-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
GVC stuck on acquiring IP for some users



Description
GVC is stuck on acquiring IP for some users. No IP is leased.
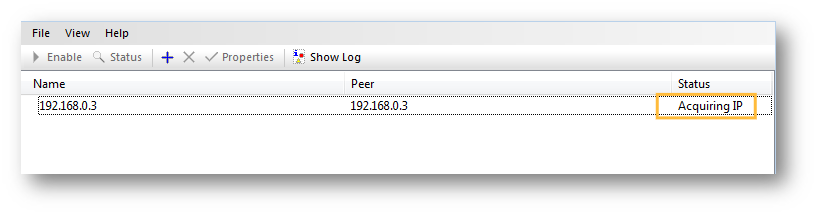
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
If you are using the SonicWall’s internal DHCP server
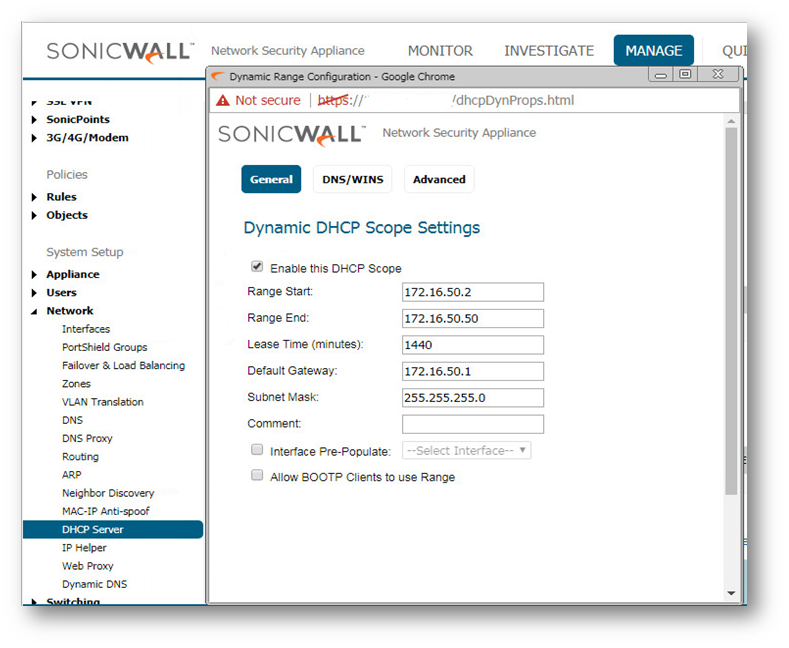
