-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I configure a PortShield interface (LAN,DMZ,etc.) working in transparent mode?



Description
Transparent Mode works by defining a Transparent Range which will retain their original source IP address (will not be NAT'd) when egress from the WAN interface. While, a PortShield interface is a virtual interface with a set of ports assigned to it. These interfaces in the PortShield group will shared the same network subnet.
PortShield interface can work in two modes (Static and Transparent). This article covers the feature how to configure a PortShield interface in transparent mode.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
We are going to configure PortShield for Transparent mode.
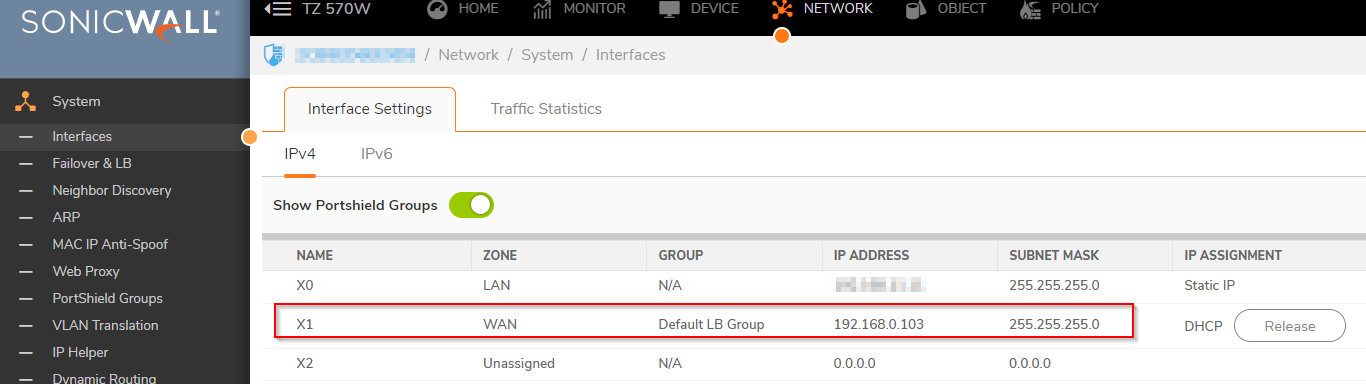
- Assume, We have X1 interface configured as WAN with IP 1.1.1.2/24 IP subnet.
- We need to configure X2 and X3interfaces in a PortShield group with a transparent IP range (1.1.1.3 to 1.1.1.5).
- We need to connect SMTP server with IP as 1.1.1.3/24 to interface X2, two servers (one FTP server with IP 1.1.1.4/24 and one Web server with IP 1.1.1.5/24) connected to interface X3.
To configure the PortShield interface in transparent mode, please complete the following steps.
Create Address Object for DMZ Range:
- Login to your SonicWall management page and click Object tab on top of the page.
- Navigate to Match Object | Address page. On right Side, Click Address objects tab and select View as Custom.
- Click Add button under Address Objects, to get Add Address Object Window.
- Create an address object as below.
