-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Extracting wildcard certificate and keys for import to GMS/Analytics Server



Description
A website certificate can be imported into GMS or Analytics for HTTPS access. Some Administrators opt to utilize a single wildcard certificate which can be imported with both the public and private key to multiple servers, and therefore used to authenticate multiple servers at multiple subdomains within the domain.
A wildcard certificate approved by a certificate authority is typically exported in a .pfx (PKCS12) file, which includes the both certificate with the public key and the private key encrypted with a passphrase. The Open SSL utility has the ability to extract the certificate and private keys to separate .pem files, then extract the server private key from the passphrase so it can be imported into your GMS deployment.
The following steps can be used to perform this action for any public webserver certificate, whether wildcard for the domain or else a single subdomain, from an exported .pfx file, using Win32 OpenSSL:
Resolution
Install Win32 OpenSSL
1.) On any supported Windows 32 or 64 bit OS, download the latest version of Win32 Open SSL. (Note that whereas the 32 bit version works for both 32 and 64 bit deployments, the 64 bit version will only work for 64 bit deployments).
https://slproweb.com/products/Win32OpenSSL.html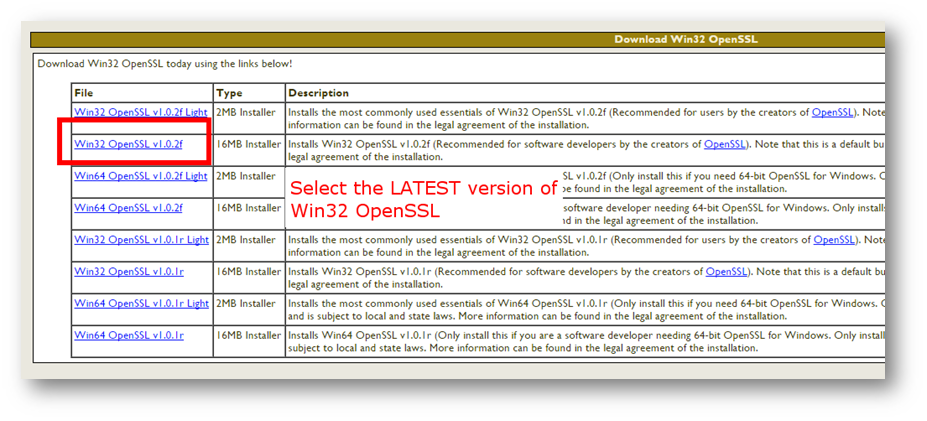
1a.) Only if necessary, also download and install Visual C++ 2008 Redistributable Package (Already included on many recent windows server versions or with some other software downloads).
2.) Install to c:openssl-win32 (if modified, use the modified location instead of the location given in the instructions below).
3.) Once installed, open a command prompt as administrator
4.) Navigate to the bin folder of the installation at prompt:
cd c:openssl-win32bin
5.) Execute the following command (if this is not run, an error may occur later):
set OPENSSL_CONF=c:openssl-win32binopenssl.cfg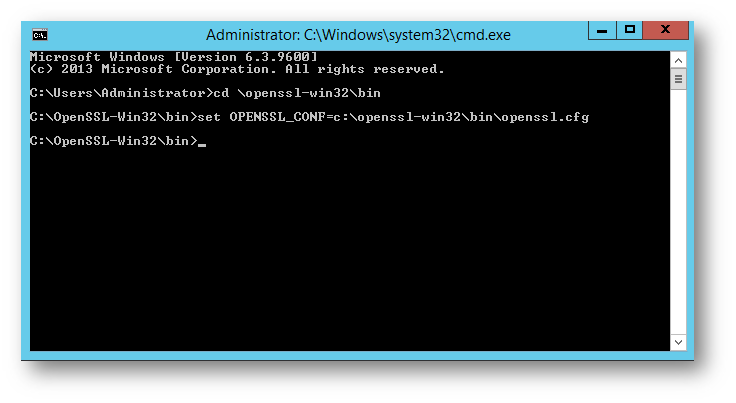
Extract Certificate and Private Key Files from a .pfx file
1.) Copy the .pfx file certificate to the system (TheOpenSSL-Win32 bin folder is often used for this)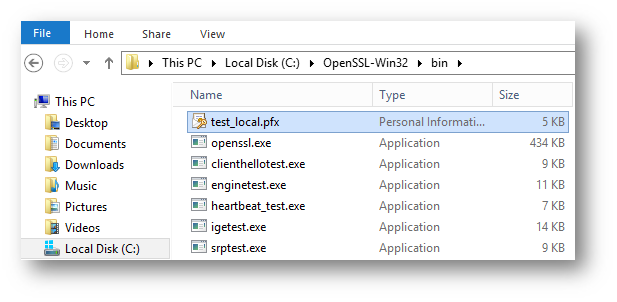
2.) Export the private key to key.pem.
