-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I block HTTPS websites in CFS 3.0?



Description
This article shows how to block HTTPS websites using CFS3.0 (SonicOS 6.2.5.3 or earlier).
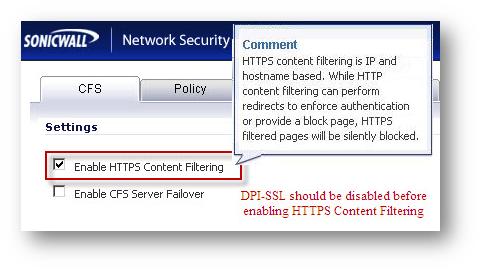
The earlier IP based HTTPS filtering filtered HTTPS traffic based on server IP addresses. The enhancement described here is applicable to both IP addresses and hostnames for rating HTTPS websites. HTTPS Content Filtering is applicable for the domains entered in the Custom List and the Match Objects entries in Allowed/Forbidden List under Firewall | Match Objects page. In other words, when Enable HTTPS Content Filtering is checked under CFS | Configure | CFS window , it is a global CFS setting applicable to the following:
- Allow Domains
- Forbidden Domains
- Keyword Blocking
- App Rules > CFS Category List
- App Rules > CFS Allowed/Forbidden List
Hostnames are obtained in two ways:
- Examine SSL Client Hello message and if it supports SSL server name extension, it will have hostname included in the SSL Client Hello. This hostname is used to get rating information.
- Another method is to examine Server Hello messages to get certificate Common Name (CN) from the certificate and use the same to get rating information.
 EXAMPLE: To blockGmail.com, addmail.google.com in theForbidden Domainsbox. This would block any HTTP host with mail.google.com in the URL. Further, if using HTTPS, CFS will examine the Server Extensions field in the Client Hello message and/or the CN in the Server Hello message and block the page if it matches google.com. In the case of Gmail.com the CN is www.google.com and will be blocked by CFS. The downside of this would be that any Google services using that CN would also be blocked.
EXAMPLE: To blockGmail.com, addmail.google.com in theForbidden Domainsbox. This would block any HTTP host with mail.google.com in the URL. Further, if using HTTPS, CFS will examine the Server Extensions field in the Client Hello message and/or the CN in the Server Hello message and block the page if it matches google.com. In the case of Gmail.com the CN is www.google.com and will be blocked by CFS. The downside of this would be that any Google services using that CN would also be blocked.
Resolution
Enabling HTTPS Content Filter Globally
- Login to the SonicWall management GUI
- Navigate to Security Services | Content Filter page.
- Click Configure under Content Filter Type with SonicWall CFS selected.
- Check the box Enable HTTPS Content Filtering.
- Click OK.
Adding Allow/Forbidden Custom List in CFS via Users and Zone Screens
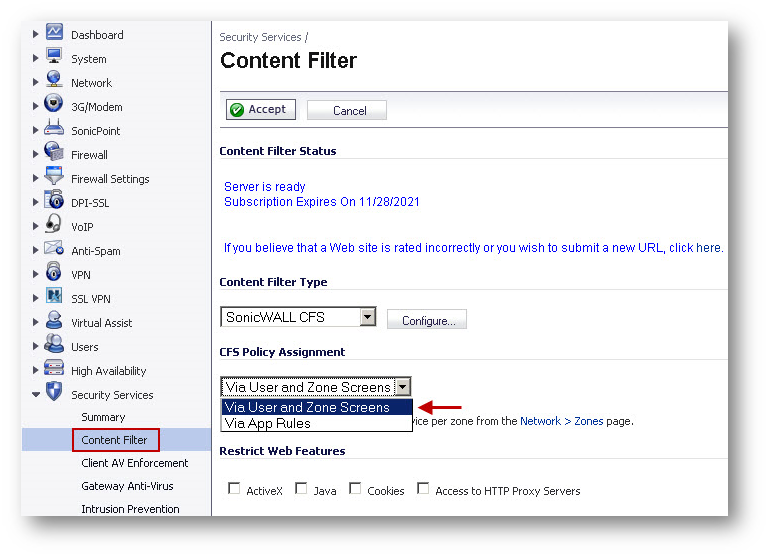
- Select Via User and Zone Screens under CFS Policy Assignment.
