-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Explanation of SonicPoint and Internal Wireless advanced settings



Description
- EAPOL Version and Band Steering
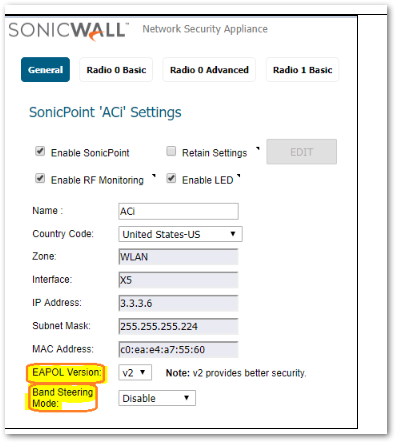
- EAPOL Version
EAPOL packet Protocol version field holds the version of the protocol supported by the sender of the EAPOL packet. It means the supplicant will try with a more secure protocol version with the server if server does not support that, then supplicant with try with the next/lower one available until both server and client negotiate on a common protocol version.
EAPOL Version 2 will provide better security however if we see unexpected replay counter then we can use EAPOL v1 which can be addressed by using v1. - Band Steering
Band Steering detects clients capable of 5 GHz and steers them to that frequency, while leaving 2.4 GHz available for legacy clients.If the AP hears a probe request from a wireless client on the 2.4GHz band while band steering is enabled, it only responds if it has not heard anything on the 5GHz band from that same client in the last 60 seconds. The AP promiscuously listens for all probe requests, association requests and re-association requests sent by all clients. If a 2.4GHz probe is received, the AP will not respond if it has heard any of the frame types on the 5GHz band in the last 60 seconds. If it has seen any of them, the AP will only send a probe response advertising the wireless network in response to a 5GHz probe once it gets one. This steers the client to the 5GHz band. If the AP hears probes from a wireless client on 2.4GHz only, it will respond with a probe request advertising the network.
Band steering also functions completely irrespective of the strength of the signal. Even if the signal strength on the 5GHz band is much weaker than on the 2.4GHz band, the AP will only respond to probe requests on the 5GHz band.
- Logging via SSH
Use your own created credentials (Admin / Password) below as highlighted for login via SSH.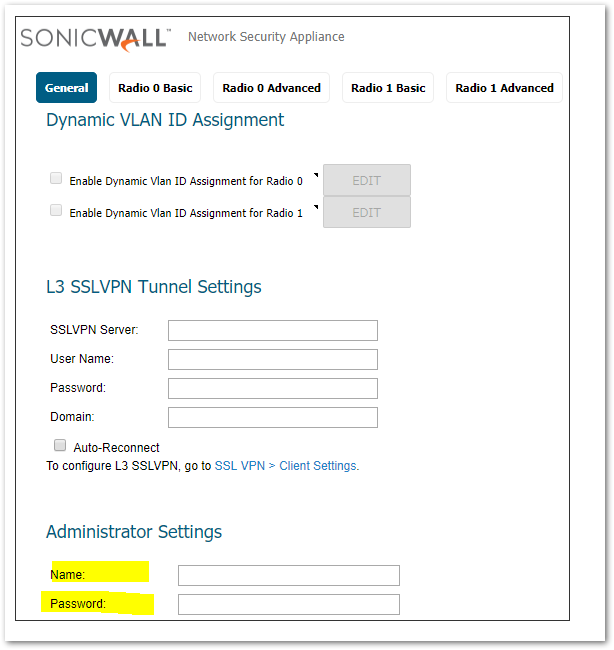
- DFS Chanel
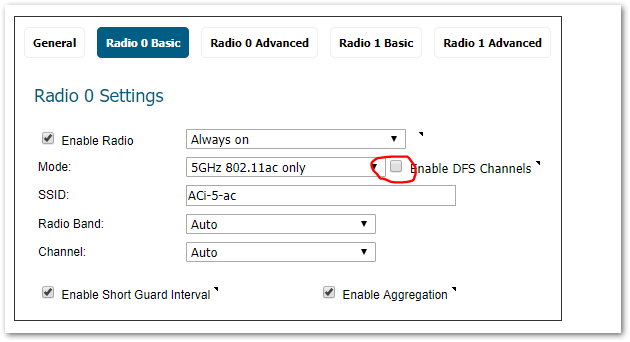
Dynamic Frequency Selection is a spectrum-sharing mechanism that allows WLANs to coexist with radar systems. It automatically selects a frequency that does not interfere with certain radar systems while operating in the 5 GHz band.DFS is a mechanism to allow unlicensed devices to use the 5 GHz frequency bands already allocated to radar systems without causing interference to those radars. The concept of DFS is to have the unlicensed device detect the presence of a radar system on the channel they are using and, if the level of the radar is above a certain threshold, vacate that channel and select an alternate channel. - When to use DFS Channel?
