-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I block ports using firewall access rules?



Description
This article explains how to block specific ports using access rules on the SonicWall.
A lot of traffic on the Internet operates on well-known or static ports. Well-known ports are ports which have numbers that are pre-assigned to them by the Internet Assigned Numbers Authority (IANA). Some examples would be SSH (TCP port 22), tftp (UDP port 69), and http (TCP port 80). Ports are blocked to stop certain types of traffic.
 EXAMPLE: SSH, http, or tftp) from passing though the firewall.
EXAMPLE: SSH, http, or tftp) from passing though the firewall.
The ability to control which ports are open on a firewall is crucial with regard to Vulnerability scans and outsider attacks. SonicWall gives you options to Allow, Deny or Discard traffic coming in on different ports.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
User Datagram Protocol (UDP) - a connectionless protocol that, like TCP, runs on top of IP networks. Unlike TCP, UDP provides very few error recovery services, offering instead a direct way to send and receive datagrams over an IP network. UDP is used primarily for multimedia and streaming applications, and broadcasting messages over a network.
Transport Control Protocol (TCP) - enables two hosts to establish a connection and exchange streams of data. TCP guarantees delivery of data and also guarantees that packets will be delivered in the same order in which they were sent.
Deny vs. Discard Denying packets blocks the packet from going through the firewall, but also sends a packet back to the sending device notifying the sender that the packet was not allowed access through the SonicWall. Discard will black-hole the packet. This means the packet is silently discarded by the firewall, and a notification message is not sent.