- Click Accept.
- Click Configure under Content Filter Type with SonicWall CFS selected.
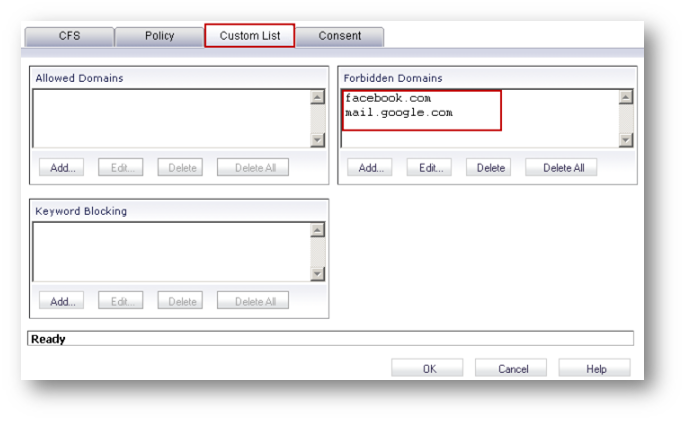
- Click Custom List tab.
- Click Add under Forbidden Domains and enter facebook.com and mail.google.com.
- Click OK.
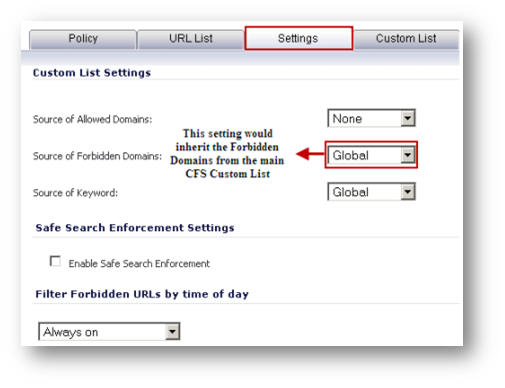
Configuring Custom CFS Policies to inherit the Allow/Forbidden Custom List.
What has been entered under the forbidden domains is automatically applicable to the default policy. To enforce the same on custom CFS policies their Custom List Settings needs to be manually set to Global.
- Edit the custom CFS policy.
- Click Settings tab.
- Set the Source of Forbidden Domains to Global.
- Click OK .
Adding Allow/Forbidden Custom List to CFS using App Rules
- On the Security Services | Content Filter page, select Via App Rules under CFS Policy Assignment.
- Click Accept .
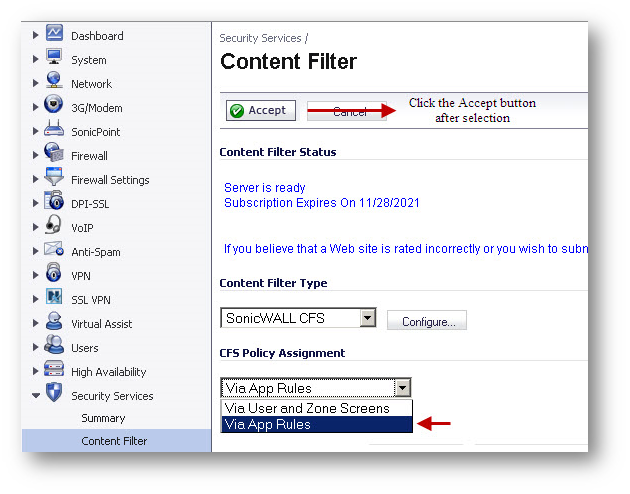
Match Objects
- Navigate to Firewall | Match Objects.