5 GHz interfered environment.Not all of the channels in the 5 GHz band are usable all of the time. If you are near an airport then some of the 5 GHz channels are not available to you. You must have that feature turned on and your APs will listen for Radar or first responders using those 'shared' frequencies and not use those channels if they are being used.
- Short Guard Interval (What is Guard Interval?)
Guard Interval is used to avoid signal loss from multipath effect. This would avoid any kind of data loss from wireless interference. In wireless transmission, RF signals reach the receiving antenna by two or more paths, if the latter information symbol reaches the antenna too fast, signal may interfere with the earlier symbol.
Inter-symbol interference is a signal distortion in telecommunication. One or more symbols can interfere with other symbols causing noise.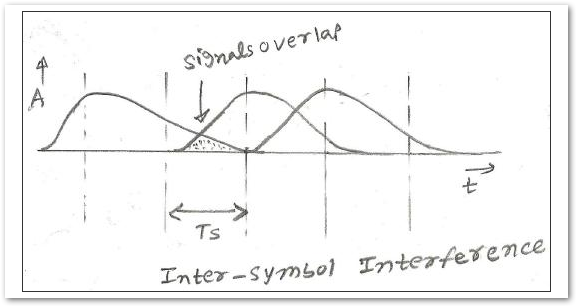
If you are in an environment that is prone to bad multipath situations, then you probably don't need as you would want the longer guard interval of 800ns. However, for office environments, having a Short Guard Interval (SGI), which lowers the interval to 400ns, can give you an increased data rate of 11%.
802.11a/b/g requires guard interval (GI) to be 800 ns. From 802.11n and the next 802.11ac, short guard interval (400 ns) is introduced, while the default value of GI is still set as 800 ns. - When to use short GI?
- To improve the throughput, enable short GI this can improve the throughput about 10%.
- If the multipath effect is not too serious (not too many metals or other reflecting materials), you can enable short GI.
- If you are using 802.11n or 802.11ac only, you can enable short GI.
- When using mixed mode, please disable the short GI, which may cause issues.
- Enable this to have a higher Tx/Rx rate if supported. It applies only to 802.11ac/n mode.
- Where to enable short GI?
Navigate to Manage|SonicPoints|Base Settings, click Configure of the SonicPoint in SonicPoint AC/N Object area, click Radio 0 basic tab.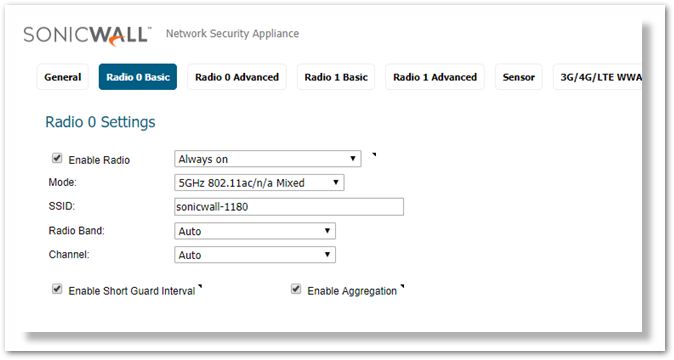
- Aggregation
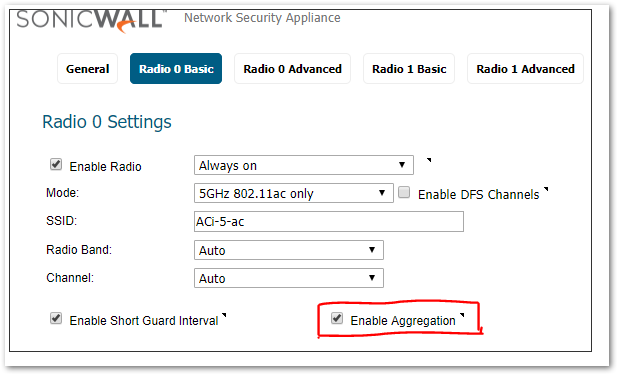
Enables 802.11n or ac frame aggregation, this combines multiple frames to reduce overhead and increase throughput by sending multiple data frames in a single transmission for the same destination. Note that even the wireless client has to support Aggregation for this to work as expected.The upper layer information for a MAC layer in 802.11 called as the MSDU. Once there is, a header and footer added to the MSDU, it is now called as MPDU. This is now send to the lower layer called physical layer.