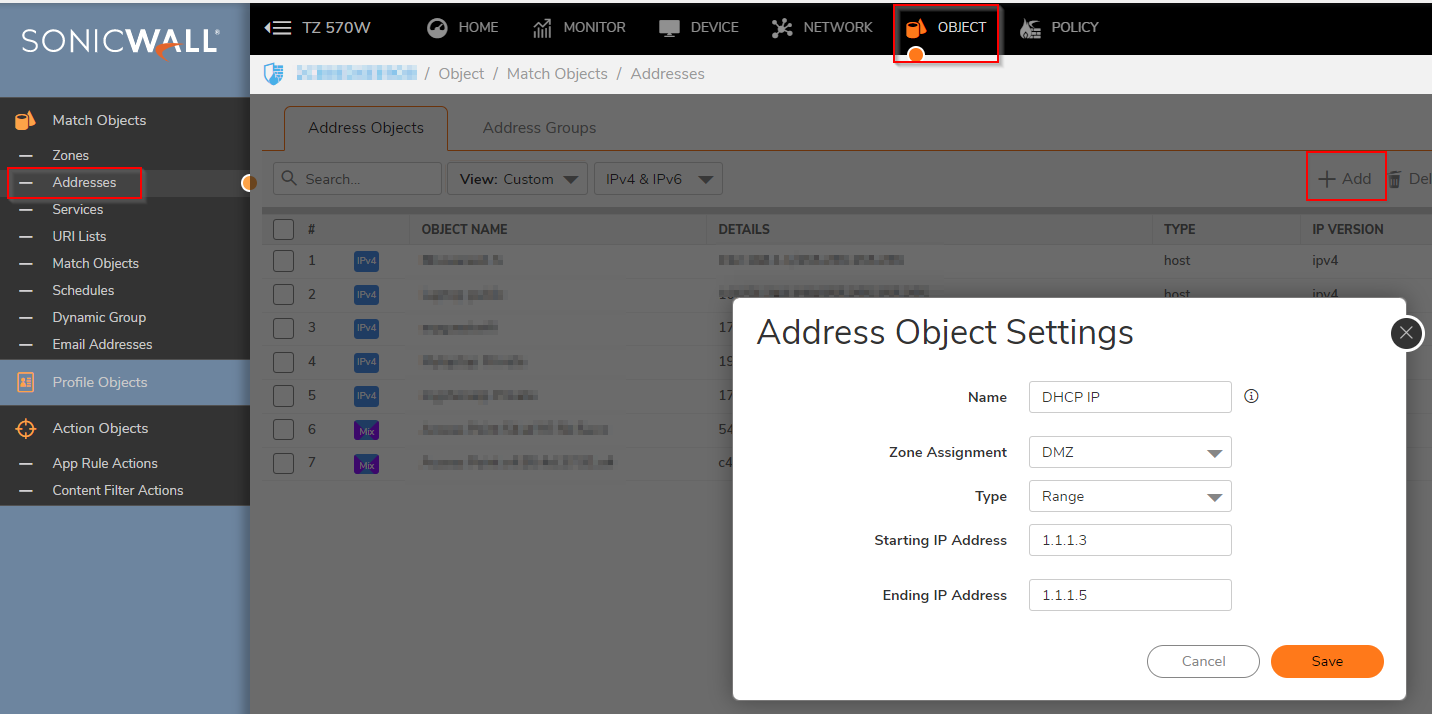
 NOTE: the address range must be within the WAN zone and must not include the WAN interface and WAN gateway IP address.
NOTE: the address range must be within the WAN zone and must not include the WAN interface and WAN gateway IP address.
Configure Transparent Mode:
 NOTE: WAN interface IP address must be static assigned when configuring transparent mode
NOTE: WAN interface IP address must be static assigned when configuring transparent mode
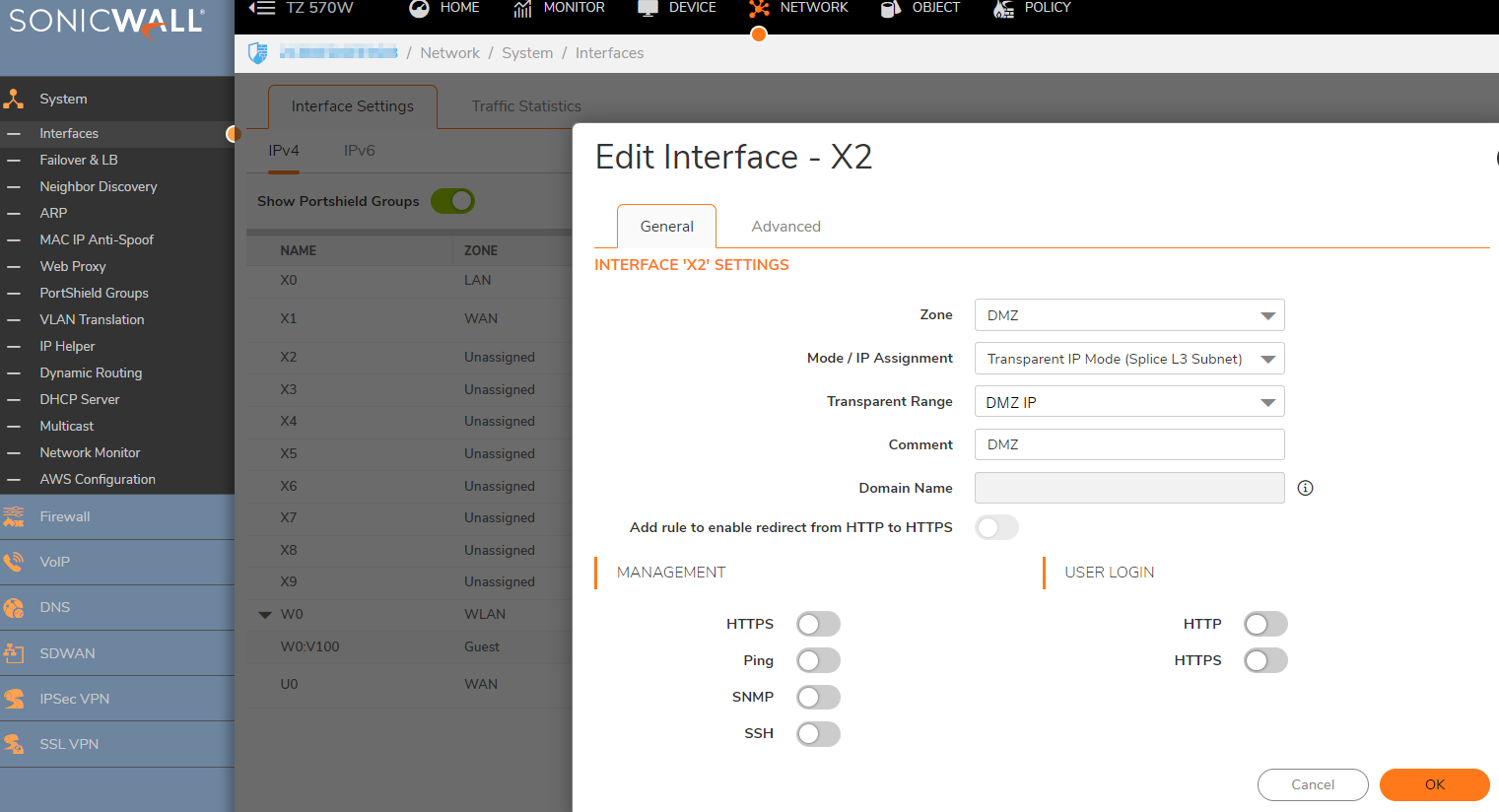
- Login to your SonicWall management page and click Network tab on top of the page.
- Navigate to System | Interfaces page. configure X2 interface as below.
- Zone: DMZ
- Mode /IP Assignment: Transparent IP Mode (Splice L3 Subnet).
- Transparent Range: DMZ IP (Created in Step 1).
- Comment: DMZ (Any useful information for the interface)
- Click OK.
Configure PortShield Mode:
1. Login to your SonicWall management page and click Manage tab on top of the page.
2. Navigate to Network | Interfaces page. configure X3 interface as below.
- Zone: DMZ.
- Mode /IP Assignment: PortShield Switch Mode.
- PortShield to: X2
- Click OK.

 NOTE: PortShield can also be configured through page Network | PortShield Groups.
NOTE: PortShield can also be configured through page Network | PortShield Groups.