- Check if the DHCP server has a range big enough to accommodate all clients. For the below example I have given 19 leases for my 15 users.
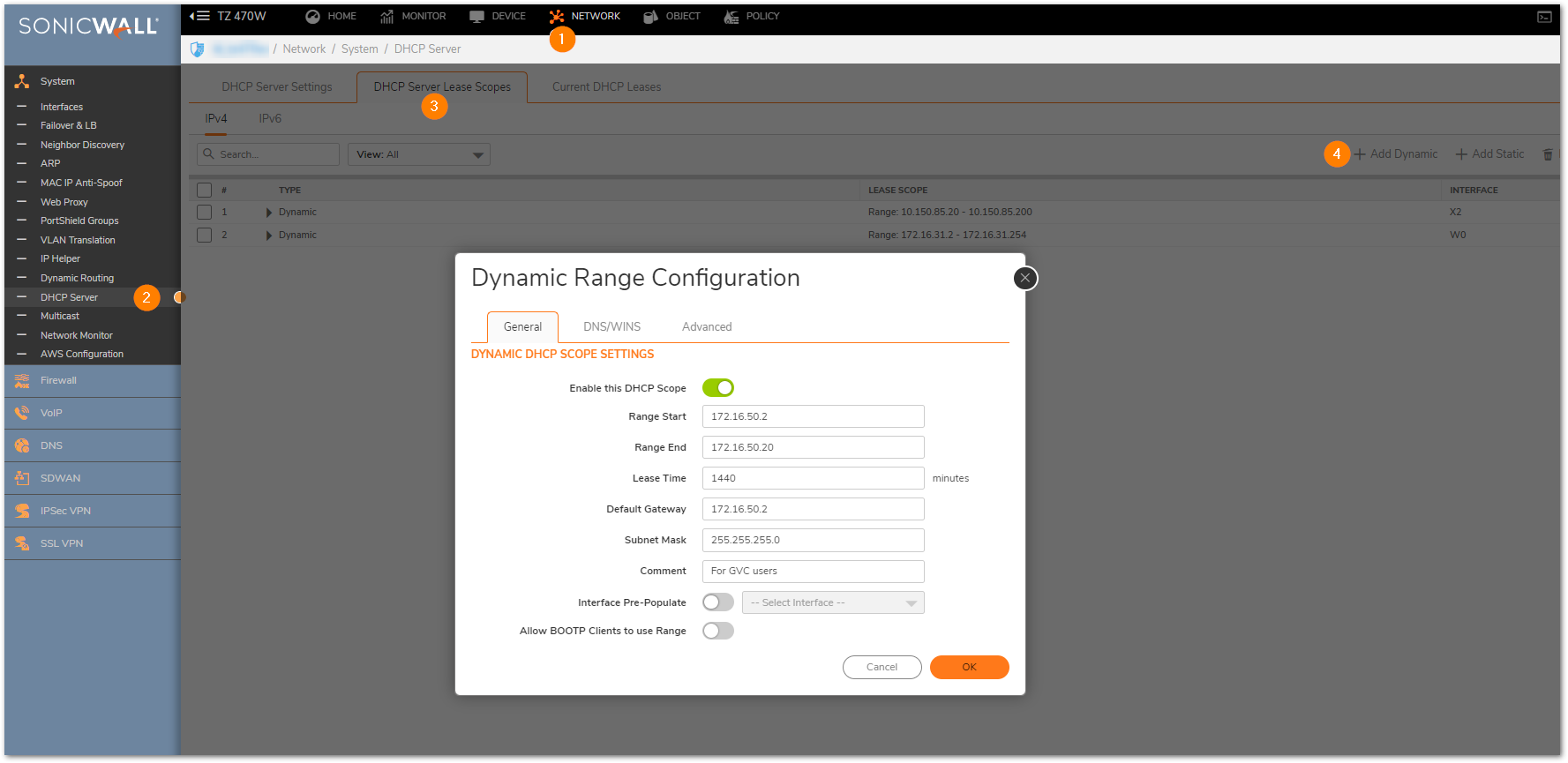
If you’re using a Windows DHCP server:
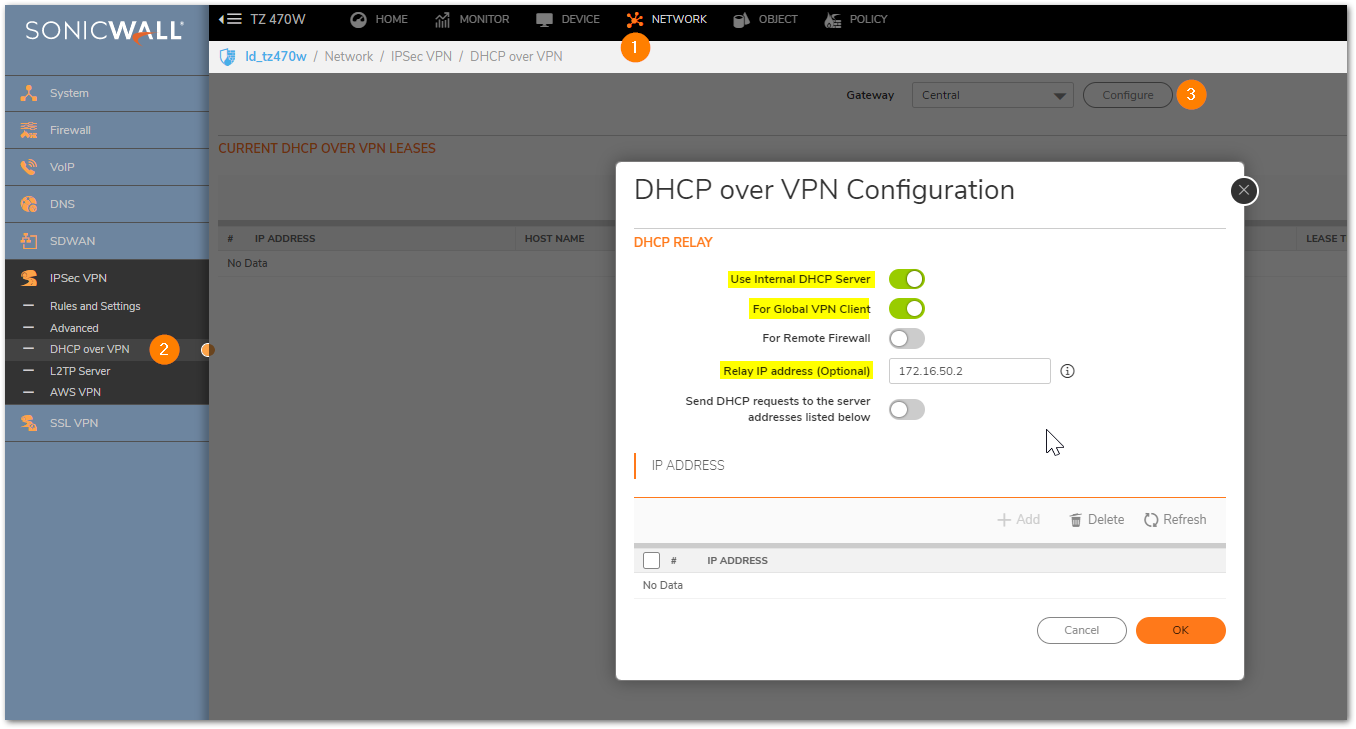
Make sure to check that the pool is big enough to accommodate all the users.- MANAGE | VPN | DHCP over VPN > Make sure that Central Gateway is selected and click Configure.