This example explains how to block traffic coming going from LAN to WAN on TCP port 22 (SSH).
- Click Policy , navigate to Rules and Policies| Access Rules.
- Click ADD.
- Here, the service is SSH, source is LAN Subnets, and destination is Any as we would like to block all SSH traffic going from the LAN to the WAN.
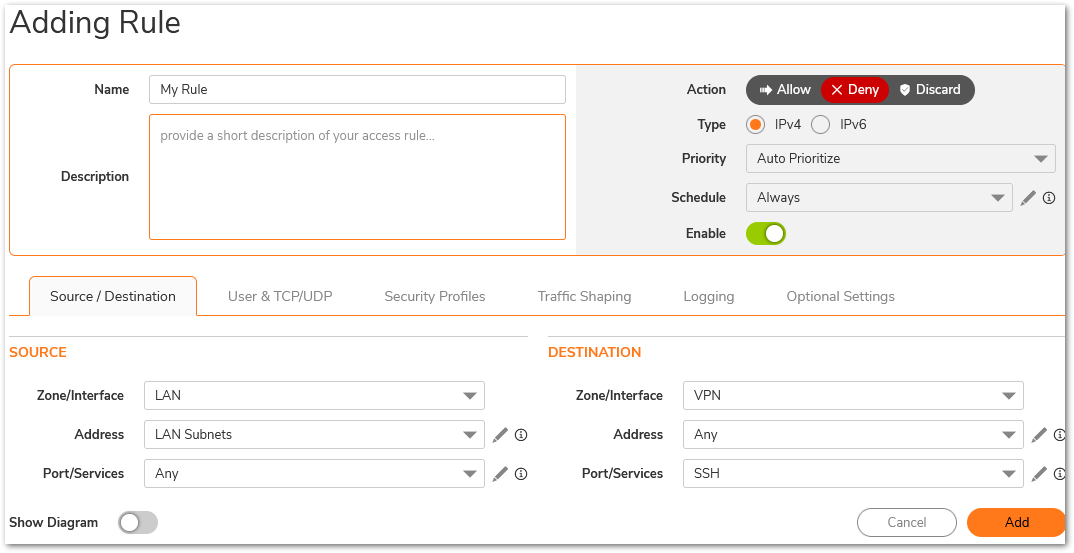
NOTE: Ensure that the Deny rule that is created in this case, is prioritized higher than the Any-> Any Allow rule. By default, all traffic from LAN to WAN is allowed and this would defeat the purpose of the Deny Rule if given a higher priority.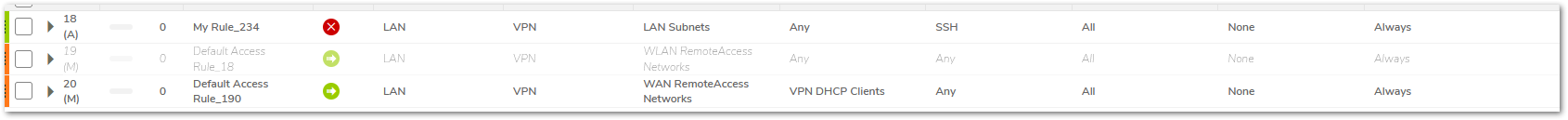
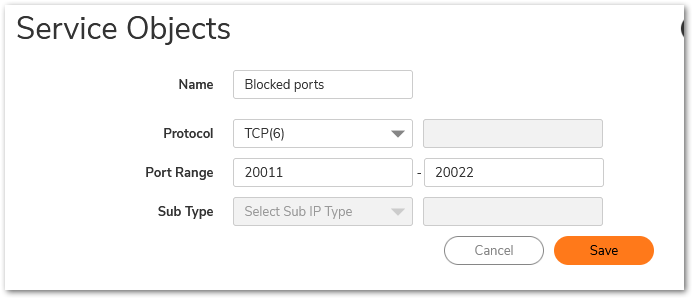
- The above example is for blocking a default port on the SonicWall. In case of a custom port, create the new service, Depending on the type of Protocol (TCP,UDP).
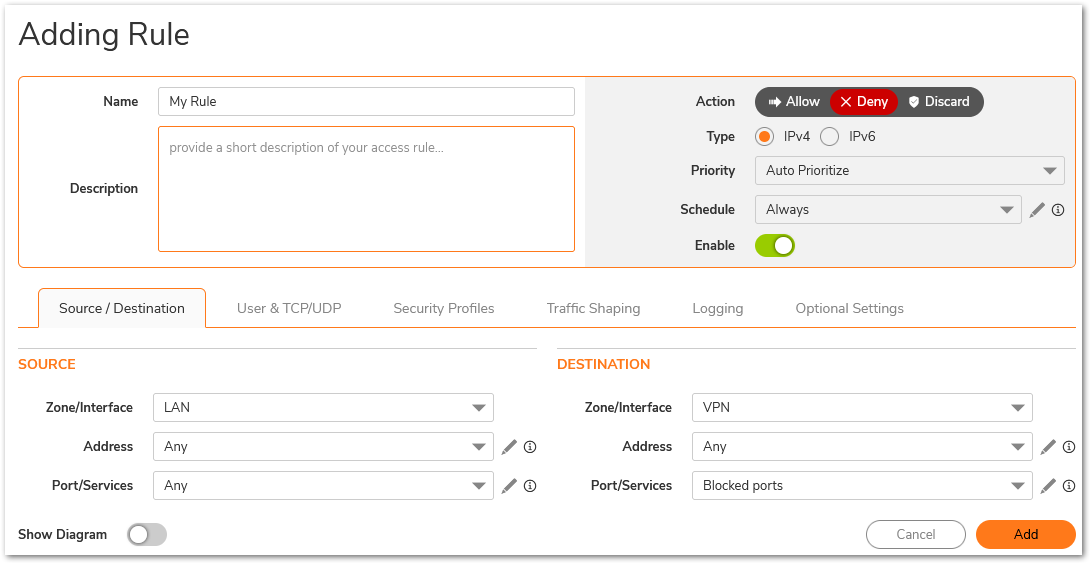
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Definitions
User Datagram Protocol (UDP) - a connectionless protocol that, like TCP, runs on top of IP networks. Unlike TCP, UDP provides very few error recovery services, offering instead a direct way to send and receive datagrams over an IP network. UDP is used primarily for multimedia and streaming applications, and broadcasting messages over a network.
Transport Control Protocol (TCP) - enables two hosts to establish a connection and exchange streams of data. TCP guarantees delivery of data and also guarantees that packets will be delivered in the same order in which they were sent.