openssl pkcs12 -in certname.pfx - nocerts -out key.pem -nodes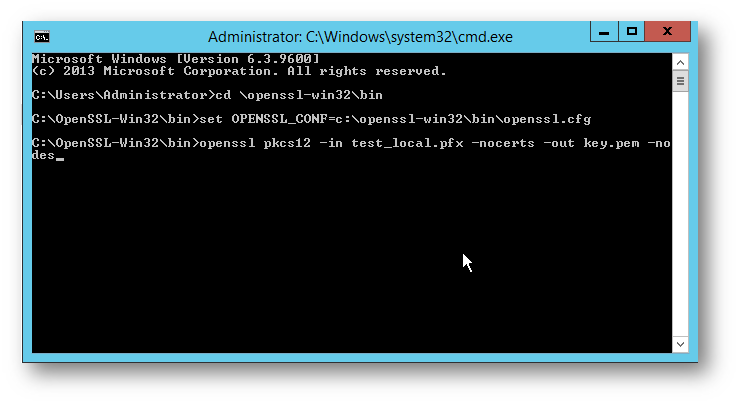
You will be prompted for the .pfx password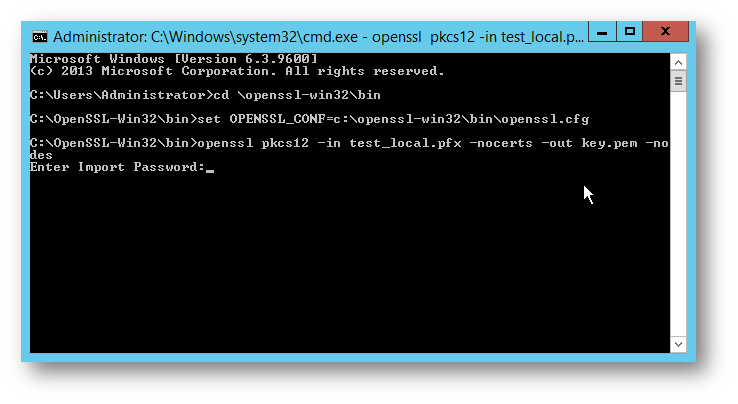
3.) Export the certificate
openssl pkcs12 -in certname.pfx - nokeys -out cert.pem
You will be prompted for the .pfx password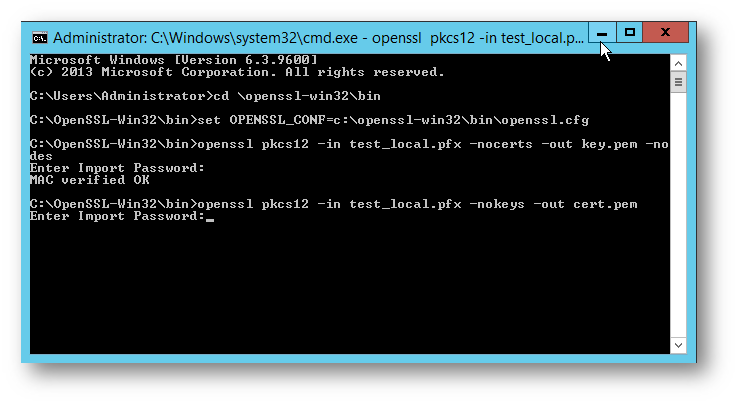
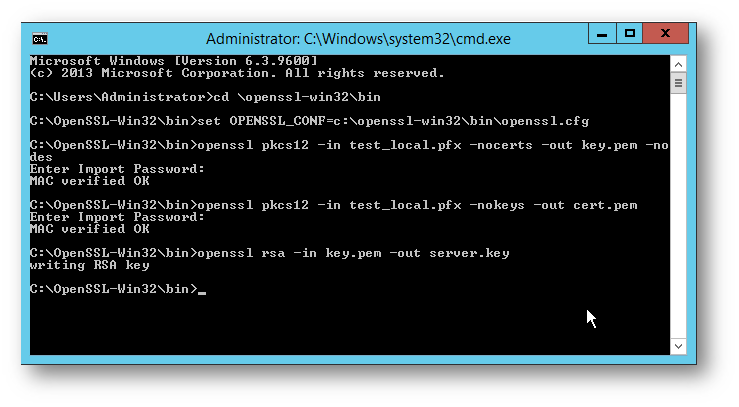
4.) Remove the passphrase from the private key, creating a keyfile
CAUTION: Do not allow key files to become accessible to anyone not responsible for domain devices
openssl rsa -in key.pem -out server.key
Import the cert.pem and server.key files into GMS for management
1.) Login to the system interface of GMS at https://(ipaddress:port)/appliance.html
2.) Navigate to Deployment > Settings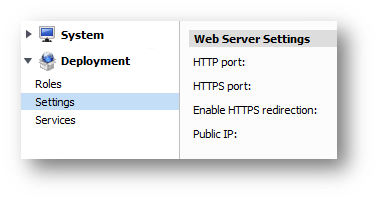