- Select Use Internal DHCP Server if the SonicWall is the DHCP server. Check the For Global VPN Client checkbox to use the DHCP Server for Global VPN Clients.
ESP Traffic is Blocked
SonicWall GVC may be run from behind a firewall or other device that allows ISAKMP traffic to pass through, but does not allow ESP traffic to pass through. The DHCP requests that get sent for the virtual adapter are sent down the tunnel like any other traffic and are thus encapsulated in ESP. The ESP packets are simply dropped by the firewall with no indication back to GVC.
To work around this problem, GVC is enabled to detect a NAT device in the middle. When GVC detects a NAT device, it encapsulates all ESP traffic (including DHCP packets) using the UDP header. The UDP header uses the same port as ISAKMP control traffic. Therefore the Peer must separate the IKE control traffic from the data traffic.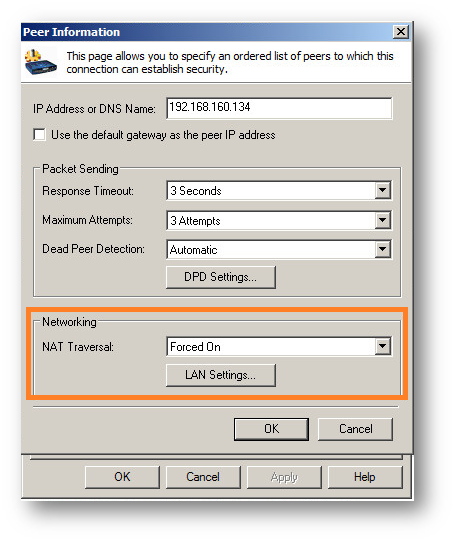
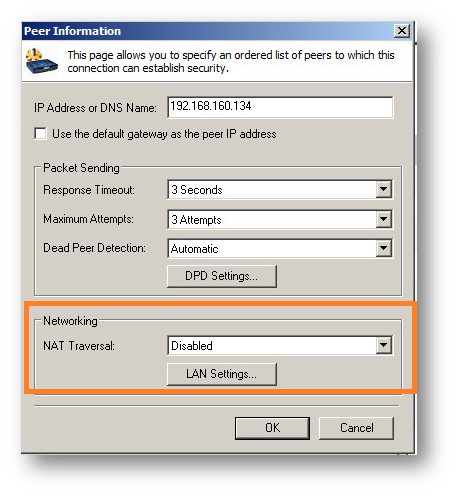
- To configure the NAT traversal setting from the client, select the Connection in GVC and then select File|Properties. Select the Peers tab and then select the appropriate peer (head-end firewall) and choose Edit. Next choose NAT Traversal and select Forced On.
NAT Traversal UDP Encapsulated ESP traffic is blocked
Occasionally GVC may be run from behind a NAT device that improperly handles NAT traversal packets (ESP packets encapsulated in ISAKMP). These packets are discarded by the NAT device without any notification sent back to GVC.
To work around this problem, set GVC never to perform NAT traversal. This means that ESP traffic will not be encapsulated in UDP. In order for this to work, the NAT device must be in IPSec pass-through mode. This mode will prevent multiple GVC clients running simultaneously behind a single NAT device.- To disable NAT traversal in the client, select the Connection in GVC and then select File -> Properties. Select the Peers tab and then select the appropriate peer (head-end firewall) and choose Edit. Next choose NAT Traversal and select Disabled.