Deny vs. Discard Denying packets blocks the packet from going through the firewall, but also sends a packet back to the sending device notifying the sender that the packet was not allowed access through the SonicWall. Discard will black-hole the packet. This means the packet is silently discarded by the firewall, and a notification message is not sent.
This example explains how to block traffic coming going from LAN to WAN on TCP port 22 (SSH).
- Click MANAGE , navigate to Policies | Rules | Access Rules.
- Click ADD.
- Here, the service is SSH, source is LAN Subnets, and destination is Any as we would like to block all SSH traffic going from the LAN to the WAN.
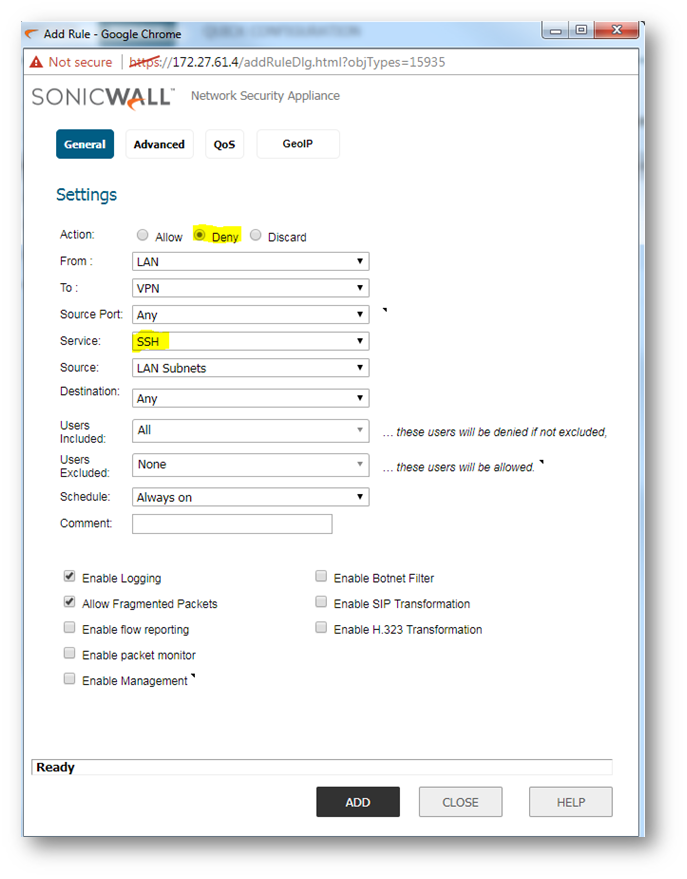
 NOTE: Ensure that the Deny rule that is created in this case, is prioritized higher than the Any-> Any Allow rule. By default, all traffic from LAN to WAN is allowed and this would defeat the purpose of the Deny Rule if given a higher priority.
NOTE: Ensure that the Deny rule that is created in this case, is prioritized higher than the Any-> Any Allow rule. By default, all traffic from LAN to WAN is allowed and this would defeat the purpose of the Deny Rule if given a higher priority.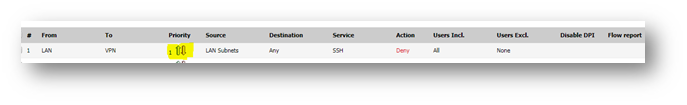
- The above example is for blocking a default port on the SonicWall. In case of a custom port, select the Create New Service option as shown.