Configuring the servers connected to the PortShield interfaces X2 and X3. - The servers connected to the interfaces X2 and X3 should be configured with the IP addresses within the Transparent Range. The default gateway could either be the upstream ISP router address or the SonicWall WAN interface IP. Once the servers are configured appropriately they will be able to go online with the IP address assigned to them without being NAT'ed.
- At the moment, if you need to reach the servers with the IP addresses assigned to them from the WAN side of SonicWall.
Access Rule from WAN to DMZ
- Login to your SonicWall management page and click Policy tab on top of the page
- Navigate to Rules and Policies| Access Rules.
- Modify the default access rule from WAN to DMZ zone as below to allow all traffic.

Check the configuration from the WAN side.
- Ping Server 3.3.3.3 connected to X9.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
We are going to configure PortShield for Transparent mode.
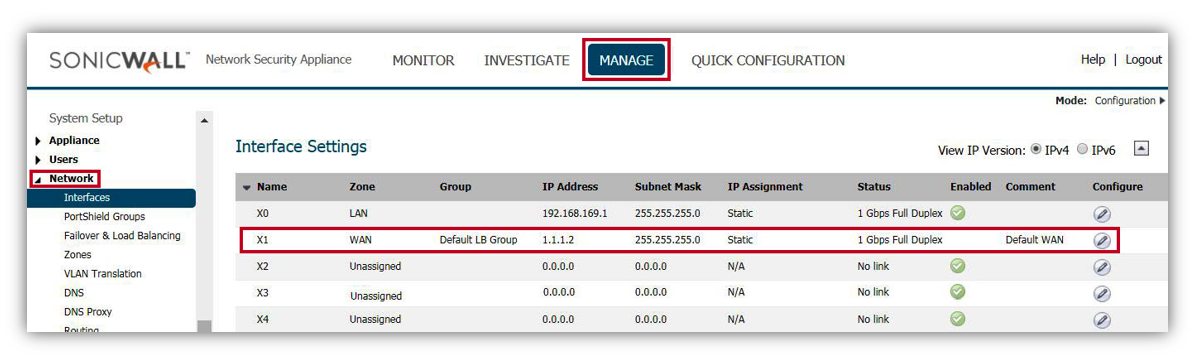
- Assume, We have X1 interface configured as WAN with IP 1.1.1.2/24 IP subnet.
- We need to configure X2 and X3interfaces in a PortShield group with a transparent IP range (1.1.1.3 to 1.1.1.5).
- We need to connect SMTP server with IP as 1.1.1.3/24 to interface X2, two servers (one FTP server with IP 1.1.1.4/24 and one Web server with IP 1.1.1.5/24) connected to interface X3.
To configure the PortShield interface in transparent mode, please complete the following steps.
Create Address Object for DMZ Range:
- Login to your SonicWall management page and click Manage tab on top of the page.
- Navigate to Objects | Address Objects page. On right Side, Click Address objects tab and select View as Custom.
- Click Add button under Address Objects, to get Add Address Object Window.
- Create an address object as below.