3.) Under SSL Access Configuration, select "Custom"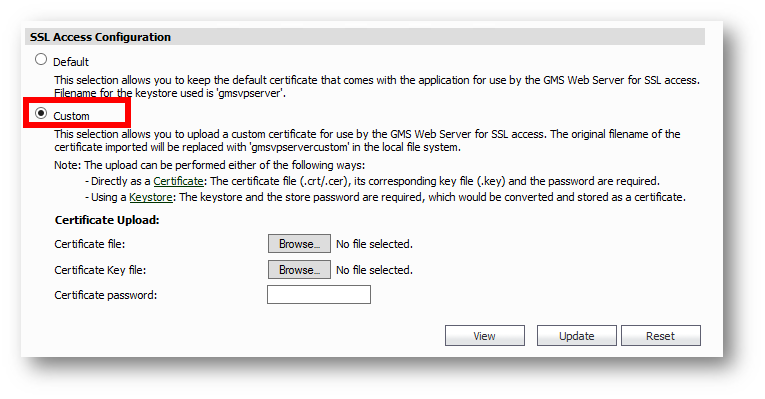
4.) For "Certificate file", click "browse" and select the cert.pem file that was extracted earlier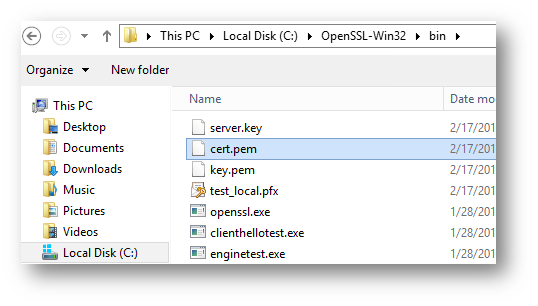
5.) For "Certificate Key file", select the server.key file that was extracted earlier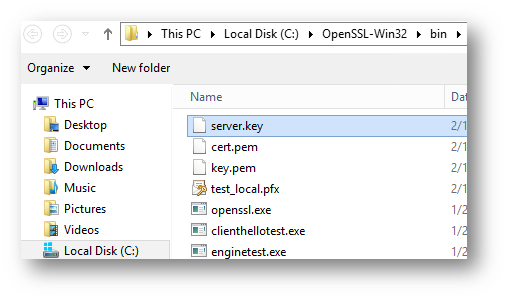
6.) Enter the password originally used to extract information from the .pfx file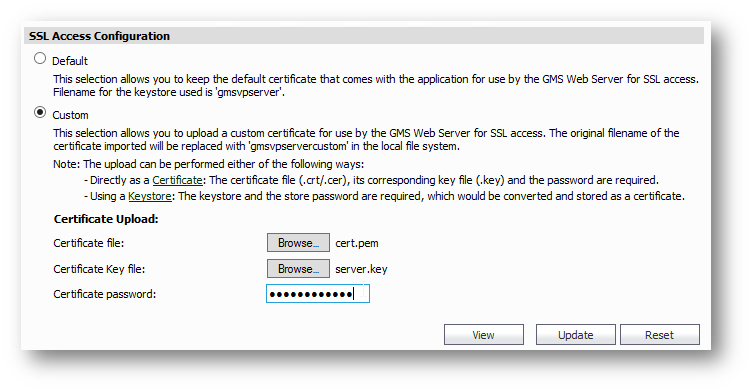
7.) Accepting the Prompt will restart the GMS server with the new certificate in place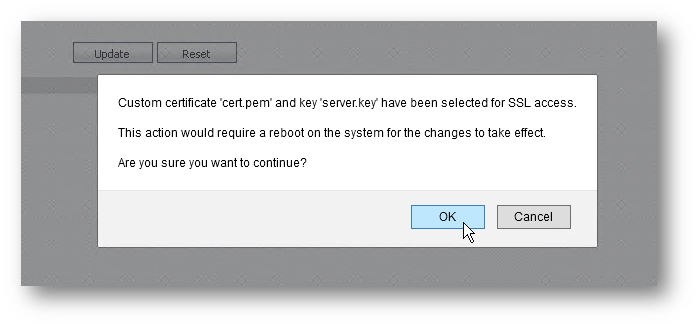
Related Articles
- Creating a license subscription report in GMS 9.3
- How to create SSLVPN login reports with Syslog GMS/Analytics
- Can I review, accept and deny the GMS changes before pushing to firewalls with workflow license?






 YES
YES NO
NO