Aggregated-MSDU - This is new function added in 802.11n, this make it possible to send more data during the given Transmit opportunity. Collection of MSDU packets are called A-MSDU and then sending them in a single burst through the physical layer.
Aggregated-MPDU - Again, this is new function added in 802.11n and its collection on multiple MPDUs and sending them in a single burst through physical layer. You will find multiple mac header and mac checksum inside an A-MPDU. - When to use Aggregation?
For achieving higher throughput as it Enables 802.11n frame aggregation, which combines multiple frames to reduce overhead and increase throughput. It applies only to 802.11ac/n mode.The Enable Short Guard Interval and Enable aggregation options can slightly improve throughput. They both function best in optimum network conditions where users have strong signals with little interference. In networks that experience less than optimum conditions (interference, weak signals, etc.), these options may introduce transmission errors that eliminate any efficiency gains in throughput.
- Authentication Type, Cypher Type, Group Key Interval
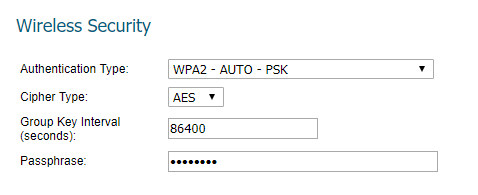
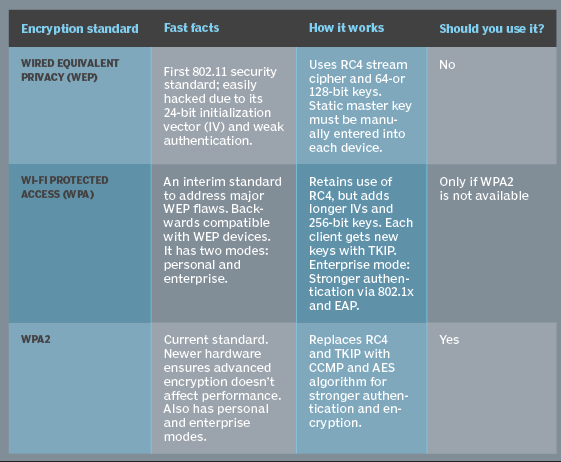
- Cypher Types
- WEP 64 (risky): The old WEP protocol standard is vulnerable and you really should’t use it.
- WEP 128 (risky): This is WEP, but with a larger encryption key size. It isn’t really any less vulnerable than WEP 64.
- WPA-PSK (TKIP): This uses the original version of the WPA protocol (essentially WPA1). It has been superseded by WPA2 and is not secure.
- WPA-PSK (AES): This uses the original WPA protocol, but replaces TKIP with the more modern AES encryption. It is offered as a stopgap, but devices that support AES will almost always support WPA2, while devices that require WPA will almost never support AES encryption.
- WPA2-PSK (TKIP): This uses the modern WPA2 standard with older TKIP encryption. This isn’t secure, and is only a good idea if you have older devices that can’t connect to a WPA2-PSK (AES) network.
- WPA2-PSK (AES): This is the most secure option. It uses WPA2, the latest Wi-Fi encryption standard, and the latest AES encryption protocol. You should be using this option.On some devices, you will just see the option “WPA2” or “WPA2-PSK.” If you do, it will probably just use AES, as that is a common-sense choice.
