is that they are placed before any other firewall rules take place that may interfere with traffic either bound to or coming from the SonicWall VPN network. In a default scenario without any restrictions we want to leave those packets untouched. If you find your VPN traffic is still being interfered with, check your other chains to see that they aren't mangling your VPN traffic.
If you need to insert the rule above another rule, for example above a MASQ rule, use the -I command instead.
 EXAMPLE:
EXAMPLE: iptables -t Nat -I POSTROUTING 1 -j ACCEPT --destination 10.0.0.0/255.255.255.0
To put the rule first in the chain.
SonicWall side configuration The screenshots below are from the web interface for the SonicWall NSA 2400.
- Go to the VPN lists to add another VPN (Usually VPN|Settings on the menu).
- Add a new VPN connexion (the Add button).
General Tab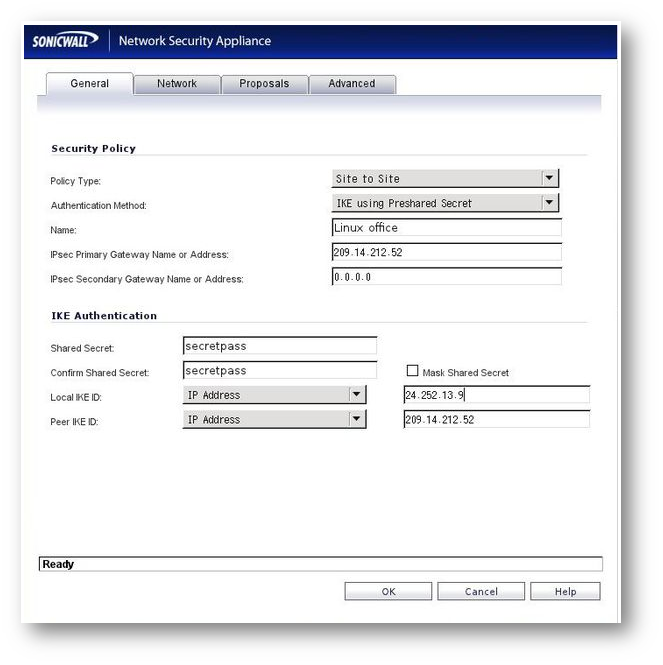
Network Tab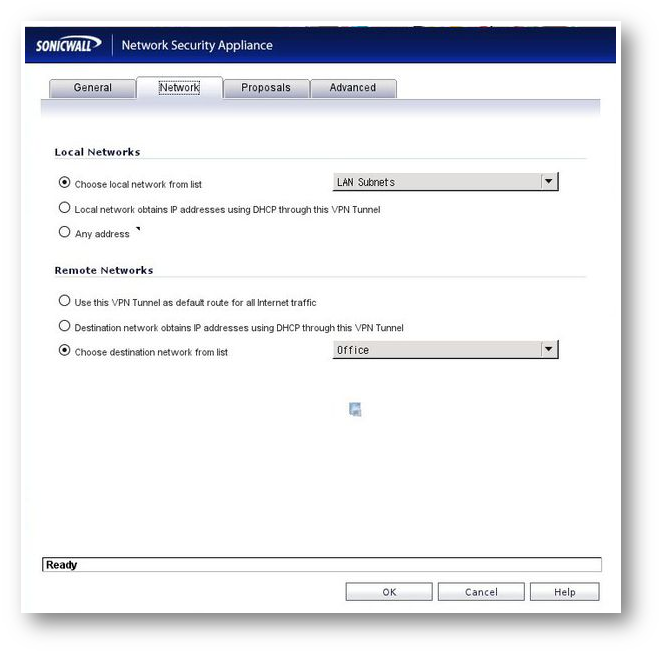
 NOTE: For the above you'll need to configure address objects for the Local Networks and Remote Networks. When configuring the Remote Networks address object make sure it's the same subnet as the Left (or Openswan/Linux) side. Otherwise you will get errors.
NOTE: For the above you'll need to configure address objects for the Local Networks and Remote Networks. When configuring the Remote Networks address object make sure it's the same subnet as the Left (or Openswan/Linux) side. Otherwise you will get errors.
Proposals Tab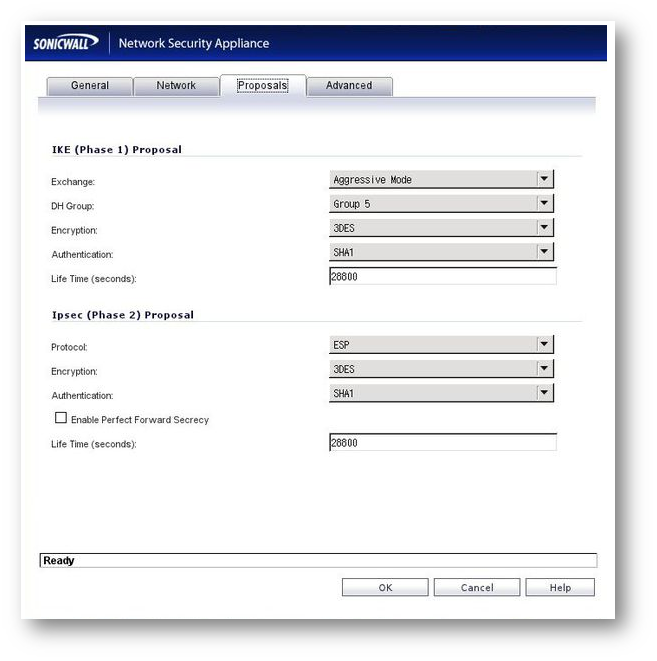
Advanced Tab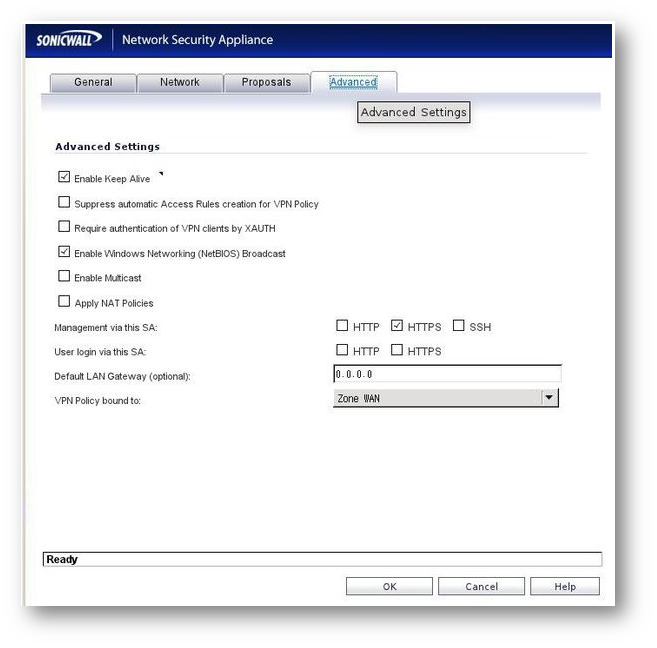
 NOTE: The XAUTH option was checked in one of the articles I did see. However, this will make Openswan prompt you for another password and you won't be able to establish the VPN without it. Also, if you do not want SMB traffic to pass through the VPN Uncheck the NetBIOS flag.
NOTE: The XAUTH option was checked in one of the articles I did see. However, this will make Openswan prompt you for another password and you won't be able to establish the VPN without it. Also, if you do not want SMB traffic to pass through the VPN Uncheck the NetBIOS flag. - Click OK.
Bringing up the VPN
- On the SonicWall side, in the VPN settings where it lists the VPN just make sure the Enable checkbox is checked.
- On the Openswan/Linux side, run the command.
/etc/init.d/IPSec restart - If everything was done correctly you should see the little green dot on the SonicWall's VPN list indicating that everything is okay.
- Some ping tests should show that you have connectivity across the VPN.
Debugging
- Check the system log file and grep out messages from pluto. This will give you a real time update on the progress of your IPSec connexions.
- Check the SonicWall log system.
- Make sure none of your iptables rules are blocking VPN traffic.
Multiple subnets across the VPN
- So your SonicWall side has multiple subnets that you want to be able to reach. This is easy with Openswan. On your SonicWall side of course configure the proper Address Objects. Then on your Openswan config do the following.
- /etc/IPSec.conf version 2.0
config setupnat_traversal=yesoe=offprotostack=netkeyfragicmp=noconn SonicWallleft=209.14.212.52leftsourceip=192.168.0.1leftsubnet=192.168.0.0/24leftid=209.14.212.52right=24.252.13.9rightid=24.252.13.9keyingtries=0pfs=noaggrmode=yesauth=espesp=3des-sha1ike=3des-sha1authby=secretkeyexchange=ikeconn SonicWall-0network# Include the other configalso=SonicWall# Our default subnetrightsubnet=10.0.0.0/24# Make sure this one autostartsauto=startconn SonicWall-1networkalso=SonicWallrightsubnet=10.0.1.0/24auto=start NOTE: Given that 10.0.1.0/24 is the other subnet behind the SonicWall on some VLAN or something. Make sure you put in the proper firewall rules to allow all traffic to and from the second subnet as well.
NOTE: Given that 10.0.1.0/24 is the other subnet behind the SonicWall on some VLAN or something. Make sure you put in the proper firewall rules to allow all traffic to and from the second subnet as well.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > NSa Series > VPN






 YES
YES NO
NO