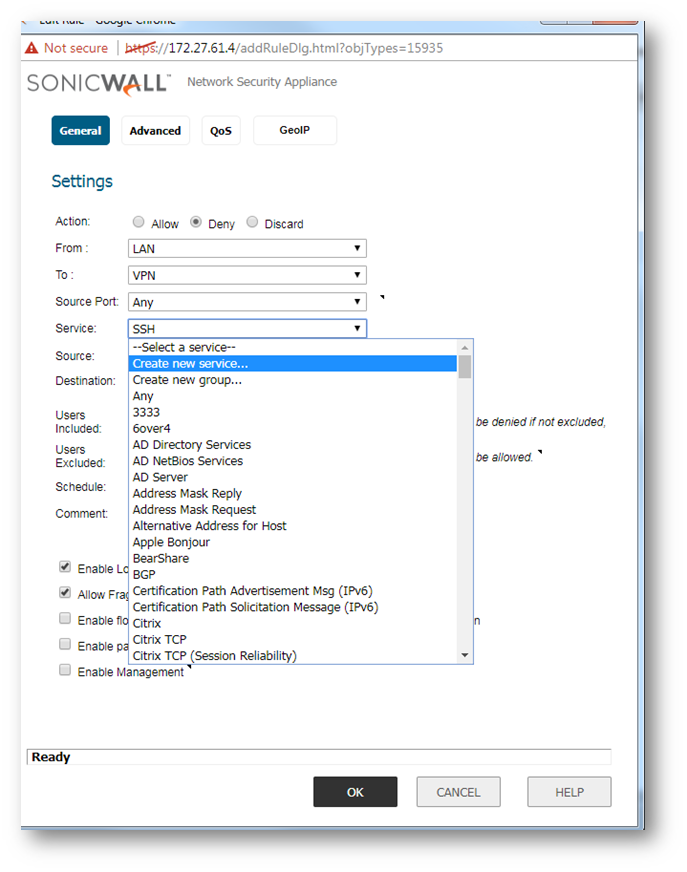
- Depending on the type of Protocol ( TCP,UDP) create the new service.
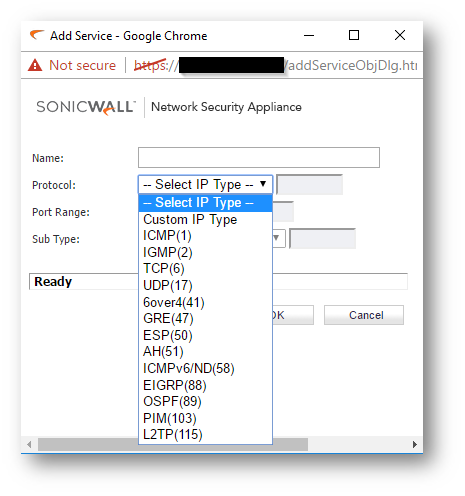
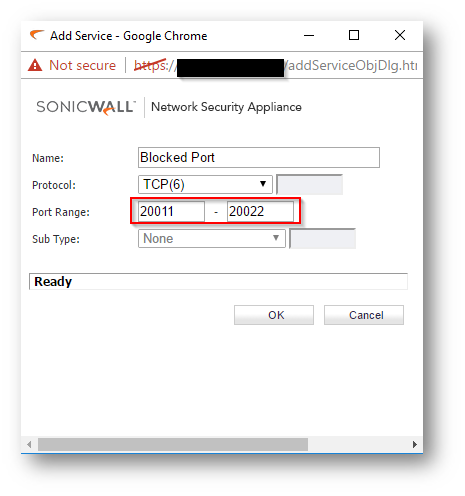
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Navigate to Firewall | Access Rules and select Add.
Here, the Service is SSH, source is LAN Subnets, and destination is Any as we would like to block all SSH traffic going from the LAN to the WAN.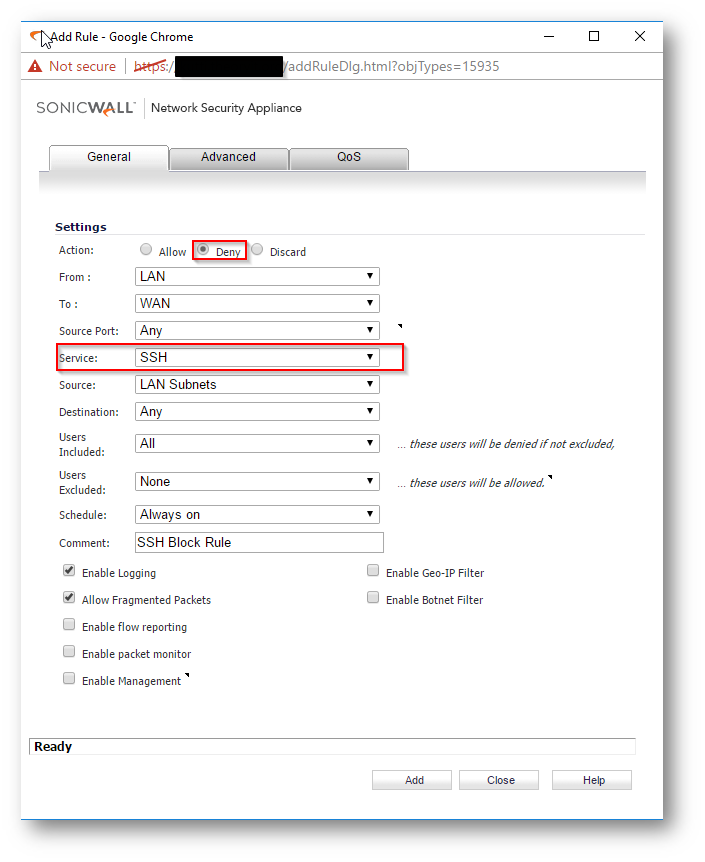
 NOTE:Ensure that the Deny rule that is created in this case, is prioritized higher than the Any-> Any Allow rule. By default, all traffic from LAN to WAN is allowed and this would defeat the purpose of the Deny Rule if given a higher priority.