Verify settings on the Workstation
- Make sure that the SonicWall LAN subnet and workstation IP address are not in the same subnet.
- Try disabling the firewall and antivirus applications on the workstation. If you are running a client-based software firewall on the Vista machine, check if the version is Vista compatible. If it is not, then upgrade to the latest version. If it does not work after the upgrade then add a rule to allow TCP/UDP port 67/68. If this does not fix the problem then go to step C. (Note: There were numerous problems reported with Norton Internet Security Suite. If you have this software installed then the final try is to Uninstall Norton and reboot your computer and then try again).
- Verify that no 3rd party IPSec VPN clients are installed on your computer. Uninstall any existing IPSec VPN clients (including GVC), reboot, and then install GVC again.
- Make sure that the virtual adapter is not assigned with any static IP address.
- Verify DNE binding is enabled for the SonicWall Virtual Adapter. Go to Start->Control Panel->Network and Internet->Network and Sharing Center->Mange network connections page. Select SonicWall Virtual Adapter and right click on properties. On the properties page verify Deterministic Network Enhancer binding is enabled.
- Wireless WLAN 4.10+ wireless network driver includes VLAN Priority Support which conflicts with getting a DHCP lease for the SonicWall Virtual Adapter. Check if VLAN Priority Support is enabled. If it is, disable it by performing the following steps:
- Right-click My Computer on the desktop and click Properties.NOTE: If there is no My Computer icon on the desktop, click Startand right-click My Computer on the right column of the Start menu.
- When the System Properties window appears, click the Hardwaretab and click Device Manager.
- When the Device Manager window appears, click the <+> next toNetwork Adapters and double-click Wireless WLAN Adapter.
- When the Wireless WLAN Adapter Properties window appears, click the Advanced tab.
- Scroll down to VLAN Priority Support and click to highlight.
- Select Disable from the drop-down menu under the Value: field.
- Click OK to close the Wireless WLAN Adapter Properties window.
- Click the X button in the upper right-hand corner of the Device Manager window to close it.
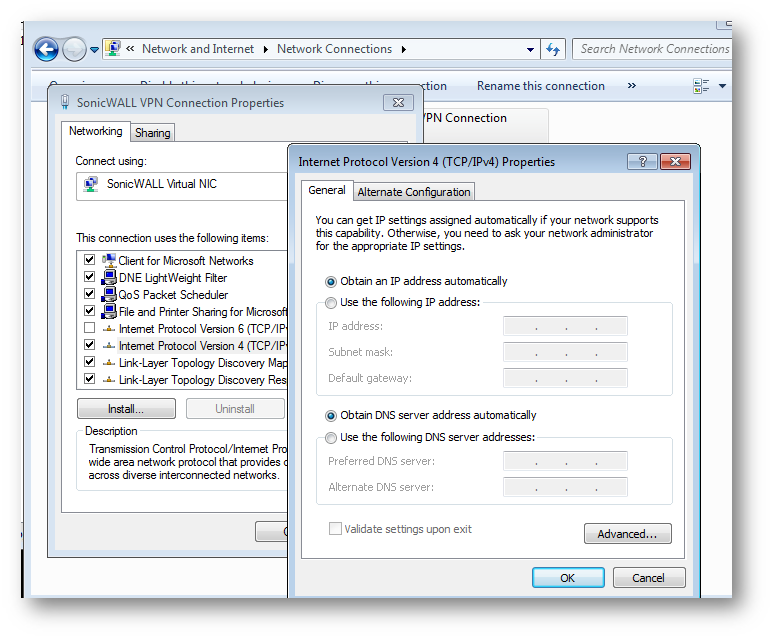
Setting on the SonicWall virtual NIC Static IP.
- To do this you will need to go into:
- Network and sharing centre .
- Change adapter settings
- Select SonicWall VPN connection
- To configure the NAT traversal setting from the client, select the Connection in GVC and then select File|Properties. Select the Peers tab and then select the appropriate peer (head-end firewall) and choose Edit. Next choose NAT Traversal and select Forced On.
- Go to properties select IPv4 and put in an unused IP from the your ip pool.
- If the client connects, with no issue after adding a static IP you are left with a couple of options.
- Export the settings, make a backup.
- Boot device into safe mode.
- Factory default settings to the current firmware.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
If you are using the SonicWall’s internal DHCP server
- Check if the DHCP server has a range big enough to accommodate all clients.
If you’re using a Windows DHCP server:
Make sure to check that the pool is big enough to accommodate all the users.- MANAGE | VPN | DHCP over VPN > Make sure that Central Gateway is selected and click Configure.