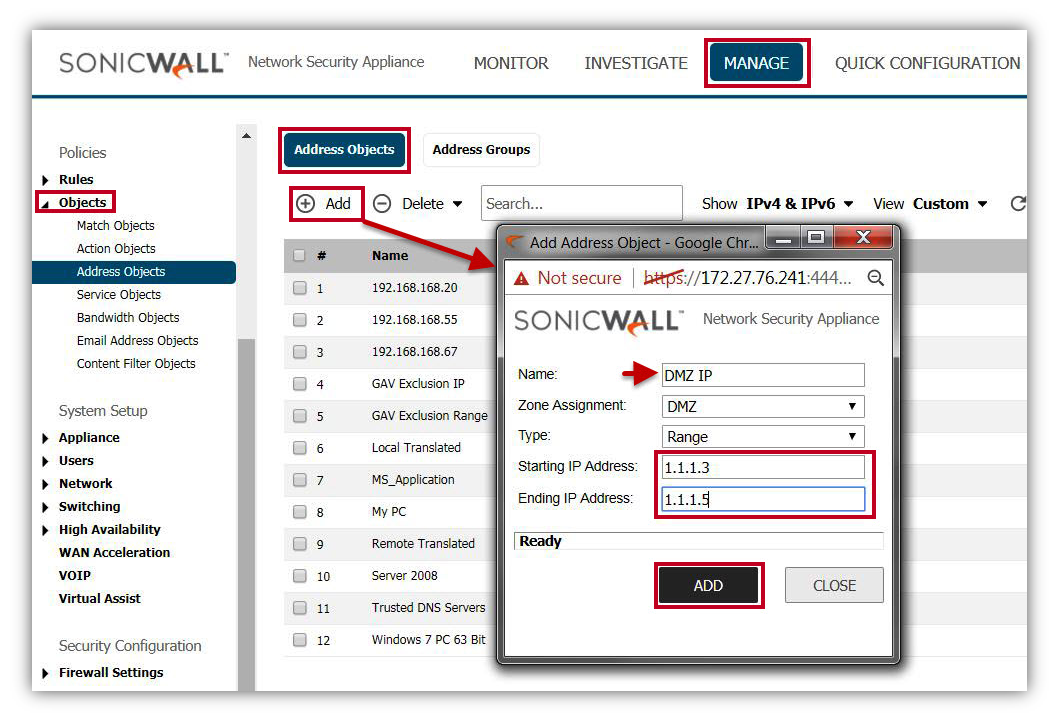
 NOTE: the address range must be within the WAN zone and must not include the WAN interface and WAN gateway IP address.
NOTE: the address range must be within the WAN zone and must not include the WAN interface and WAN gateway IP address.
Configure Transparent Mode:
- Login to your SonicWall management page and click Manage tab on top of the page.
- Navigate to Network | Interfaces page. configure X2 interface as below.
- Zone: DMZ.
- Mode /IP Assignment: Transparent IP Mode (Splice L3 Subnet).
- Transparent Range: DMZ IP (Created in Step 1).
- Comment: DMZ (Any useful information for the interface)
- Click OK.

 NOTE: WAN interface IP address must be static assigned when configuring transparent mode.
NOTE: WAN interface IP address must be static assigned when configuring transparent mode.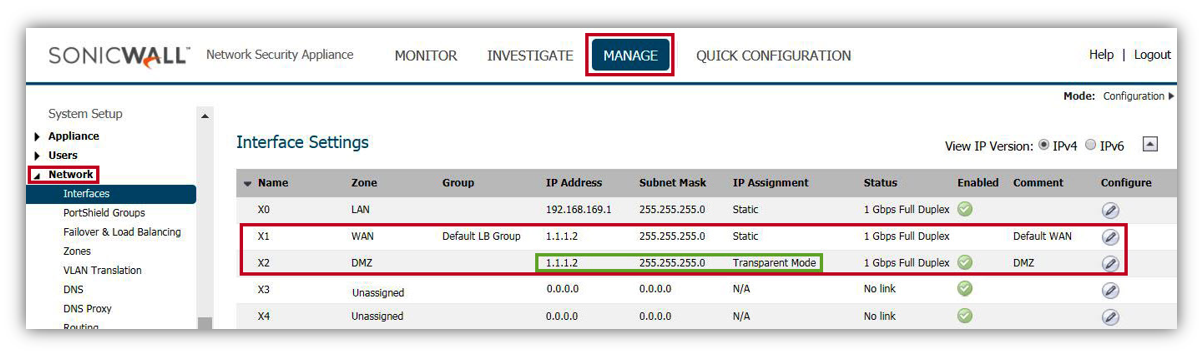
Configure PortShield Mode:
- Login to your SonicWall management page and click Manage tab on top of the page.