NOTE:Ensure that the Deny rule that is created in this case, is prioritized higher than the Any-> Any Allow rule. By default, all traffic from LAN to WAN is allowed and this would defeat the purpose of the Deny Rule if given a higher priority.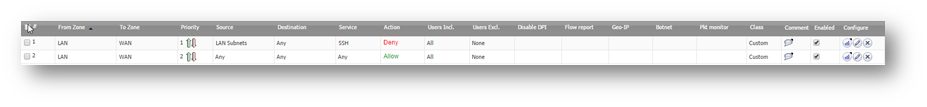
- The above example is for blocking a default port on the SonicWall. In case of a custom port, select the Create New Service option as shown.
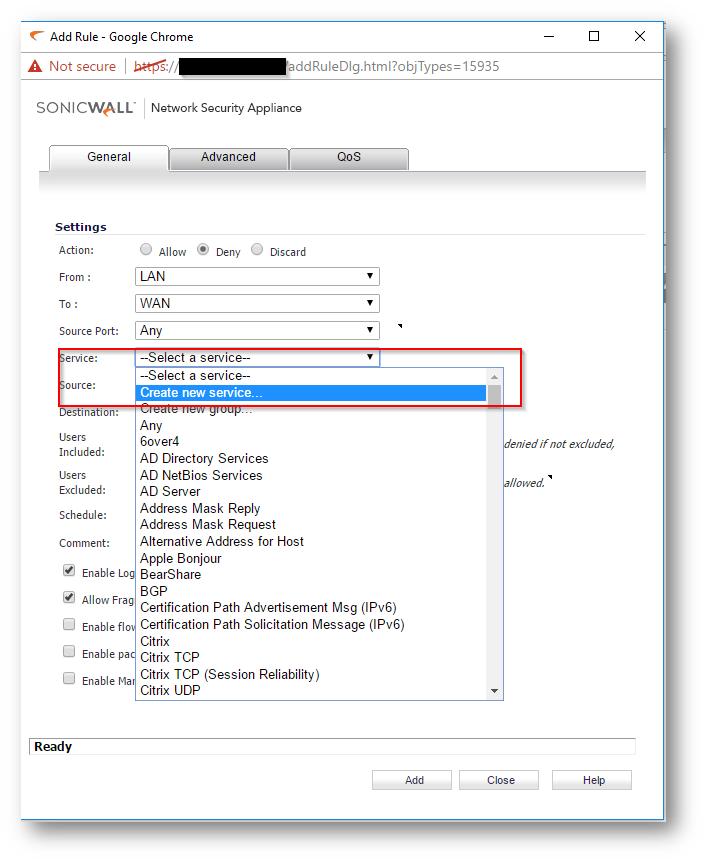
- Depending on the type of Protocol ( TCP,UDP) create the new service.


Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Networking
- Firewalls > NSv Series > Networking
- Firewalls > TZ Series > Networking






 YES
YES NO
NO