- Select Use Internal DHCP Server if the SonicWall is the DHCP server. Check the For Global VPN Client checkbox to use the DHCP Server for Global VPN Clients.

ESP Traffic is Blocked
SonicWall GVC may be run from behind a firewall or other device that allows ISAKMP traffic to pass through, but does not allow ESP traffic to pass through. The DHCP requests that get sent for the virtual adapter are sent down the tunnel like any other traffic and are thus encapsulated in ESP. The ESP packets are simply dropped by the firewall with no indication back to GVC.
To work around this problem, GVC is enabled to detect a NAT device in the middle. When GVC detects a NAT device, it encapsulates all ESP traffic (including DHCP packets) using the UDP header. The UDP header uses the same port as ISAKMP control traffic. Therefore the Peer must separate the IKE control traffic from the data traffic.
- To configure the NAT traversal setting from the client, select the Connection in GVC and then select File|Properties. Select the Peers tab and then select the appropriate peer (head-end firewall) and choose Edit. Next choose NAT Traversal and select Forced On.
NAT Traversal UDP Encapsulated ESP traffic is blocked
Occasionally GVC may be run from behind a NAT device that improperly handles NAT traversal packets (ESP packets encapsulated in ISAKMP). These packets are discarded by the NAT device without any notification sent back to GVC.
To work around this problem, set GVC never to perform NAT traversal. This means that ESP traffic will not be encapsulated in UDP. In order for this to work, the NAT device must be in IPSec pass-through mode. This mode will prevent multiple GVC clients running simultaneously behind a single NAT device.
- To disable NAT traversal in the client, select the Connection in GVC and then select File -> Properties. Select the Peers tab and then select the appropriate peer (head-end firewall) and choose Edit. Next choose NAT Traversal and select Disabled.
Verify settings on the Workstation
- Make sure that the SonicWall LAN subnet and workstation IP address are not in the same subnet.
- Try disabling the firewall and antivirus applications on the workstation. If you are running a client-based software firewall on the Vista machine, check if the version is Vista compatible. If it is not, then upgrade to the latest version. If it does not work after the upgrade then add a rule to allow TCP/UDP port 67/68. If this does not fix the problem then go to step C. (Note: There were numerous problems reported with Norton Internet Security Suite. If you have this software installed then the final try is to uninstall Norton and reboot your computer and then try again).
- Verify that no 3rd party IPSec VPN clients are installed on your computer. Uninstall any existing IPSec VPN clients (including GVC), reboot, and then install GVC again.
- Make sure that the virtual adapter is not assigned with any static IP address.
- Verify DNE binding is enabled for the SonicWall Virtual Adapter. Go to Start->Control Panel->Network and Internet->Network and Sharing Center->Mange network connections page. Select SonicWall Virtual Adapter and right click on properties. On the properties page verify Deterministic Network Enhancer binding is enabled.
- Wireless WLAN 4.10+ wireless network driver includes VLAN Priority Support which conflicts with getting a DHCP lease for the SonicWall Virtual Adapter. Check if VLAN Priority Support is enabled. If it is, disable it by performing the following steps:
- Right-click My Computer on the desktop and click Properties.NOTE: If there is no My Computer icon on the desktop, click Startand right-click My Computer on the right column of the Start menu.
- When the System Properties window appears, click the Hardwaretab and click Device Manager.
- When the Device Manager window appears, click the <+> next toNetwork Adapters and double-click Wireless WLAN Adapter.
- When the Wireless WLAN Adapter Properties window appears, click the Advanced tab.
- Scroll down to VLAN Priority Support and click to highlight.
- Select Disable from the drop-down menu under the Value: field.
- Click OK to close the Wireless WLAN Adapter Properties window.
- Click the X button in the upper right-hand corner of the Device Manager window to close it.

Setting on the SonicWall virtual NIC Static IP.
- To do this you will need to go into:
- Network and sharing centre .
- Change adapter settings
- Select SonicWall VPN connection
- Go to properties select IPv4 and put in an unused IP from the your IP pool.

- If the client connects, with no issue after adding a static IP you are left with a couple of options.
- Export the settings, make a backup.
- Boot device into safe mode.
- Factory default settings to the current firmware.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > GVC/L2TP
- Firewalls > SonicWall SuperMassive E10000 Series > GVC/L2TP
- Firewalls > TZ Series > GVC/L2TP
- Firewalls > NSa Series > GVC/L2TP






 YES
YES NO
NO