- Click Add New Match Object.
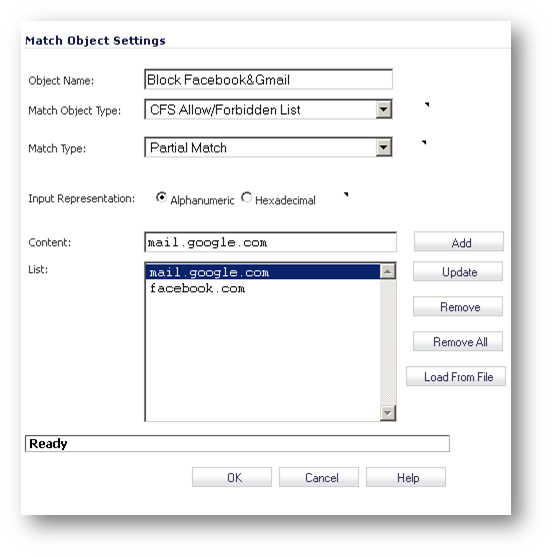
To create a custom list of allowed or forbidden domains, select CFS Allow/Forbidden List under Match Object Type. You could also load the allow/block list from a file containing the name of the domains. Each entry in the file should be separated by a line. The maximum size of the file is 8192 bytes.
Unlike CFS via Users and Zones, Custom List Objects (as above) cannot be used individually in an App Rule. It can only be used with a CFS Category List Object (see below): 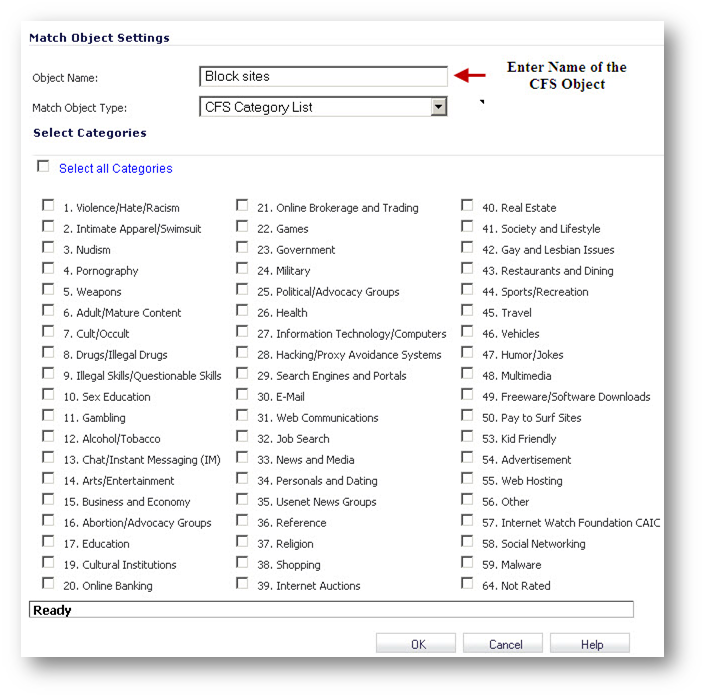
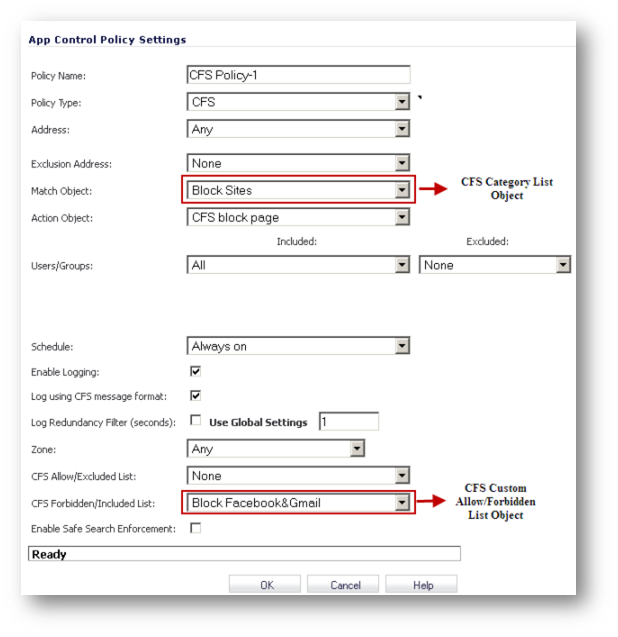
App Rules
- Navigate to the Firewall | App Rules page.