- WPAWPA2-PSK (TKIP/AES): Some devices offer—and even recommend—this mixed-mode option. This option enables both WPA and WPA2, with both TKIP and AES. This provides maximum compatibility with any ancient devices you might have, but also allows an attacker to breach your network by cracking the more vulnerable WPA and TKIP protocols.
- Group Key Interval
WPA automatically changes secret keys after a certain time period. The group rekey interval is the period of time in between automatic changes of the group key, which all devices on the network share.
The group key is used for Multicast and broadcast messages. It is shared between all clients and the access point. It is updated periodically at the interval configured. And when a client leaves the network the group key should be updated to prevent the client from receiving future Multicast or broadcast messages. - ACL Enforcement
Select this to enforce Access Control by allowing or denying traffic from specific devices. Select a MAC address group from the Allow List to automatically allow traffic from all devices with MAC address in the group. Select a MAC address group from the “Deny List” to automatically deny traffic from all devices with MAC address in the group. The deny list is enforced before the Allow list.
- Channel Bonding

Channel bonding commonly uses two contiguous 20MHz channels to create a single 40MHz channel. You can also use two contiguous 40MHz channels to create a single 80MHz channel While channel bonding can provide higher data rates, it will also result in fewer channels available for 2.4GHz or 5GHz devices.
In some high-density client environments where wireless saturation is high, having more 20MHz channels can spread client usage provides better performance than having fewer 40MHz channels. - WDS AP, Enable Green AP, Air Time Fairness

- WDS AP
Enable this to allow the WDS client to connect to this access point. - Green AP
SonicWall access points support green AP mode. When no client connects to the AP, enabling this feature will allow the radio to go to sleep mode for power saving. The sleep Radio will exit power save mode once any client associates with it. - Air Time Fairness
One of the best technology in SP i.e.. “Airtime Fairness” and how it works?
 EXAMPLE:
EXAMPLE: - Let us say you have an ACe model, which is 802.11n
- Connected to it you got 1 802.11g which can transmit theatrically to 54mbps.
- Connected to it you got a 802.11n which can transmit theatrically to 300mbs
- Now how will this work?
As you know, just one client can access the wireless medium at time in Wireless medium, if one is transmitting at that time no one else cannot, so just one can be on the channel at one time.
Now without the fairness the AP sends a packet let say of 1500bytes to 802.11n station and then it send another packet 1500bytes packet to the 802.11g station (This is packet based! with no airtime fairness on).This is what how it normally works without the airtime fairness on.If you see 802.11g will need more time in the channel to get those 1500 packet while the 802.11n does not need too much time because of bandwidth. As you see this is awful for the 802.11n. Why? Because its making it goes slower, as the 802.11g client spend more time on the channel. This is the reason when we turn on the “Airtime fairness” so slower clients like 802.11b or 802.11g do not monopolize the BW.
- What happens when you turn the airtime fairness ON?
Instead of sending a 1500 packet for example to the 802.11n and one packet of 1500 packet to 802.11g, it will assign a time! for example it will assign 200micro second to the 802.11n station and also 200ms to the 802.11g station so as you see now its "FAIR" the 802.11g will send yes less data than 802.11n but now it’s will not slower the 802.11n and now the 802.11g is not making the 802.11n going slower.
That is why it’s known as Airtime Fairness because it give fair time in the air to both clients.