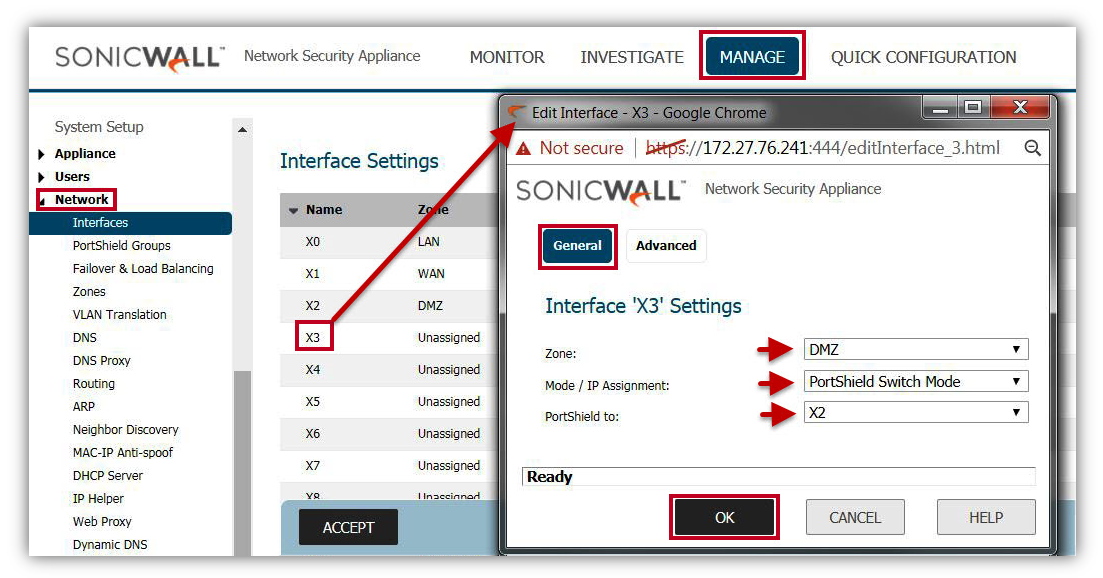
- Navigate to Network | Interfaces page. configure X2 interface as below.
- Zone: DMZ.
- Mode /IP Assignment: PortShield Switch Mode.
- PortShield to: X2
- Click OK.
 NOTE: PortShield can also be configured through page Network | PortShield Groups.
NOTE: PortShield can also be configured through page Network | PortShield Groups.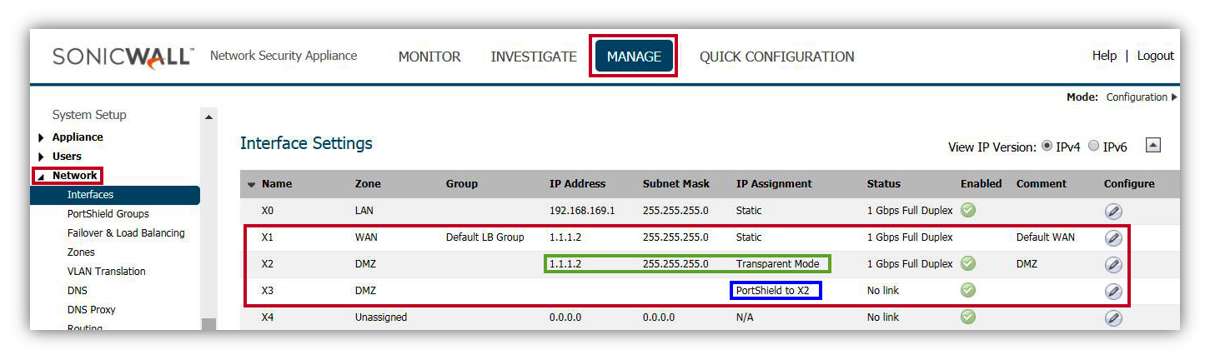
Configuring the servers connected to the PortShield interfaces X2 and X3.