- Check the box under Enable App Rules.
- Click Add New Policy and create the following App Rule.
Log Messages
When SonicWall CFS blocks HTTPS websites users will not see a blocked page only a connection-reset page. 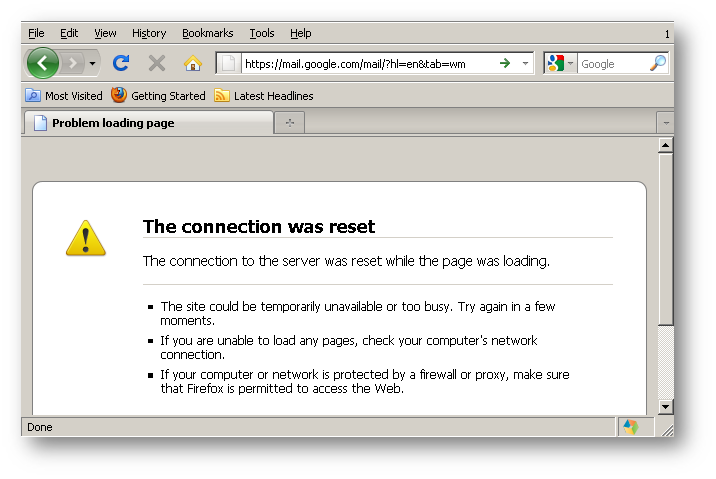
However the following messages will appear in the logs: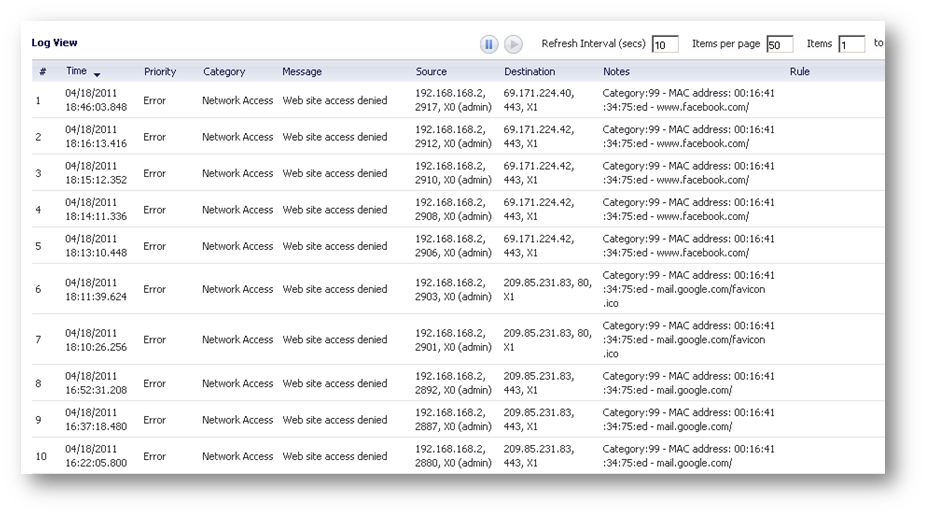
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Content Filtering Service
- Firewalls > TZ Series > Content Filtering Service
- Firewalls > NSv Series > Content Filtering Service






 YES
YES NO
NO