- Radio 0 and Radio 1 Advanced options
|
|
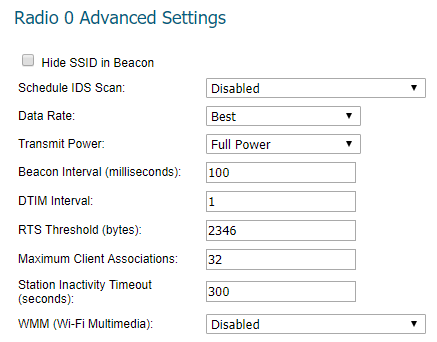
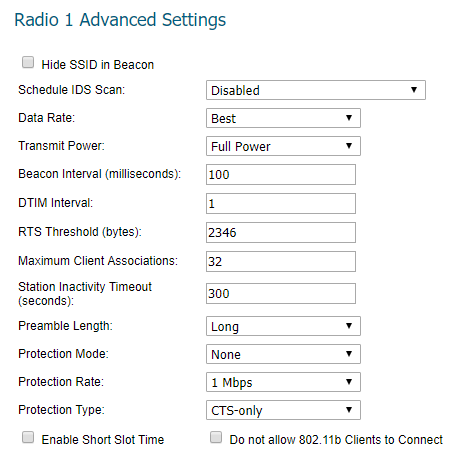
- Hide SSID in Beacon
This is an option to suppress the SSID. The wireless clients have to manually create the profiles to get connected to the appropriate SSID. - Schedule IDS Scan
Select a time when there are fewer demands on the wireless network to schedule an Intrusion Detection Service (IDS) scan to minimize the inconvenience of dropped wireless connections. - Data Rate
Select the speed at which the data is transmitted and received. Best automatically selects the best rate available in your area given interference and other factors. Or you can manually select a data rate. - Transmit Power
Transmission power effects the range of the Sonic Point. Transmit power is directly proportional with the coverage area. High the transmit power more area can be covered. - Antenna Diversity
The Antenna Diversity setting determines which antenna the Sonic Point uses to send and receive data. When Best is selected, the Sonic Point automatically selects the antenna with the strongest, clearest signal. This is a technique used to improve the quality and reliability of a wireless link when using two or more antennas. - Beacon Interval (milliseconds)
Enter the number of milliseconds between sending out a wireless beacon. This packet carries the SSID, channel number and the security protocols. The Beacon interval is a part of the Beacon frame. - DTIM Interval
A DTIM is a kind of Traffic Indication Message (TIM), which informs the clients about the presence of buffered Multicast/broadcast data on the access point. When the AP has buffered broadcast or Multicast messages for associated clients, it sends the next DTIM with a DTIM Interval value (Default=1). Clients for that AP hear beacons and awaken to receive the broadcast and Multicast messages. - Fragmentation Threshold (bytes)
It specifies the maximum size for a packet before data is fragmented into multiple packets. The range can be from 256-2346. For best throughput, keep it at the default value- 2346. - RTS Threshold (bytes)
This is the threshold bytes where the access point waits to send a ‘Request to Send’ message to the wireless client. Default value- 2346. - Maximum Client Associations
Enter the maximum number of clients you want the Sonic Point to support on this radio at one time. - Preamble Length
Preambles are pauses that come before a wireless signal hits a networking device. This pause varies in length, the duration of which defines it as a long or short preamble. The gap between two data packets to be sent across to the wireless client. Short Preamble length reduces the overhead and the wait time. Select the long option if you have too much interference in the wireless signals.
Long preamble is mostly used by legacy systems. Short preamble was primarily introduced for efficiency. All 802.11g devices must be able to transmit and receive long preamble. However, support of short preamble is optional for 802.11b devices.Short preamble is enabled by default. - Protection Mode
When set to Auto, a protection mechanism will ensure that your Wireless-B devices will connect to the Wireless-G router when many Wireless-G devices are present. However, performance of your Wireless-G devices may get decreased. Auto option will engage only in the case of overlapping Sonic Points. Protection can decrease collisions, particularly where you have two overlapping Sonic Points. - Protection Rate
The protection rate determines the data rate when protection is on. The slowest rate offers the greatest degree of protection but the slowest data transmission rate. Protection rate can vary between 1, 2, 5 and 11 Mbps, which can be set manually. - Protection Type
Select the type of handshake used to establish a wireless connection: CTS-only or RTS-CTS. 802.11b traffic is only compatible with CTS. - Enable Short Slot Time
The amount of time a device waits after a collision before retransmitting a packet. The short slot time is reduced from a standard 20 microsecond to 9 microsecond mark when it is enabled. This is helpful only in 802.11g environment. Allow clients to disassociate and re-associate more quickly. - Allow only 802.11g Clients to Connect
Use this if you are using Turbo G mode and therefore are not allowing 802.11b clients to connect.
Related Articles
- SonicWall deprecates support for WEP and TKIP encryption on SonicOS 8.0.0
- End of sale "SMA and Sonicwave" product for India.
- What is the WPA2 KRACK exploit and is SonicWall vulnerable?






 YES
YES NO
NO