- The servers connected to the interfaces X2and X3 should be configured with the IP addresses within the Transparent Range. The default gateway could either be the upstream ISP router address or the SonicWall WAN interface IP. Once the servers are configured appropriately they will be able to go online with the IP address assigned to them without being NAT'ed.

- At the moment, if you need to reach the servers with the IP addresses assigned to them from the WAN side of the SonicWall.
Access Rule from WAN to DMZ
- Login to your SonicWall management page and click Manage tab on top of the page
- Navigate to Rules| Access Rules.
2) Modify default access rule from WAN to DMZ zone as below to allow all traffic.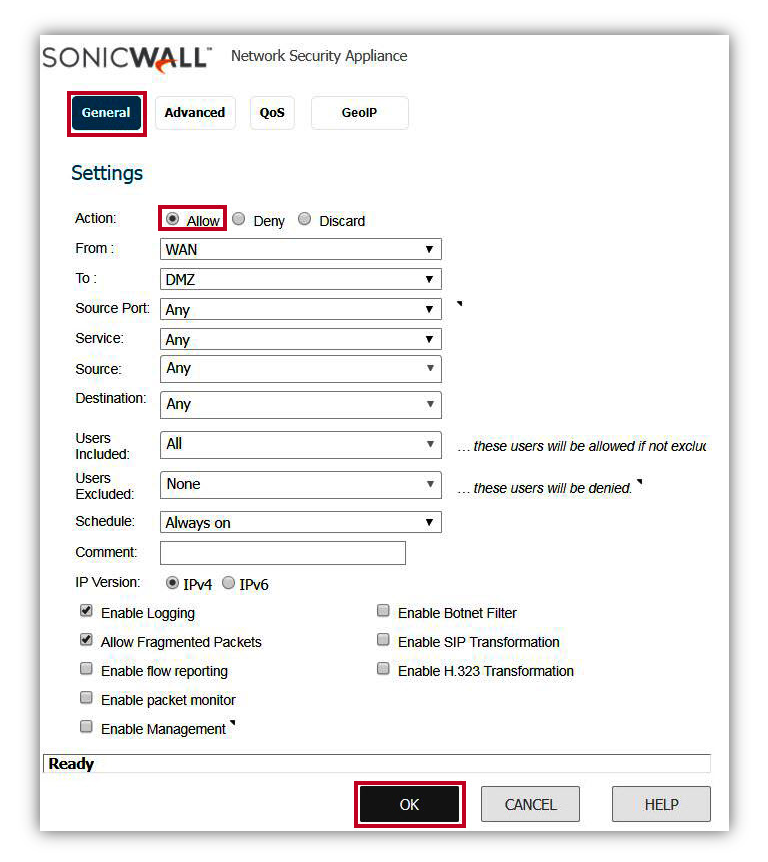
Check the configuration from the WAN side.
- Ping Server 3.3.3.3 connected to X10.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
We are going to configure PortShield for Transparent mode.
- Assume, We have X1 interface configured as WAN with IP 3.3.3.1/24 IP subnet.
- We need to configure X9 and X10 interfaces in a PortShield group with a transparent IP range (3.3.3.2 to 3.3.3.4).
- We need to connect SMTP server with IP as 3.3.3.2/24 to interface X9, two servers (one FTP server with IP 3.3.3.3/24 and one Web server with IP 3.3.3.4/24) connected to interface X10.
To configure the PortShield interface in transparent mode, please complete the following steps.
- Navigate to Network | Address Objects to create an address object (IP Range: 3.3.3.2 to 3.3.3.4) for transparent mode configure.
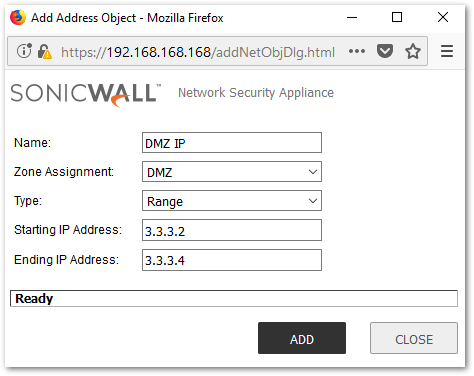
 NOTE: The address range must be within the WAN zone and must not include the WAN interface and WAN gateway IP address.
NOTE: The address range must be within the WAN zone and must not include the WAN interface and WAN gateway IP address. - Navigate to Network | Interfaces page, click Edit button of interface X9 and do the following configuration.
- Zone: DMZ.
- Mode /IP Assignment: Transparent IP Mode (Splice L3 Subnet).
- Transparent Range: DMZ IP (Created in Step 1).
- Comment: DMZ (Any useful information for the interface)

 NOTE: WAN interface IP address must be static assigned when configuring transparent mode.
NOTE: WAN interface IP address must be static assigned when configuring transparent mode.
- Navigate to Network | Interfaces page, click the Edit button of interface X10 and do the following configuration.
- Zone: DMZ.
- Mode /IP Assignment: PortShield Switch Mode.
- PortShield to: X9 ( interfaces in the same Zone will be displayed for selection)
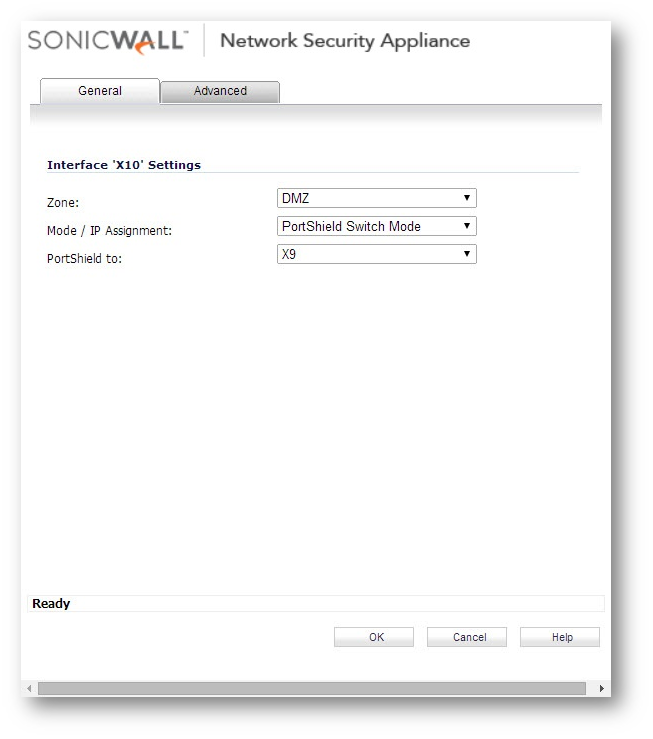
 NOTE: PortShield can also be configured through page Network | PortShield Groups.
NOTE: PortShield can also be configured through page Network | PortShield Groups. - Navigate to Network | Interfaces or Network | PortShield Group page to check the configuration.
 TIP: If you cannot see the PortShield interface , you can click the button Show PortShield Interfaces on the top left of Network | Interfaces page.
TIP: If you cannot see the PortShield interface , you can click the button Show PortShield Interfaces on the top left of Network | Interfaces page. - Configuring the servers connected to the PortShield interfaces X9 and X10. The servers connected to the interfaces X9 and X10 should be configured with the IP addresses within the Transparent Range. The default gateway could either be the upstream ISP router address or the SonicWall WAN interface IP. Once the servers are configured appropriately they will be able to go online with the IP address assigned to them without being NAT'ed.
At the moment, if you need to reach the servers with the IP addresses assigned to them from the WAN side of the SonicWall, please navigate to Firewall | Access Rules page.- Select radio button Matrix .
- Select from WAN to DMZ.
- Click Add button.

- Click OK.
- Select radio button Matrix .
- Check the configuration from the WAN side. Ping Server 3.3.3.3 connected to X10.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO